当前位置:网站首页>Rhcsa the next day
Rhcsa the next day
2022-07-04 07:11:00 【Where are the peaches】
1. Introduce the difference between soft and hard links
Symbolic links are also called soft links , And the original file is not a file . for example Windows Shortcut to ,
Characteristics of action : Find a file in the specified path and access it quickly and easily , Delete source file shortcut cannot be accessed
Create objects : Text files and directory files can be created , And can cross file systems
Hard links , Multiple filenames point to the same Inode
Characteristics of action : Prevent users from deleting by mistake , Backup ( Backup only for file names )
Create objects : Cannot create for catalog file , And can't cross file systems
2. Create hard and soft link files as required ( stay /home Create the file as aaa, And in / Create a soft link file in the directory a.txt; /root Create a hard link file as )


3. In the current system / Create under directory 100 File ( File name e.g :abc1..abc100)

4. Introduce ll List what each column of information in a directory is

5. Create directory /test/sysroot Create three files in this directory a,b,c After then sysroot Directory move to /tmp Change the name to sys Ensure that the three files in the directory also exist


6 Delete /tmp/sys/a file .

7. Catalog /tmp Create 4 A catalog , And create one under each of these four directories test Catalog

8. Create a test Catalog , Create a file in this directory , Content writing nano

9. stay /dir Create directory under dir2 And documents file1, Moving files file1 To create test Directory , Put the table of contents dir2 Copied to the test Directory 
边栏推荐
- [network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
- 【森城市】GIS数据漫谈(一)
- Selection (021) - what is the output of the following code?
- selenium IDE插件下载安装使用教程
- Label management of kubernetes cluster
- CMS source code of multi wechat management system developed based on thinkphp6, with one click curd and other functions
- Campus network problems
- Tar source code analysis Part 2
- Electronic Association C language level 1 35, bank interest
- 高薪程序员&面试题精讲系列119之Redis如何实现分布式锁?
猜你喜欢
![[Mori city] random talk on GIS data (I)](/img/e4/2a2ceb10a2c0285cdd0c922f827930.png)
[Mori city] random talk on GIS data (I)

Two years ago, the United States was reluctant to sell chips, but now there are mountains of chips begging China for help
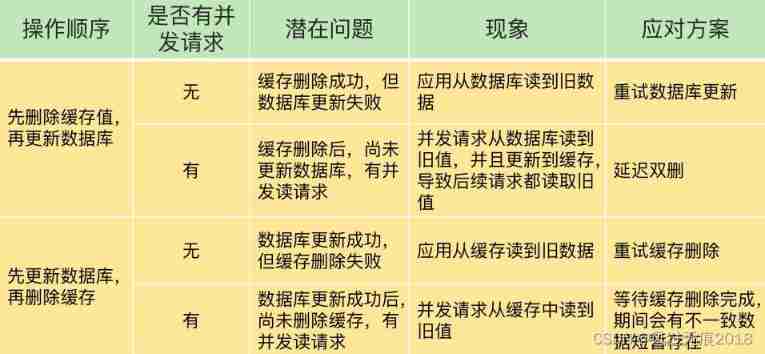
Data double write consistency between redis and MySQL
![[kubernetes series] kubesphere is installed on kubernetes](/img/2b/eb39cf78b3bb9908b01f279e2f9958.png)
[kubernetes series] kubesphere is installed on kubernetes
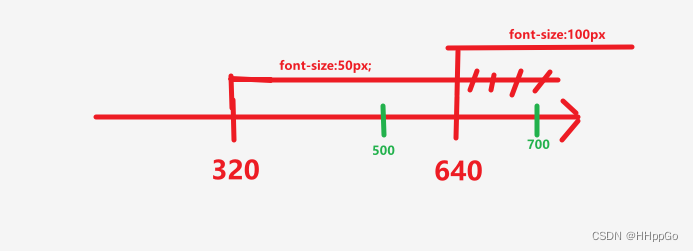
Responsive mobile web test questions
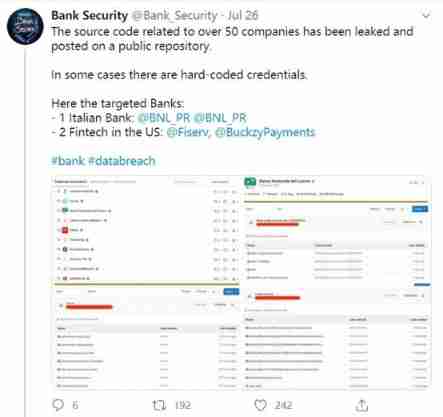
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
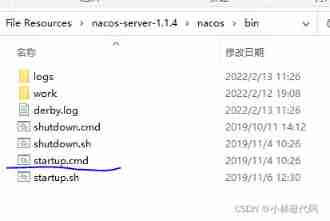
com. alibaba. nacos. api. exception. NacosException

