当前位置:网站首页>[blackmail virus data recovery] suffix Crylock blackmail virus
[blackmail virus data recovery] suffix Crylock blackmail virus
2022-07-02 08:35:00 【qq_ thirty-eight million five hundred and thirteen thousand thr】
Catalog
1. suffix .crylock Blackmail virus introduction ?
2. suffix .crylock How the blackmail virus infected my computer ?
3. How to restore .crylock Blackmail virus ?
4. How to avoid .crylock Blackmail virus attack ?
1. suffix .crylock Blackmail virus introduction ?
CryLock Is the name of the malicious program , yes Cryakl Blackmail Software A new variation of . The malware is designed to encrypt data and require payment for decryption .
In the process of encryption , All affected files are renamed in the following pattern : Developer's email address ; The only victim ID, as well as ; An extension consisting of three random characters . The extension of each file is random . for example :
- file.doc.[[email protected]][fervis].[98252B9E-3FE98E00]
- file.doc.[[email protected]][sel4auto].[A15F580C-524AC4DB]
After completing this process ,CryLock Blackmail software will display a pop-up window containing blackmail messages .
Screenshots of messages encouraging users to pay ransom to decrypt their damaged data :

2. suffix .crylock How the blackmail virus infected my computer ?
Blackmail software is spread through the Internet and hidden in many different places . The most common way to infect computer systems is to open spam and visit malicious websites , for example torrent File sharing platform .
Through the so-called spam campaign , Cyber criminals will send millions of emails with infectious email attachments or hyperlinks that redirect unwitting users to malicious websites . If you turn on any of these options , The payload file will be downloaded to the device , Then it starts to infect . There is always an updated antimalware monitoring you .
Cyber criminals can disguise the malware they create as any file type (.exe、.pdf、.jpeg、.txt etc. ). therefore , Torrent website is an ideal place to hide its creation . They can name the file whatever they think will attract the upcoming victim and upload it . Users should not download any software from these sites 、 Crack ( Illegal activation of toolkit ) Or any other suspicious material .
By CryLock Screenshot of encrypted file (“ [cyber_criminals'_email_address][victim's_ID].[3_random_letters] ” Extension ):

CryLock Screenshot of variant encrypted file :

3. How to restore .crylock Blackmail virus ?
This suffix virus file is due to the encryption algorithm , Every infected computer has different server files , It is necessary to independently detect and analyze the virus characteristics and encryption of encrypted files , To determine the most appropriate recovery plan .
Considering the time required for data recovery 、 cost 、 Risk and other factors , If the data is not important , It is recommended to scan the whole disk directly, format and reload the system after antivirus , Follow up system security work can be done . If the infected data does have the value and necessity of recovery , You can add our technical service number (data966) Consult for free to get help with data recovery .
4. How to avoid .crylock Blackmail virus attack ? 
1. Set access to important files and turn off unnecessary file sharing .
2. Perform non local operations on a regular basis ( offline ) Backup .
3. Use a highly secure host password and avoid multiple devices using the same password .
4. Do not 3389 Wait for ports to map directly to Internet Or external network , To prevent brute force cracking .
5. Avoid opening emails from unknown sources 、 Link and URL The attachment .
6. Do not download non genuine software from unofficial websites .
7. If you find that the file type does not match the original icon , You should use endpoint detection software to scan the file to detect any malicious code in the file .
8. Regularly scan for system vulnerabilities , Timely installation of patches .
边栏推荐
- 用数字 5,5,5,1 ,进行四则运算,每个数字当且仅当用一次,要求运算结果值为 24
- What is SQL injection
- W10 is upgraded to W11 system, but the screen is black, but the mouse and desktop shortcuts can be used. How to solve it
- When a custom exception encounters reflection
- Vs code configuration problem
- Web安全--核心防御机制
- In depth understanding of prototype drawings
- Solid principle: explanation and examples
- Nacos 下载启动、配置 MySQL 数据库
- 使用wireshark抓取Tcp三次握手
猜你喜欢
Sqli labs level 12

