当前位置:网站首页>App compliance
App compliance
2022-07-03 20:04:00 【weixin_ forty-five million eight hundred and seventy-nine thous】
Security testing _ The test case | |||||||||||
Use case number | modular | Subfunction | Use case title | Test priority | label | precondition | testing procedure | Expected results | test result | Defect level | The actual result |
1 | Privacy policy / User's Manual ( Whether the user agreement needs PM Mail confirmation ) | register | The privacy policy pop-up succeeded when verifying registration | P1 | Security testing - Safety compliance | Successfully installed APP | 1. Enter the login registration guide page 2. Click the register button | 1. A pop-up window prompts users to read the privacy policy | |||
2 | Verification privacy policy does not agree, unable to enter the registration | P2 | Security testing - Safety compliance | 1. Enter the login registration guide page 2. Click the register button 3. Click disagree | 1. Keep it on the login registration guide page , Will not enter the registration page | ||||||
3 | Verify the privacy policy and agree to enter the registration page successfully | P2 | Security testing - Safety compliance | 1. Enter the login registration guide page 2. Click the register button 3. Click agree | 1. Enter the registration page | ||||||
4 | If consent is not checked on the verification registration page, registration cannot be completed | P2 | Security testing - Safety compliance | You have entered the registration page | 1. Remove the check box for agreeing to the privacy policy 2. Continue with registration | 1. Unable to click to go to the next step | |||||
5 | Check "agree to complete registration" on the verification registration page | P2 | Security testing - Safety compliance | 1. Check "agree to privacy policy" 2. Continue with registration | 1. Click to enter the next registration step | ||||||
6 | land | Verify that the login privacy policy reading prompt is successful | P1 | Security testing - Safety compliance | On the login registration guide page | 1. Click login 2. Go to the landing page | 1. Click to login without pop-up ( If there is a pop-up window, it is also ok ) 2. To enter the login page, you need to manually check the agree privacy policy ( Foreign countries can directly take the hook , In China, you need to manually check ) | ||||
7 | The login cannot be completed without checking "agree" on the verification login page | P2 | Security testing - Safety compliance | Has entered the landing page | 1. Remove the check box for agreeing to the privacy policy 2. Continue to login | 1. Unable to click to go to the next step | |||||
8 | Check "agree to complete login" on the verification login page | P2 | Security testing - Safety compliance | 1. Check "agree to privacy policy" 2. Continue to login | 1. Click to enter the next login operation | ||||||
9 | Policy content | Verify that the privacy policy jump is successful | P2 | Security testing - Safety compliance | On the login registration guide page | 1. Click the pop-up privacy policy | 1. Privacy policy jump succeeded 2. The page layout is normal , No blur and abnormality ( Copy version and content PM confirm ) | ||||
10 | Verify the three parties in the privacy policy SDK The description of use is correct | P2 | Security testing - Safety compliance | APP Using a third party SDK | 1. Go to the privacy policy page 2. Click three parties SDK link | 1. There is this in the privacy policy SDK Link to 2. Describe that the typesetting is normal | |||||
11 | APP Internal resident entrance | verification APP Internal access privacy policy steps do not exceed 4 Step | P1 | Security testing - Safety compliance | Entered APP | 1. Go to the personal center page 2. Find the privacy policy entry | 1. Click... From the main interface “ Personal center ” Start to calculate the first step to access the privacy policy 2.APP A permanent entrance with privacy policy is required | ||||
12 | Policy update | Verify that the privacy policy update prompt is successful | P2 | Security testing - Safety compliance | The privacy policy is significantly updated compared with the previous version (PM Need to inform ) | 1. Click to enter APP | 1. Need to be in APP Users are prompted to read ( stay APP Inside ) | ||||
13 | System permissions | Notice of news | verification IOS Message notification request popup succeeded | P1 | Security testing - Safety compliance | New installation APP,APP There is a message notification function | 1. land APP, Enter the home page | 1. There is a message notification request pop-up prompt | |||
