当前位置:网站首页>Jetty: configure connector [easy to understand]
Jetty: configure connector [easy to understand]
2022-07-07 21:04:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack .
Connector configuration Overview
Connectors are used to receive network connections , To configure a connector, you need to configure : 1) The network parameters of the connector ( such as :port); 2) The services used by the connector ( such as :executors,schedulers). 3) Initialize and configure the protocol's connection factory to receive connections . Jetty The main types of connectors used are ServerConnector. standard Jetty Publish using the following Jetty XML File creation and configuration connector : 1)jetty-http.xml Initialize a ServerConnector, Used to receive HTTP Connect ( Can be upgraded to WebSocket Connect ). 2)jetty-https.xml Initialize a ServerConnector. Used to receive SSL/TLS Connect . 3)example-jetty-spdy.xml Initialize a ServerConnector. Used to receive SSL Connect , Connection to use HTTP perhaps SPDY signal communication .
Construct a ServerConnector
One ServerConnector The service used is set at construction time , The back can't change , Services are mostly set to the default null or 0, Such a reasonable default value will be adopted , therefore , In most cases, you just need to set Server And connection factory . stay Jetty XML in ( namely jetty-http.xml in ). You can configure :
<New class="org.eclipse.jetty.server.ServerConnector">
<Arg name="server"><Ref refid="Server" /></Arg>
<Arg name="factories">
<Array type="org.eclipse.jetty.server.ConnectionFactory">
<!-- insert one or more factories here -->
</Array>
</Arg>
<!-- set connector fields here -->
</New>Can you in Javadoc You see the structure in ServerConnector Other parameters of , But for almost all the deployment , The default is enough .
Network settings
Configure the network settings of the connector before it starts , call setters Set up .
such as , Can you in Jetty XML Set in port:
<New class="org.eclipse.jetty.server.ServerConnector">
<Arg name="server"><Ref refid="Server" /></Arg>
<Arg name="factories"><!-- insert one or more factories here --></Arg>
<Set name="port">8080</Set>
</New>Jetty XML The values in can also be parameterized , So that they can pass in through the properties file or the command line . Here is an example of using the properties file :
<New class="org.eclipse.jetty.server.ServerConnector">
<Arg name="server"><Ref refid="Server" /></Arg>
<Arg name="factories"><!-- insert one or more factories here --></Arg>
<Set name="port"><Property name="jetty.port" default="8080"/></Set>
</New>ServerConnector The network settings for include : 1)host: Connector bound network interface , Can be IP Address or host name . The assumption is null or 0.0.0.0, Bind to all interfaces . 2)port: The connector port,0 It means to use random port( adopt getLocalPort() Choose what is available port); 3)idleTimeout: After the connector is idle for that time ( Unit millisecond ) close . 4)defaultProtocol: For choosing ConnectionFactory The default protocol name of the instance . 5)stopTimeout: Gently stop the waiting time before a connector ( millisecond ); 6)acceptQueueSize: The size of the connection queue waiting to be processed , It's better to keep the default value . Unless you have a reason to change it ; 7)reuseAddress: agree! Server socket Rebinding , Even in TIME_WAIT state .
Usually keep the default value true; 8)soLingerTime: If value >=0. Is set socket SO_LINGER value , Unit millisecond .
Jetty Try to gently close all TCP/IP Connect , Therefore, the value should not be changed , Keep the default -1.
HTTP To configure
HttpConfiguration by HTTPChannel Provide configuration . You can create 1 Yes 1 Of HTTP Connect . perhaps 1 Yes n Multiplexing of SPDY Connect .
So a HTTPConfiguration Can be used for HTTP and SPDY Connection factory .
To avoid repeated configuration . standard Jetty Published in jetty.xml Create a common HttpConfiguration example , It's a Ref Elements , In the jetty-http.xml, jetty-https.xml and example-jetty-spdy.xml Use it in . A normal HttpConfiguration Configuration, for example :
<New id="httpConfig" class="org.eclipse.jetty.server.HttpConfiguration">
<Set name="secureScheme">https</Set>
<Set name="securePort"><Property name="jetty.tls.port" default="8443" /></Set>
<Set name="outputBufferSize">32768</Set>
<Set name="requestHeaderSize">8192</Set>
<Set name="responseHeaderSize">8192</Set>
<Call name="addCustomizer">
<Arg><New class="org.eclipse.jetty.server.ForwardedRequestCustomizer"/></Arg>
</Call>
</New>This example adds a ForwardedRequestCustomizer Handle X-Forward-For And related protocol headers .
