当前位置:网站首页>[Android reverse] function interception (use cache_flush system function to refresh CPU cache | refresh CPU cache disadvantages | recommended time for function interception)
[Android reverse] function interception (use cache_flush system function to refresh CPU cache | refresh CPU cache disadvantages | recommended time for function interception)
2022-07-04 07:09:00 【Programmer community】
List of articles
- One 、 Use cache_flush System function refresh CPU Cache
- Two 、 Use cache_flush System function refresh CPU The disadvantages of cache
- 3、 ... and 、 Function intercept recommended timing
One 、 Use cache_flush System function refresh CPU Cache
Use " Add jump code to the actually called function to realize function interception " programme Function interception , Due to the existence CPU Cache mechanism , No guarantee 100% success ;
Here you need to refresh CPU The cache of , call cache_flush System function , Will be CPU All data related to the process in the cache are cleared , Then reload the cache information from memory , At this point, you can put After modification Added jump function Intercepted function , Reload into memory , here CPU You can execute The modified Intercepted function ; Interception effective ;
Two 、 Use cache_flush System function refresh CPU The disadvantages of cache
Use cache_flush System function refresh CPU The disadvantages of cache :
① Performance loss : CPU Rebuild cache , Resulting in reduced execution efficiency , Could cause Caton , Flashback, etc ;
② Affect other processes : Multicore CPU If you refresh Cache , May cause other processes Cache Also refreshed , Affect the execution of other processes ;
③ Affect multithreaded code logic : Multiple threads compete CPU Executive authority , It's empty CPU In cache ,
Multithreaded execution logic Reference resources 【Java Concurrent programming 】 Thread Introduction ( Concurrency type | Thread state | CPU Data caching ) Blog , Java Threads Runtime , Every Java Threads are equipped with a The working memory , Then the working memory starts from Main memory Get data in , Main memory is shared by all working memory ;
- The working memory Namely Thread Local memory , Which is stored in the main memory Copies of variables , Before using variables in main memory , First copy the variable to the working memory ;
- When in a thread Modified the data in working memory , At the same time Synchronize the changes of variables to main memory ;
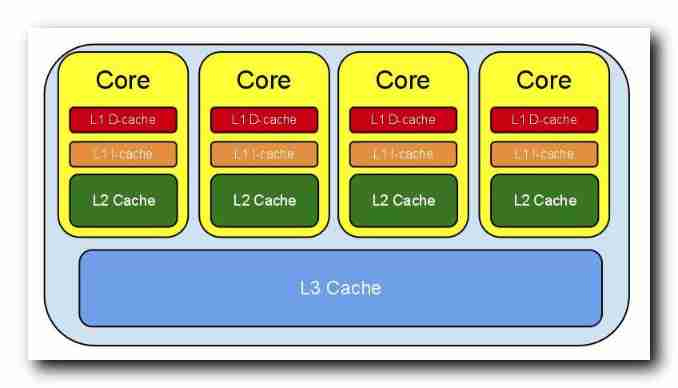
there The worker thread / Local thread amount to CPU Medium L1 / L2 cache , Main memory amount to CPU Medium L3 cache ;
If the cache is cleared , There must be problems with multithreading execution ;
3、 ... and 、 Function intercept recommended timing
Whereas Function interception need Empty CPU Cache There are the above disadvantages , Therefore, it is suggested that Function interception during program initialization , Do not do this while the program is running Function interception ;
If you have to intercept after the program starts , Can only risk Empty CPU Cache , However, it is recommended to intercept all functions at one time , Don't do it frequently Function interception + Empty CPU Cache operation , The more times , The more likely it is to go wrong ;
边栏推荐
- The final week, I split
- Computer connects raspberry pie remotely through putty
- The most effective futures trend strategy: futures reverse merchandising
- Boast about Devops
- tars源码分析之4
- The number of patent applications in China has again surpassed that of the United States and Japan, ranking first in the world for 11 consecutive years
- Tar source code analysis Part 2
- 2022, peut - être la meilleure année économique de la prochaine décennie, avez - vous obtenu votre diplôme en 2022? Comment est - ce prévu après la remise des diplômes?
- Since DMS is upgraded to a new version, my previous SQL is in the old version of DMS. In this case, how can I retrieve my previous SQL?
- About how idea sets up shortcut key sets
猜你喜欢

Boosting the Performance of Video Compression Artifact Reduction with Reference Frame Proposals and
【森城市】GIS数据漫谈(一)

The number of patent applications in China has again surpassed that of the United States and Japan, ranking first in the world for 11 consecutive years

NLP literature reading summary
Responsive mobile web test questions
BasicVSR++: Improving Video Super-Resolutionwith Enhanced Propagation and Alignment
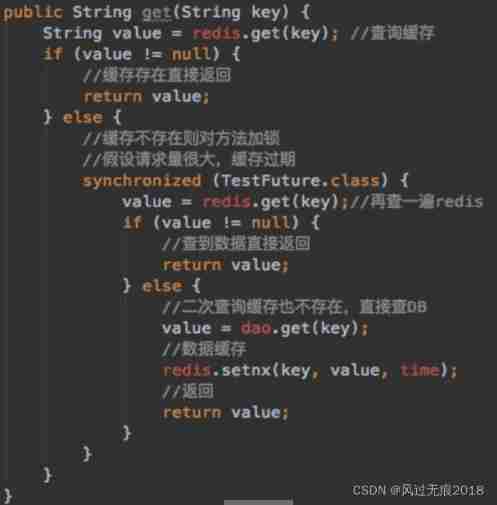
Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
selenium IDE插件下载安装使用教程
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Responsive - media query
随机推荐
Recursive Fusion and Deformable Spatiotemporal Attention for Video Compression Artifact Reduction
MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native
响应式——媒体查询
Tar source code analysis Part 7
Electronic Association C language level 1 35, bank interest
由于dms升级为了新版,我之前的sql在老版本的dms中,这种情况下,如何找回我之前的sql呢?
[FPGA tutorial case 7] design and implementation of counter based on Verilog
How does the recv of TCP socket receive messages of specified length?
Pangu open source: multi support and promotion, the wave of chip industry
Splicing plain text into JSON strings - easy language method
A new understanding of how to encrypt industrial computers: host reinforcement application
[MySQL transaction]
centos8安装mysql.7 无法开机启动
[network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
Tar source code analysis Part 3
If there are two sources in the same job, it will be reported that one of the databases cannot be found. Is there a boss to answer
MySQL 45 lecture learning notes (XIV) count (*)
js 常用时间处理函数
leetcode825. Age appropriate friends