当前位置:网站首页>Paper notes ACL 2020 improving event detection via open domain trigger knowledge
Paper notes ACL 2020 improving event detection via open domain trigger knowledge
2022-07-04 12:34:00 【hlee-top】
List of articles
1 brief introduction
Thesis title :Improving Event Detection via Open-domain Trigger Knowledge
Source of the paper :ACL 2020
Thesis link :https://aclanthology.org/2020.acl-main.522.pdf
Code link :https://github.com/shuaiwa16/ekd
1.1 motivation
- Due to the long tail problem of marked data ( A large number of categories, only a small number of samples ) And the homogeneity of generated data , Previous methods have performed poorly on unseen or sparse data , Over fitting on dense data .
1.2 innovation
- The first one is to improve the performance of event detection by using the trigger word knowledge of open domain .
- Put forward a new teacher-student Model , Learn from tagged and unlabeled data , Reduce the built-in deviation in the tag .
2 Method
2.1 Knowledge collection
from WordNet Collect open domain trigger word knowledge , It is divided into the following two steps :
- Disambiguate words : Use IMS disambiguation , And then use Stanford CoreNLP Get features ( Part of speech tagging 、 Syntactic parsing ).
- Determine whether the event is triggered : Use a table lookup method , Determine whether the event is triggered .
2.2 Model
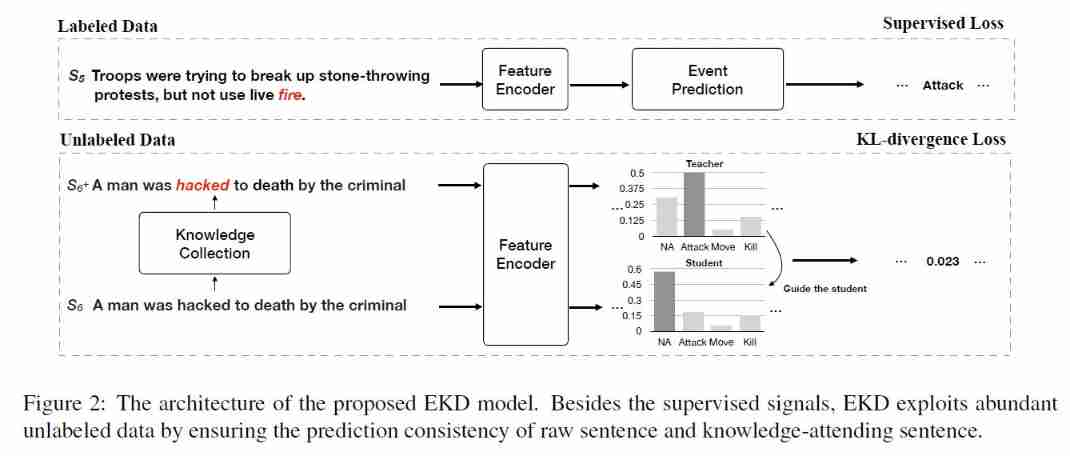
The overall framework of the model is shown in the figure above , It mainly includes the following parts :
- feature extraction : Use BERT Code the sentence .
- Event prediction : For marked data , Predict the event type of each word . The formula is as follows :
 |  |
- Distillation of knowledge : The goal of knowledge distillation is to make teacher The probability of the model is equal to student Probability of model ( The formula is as follows ), Two models share parameters ,teacher The input to the model is S + S^+ S+(Knowledge-attending Sentences), Trigger word knowledge through open domain , Use B-TRI and E-TRI Mark the start and end boundaries of the trigger word . If the original sentence is S = { w 1 , w 2 , . . . , w i , . . . , w n } S=\{w_1,w_2,...,w_i,...,w_n\} S={ w1,w2,...,wi,...,wn}, w i w_i wi Trigger words defined for open domain trigger word knowledge , S + = { w 1 , w 2 , . . . , B − T R I , w i , E − T R I , . . . , w n } S^+=\{w_1,w_2,...,B-TRI,w_i,E-TRI,...,w_n\} S+={ w1,w2,...,B−TRI,wi,E−TRI,...,wn}.B-TRI and E-TRI Fine tune the sentences of knowledge collection (mask The probability of is 15%).student The input to the model is S − S^- S−(Knowledge-absent Sentences), Random mask Trigger words defined by open domain trigger word knowledge , Such as S − = { w 1 , w 2 , . . . , [ M A S K ] , . . . , w n } S^-=\{w_1,w_2,...,[MASK],...,w_n\} S−={ w1,w2,...,[MASK],...,wn}. Use KL Divergence minimizes the difference between probability distributions , The formula is as follows :
 |  |
- Joint training : The goal of optimization is the supervision with labeled data loss And unmarked data KL The divergence loss, The formula is as follows :
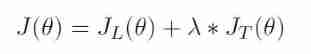
3 experiment
stay ACE 2005 The experimental results on the data set are shown in the figure below :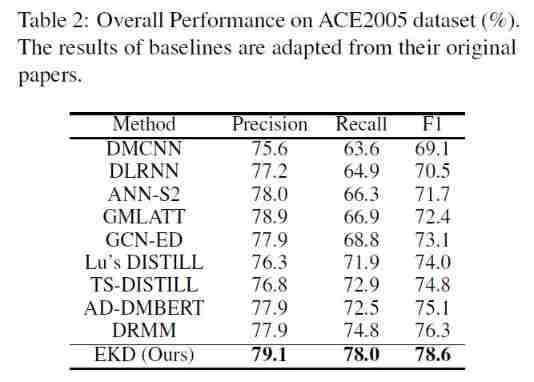
