当前位置:网站首页>User datagram protocol UDP
User datagram protocol UDP
2022-07-06 03:56:00 【Pupu pupu】
Author: intellectuals
Computer science
Controllable things Heavy and calm Uncontrollable things Optimistic face
[email protected]
️
️ ️ ️
————————————————
Copyright notice : This paper is about CSDN Blogger 「 Pu Shangqing sky 」 The original article of
List of articles
Knowledge point
UDP brief introduction
Content
- UDP yes OSI A connectionless transport layer protocol in the reference model , It is mainly used in the transmission which does not require the packet to arrive in sequence , The checking and sorting of packet transmission order is completed by the application layer , Provide simple and unreliable transaction oriented information transfer services .UDP The agreement is basically IP The interface between protocol and upper protocol . A process can have multiple port numbers ( The port number and Socket Object association , There can be more than one... In a process Socket object ), But a port number can only correspond to one process ( There are special cases )
- UDP Provide connectionless communication , And there is no reliability guarantee for the transmission of data packets , Suitable for transmitting a small amount of data at a time ,UDP The application layer is responsible for the reliability of the transmission . frequently-used UDP Port number :53(DNS),69(TFTP),161(SNMP), Use UDP The agreement includes :TFTP,SNMP,NFS,DNS,BOOTP.
- UDP The message has no reliability guarantee , Sequence assurance , Flow control fields, etc , Poor reliability , But because of UDP Protocol has fewer control options , Small delay in data transmission , High data transmission efficiency , Suitable for applications with low reliability requirements , Or applications that can guarantee reliability , Such as DNS,TFTP,SNMP.
- Many applications only support DUP, Such as : Multimedia data stream , No additional data will be generated , Don't resend even if you know that there are broken packets . When transmission performance is emphasized instead of transmission integrity , Such as : Audio and multimedia applications ,UDP Is the best choice . When the data transmission time is very short , So that the previous connection process becomes the main body of the whole flow ,UDP It's also a good choice
Actual application site
- In the choice UDP As a transport protocol, we must be careful , In a very unsatisfactory network quality environment ,UDP Protocol packets will be lost seriously , But because of UDP Characteristics of : It belongs to connectionless protocol , Therefore, the consumption of resources is small , The advantage of fast processing speed , So usually audio , Video and ordinary data are used in transmission UDP More , Because even if they occasionally lose oneortwo packets , It will not have too much impact on the acceptance results , For example, we chat with QQ It is used UDP agreement
- In the field of field measurement and control , For distributed controllers , Detector, etc , Its application environment is relatively harsh , In this way, different requirements are put forward for earth ah transmission data , Such as real-time , Anti interference , Safety and so on . Based on this , In field communication , If an application wants to transmit a set of data to another node in the network , May by UDP The process adds a header to the data and sends it to IP process ,UDP The protocol eliminates the process of establishing and dismantling connections and cancels the retransmission inspection mechanism , It can reach a relatively high communication rate
Message format

- UDP The newspaper is headed by 4 Domains make up , Each of these domains accounts for 2 Bytes , Specific include : Source port number , Destination port number , Datagram length , Check value
Port number
- The party sending the data ( It can be client or server ) take UDP Packets are sent through the source port , The data receiving party receives data through the target port . Some network applications can only use static ports reserved or registered in advance ; Other network applications can use unregistered dynamic ports . because UDP The header uses two bytes to store the port number , So the valid range of port number 0-65535
- Division of port number
0-1023 Well known port number ,HTTP,FTP,SSH These widely used application layer protocols , Their port numbers are fixed
1024-65535: Port number dynamically assigned by the operating system , The port number of the client is assigned by the operating system from this range
- Well known port number
SSH The server :22 port
FTP The server :21 port
TELNET The server :23 port
HTTP The server :80 port
HTTPS The server :443 port
length
