当前位置:网站首页>输入年份、月份,确定天数
输入年份、月份,确定天数
2022-07-04 06:58:00 【cycy_0918】
#include<iostream>
using namespace std;
int year,month;
//年份正确
bool isRightYear(int year){
if(year>=0&&year<=9999)
return true;
return false;
}
//月份正确
bool isRightMonth(int month){
if(month>=1&&month<=12)
return true;
return false;
}
//年份是否为闰年
bool isLeapYear(int year){
if(year%400==0||(year%100!=0&&year%4==0))
return true;
return false;
}
//月份类型
int monthType(int month){
int days;
switch(month){
case 1:case 3:case 5:case 7:case 8:case 10:case 12:
days=31;break;
case 4:case 6: case 9: case 11:
days=30;break;
case 2:
if(isLeapYear(year))
{
days=29;break;
}
else{
days=28;break;
}
}
return days;
}
int main()
{
cin>>year>>month;
isRightYear(year);
isRightMonth(month);
cout<<monthType(month)<<endl;
return 0;
}
边栏推荐
- Responsive - media query
- 2022 is probably the best year for the economy in the next 10 years. Did you graduate in 2022? What is the plan after graduation?
- Analysis of tars source code 1
- Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
- MySQL 45 lecture learning notes (XIII) delete half of the table data, and the table file size remains the same
- Cochez une colonne d'affichage dans une colonne de tableau connue
- The difference between synchronized and lock
- MySQL 45 lecture learning notes (XIV) count (*)
- Wechat applet scroll view component scrollable view area
- Tar source code analysis Part 3
猜你喜欢
Deep understanding of redis -- a new type of bitmap / hyperloglgo / Geo
Review of enterprise security incidents: how can enterprises do a good job in preventing source code leakage?
centos8安装mysql.7 无法开机启动

Master-slave replication principle of MySQL database

Su Weijie, a member of Qingyuan Association and an assistant professor at the University of Pennsylvania, won the first Siam Youth Award for data science, focusing on privacy data protection, etc
电脑通过Putty远程连接树莓派
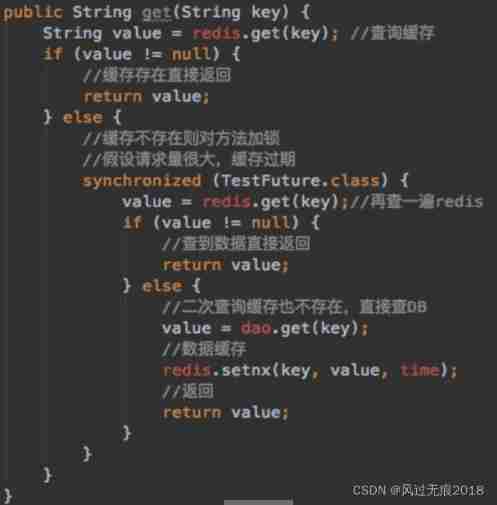
Redis - detailed explanation of cache avalanche, cache penetration and cache breakdown
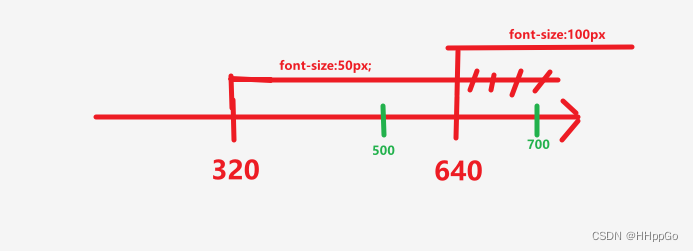
响应式移动Web测试题
![[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)](/img/03/2b37e63d0d482d5020b7421ac974cb.jpg)
[MySQL] introduction, function, creation, view, deletion and modification of database view (with exercises)
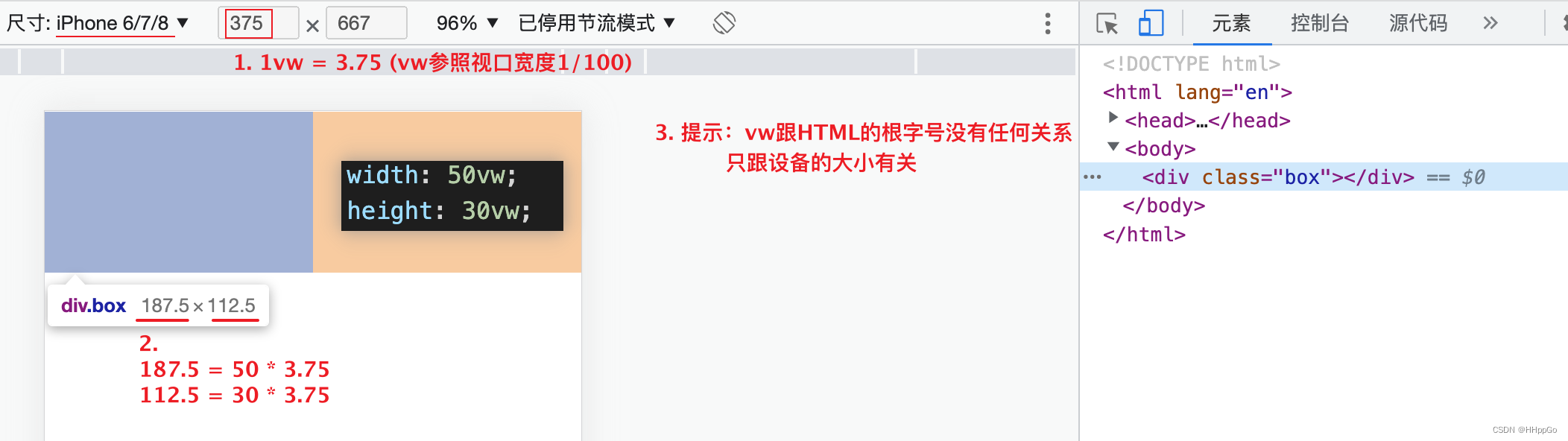
移动适配:vw/vh
随机推荐
[FPGA tutorial case 8] design and implementation of frequency divider based on Verilog
Campus network problems
Vulhub vulnerability recurrence 76_ XXL-JOB
MySQL 45 lecture learning notes (12) MySQL will "shake" for a while
Boosting the Performance of Video Compression Artifact Reduction with Reference Frame Proposals and
Background and current situation of domestic CDN acceleration
Node connection MySQL access denied for user 'root' @ 'localhost' (using password: yes
MySQL 45 lecture learning notes (XIV) count (*)
【网络数据传输】基于FPGA的百兆网/兆网千UDP数据包收发系统开发,PC到FPGA
tars源码分析之3
Research on an endogenous data security interaction protocol oriented to dual platform and dual chain architecture
[GF (q) + LDPC] regular LDPC coding and decoding design and MATLAB simulation based on the GF (q) field of binary graph
How does the inner roll break?
tars源码分析之4
Check and display one column in the known table column
2022年6月小结
the input device is not a TTY. If you are using mintty, try prefixing the command with ‘winpty‘
2022年,或許是未來10年經濟最好的一年,2022年你畢業了嗎?畢業後是怎麼計劃的?
A new understanding of how to encrypt industrial computers: host reinforcement application
Introduction to deep learning Ann neural network parameter optimization problem (SGD, momentum, adagrad, rmsprop, Adam)