jetty-https.xml Can pass through ID Use this example :
<Call name="addConnector">
<Arg>
<New class="org.eclipse.jetty.server.ServerConnector">
<Arg name="server"><Ref refid="Server" /></Arg>
<Arg name="factories">
<Array type="org.eclipse.jetty.server.ConnectionFactory">
<Item>
<New class="org.eclipse.jetty.server.HttpConnectionFactory">
<Arg name="config"><Ref refid="httpConfig" /></Arg>
</New>
</Item>
</Array>
</Arg>
<!-- ... -->
</New>
</Arg>
</Call>by SSL( stay jetty-https.xml and jetty-spdy.xml in ),”httpConfig” Instances can be used to create SSL The foundation of a specific configuration :
<New id="tlsHttpConfig" class="org.eclipse.jetty.server.HttpConfiguration">
<Arg><Ref refid="httpConfig"/></Arg>
<Call name="addCustomizer">
<Arg><New class="org.eclipse.jetty.server.SecureRequestCustomizer"/></Arg>
</Call>
</New>Use here SecureRequestCustomizer. add to SSL Session IDs And authentication information as request attributes .
SSL Context configuration
SSL/TLS Connectors are used for HTTPS and SPDY, Require authentication information to establish a secure connection . In the following “ To configure SSL” The festival will make a specific discussion .
Configure connection factory
stay Jetty In publication . The simplest example of a connection factory is jetty-http.xml:
<?xml version="1.0"?><!DOCTYPE Configure PUBLIC "-//Jetty//Configure//EN" "http://www.eclipse.org/jetty/configure_9_0.dtd"> <!-- ============================================================= --><!-- Configure the Jetty Server instance with an ID "Server" --><!-- by adding a HTTP connector. --><!-- This configuration must be used in conjunction with jetty.xml --><!-- ============================================================= --><Configure id="Server" class="org.eclipse.jetty.server.Server"> <!-- =========================================================== --> <!-- Add a HTTP Connector. --> <!-- Configure an o.e.j.server.ServerConnector with a single --> <!-- HttpConnectionFactory instance using the common httpConfig --> <!-- instance defined in jetty.xml --> <!-- --> <!-- Consult the javadoc of o.e.j.server.ServerConnector and --> <!-- o.e.j.server.HttpConnectionFactory for all configuration --> <!-- that may be set here. --> <!-- =========================================================== --> <Call name="addConnector"> <Arg> <New class="org.eclipse.jetty.server.ServerConnector"> <Arg name="server"><Ref refid="Server" /></Arg> <Arg name="factories"> <Array type="org.eclipse.jetty.server.ConnectionFactory"> <Item> <New class="org.eclipse.jetty.server.HttpConnectionFactory"> <Arg name="config"><Ref refid="httpConfig" /></Arg> </New> </Item> </Array> </Arg> <Set name="host"><Property name="jetty.host" /></Set> <Set name="port"><Property name="jetty.port" default="80" /></Set> <Set name="idleTimeout"><Property name="http.timeout" default="30000"/></Set> <Set name="soLingerTime"><Property name="http.soLingerTime" default="-1"/></Set> </New> </Arg> </Call> </Configure>There's only one ConnectionFactory Injected , When a new connection is received ,HttpConnectionFactory Will create a HttpConnection. A more complex example is jetty-spdy.xml, Multiple connection factories are configured :
/*
* Tips : This line of code is too long , The system automatically comments without highlighting . One click Copy removes system comments
* <?xml version="1.0" encoding="UTF-8"?><!DOCTYPE Configure PUBLIC "-//Jetty//Configure//EN" "http://www.eclipse.org/jetty/configure_9_0.dtd"> <Configure id="Server" class="org.eclipse.jetty.server.Server"> <New id="sslContextFactory" class="org.eclipse.jetty.util.ssl.SslContextFactory"> <Set name="keyStorePath">src/main/resources/keystore.jks</Set> <Set name="keyStorePassword">storepwd</Set> <Set name="trustStorePath">src/main/resources/truststore.jks</Set> <Set name="trustStorePassword">storepwd</Set> <Set name="protocol">TLSv1</Set> </New> <New id="tlsHttpConfig" class="org.eclipse.jetty.server.HttpConfiguration"> <Arg> <New id="httpConfig" class="org.eclipse.jetty.server.HttpConfiguration"> <Set name="secureScheme">https</Set> <Set name="securePort"> <Property name="jetty.tls.port" default="8443"/> </Set> <Set name="outputBufferSize">32768</Set> <Set name="requestHeaderSize">8192</Set> <Set name="responseHeaderSize">8192</Set> <!