- Datagram length refers to the total number of words and bytes including header and data part . Because the header length is fixed , Therefore, this field is mainly used to calculate the variable length data part ( Also known as data load ). The maximum length of datagram varies according to the operating environment . In theory , The maximum length of datagram including header is 65535 byte . however , Some practical applications often limit the size of datagrams , Sometimes it will be reduced to 8192 byte
- So there's a problem ,UDP There is one in the first part of the agreement 2 Maximum length of bits , That is to say a UDP The maximum length of data that can be transmitted is (65535 byte ) about 64K( contain UDP The first one ), However 64K In today's Internet Environment , It's a very small number , If we need to transmit more data than 64K, You need to manually subcontract at the application layer , Send... Multiple times , And manually assemble at the receiving end , And manual disassembly and assembly will have great BUG risk , This has to be used TCP transmission
Check value
- UDP The protocol uses the check value in the header to ensure the security of data . The check value is first calculated by a special algorithm at the data sender , After delivery to the receiver , You need to recalculate . If a datagram is tampered with by a third party or damaged due to line noise during retransmission , The verification value calculation of the sender and the receiver does not match , thus UDP The protocol can check for errors
- Introduce a common check value MD5
Its characteristic is
1. No matter how long the data is , Got MD5 It's a fixed length
2. Calculated from data MD5 Value is very convenient and simple , But by MD5 It is almost impossible to push back data
3. Even if the data is changed a little ,MD5 The value of will change greatly
UDP The main features
There is no connection
- UDP It's a connectionless protocol , Before transmitting data , No connection is established between the source end and the terminal , When it wants to transmit , Simply grab the data from the application , And throw it on the Internet as soon as possible . At the sending end ,UDP The speed of data transmission is only the speed generated by the application , The capacity of the computer and the limitation of the transmission bandwidth ; At the receiving end ,UDP Put each message in the queue , The application reads one message segment at a time from the queue
- Because the transmission data does not establish a connection , So there is no need to maintain the connection state , Including sending and receiving status, etc , Therefore, a server can transmit the same message to multiple airliners at the same time
unreliable
- There is no confirmation mechanism , There is no retransmission mechanism , If it's due to a network failure , It will cause that the paragraph cannot be sent to the other party , Of course UDP The protocol layer will not return any error information to the application layer
- although UDP It's an unreliable agreement , But it's an ideal protocol for distributing information . for example , Report the stock market on the screen , Display aviation information, etc .UDP Also used for routing information RIP Modify the routing table in . In these applications , If a message is lost , In a few seconds, another new message will replace it .UDP Widely used in multimedia applications
For datagram
- UDP It's message oriented .
- Application layer to UDP Message of ,UDP After adding the first part, it will be delivered to the lower layer . Neither split , It doesn't merge , But keep the boundaries of these messages , therefore , The application needs to select the appropriate message size
- for example : The sender calls once sendto, send out 100 Bytes , Then the receiver must also call the corresponding one recvfrom, Accept 100 Bytes , Instead of calling in cycles 10 Time recvfrom, Each acceptance 10 Bytes
- UDP The buffer .
- UDP In the true sense of the United States and Europe Send buffer , call sendto Will be handed over directly to the kernel , The kernel transmits the data to the network layer protocol , Carry out subsequent transmission actions
- UDP have Accept buffer But this accept buffer does not guarantee the received UDP The order and delivery of the newspaper UDP The order of reporting is the same , If the buffer is full , Arrive again UDP The data will be discarded . therefore ,UDP Of socket Can read , Can also write , This is full duplex .
Praise first and then watch , Develop habits !!!^ _ ^
Update your knowledge every day !!!
It's not easy to code words , Everyone's support is my driving force to stick to it . Don't forget after you like Focus on I oh !
