当前位置:网站首页>How to buy financial products in 2022?
How to buy financial products in 2022?
2022-07-04 07:07:00 【Koufu Q & A】
Take the answer 1:
Take the answer 2:
If you have other questions about financial management, please contact me . Our listed securities firm , Open an account with me and enjoy the ultra-low Commission in the industry ,24 It's convenient and fast to open an account anytime, anywhere within hours
边栏推荐
- [MySQL transaction]
- Tar source code analysis Part 10
- "Sword finger offer" 2nd Edition - force button brush question
- 2022年,或许是未来10年经济最好的一年,2022年你毕业了吗?毕业后是怎么计划的?
- Mysql 45讲学习笔记(六)全局锁
- The most effective futures trend strategy: futures reverse merchandising
- 用于压缩视频感知增强的多目标网络自适应时空融合
- 【FPGA教程案例8】基于verilog的分频器设计与实现
- Tar source code analysis 9
- Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc
猜你喜欢
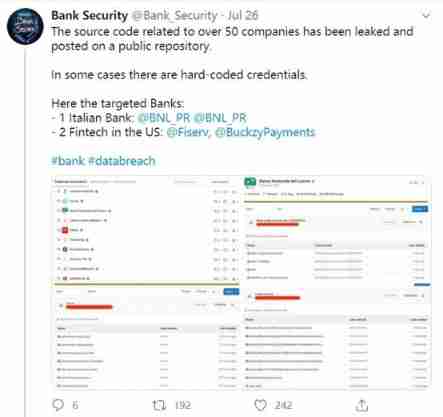