14 | The verification message notifies that the request is rejected successfully | P1 | Security testing - Safety compliance | A message notification request has occurred | 1. land APP, Enter the home page 2. Click the pop-up box to reject the request | 1.APP Unable to send message notification 2. This authorization will not be requested continuously ( When this function is not used ) 3. If it is an alarm message, the request will be repeated ( Ask again after the first refusal ) | |||||
15 | The verification message notifies that the request is rejected and prompts success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Once again into the APP Message center | 1.APP Prompt again that you need to open this permission | ||||||
16 | Verify that the message notification request was accepted successfully | P2 | Security testing - Safety compliance | 1. land APP, Enter the home page 2. Click the pop-up box to accept the request | 1.APP You can send a message notification | ||||||
17 | Location permissions | verification IOS Position permission pop-up succeeded | P1 | Security testing - Safety compliance | New installation APP,APP It has the function of accessing location | 1. land APP, Enter the home page | 1. There is a pop-up prompt for position permission request | ||||
18 | verification Android Position permission pop-up succeeded | P1 | Security testing - Safety compliance | 1. land APP, Enter the home settings page 2. Set home location / Connect WI-FI/ bluetooth / Automation scenarios | 1. There is a pop-up prompt for position permission request | ||||||
19 | Verify that the foreground location permission request was rejected successfully | P1 | Security testing - Safety compliance | The location permission request pop-up window has appeared | 1. Click the pop-up box to reject the request | 1.APP Unable to enable geo location service , Unable to set home location, etc ( Foreground location permission ) 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
20 | Verify that the background location permission request was rejected successfully | P1 | Security testing - Safety compliance | 1. Click the pop-up box to reject the request 2.APP Switch to the background | 1. Cannot use geofencing ( Background location permissions ) | ||||||
21 | Verify that the location permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Enter setting home location again / Connect WI-FI/ bluetooth / Automation scenarios | 1.APP Prompt again that you need to open this permission | ||||||
22 | Verify that the foreground location permission request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1.APP Geographical location services can be enabled , Home location can be set / Connect WI-FI/ bluetooth / Automation scenarios | ||||||
23 | Verify that the background location permission request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request 2.APP Switch to the background | 1. You can use the geographic fence function ( If it has this function ) | ||||||
24 | Bluetooth rights | verification IOS Bluetooth permission request popup succeeded | P1 | Security testing - Safety compliance | New installation APP,APP Bluetooth connection function | 1. land APP, Enter the home page | 1. There is a pop-up prompt for Bluetooth permission request | ||||
25 | verification Android Bluetooth permission request popup succeeded | P1 | Security testing - Safety compliance | 1. land APP, Enter the automatic search distribution network page / Bluetooth category of manual distribution network ( The Bluetooth function of the system is off ) | 1. Bluetooth function switch request pop-up prompt | ||||||
26 | Verify that the Bluetooth request is rejected successfully | P1 | Security testing - Safety compliance | The Bluetooth permission request pop-up window has appeared | 1. Click the pop-up box to reject the request | 1.APP Unable to use Bluetooth function , Unable to configure and connect Bluetooth devices 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
27 | Verify that the Bluetooth request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Enter the Bluetooth enable option of automatic search configuration page again | 1.APP Prompt again that you need to open this permission | ||||||
28 | Verify that the Bluetooth request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1.APP You can use Bluetooth function , Configure and connect Bluetooth devices | ||||||
29 | Album permissions | Verify the photo album permission request pop-up successfully | P1 | Security testing - Safety compliance | 1. land APP, Enter the device settings page , Replace the equipment ICON 2. Enter the personal Center , Change your avatar 3. Cloud album | 1.IOS There is a pop-up prompt for requesting an album 2.Android There is a request album 、 Tips for files and media | |||||