边栏推荐
- Ybtoj coloring plan [tree chain dissection, segment tree, tarjan]
- 2.2 STM32 GPIO operation
- MySQL master-slave replication
- Microkernel structure understanding
- MySQL 中的数据类型介绍
- JS Vanke banner rotation chart JS special effect
- 自动化测试的好处
- Network security - Security Service Engineer - detailed summary of skill manual (it is recommended to learn and collect)
- Security xxE vulnerability recurrence (XXe Lab)
- [meisai] meisai thesis reference template
猜你喜欢
Record the pit of NETCORE's memory surge
2.13 weekly report
ESP32_ FreeRTOS_ Arduino_ 1_ Create task
How to modify field constraints (type, default, null, etc.) in a table
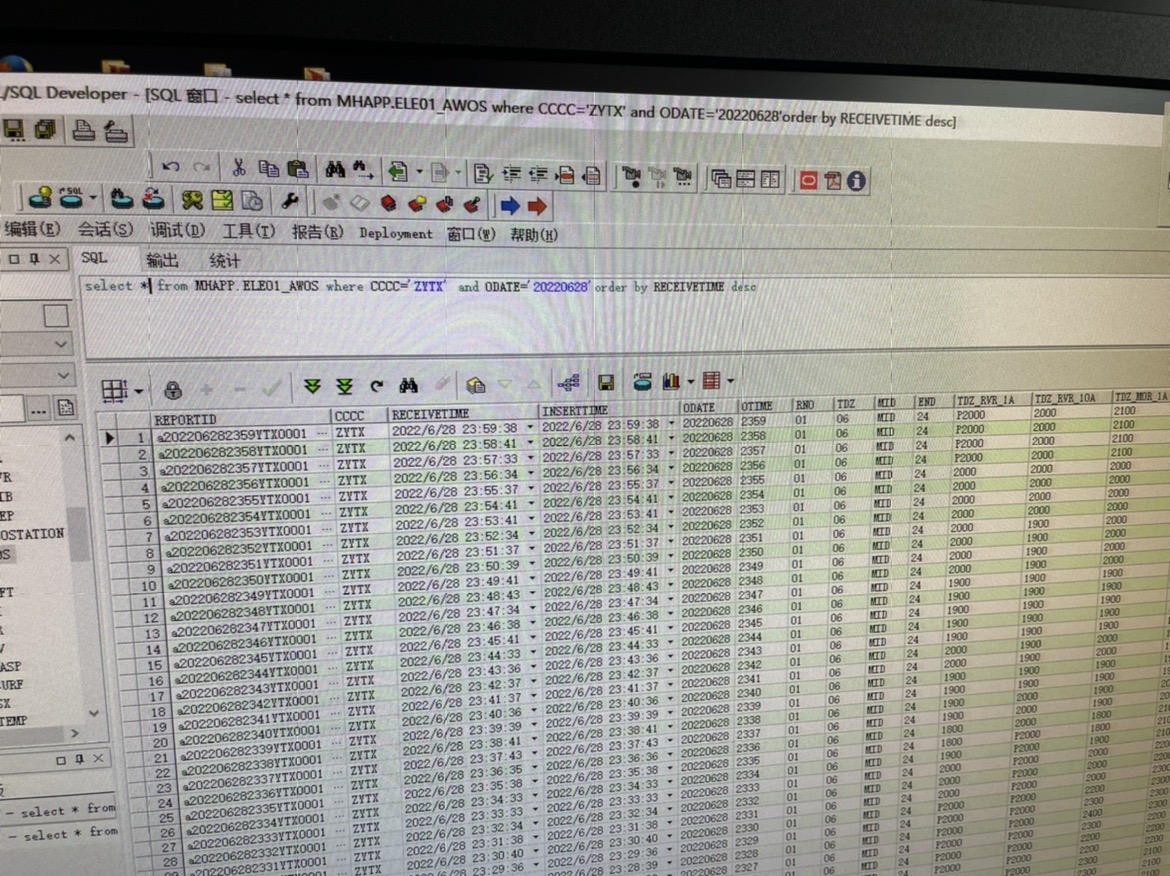
