当前位置:网站首页>Awk processing JSON processing
Awk processing JSON processing
2022-07-07 21:15:00 【Chestnut less】
Nested parsing and lists will be a little bug... However, it meets the requirements of light use
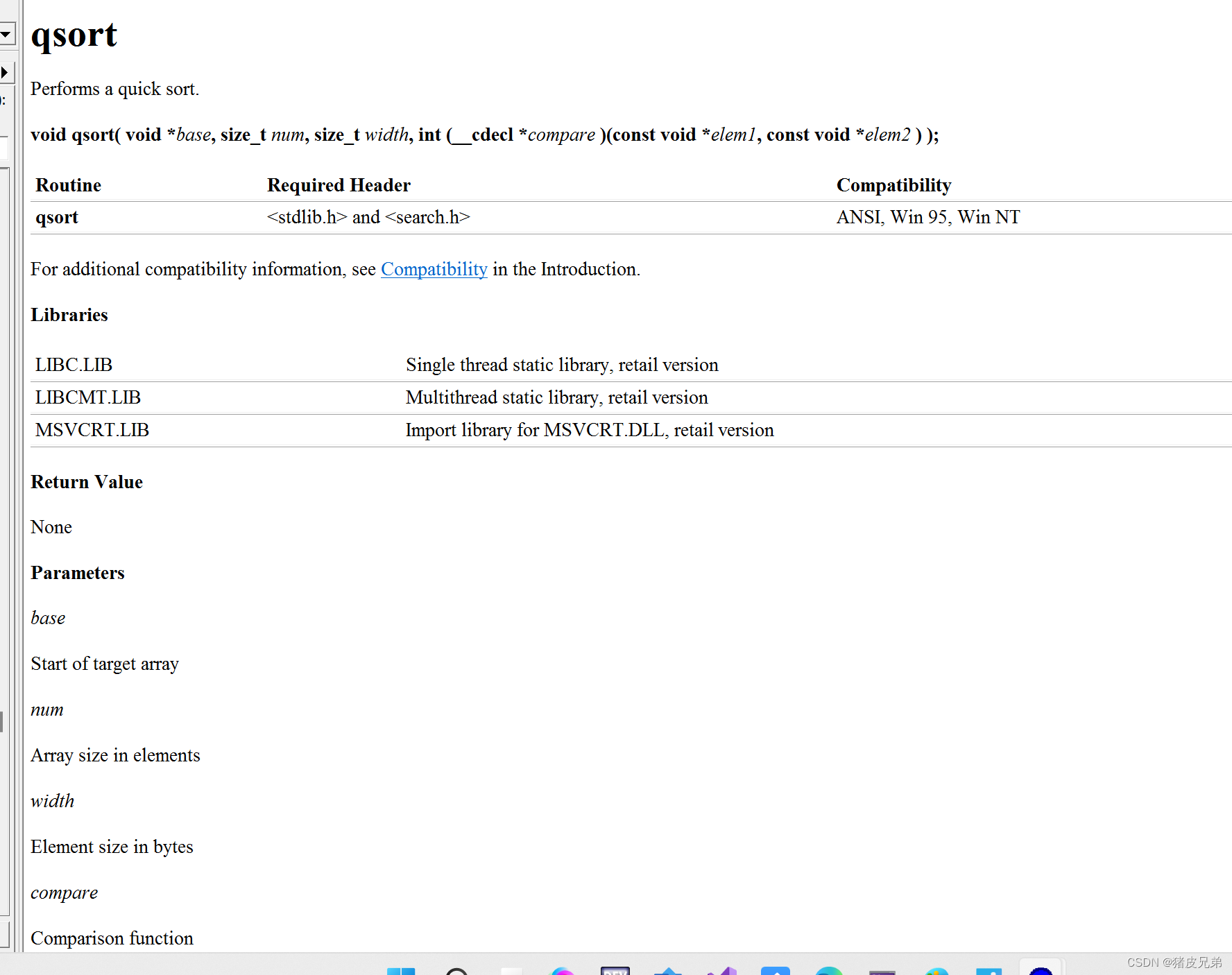
#!/bin/bash
json_str='{
"access_token":"12345678-1234-1234-1234-123456789012",
"token_type":"bearer",
"refresh_token":"12345678-1234-1234-1234-12345678901"
}'
get_json_value() {
awk -v json="$1" -v key="$2" -v defaultValue="$3" 'BEGIN{
foundKeyCount = 0
while (length(json) > 0) {
pos = match(json, "\""key"\"[ \\t]*?:[ \\t]*");
if (pos == 0) {if (foundKeyCount == 0) {print defaultValue;} exit 0;}
++foundKeyCount;
start = 0; stop = 0; layer = 0;
for (i = pos + length(key) + 1; i <= length(json); ++i) {
lastChar = substr(json, i - 1, 1)
currChar = substr(json, i, 1)
if (start <= 0) {
if (lastChar == ":") {
start = currChar == " " ? i + 1: i;
if (currChar == "{" || currChar == "[") {
layer = 1;
}
}
} else {
if (currChar == "{" || currChar == "[") {
++layer;
}
if (currChar == "}" || currChar == "]") {
--layer;
}
if ((currChar == "," || currChar == "}" || currChar == "]") && layer <= 0) {
stop = currChar == "," ? i : i + 1 + layer;
break;
}
}
}
if (start <= 0 || stop <= 0 || start > length(json) || stop > length(json) || start >= stop) {
if (foundKeyCount == 0) {print defaultValue;} exit 0;
} else {
print substr(json, start, stop - start);
}
json = substr(json, stop + 1, length(json) - stop)
}
}'
}
echo $(get_json_value "${json_str}" "refresh_token")边栏推荐
- UVA 12230 – crossing rivers (probability) "suggested collection"
- 【矩阵乘】【NOI 2012】【cogs963】随机数生成器
- Cantata9.0 | 全 新 功 能
- 恶魔奶爸 A3阶段 近常速语流初接触
- 2022年在启牛开中银股票的账户安全吗?
- Contour layout of margin
- 现在网上开户安全么?想知道我现在在南宁,到哪里开户比较好?
- 部署、收回和删除解决方式—-STSADM和PowerShell「建议收藏」
- Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
- FatMouse&#39; Trade (Hangdian 1009)
猜你喜欢
随机推荐
FatMouse&#39; Trade (Hangdian 1009)
数值法求解最优控制问题(〇)——定义
I have to use my ID card to open an account. Is the bank card safe? I don't understand it
Datatable data conversion to entity
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
Helix QAC 2020.2 new static test tool maximizes the coverage of standard compliance
Solve the problem of using uni app mediaerror mediaerror errorcode -5
How to choose fund products? What fund is suitable to buy in July 2022?
万字总结数据存储,三大知识点
Do you have to make money in the account to open an account? Is the fund safe?
Hdu4876zcc love cards (multi check questions)
Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
刚开户的能买什么股票呢?炒股账户安全吗
Codesonar enhances software reliability through innovative static analysis
恶魔奶爸 A0 英文零基础的自我提升路
Codesonar Webinar
[award publicity] issue 22 publicity of the award list in June 2022: Community star selection | Newcomer Award | blog synchronization | recommendation Award
恶魔奶爸 B1 听力最后壁垒,一鼓作气突破
目标:不排斥 yaml 语法。争取快速上手
Is private equity legal in China? Is it safe?