30 | Verify that the album permission request was rejected successfully | P1 | Security testing - Safety compliance | An album has appeared ( Or media files ) Request pop-up | 1. Click the pop-up box to reject the request | 1.APP The device cannot be replaced ICON/ Personal portrait 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
31 | Verify that the photo album permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Enter the personal center again and change the avatar | 1.APP Prompt again that you need to open this permission | ||||||
32 | Verify that the album permission request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1.APP Equipment can be replaced ICON/ Personal portrait | ||||||
33 | Camera permissions | Verify that the camera permission request pop-up succeeded | P1 | Security testing - Safety compliance | New installation APP | 1. land APP, Use the scan function / Camera request during video call ( Need to add a class with video call IPC equipment ) | 1. There is a pop-up prompt for camera permission request | ||||
34 | Verify that the camera permission is denied successfully | P1 | Security testing - Safety compliance | A camera request pop-up has occurred | 1. Click the pop-up box to reject the request | 1. Unable to use the scan function /IPC Video call 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
35 | Verify that the camera permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Use the scan function again / Camera request during video call ( Need to add a class with video call IPC equipment ) | 1.APP Prompt again that you need to open this permission | ||||||
36 | Verify that the camera permission is accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1. Use the scan function /IPC Video call | ||||||
37 | Marketing information control authority | verification APP Have marketing information control authority | P1 | Security testing - Safety compliance | Has landed APP | 1. Enter the personal Center - Set up - Message settings | 1. There are marketing information control buttons , Controllable switch | ||||
38 | Share message request access ( Community classes and developers APP Share messages ( Read user pasteboard information )) | verification APP Shared message has request notification | P1 | Security testing - Safety compliance | 1. Get into APP Share information | 1. There is a request notification when sharing | |||||
39 | Mobile phone address book permission ( Community communication network APP) | Verify the mobile phone address book permission pop-up successfully | P1 | Security testing - Safety compliance | New installation APP | 1. land APP | 1. There is a pop-up prompt for mobile phone address book permission request | ||||
40 | Camera request during video call | When verifying the video call, the camera request pop-up succeeds | P1 | Security testing - Safety compliance | Added with video call IPC equipment | 1. Enter the device panel , Click the video call function button | 1. There is a pop-up prompt for camera permission request | ||||
41 | Verify that the camera request was rejected | P1 | Security testing - Safety compliance | A camera request pop-up has occurred | 1. Click the pop-up box to reject the request | 1. Unable to use the video call function 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
42 | Verify that the camera permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Click the video call function button again | 1.APP Prompt again that you need to open this permission | ||||||
43 | Verify that the camera request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1. You can use the video function normally , And will not pop up again | ||||||
44 | Microphone request during recording | When verifying the recording, the microphone request pop-up succeeded | P1 | Security testing - Safety compliance | Added with recording IPC equipment | 1. Enter the device panel , Click the recording function button / Voice control | 1. There is a pop-up prompt for microphone permission request | ||||
45 | Verify that the microphone request was rejected successfully | P1 | Security testing - Safety compliance | The microphone request pop-up window has appeared | 1. Click the pop-up box to reject the request | 1. Unable to use the recording function 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
46 | Verify that the microphone permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Click the recording function button again | 1.APP Prompt again that you need to open this permission | ||||||
47 | Verify that the microphone request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1. You can use the recording function normally , And will not pop up again | ||||||