Use Wireshark to grab TCP three handshakes
OpenFeign 簡單使用
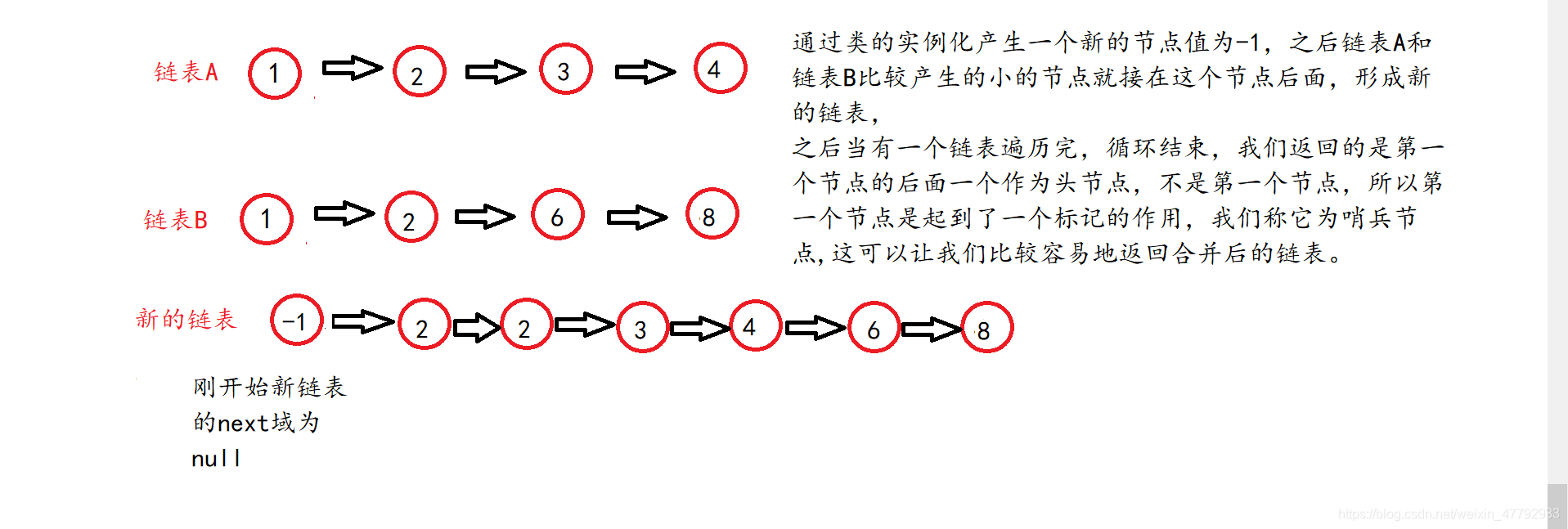
Linked list classic interview questions (reverse the linked list, middle node, penultimate node, merge and split the linked list, and delete duplicate nodes)