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
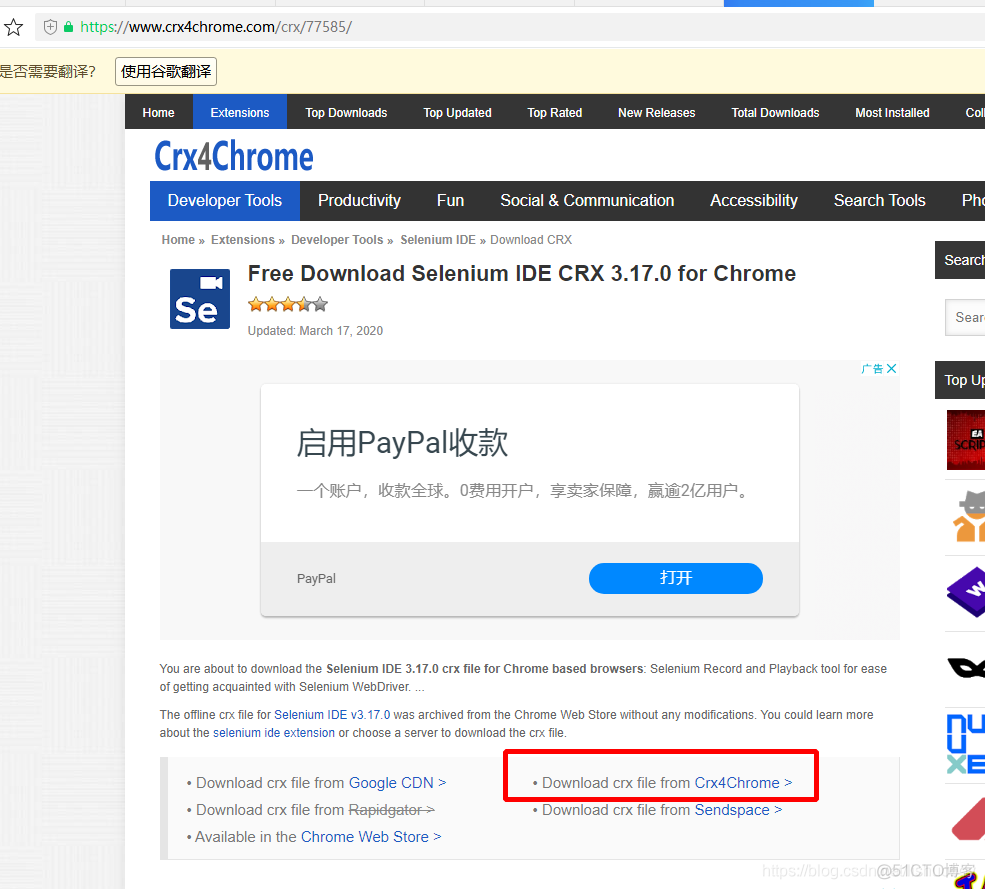
selenium IDE插件下载安装使用教程
Knowledge payment applet dream vending machine V2
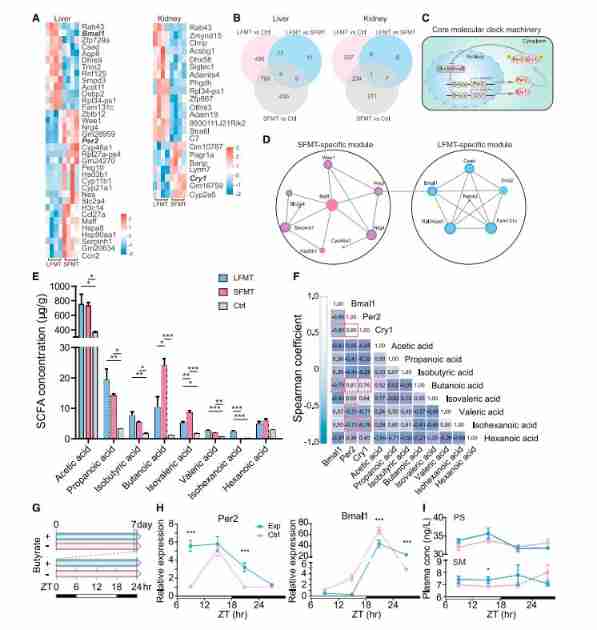
Cell reports: Wei Fuwen group of the Institute of zoology, Chinese Academy of Sciences analyzes the function of seasonal changes in the intestinal flora of giant pandas
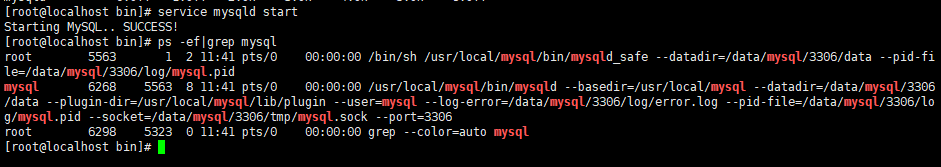
Centos8 install mysql 7 unable to start up
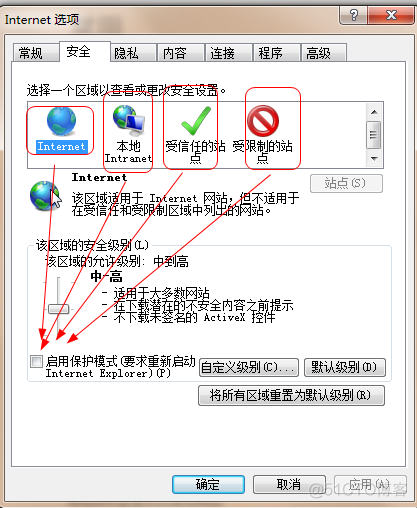
Selenium driver ie common problem solving message: currently focused window has been closed
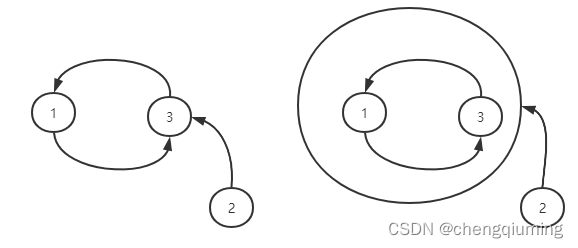
Bottom problem of figure
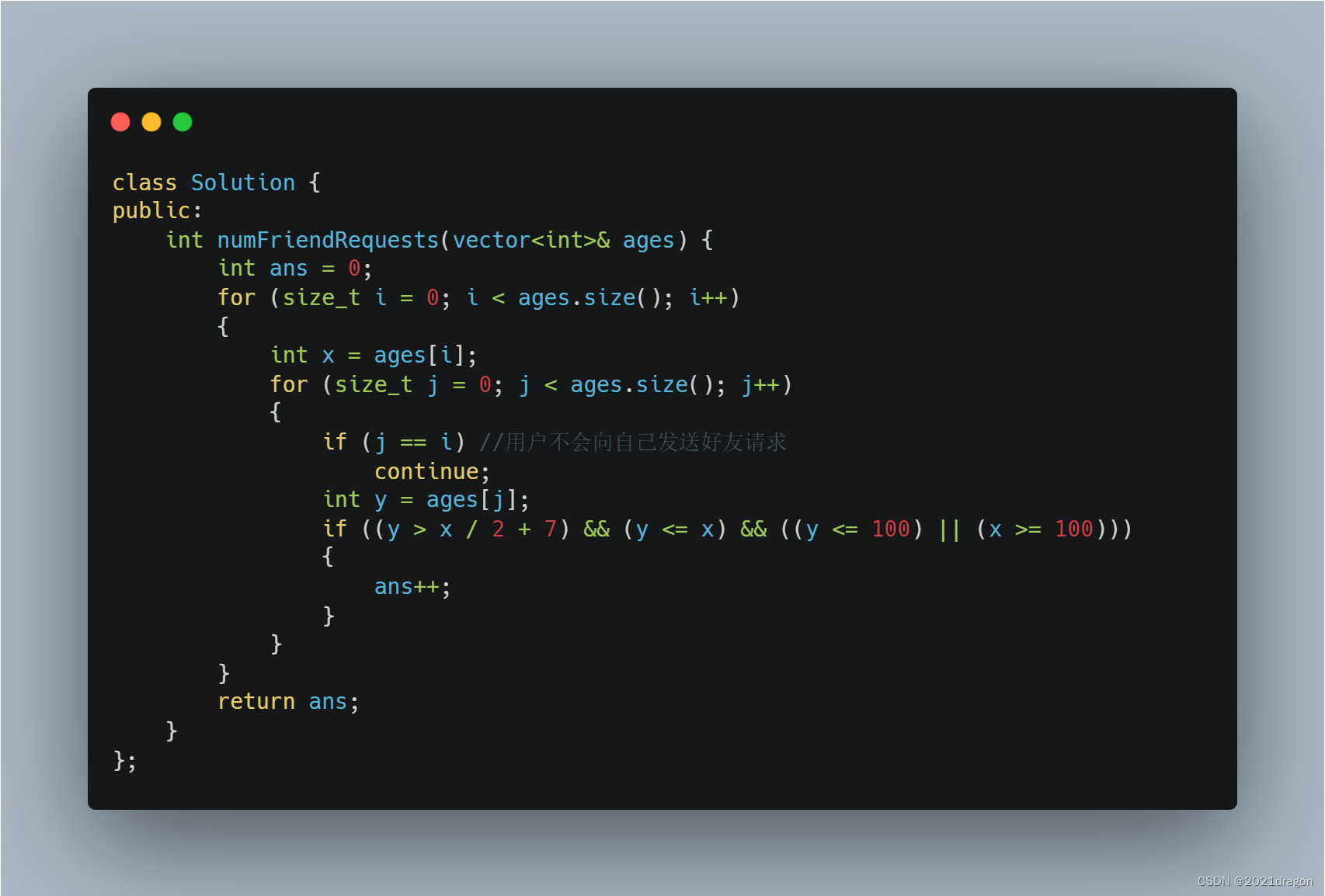
leetcode825. Age appropriate friends
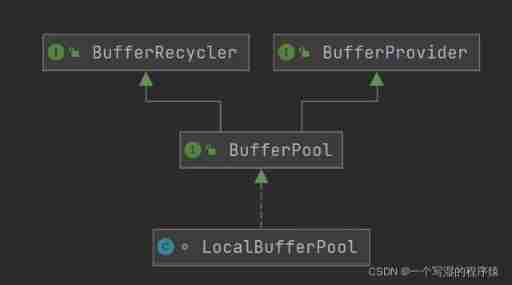
Flink memory model, network buffer, memory tuning, troubleshooting
Campus network problems
随机推荐
Download address of the official website of national economic industry classification gb/t 4754-2017
Novel website program source code that can be automatically collected
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
Selenium ide plug-in download, installation and use tutorial
tars源码分析之6
Responsive mobile web test questions
"Sword finger offer" 2nd Edition - force button brush question
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
tars源码分析之9
tars源码分析之2
Mysql 45讲学习笔记(七)行锁
Label management of kubernetes cluster
Tar source code analysis 4
Check and display one column in the known table column
Mysql 45讲学习笔记(六)全局锁
win10微软拼音输入法输入文字时候下方不出现中文提示
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
Paddleocr prompt error: can not import AVX core while this file exists: xxx\paddle\fluid\core_ avx
Uniapp applet subcontracting
Analysis of tars source code 5