当前位置:网站首页>Industrial computer anti-virus
Industrial computer anti-virus
2022-07-04 06:50:00 【CNSINDA_ HK】
One 、 Overview of industrial control safety
Want to know about industrial control safety , First, understand the asset object itself , That is, industrial control system .
1、 What is industrial control
About the definition of industrial control system , There are many on the Internet , I won't go back to , The following picture is from csdn Found , I think it's pretty good . Refer to the definition of industrial control , Can help you have a better understanding .
2、 The impact of industrial control safety
There are many cases about industrial control safety , Recent examples are 2019 year 3 month , Most parts of Venezuela are without power , The national transportation system is paralyzed , The subway system is shut down , Mass disruption of communication .2019 year 7 month , The Iranian information Corps broke into the United States 30 Control centers for multiple substations , It led to a massive blackout in New York 4 Hours , Cause large-scale chaos, etc . One of the most famous 、 The most influential is 2010 year 6 month , The Iranian nuclear power plant suffered “ Seismic net ” Virus attack . There was once a film in China “ Seismic net ” A movie based on events , named 《 Hackers fight 》, Starring Wang Leehom and Tang Wei , Those who are interested can go and have a look , You can have a more intuitive understanding of industrial control safety .
The pain point of the industrial computer is that it is not connected to the Internet , The operating system cannot be patched , Virus library cannot be updated , Ordinary anti-virus software is useless ; Because it is a special equipment , The user's NMS dare not install anti-virus software on it ; Is there a virus in the system , The production line is interrupted , Great loss .
Personal suggestion is to use the way of host reinforcement to strengthen the industrial computer , To resist the virus
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
Which host reinforcement brands are worth recommending :
At present, several brands that have done well in the field of host reinforcement are known in the market :
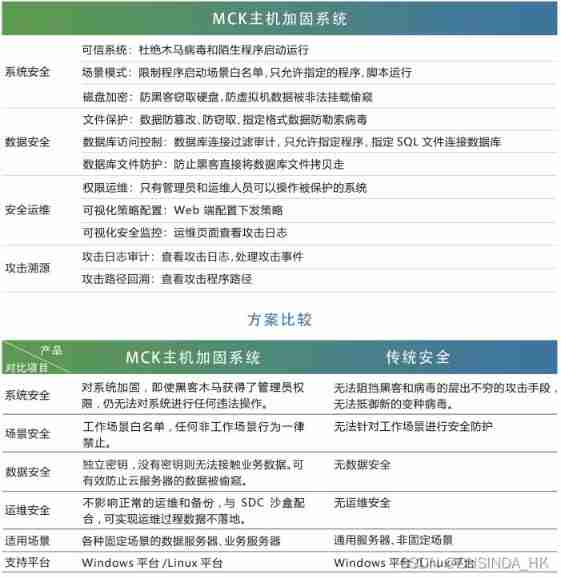
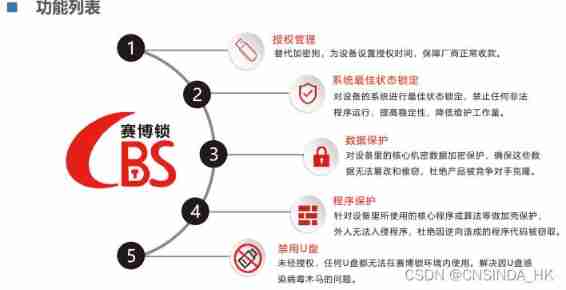
1、 Xinda's MCK Host reinforcement and CBS Sebo lock .
2、 Wisteria cloud security .
3、 Luoan Technology .
4、 wave .
5、 Anheng .
6、 Convinced .
7、 Tian Rong Xin .
In no particular order . Personal recommendations MCK Mainframe reinforcement +CBS Plan , Because what our company buys is MCK Mainframe reinforcement +CBS. It is said that their sandbox encryption is also an old brand in the industry , You can rely on .
边栏推荐
- leetcode825. 适龄的朋友
- 24 magicaccessorimpl can access the debugging of all methods
- What is the "relative dilemma" in cognitive fallacy?
- 2022 is probably the best year for the economy in the next 10 years. Did you graduate in 2022? What is the plan after graduation?
- 【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
- 响应式移动Web测试题
- Centos8 install mysql 7 unable to start up
- [FPGA tutorial case 7] design and implementation of counter based on Verilog
- [network data transmission] FPGA based development of 100M / Gigabit UDP packet sending and receiving system, PC to FPGA
- tars源码分析之5
猜你喜欢
notepad++如何统计单词数量
![[backpack DP] backpack problem](/img/7e/1ead6fd0ab61806ce971e1612b4ed6.jpg)
[backpack DP] backpack problem
Tree DP
Variables d'environnement personnalisées uniapp

The cloud native programming challenge ended, and Alibaba cloud launched the first white paper on application liveliness technology in the field of cloud native

Cervical vertebra, beriberi
R statistical mapping - random forest classification analysis and species abundance difference test combination diagram

what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!

what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
图的底部问题
随机推荐
uniapp 自定義環境變量
24 magicaccessorimpl can access the debugging of all methods
what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!
Download address of the official website of national economic industry classification gb/t 4754-2017
内卷怎么破?
leetcode825. 适龄的朋友
Another company raised the price of SAIC Roewe new energy products from March 1
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
云Redis 有什么用? 云redis怎么用?
Appium基础 — APPium安装(二)
How does the inner roll break?
校园网络问题
Which water in the environment needs water quality monitoring
【FPGA教程案例7】基于verilog的计数器设计与实现
Explain in one sentence what social proof is
leetcode 310. Minimum Height Trees
If there are two sources in the same job, it will be reported that one of the databases cannot be found. Is there a boss to answer
测试用例的设计
tars源码分析之9
List of top ten professional skills required for data science work