48 | Calendar permissions ( If you need to bind with the system calendar, test ) | Verify the calendar permission request pop-up successfully | P1 | Security testing - Safety compliance | New installation APP | 1. Get into APP Schedule reservation function 2. Add appointment schedule | 1. There is a pop-up prompt for calendar permission request ( read / Write ) | ||||
49 | Verify calendar request rejected successfully | P1 | Security testing - Safety compliance | The calendar request pop-up window has appeared | 1. Click the pop-up box to reject the request | 1. Unable to use the schedule appointment function 2. This authorization will not be requested continuously ( When this function is not used ) | |||||
50 | Verify that the calendar permission request is rejected and prompt success again | P2 | Security testing - Safety compliance | 1. Click to reject the request 2. Click the add schedule function button again | 1.APP Prompt again that you need to open this permission | ||||||
51 | Verify that the calendar request was accepted successfully | P2 | Security testing - Safety compliance | 1. Click the pop-up box to accept the request | 1. The schedule management function can be used normally , And will not pop up again | ||||||
52 | Home Data jurisdiction | Verification request Home Data Pop up successful (IOS) | P2 | Security testing - Safety compliance | New installation APP | 1. land APP, Enter the home page ( family /Home APP) | 1. There is a request Home Data Pop up tips | ||||
53 | Authority verification | Verify that the permissions remain unchanged after the installation of the same mobile phone overlay | P1 | Security testing - Safety compliance | already installed APP, All system permissions are not accepted | 1. Overlay installation APP 2. Enter system settings , View correspondence APP The system authority of | 1. The opening of system permissions is the same as that before overlay installation APP Authority | ||||
54 | Verifying that different mobile phone installations require permission requests | P2 | Security testing - Safety compliance | New installation APP stay IOS and Android mobile phone | 1. Log in with the same account | 1. New installation APP You need to request permission | |||||
55 | Verify that the corresponding function cannot be used when the permission is turned off in the system settings | P1 | Security testing - Safety compliance | APP Has agreed to open various permissions | 1. Enter the mobile phone system , Turn off Bluetooth manually 、 Location 、 The camera 、 Message notification and other permissions 2. Once again into the APP Use the function corresponding to permission | 1. This function cannot be used , Prompt that you need to open permission | |||||
56 | Sensitive information collection ( If there are corresponding functions that need to be tested , Generally community SaaS class APP license plate number 、 Property fee (PM Provide a list of personal data collection )) | Sensitive information collection | A pop-up prompt appears when verifying the collection of ID card information | P1 | Security testing - Safety compliance | New installation APP | 1. land APP, Enter the page where you need to fill in the ID card information | 1. There is a pop-up box to inform the user ( Type of information collected 、 Collection and processing purposes 、 Handling rules 、 How to undo ) | |||
57 | Pop up prompt when verifying the collection of bank account information | P1 | Security testing - Safety compliance | 1. land APP, Enter the page where you need to fill in the bank account information | |||||||
58 | Pop up prompt when verifying the collection of whereabouts and trajectory information | P1 | Security testing - Safety compliance | 1. land APP, Enter the page where you need to fill in the whereabouts track information | |||||||
59 | Pop up prompt when verifying the collection of facial recognition information | P1 | Security testing - Safety compliance | 1. land APP, When face recognition is required for entry | |||||||
60 | Pop up prompt when verifying fingerprint information collection | P1 | Security testing - Safety compliance | 1. land APP, When you need to use fingerprints to enter | |||||||
61 | Pop up prompt when verifying address information collection | P1 | Security testing - Safety compliance | 1. land APP, When you need to fill in the address information to enter | |||||||
62 | The three party SDK( If there are corresponding functions that need to be tested , Privacy agreements correspond to the needs in China SDK Related description , The overseas English version does not describe ) | The three party SDK( Customized new ones are also ok ) | Verify that the three-party login contains the correct | P2 | Security testing - Safety compliance | New installation APP | 1. On the login registration guide page 2. Click the login button | 1.Android The domestic landing page has QQ、 WeChat ; Abroad have Facebook、Twitter、Google( No other three parties login ) 2.IOS The landing page is available in China QQ、 WeChat ; Abroad have Facebook、Twitter、Google、Apple ID( No other three parties login ) | |||