To evaluate whether knowledge is distilled into the model , Observe the experimental effect of trigger word knowledge with and without open domain on the test set , The results are as follows :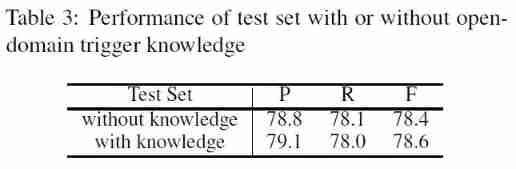
Experimental results in the case of domain transfer :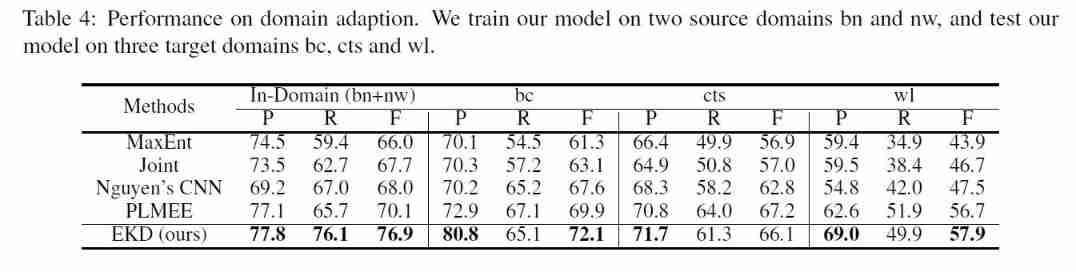
Experimental results of trigger words with different frequencies :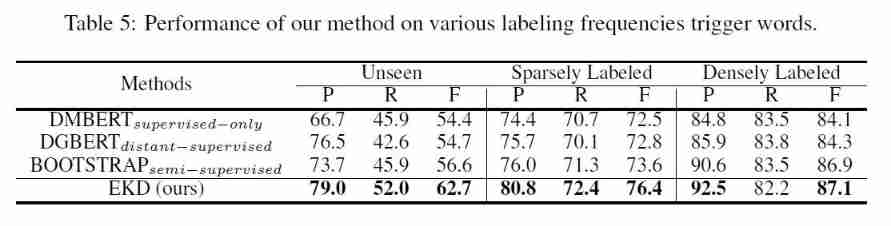
Use three different kinds of knowledge , Verify whether the model can distill other knowledge types , The experimental results are shown below :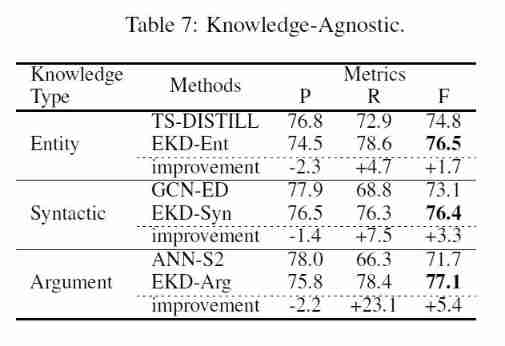
Case Study:
边栏推荐
- LVS load balancing cluster deployment - Dr direct routing mode
- Wechat video Number launches "creator traffic package"
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 22
- The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
- Introduction of network security research direction of Shanghai Jiaotong University
- 8.8.1-PointersOnC-20220214
- [solve the error of this pointing in the applet] SetData of undefined
- Enter the smart Park, and change begins here
- Iframe to only show a certain part of the page
猜你喜欢
Leetcode: 408 sliding window median
Process communication and thread explanation
Servlet learning notes
Method of setting default items in C # ComboBox control code
DVC use case (VI): Data Registry
The detailed installation process of Ninja security penetration system (Ninjitsu OS V3). Both old and new VM versions can be installed through personal testing, with download sources
MySQL performance optimization index
Complementary knowledge of auto encoder

It's hard to hear C language? Why don't you take a look at this (V) pointer
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8](/img/16/33f5623625ba817e6e022b5cb7ff5d.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
随机推荐
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
R语言--readr包读写数据
Btrace tells you how to debug online without restarting the JVM
Entitas learning [3] multi context system
Ml and NLP are still developing rapidly in 2021. Deepmind scientists recently summarized 15 bright research directions in the past year. Come and see which direction is suitable for your new pit
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
How to disable debug messages on sockjs stomp - how to disable debug messages on sockjs Stomp
[ES6] template string: `string`, a new symbol in es2015
The frost peel off the purple dragon scale, and the xiariba people will talk about database SQL optimization and the principle of indexing (primary / secondary / clustered / non clustered)
The detailed installation process of Ninja security penetration system (Ninjitsu OS V3). Both old and new VM versions can be installed through personal testing, with download sources
DVC use case (VI): Data Registry
It's hard to hear C language? Why don't you take a look at this (V) pointer
Introduction of network security research direction of Shanghai Jiaotong University
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 10
VBA, JSON interpretation, table structure -json string conversion
Openssl3.0 learning 20 provider KDF
MySQL performance optimization index
Snowflake won the 2021 annual database
Global and Chinese market of piston rod 2022-2028: Research Report on technology, participants, trends, market size and share
BCD code Baidu Encyclopedia