当前位置:网站首页>With excellent strength, wangchain technology, together with IBM and Huawei, has entered the annual contribution list of "super ledger"!
With excellent strength, wangchain technology, together with IBM and Huawei, has entered the annual contribution list of "super ledger"!
2022-07-04 07:27:00 【InfoQ】
边栏推荐
- Chapter 1 programming problems
- Unity opens the explorer from the inspector interface, selects and records the file path
- The final week, I split
- There is no Chinese prompt below when inputting text in win10 Microsoft Pinyin input method
- Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
- Zabbix agent主动模式的实现
- 电子协会 C语言 1级 34 、分段函数
- Literature collation and thesis reading methods
- Unity 从Inspector界面打开资源管理器选择并记录文件路径
- tornado项目之路由装饰器
猜你喜欢
Zhanrui tankbang | jointly build, cooperate and win-win zhanrui core ecology

云Redis 有什么用? 云redis怎么用?
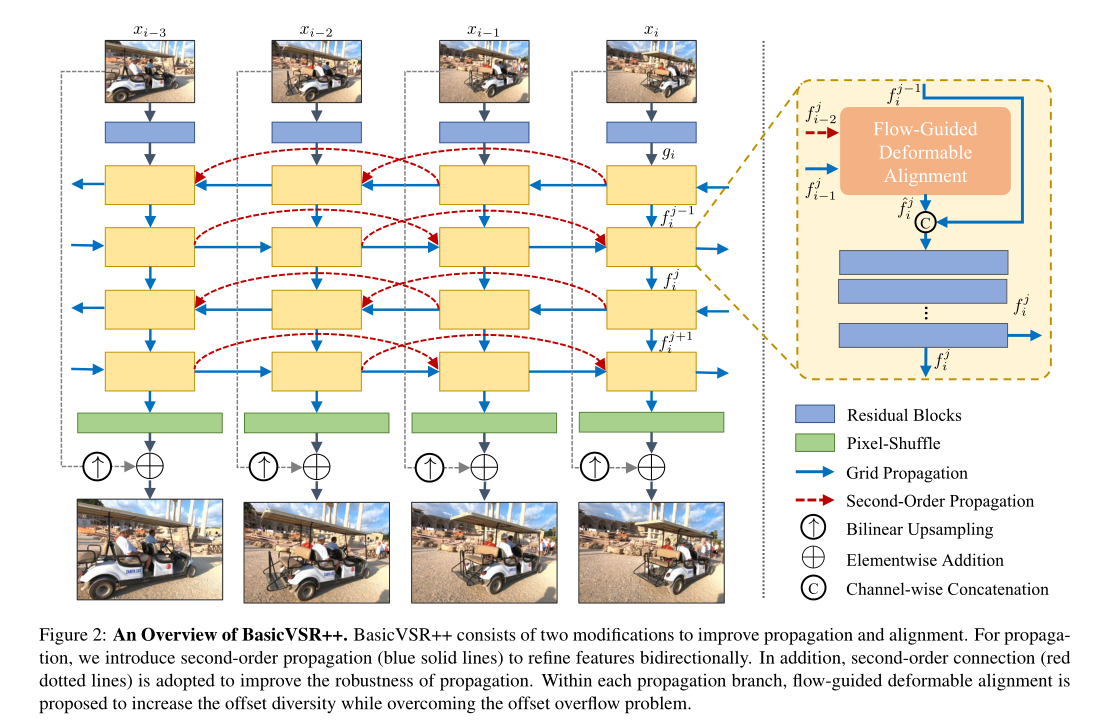
BasicVSR++: Improving Video Super-Resolutionwith Enhanced Propagation and Alignment
![[Mori city] random talk on GIS data (I)](/img/e4/2a2ceb10a2c0285cdd0c922f827930.png)
[Mori city] random talk on GIS data (I)
【森城市】GIS数据漫谈(一)

The most effective futures trend strategy: futures reverse merchandising
Rhcsa day 3

Routing decorator of tornado project
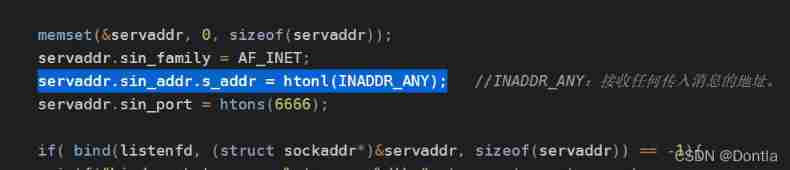
The IP bound to the socket is inaddr_ The meaning of any htonl (inaddr_any) (0.0.0.0 all addresses, uncertain addresses, arbitrary addresses)
CMS source code of multi wechat management system developed based on thinkphp6, with one click curd and other functions
随机推荐
Zephyr Learning note 2, Scheduling
NLP-文献阅读总结
【Kubernetes系列】Kubernetes 上安装 KubeSphere
tornado项目之路由装饰器
Life planning (flag)
[Android reverse] function interception (use cache_flush system function to refresh CPU cache | refresh CPU cache disadvantages | recommended time for function interception)
Distributed transaction management DTM: the little helper behind "buy buy buy"
Bottom problem of figure
[Chongqing Guangdong education] National Open University spring 2019 770 real estate appraisal reference questions
Pangu open source: multi support and promotion, the wave of chip industry
Rhcsa the next day
Flink memory model, network buffer, memory tuning, troubleshooting
MySQL 数据库 - 函数 约束 多表查询 事务
Paddleocr prompt error: can not import AVX core while this file exists: xxx\paddle\fluid\core_ avx
Set JTAG fuc invalid to normal IO port
flask-sqlalchemy 循环引用
Vulhub vulnerability recurrence 76_ XXL-JOB
Guoguo took you to write a linked list, and the primary school students said it was good after reading it
Lottery system test report
[freertos] freertos Learning notes (7) - written freertos bidirectionnel Link LIST / source analysis