63 | Verify that the name of the three-party push service contains the correct | P2 | Security testing - Safety compliance | 1. Get into Backng backstage , Check the third-party push service | 1.Android There is Huawei in China 、OPPO、VIVO、 millet 、 meizu 、 umeng (3.10.0 Don't use it again ,KA Some old users still use Youmeng )、 Carrier pigeon (3.17.0 Don't use it again ); There is Google abroad FCM-Firebase、Messaging | ||||||
64 | Verify third parties IPC The service contains the correct | P2 | Security testing - Safety compliance | 1. Get into Backng backstage , View third-party video services | 1.Android contain Tutk 2.IOS Including easy pupil 、Tutk | ||||||
65 | Verify that the third-party voice service contains the correct | Security testing - Safety compliance | 1. Get into Backng backstage , View third-party voice services | 1.Android Including iFLYTEK (3.10.0 Existed before ,3.11/0 Replace it with graffiti's own service )、Google | |||||||
66 | Verify that the third-party speaker service contains the correct | P1 | Security testing - Safety compliance | 1. Get into Backng backstage , Check the third-party speaker service | 1.Android Domestic includes Ding Dong -QQ Loudspeaker box ; Foreign countries include Amazon(Alexa)、Google 2.IOS Domestic includes Ding Dong -QQ Loudspeaker box ; Foreign countries include Amazon(Alexa)、Google | ||||||
67 | Verify that the third-party map service contains the correct | P1 | Security testing - Safety compliance | 1. Get into Backng backstage , View third-party map services | 1.Android China includes Gaode ; Foreign countries include Google Maps 2.IOS China includes Gaode map | ||||||
68 | Verify that the three party information sharing contains correct | P1 | Security testing - Safety compliance | 1. Get into APP, Share information | 1.Android contain QQ、 WeChat 2.IOS Including microblogs | ||||||
69 | other | Tourist mode | Verify that the visitor mode login does not collect mobile phone information | P1 | Security testing - Safety compliance | New installation APP | 1. Use the visitor mode to log in and enter the homepage 2. Go to the personal center page | 1. You can normally experience the functions in the tourist mode , There is no need to fill in user data 2. The personal center page needs to fill in the user information to enter the personal account 、 Family members invite 、 Help and feedback and more services | |||
70 | Account cancellation | verification C End APP There is a logout entry | P1 | Security testing - Safety compliance | 1. land APP, Enter the personal Center - Account security | 1. The page has a logout button , Can complete logout | |||||
71 | APP There is logout guidance | P1 | Security testing - Safety compliance | 1. land APP, Enter the personal Center - Account security | 1. There can be no logout entry , But guidance is needed | ||||||
边栏推荐
- Print linked list from end to end
- PR FAQ: how to set PR vertical screen sequence?
- The 15 year old interviewer will teach you four unique skills that you must pass the interview
- [effective Objective-C] - block and grand central distribution
- 第一章: 舍罕王失算
- 原生表格-滚动-合并功能
- PR 2021 quick start tutorial, how to create new projects and basic settings of preferences?
- 2.7 format output of values
- Chapter 2: 4-digit Kaplan number, search even digit Kaplan number, search n-digit 2-segment sum square number, m-digit ingenious square number without 0, specify the number to form a 7-digit square nu
- 2.1 use of variables
猜你喜欢

Chapter 20: y= sin (x) /x, rambling coordinate system calculation, y= sin (x) /x with profile graphics, Olympic rings, ball rolling and bouncing, water display, rectangular optimization cutting, R que

Derivation of decision tree theory
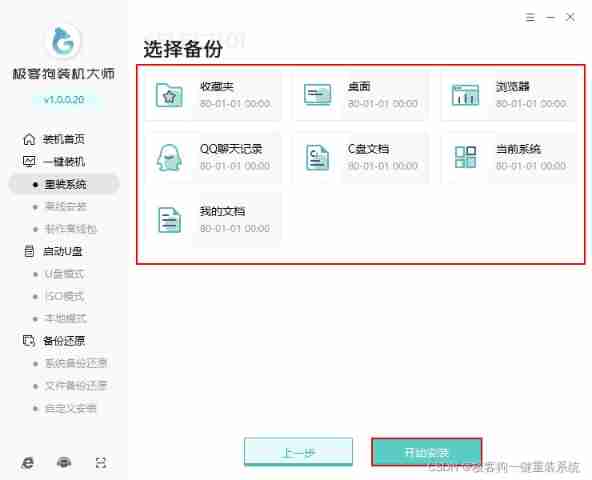
Don't be afraid of no foundation. Zero foundation doesn't need any technology to reinstall the computer system
![2022 - 06 - 30 networker Advanced (XIV) Routing Policy Matching Tool [ACL, IP prefix list] and policy tool [Filter Policy]](/img/b6/5d6b946d8001e2d73c2cadbdce72fc.png)
2022 - 06 - 30 networker Advanced (XIV) Routing Policy Matching Tool [ACL, IP prefix list] and policy tool [Filter Policy]
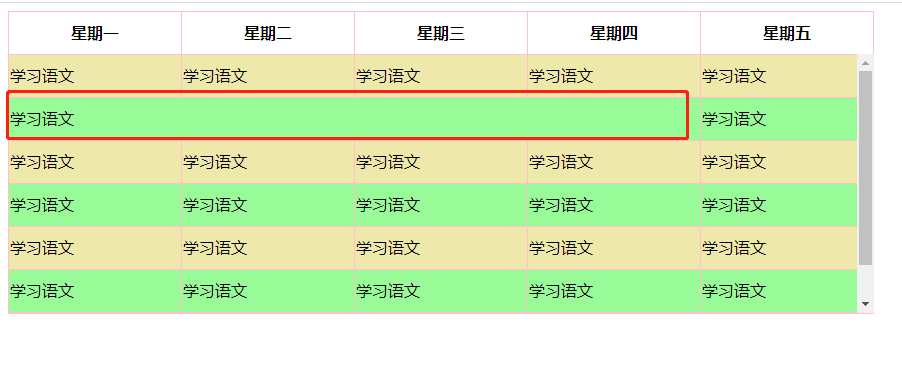
Native table - scroll - merge function
![Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue](/img/5b/fc776a1982e24b82984d82be6a016f.jpg)
Meso tetra [P - (p-n-carbazole benzylidene imino)] phenylporphyrin (tcipp) /eu (tcipp) [pc( α- 2-oc8h17) 4] and euh (tcipp) [pc (a-2-oc8h17) 4] supplied by Qiyue
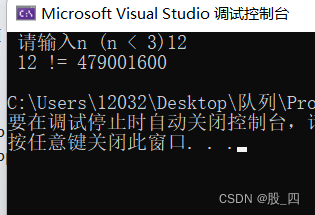
Chapter 1: find the factorial n of n!
