当前位置:网站首页>Three stage operations in the attack and defense drill of the blue team
Three stage operations in the attack and defense drill of the blue team
2022-07-04 22:44:00 【InfoQ】
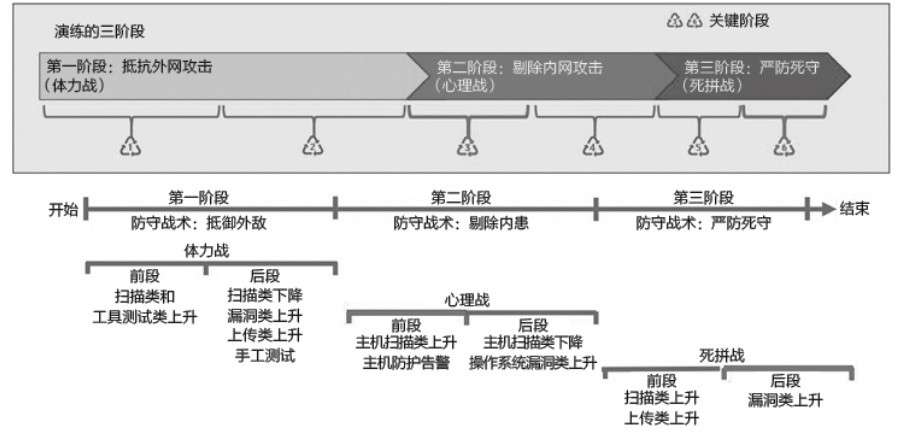
One 、 Physical warfare
Two 、 Psychological warfare
3、 ... and 、 Fight hard
边栏推荐
- 攻防世界 MISC 进阶区 Erik-Baleog-and-Olaf
- 2022-07-04:以下go语言代码输出什么?A:true;B:false;C:编译错误。 package main import “fmt“ func main() { fmt.Pri
- Close system call analysis - Performance Optimization
- Concurrent optimization summary
- 测试必会:BUG的分类及推进解决
- Gnawing down the big bone - sorting (II)
- Shell script implements application service log warehousing MySQL
- Recommendation of mobile app for making barcode
- Unity vscode emmylua configuration error resolution
- NFT Insider #64:电商巨头eBay提交NFT相关商标申请,毕马威将在Web3和元宇宙中投入3000万美元
猜你喜欢
攻防世界 MISC 高手进阶区 001 normal_png
Locust performance test - environment construction and use
安装人大金仓数据库
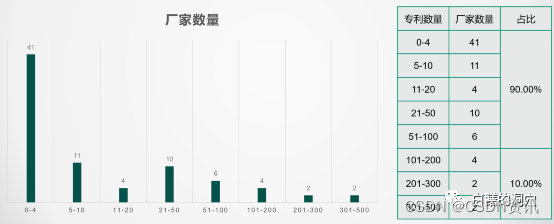
Domestic database chaos
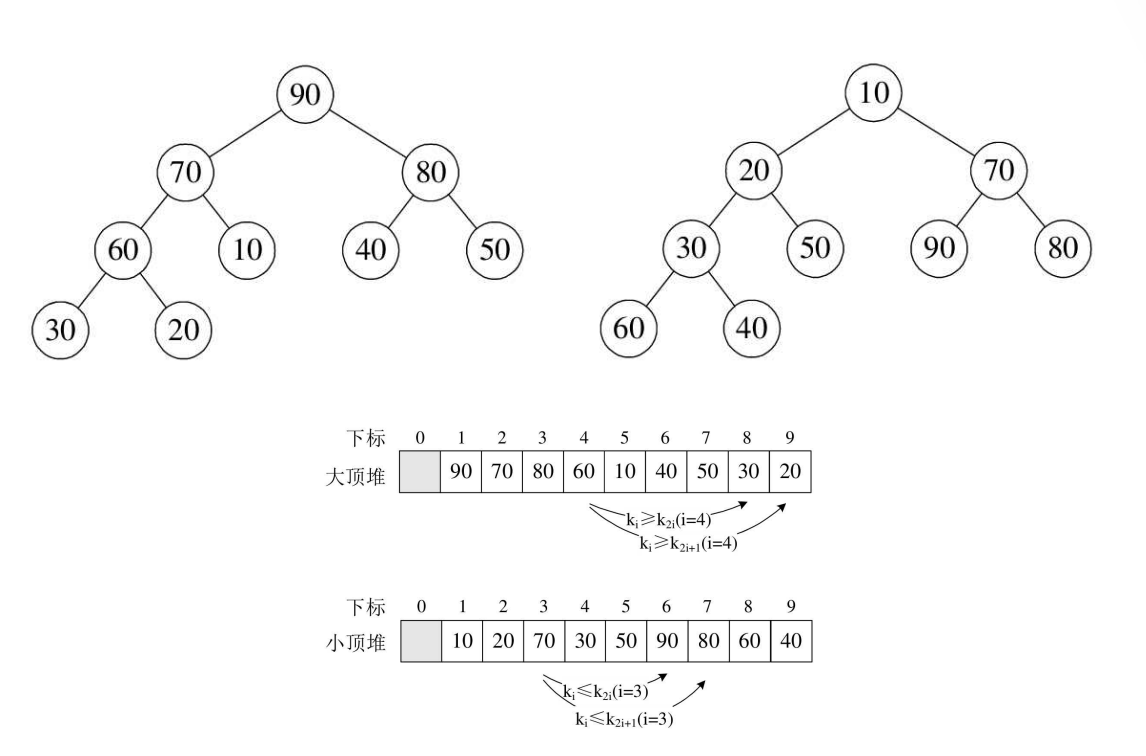
Detailed explanation of heap sort code
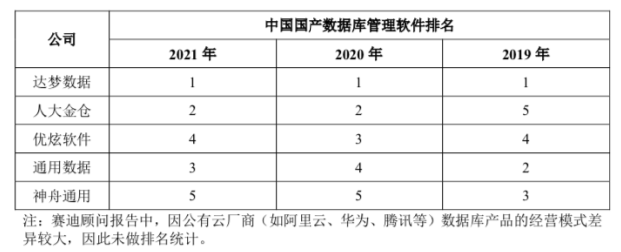
达梦数据凭什么被称为国产数据库“第一股”?
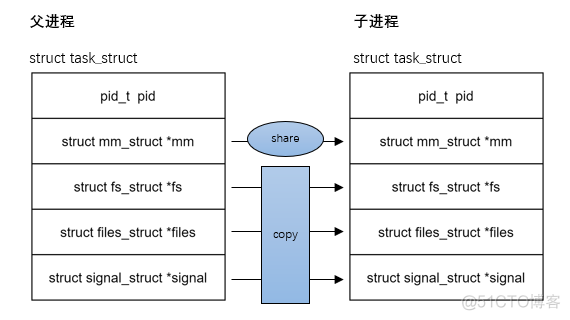
Close system call analysis - Performance Optimization
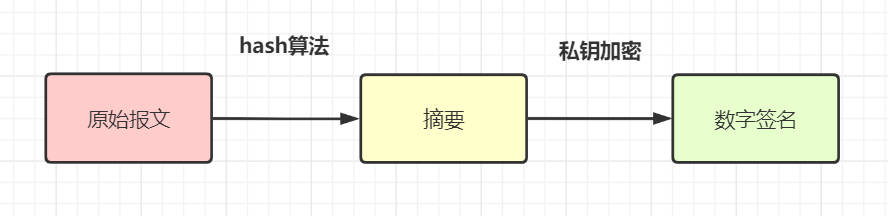
