当前位置:网站首页>Xin'an Second Edition: Chapter 25 mobile application security requirements analysis and security protection engineering learning notes
Xin'an Second Edition: Chapter 25 mobile application security requirements analysis and security protection engineering learning notes
2022-07-06 17:34:00 【Moon Dream Studio】
Two 、 The outline of this chapter requires
8. Mobile application security requirement analysis and security protection engineering
8.1 Mobile application security threat and demand analysis
● Mobile operating system security analysis ● Security analysis of mobile communication network ● Mobile application App Safety analysis
8.2 Android System security and protection mechanism ● Android System security system
●Android System security mechanism ( Process sandbox isolation mechanism 、SOLite database security 、 Application signature mechanism 、 Permission declaration mechanism 、 Network transmission encryption )
8.3 iOS System security and protection mechanism
● i0S System security system
●iOS System security mechanism ( Safety start chain 、 Permission separation mechanism 、 Code signing mechanism 、DEP、 Address space layout randomization 、 Sandbox mechanism 、 Data encryption and protection mechanism 、 Network transmission encryption )
8.4 Mobile application security protection mechanism and technical scheme
8.4.1 Mobile application App Safety risk
● Reverse engineering risk ● Risk of tampering ● Data theft risk
84.2 Mobile application App Safety reinforcement
● Reverse prevention 、 Anti commissioning 、 tamper-proof ● Data leakage prevention 、 Transmission data protection
8.4.3 Mobile application App Safety inspection
● Identity authentication mechanism detection
● Communication session security mechanism detection ● Sensitive information protection mechanism detection ● Log security policy detection ● Transaction process security mechanism detection ● Server authentication mechanism detection ● Access control mechanism detection ● Data tamper proof capability detection ● prevent SQL Injection capability test ● Anti fishing safety capability test ●App Security vulnerability detection
8.5 Mobile application security comprehensive application case analysis
● Financial mobile security ● Mobile security of operators ● Mobile office security
3、 ... and 、 List of important and easy knowledge points in this chapter
25.1 Mobile application security threat and demand analysis
1. The basic composition of mobile application system based on smart phone includes three parts : First, mobile applications , abbreviation App; The second is the communication network , Including wireless networks 、 Mobile communication network and Internet ; The third is the application server , Composed of related servers , Responsible for handling from App Relevant information or data .
<边栏推荐
- EasyRE WriteUp
- Precipitated database operation class - version C (SQL Server)
- 【逆向】脱壳后修复IAT并关闭ASLR
- mysql的合计/统计函数
- 虚拟机启动提示Probing EDD (edd=off to disable)错误
- C#版Selenium操作Chrome全屏模式显示(F11)
- CTF reverse entry question - dice
- Akamai浅谈风控原理与解决方案
- Concept and basic knowledge of network layering
- Automatic operation and maintenance sharp weapon ansible Foundation
猜你喜欢
Akamai talking about risk control principles and Solutions
Flink源码解读(二):JobGraph源码解读
JVM之垃圾回收器下篇
【ASM】字节码操作 ClassWriter 类介绍与使用

Interpretation of Flink source code (II): Interpretation of jobgraph source code
CTF reverse entry question - dice
1. Introduction to JVM

肖申克的救赎有感
Virtual machine startup prompt probing EDD (edd=off to disable) error
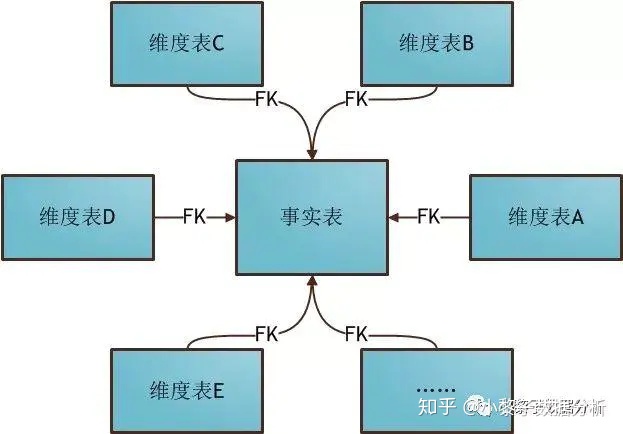
数据仓库建模使用的模型以及分层介绍
随机推荐
Redis quick start
connection reset by peer
自动答题 之 Selenium测试直接运行在浏览器中,就像真正的用户在操作一样。
华为认证云计算HICA
虚拟机启动提示Probing EDD (edd=off to disable)错误
Coursera cannot play video
Take you hand-in-hand to do intensive learning experiments -- knock the level in detail
vscode
JVM garbage collector part 2
Redis快速入门
C WinForm series button easy to use
Akamai talking about risk control principles and Solutions
Wu Jun's trilogy experience (VII) the essence of Commerce
[reverse] repair IAT and close ASLR after shelling
07个人研发的产品及推广-人力资源信息管理系统
Solr appears write Lock, solrexception: could not get leader props in the log
Precipitated database operation class - version C (SQL Server)
EasyRE WriteUp
Vscode matches and replaces the brackets
自动化运维利器ansible基础