Flex layout
cve_ 2019_ 0708_ bluekeep_ Rce vulnerability recurrence
k8s入门:Helm 构建 MySQL
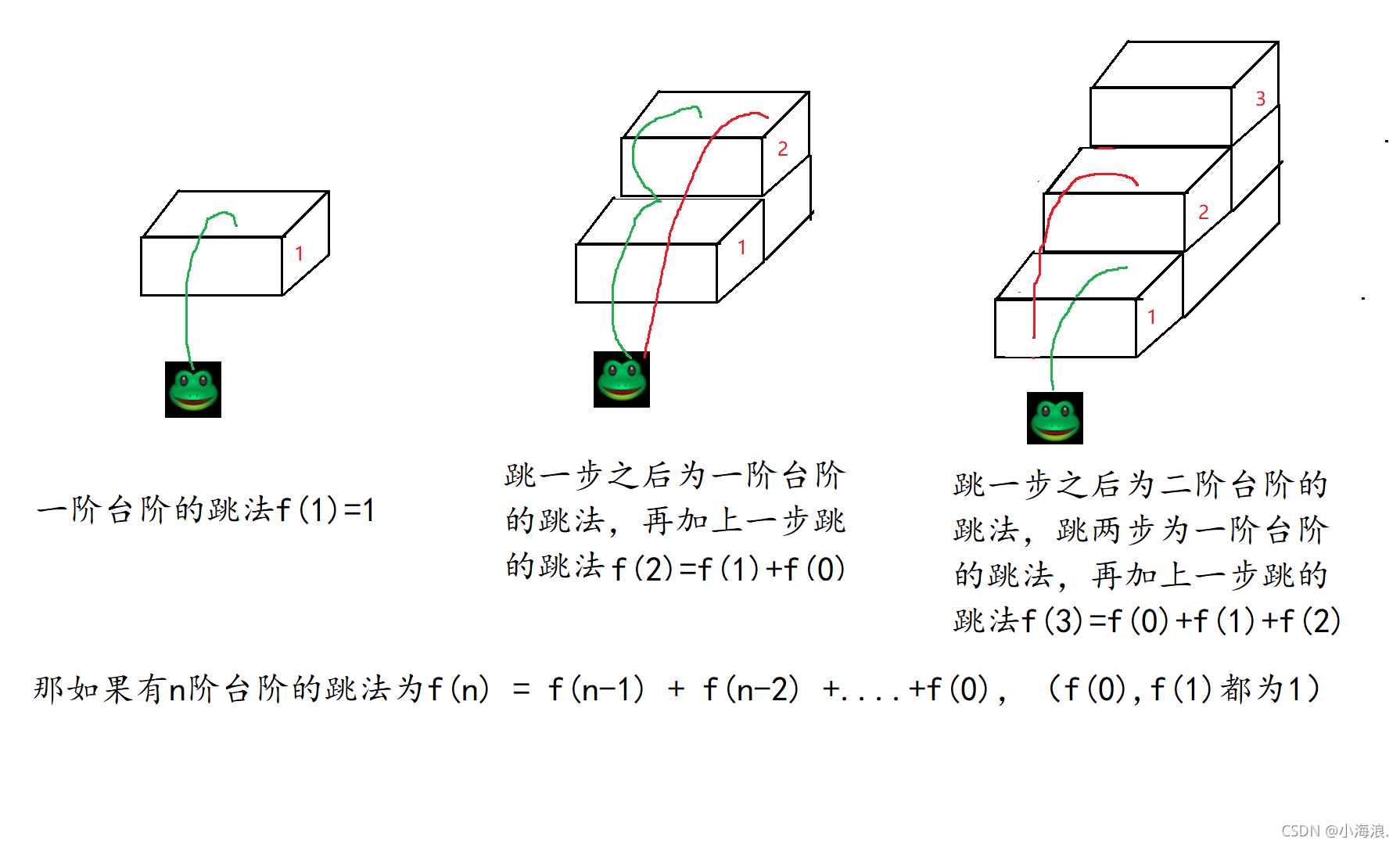
Method recursion (Fibonacci sequence, frog jumping steps, tower of Hanoi problem)
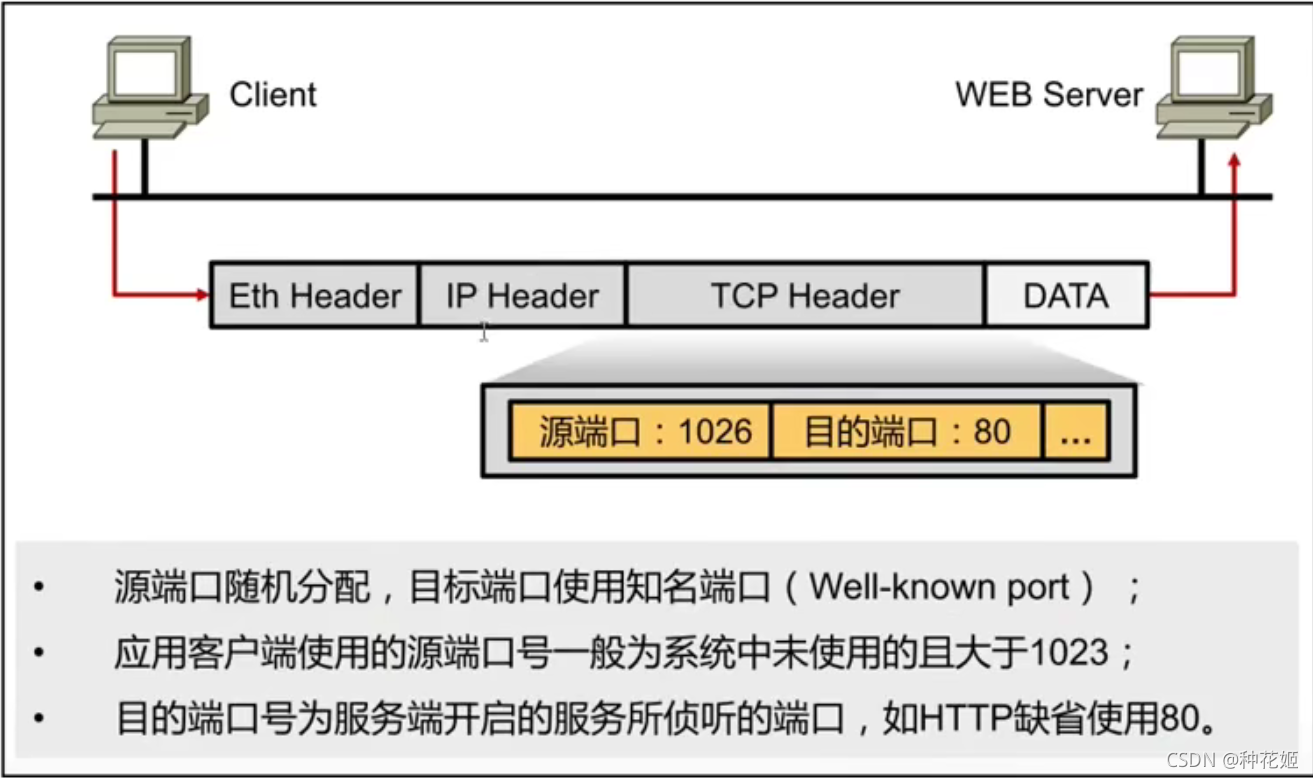
TCP/IP—传输层

C language replaces spaces in strings with%20
随机推荐
Detailed explanation of NIN network
Linked list classic interview questions (reverse the linked list, middle node, penultimate node, merge and split the linked list, and delete duplicate nodes)
Use Matplotlib to draw a preliminary chart
Valin cable: BI application promotes enterprise digital transformation
IP protocol and IP address
Global and Chinese market of wire loop, 2022-2028: Research Report on technology, participants, trends, market size and share
zipkin 简单使用
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Openfeign is easy to use
文件上传-upload-labs
On November 24, we celebrate the "full moon"
Introduction to parameters of CarSim pavement 3D shape file
Multi site high availability deployment
【无标题】
Web security -- Logical ultra vires
Common shortcut keys of Jupiter notebook (you can also view it by pressing h in command mode)
web安全--逻辑越权
c语言自定义类型枚举,联合(枚举的巧妙使用,联合体大小的计算)
方法递归(斐波那契数列,青蛙跳台阶,汉诺塔问题)
Sentinel easy to use