Master-slave replication principle of MySQL database
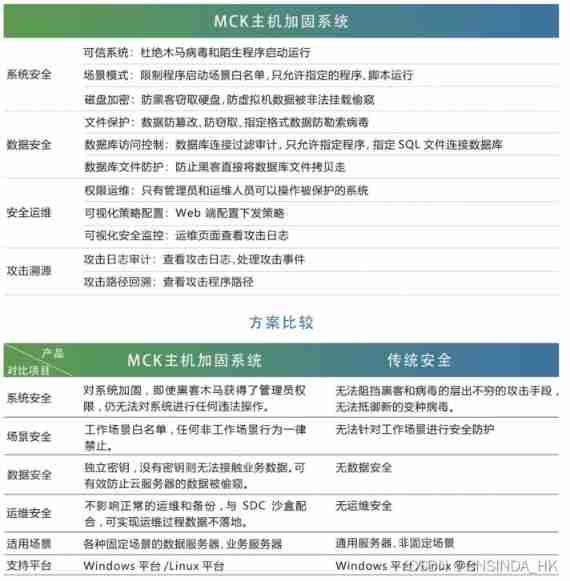
What is industrial computer encryption and how to do it
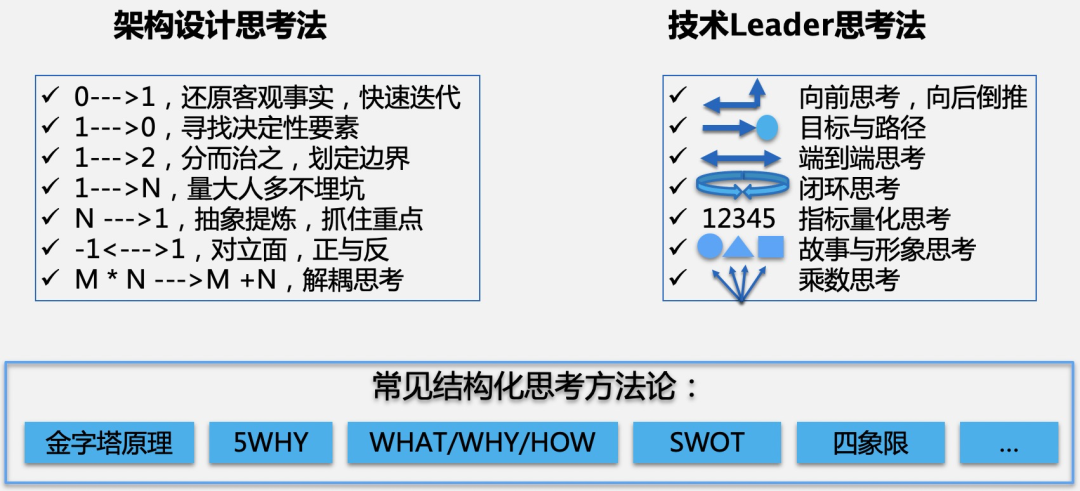
大厂技术专家:架构设计中常用的思维模型
随机推荐
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
There is no Chinese prompt below when inputting text in win10 Microsoft Pinyin input method
Check and display one column in the known table column
大厂技术专家:架构设计中常用的思维模型
MySQL 45 lecture learning notes (XIV) count (*)
A new understanding of how to encrypt industrial computers: host reinforcement application
Cochez une colonne d'affichage dans une colonne de tableau connue
selenium IDE插件下载安装使用教程
How can the old version of commonly used SQL be migrated to the new version?
输入年份、月份,确定天数
A real penetration test
The important role of host reinforcement concept in medical industry
"Sword finger offer" 2nd Edition - force button brush question
Introduction to spark core components
[Android reverse] function interception (use cache_flush system function to refresh CPU cache | refresh CPU cache disadvantages | recommended time for function interception)
Tar source code analysis 6
Vulhub vulnerability recurrence 77_ zabbix
tornado之目录
Download address of the official website of national economic industry classification gb/t 4754-2017
电子协会 C语言 1级 34 、分段函数