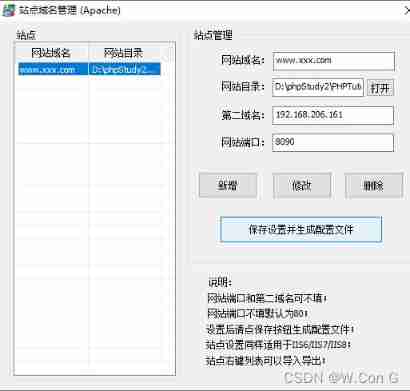
Phpstudy set LAN access

NFT without IPFs and completely on the chain?
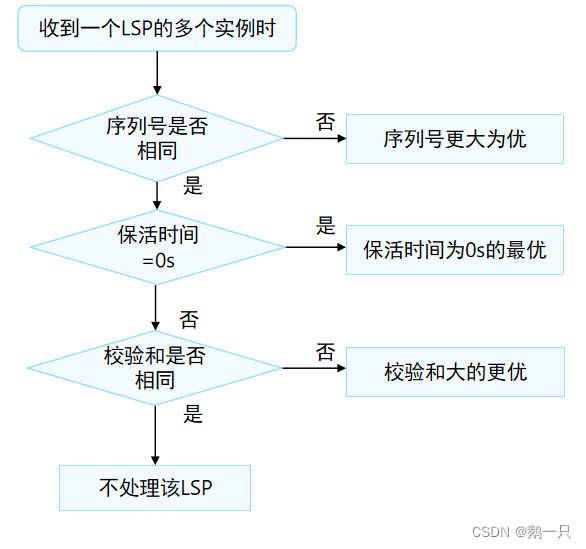
2022-06-27 网工进阶(十二)IS-IS-开销类型、开销计算、LSP的处理机制、路由撤销、路由渗透
随机推荐
PR FAQ: how to set PR vertical screen sequence?
Gym welcomes the first complete environmental document, which makes it easier to get started with intensive learning!
2022-06-25 advanced network engineering (XI) IS-IS synchronization process of three tables (neighbor table, routing table, link state database table), LSP, cSNP, psnp, LSP
kubernetes集群搭建efk日志收集平台
HCIA-USG Security Policy
Chapter 1: recursively find the factorial n of n!
Bool blind note - score query
Nerfplusplus parameter format sorting
Ae/pr/fcpx super visual effects plug-in package fxfactory
Virtual machine installation deepin system
Chapter 1: find the algebraic sum of odd factors, find the same decimal sum s (D, n), simplify the same code decimal sum s (D, n), expand the same code decimal sum s (D, n)
Detailed and not wordy. Share the win10 tutorial of computer reinstallation system
Micro service knowledge sorting - asynchronous communication technology
第一章: 舍罕王失算
Exercises of function recursion
Ruby replaces gem Alibaba image
2.3 other data types
Acquisition and transmission of parameters in automatic testing of JMeter interface
Implementation of stack
Basic command of IP address configuration ---ip V4