mysql从一个连续时间段的表中读取缺少数据
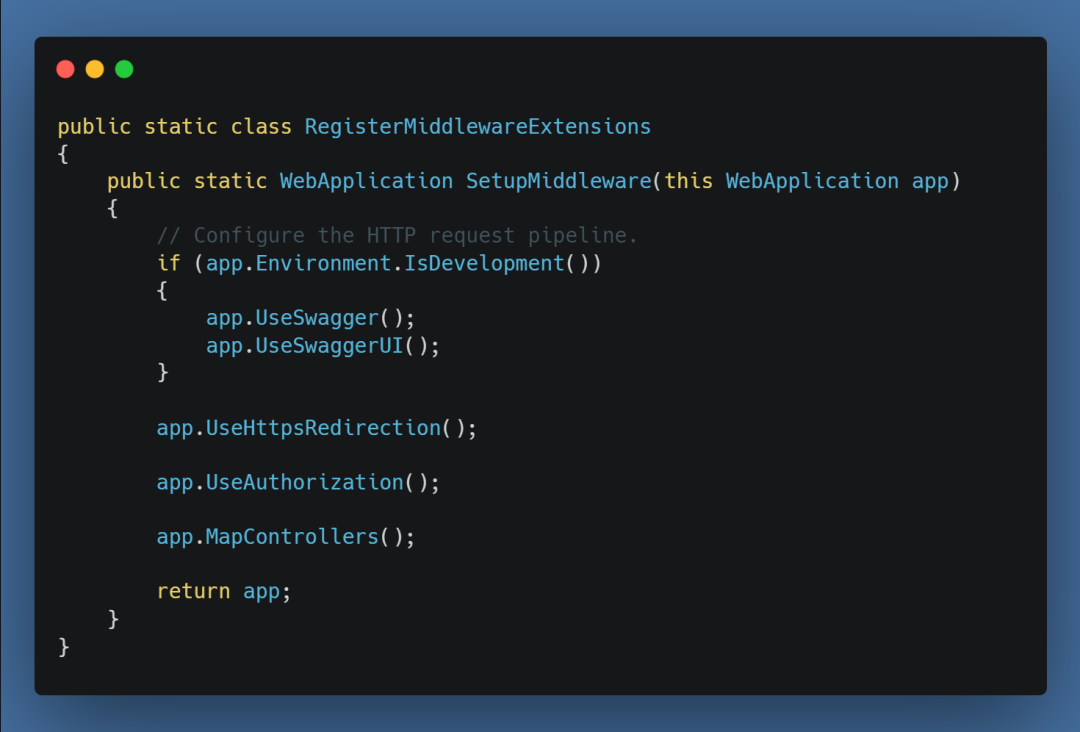
在 .NET 6 中使用 Startup.cs 更简洁的方法
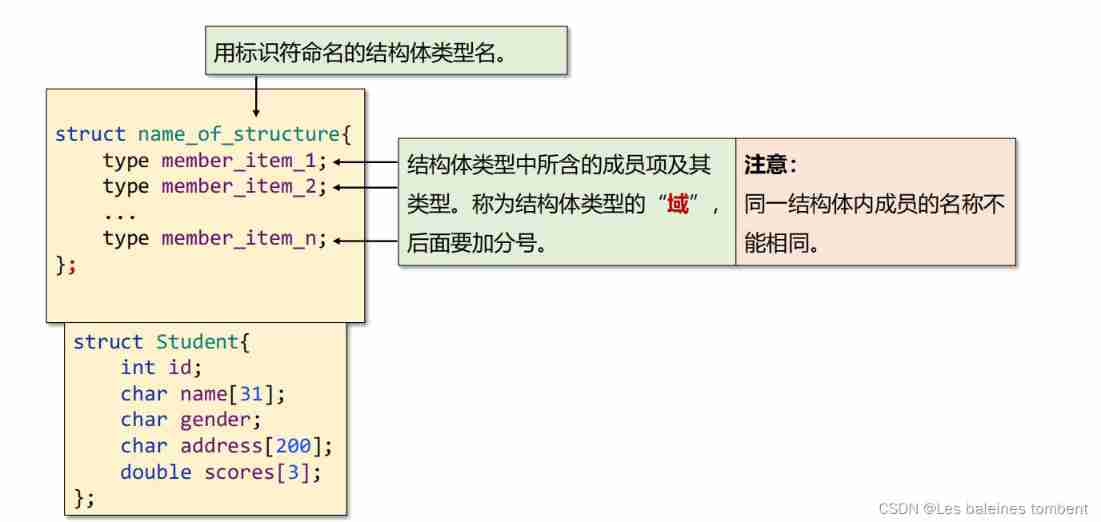
C language -- structs, unions, enumerations, and custom types
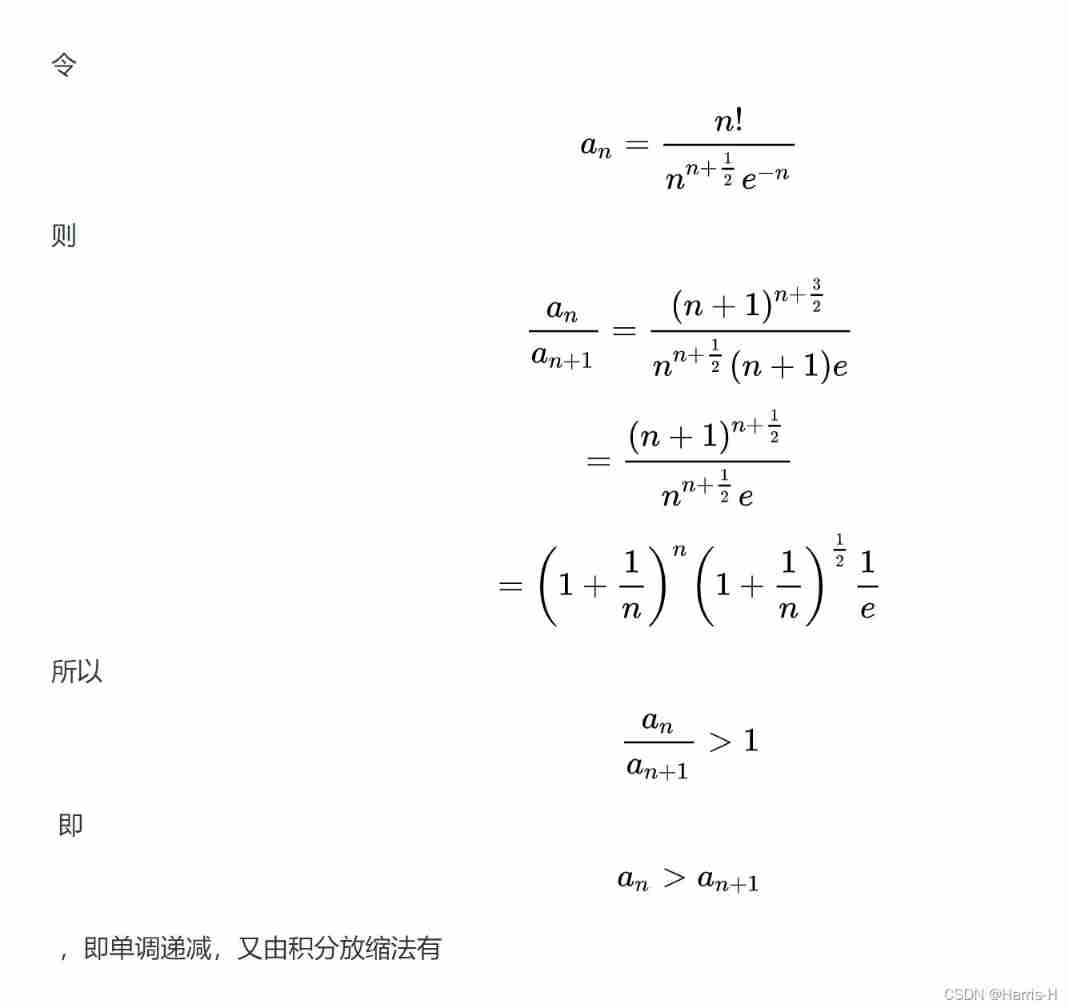
Proof of Stirling formula

Database, relational database and NoSQL non relational database
Thread sleep, thread sleep application scenarios
随机推荐
Microkernel structure understanding
【FPGA教程案例12】基于vivado核的复数乘法器设计与实现
Use js to complete an LRU cache
Do you know cookies, sessions, tokens?
WPF effect Article 191 box selection listbox
Remote Sensing Image Super-resolution and Object Detection: Benchmark and State of the Art
On Data Mining
User experience index system
Pandora IOT development board learning (HAL Library) - Experiment 9 PWM output experiment (learning notes)
mysql关于自增长增长问题
[practice] mathematics in lottery
[matlab] - draw a five-star red flag
math_极限&微分&导数&微商/对数函数的导函数推导(导数定义极限法)/指数函数求导公式推导(反函数求导法则/对数求导法)
[optimization model] Monte Carlo method of optimization calculation
Schnuka: what is visual positioning system and how to position it
C (XXIX) C listbox CheckedListBox Imagelist
BUAA calculator (expression calculation - expression tree implementation)
有条件地 [JsonIgnore]
Pytoch foundation - (2) mathematical operation of tensor
asp. Core is compatible with both JWT authentication and cookies authentication