10 schemes to ensure interface data security
![[acwing] solution of the 58th weekly match](/img/e3/fd2c0ffbc9c7ca8a71875882d6c71b.png)
[acwing] solution of the 58th weekly match

Concurrent network modular reading notes transfer
随机推荐
攻防世界 MISC 进阶区 Erik-Baleog-and-Olaf
NFT Insider #64:电商巨头eBay提交NFT相关商标申请,毕马威将在Web3和元宇宙中投入3000万美元
Google Earth Engine(GEE)——Tasks升级,实现RUN ALL可以一键下载任务类型中的所有影像
记录:关于Win10系统中Microsoft Edge上的网页如何滚动截屏?
Attack and defense world misc advanced grace-50
NFT insider 64: e-commerce giant eBay submitted an NFT related trademark application, and KPMG will invest $30million in Web3 and metauniverse
LOGO特训营 第一节 鉴别Logo与Logo设计思路
Attack and defense world misc advanced zone 2017_ Dating_ in_ Singapore
md5工具类
PostgreSQL server programming aggregation and grouping
Introduction and application of bigfilter global transaction anti duplication component
新版判断PC和手机端代码,手机端跳转手机端,PC跳转PC端最新有效代码
Prosperity is exhausted, things are right and people are wrong: where should personal webmasters go
攻防世界 MISC 進階區 Erik-Baleog-and-Olaf
[Lua] Int64 support
集群的概述与定义,一看就会
LOGO special training camp section I identification logo and Logo Design Ideas
Attack and Defense World MISC Advanced Area Erik baleog and Olaf
[cooking record] - stir fried 1000 pieces of green pepper
30余家机构联合发起数字藏品行业倡议,未来会如何前进?