-- Uncomment to enable handling of X-Forwarded- style headers <Call name="addCustomizer"> <Arg><New class="org.eclipse.jetty.server.ForwardedRequestCustomizer"/></Arg> </Call> --> </New> </Arg> <Call name="addCustomizer"> <Arg> <New class="org.eclipse.jetty.server.SecureRequestCustomizer"/> </Arg> </Call> </New> <New id="pushStrategy" class="org.eclipse.jetty.spdy.server.http.ReferrerPushStrategy"> <!-- Uncomment to blacklist browsers for this push strategy. If one of the blacklisted Strings occurs in the user-agent header sent by the client, push will be disabled for this browser. This is case insensitive" --> <!-- <Set name="UserAgentBlacklist"> <Array type="String"> <Item>.*(?i)firefox/14.*</Item> <Item>.*(?i)firefox/15.*</Item> <Item>.*(?i)firefox/16.*</Item> </Array> </Set> --> <!-- Uncomment to override default file extensions to push --> <!-- <Set name="PushRegexps"> <Array type="String"> <Item>.*\.css</Item> <Item>.*\.js</Item> <Item>.*\.png</Item> <Item>.*\.jpg</Item> <Item>.*\.gif</Item> </Array> </Set> --> <Set name="referrerPushPeriod">5000</Set> <Set name="maxAssociatedResources">32</Set> </New> <Call id="sslConnector" name="addConnector"> <Arg> <New class="org.eclipse.jetty.server.ServerConnector"> <Arg name="server"><Ref refid="Server"/></Arg> <Arg name="factories"> <Array type="org.eclipse.jetty.server.ConnectionFactory"> <!-- SSL Connection factory with NPN as next protocol --> <Item> <New class="org.eclipse.jetty.server.SslConnectionFactory"> <Arg name="next">npn</Arg> <Arg name="sslContextFactory"> <Ref refid="sslContextFactory"/> </Arg> </New> </Item> <!-- NPN Connection factory with HTTP as default protocol --> <Item> <New class="org.eclipse.jetty.spdy.server.NPNServerConnectionFactory"> <Arg name="protocols"> <Array type="String"> <Item>spdy/3</Item> <Item>spdy/2</Item> <Item>http/1.1</Item> </Array> </Arg> <Set name="defaultProtocol">http/1.1</Set> </New> </Item> <!-- SPDY/3 Connection factory --> <Item> <New class="org.eclipse.jetty.spdy.server.http.HTTPSPDYServerConnectionFactory"> <Arg name="version" type="int">3</Arg> <Arg name="config"> <Ref refid="tlsHttpConfig"/> </Arg> <Arg name="pushStrategy"> <Ref refid="pushStrategy"/> </Arg> </New> </Item> <!-- SPDY/2 Connection factory --> <Item> <New class="org.eclipse.jetty.spdy.server.http.HTTPSPDYServerConnectionFactory"> <Arg name="version" type="int">2</Arg> <Arg name="config"> <Ref refid="tlsHttpConfig"/> </Arg> </New> </Item> <!-- HTTP Connection factory --> <Item> <New class="org.eclipse.jetty.server.HttpConnectionFactory"> <Arg name="config"> <Ref refid="tlsHttpConfig"/> </Arg> </New> </Item> </Array> </Arg> <Set name="port">8443</Set> </New> </Arg> </Call> </Configure>
*/In this example, there are 5 A connection factory was created . Linked by their protocol name : 1)”SSL-npn” The default protocol identified by the first connection factory , The connection factory configured here is SslConnectionFactory, Use ”npn” As the next agreement .
So the receiving endpoint and SslConnection Examples are related ,SslConnection Examples and ”npn” Connection factory created NextProtoNegoServerConnection Examples form the processing chain . 2)”npn” Here is NPNServerConnectionFactory. link to SslConnectionFactory.NPN Connect with client The type of negotiation agreement . Then find the factory according to the name of the agreement ( following 3 One of them ) And create a connection to replace NPN Connect . hypothesis NPN Is not supported ,defaultProtocol Be configured as “http/1.1”. 3)”spdy/3″ hypothesis SPDY The version number is 3, be NPN Connect to use the factory . 4)”spdy/2″ hypothesis SPDY The version number is 2. be NPN Connect to use the factory . 5)”http/1.1″ hypothesis HTTP The version number is 1.1, Or suppose NPN Is not supported .NPN Connect with the factory .
Be careful HTTP/1.1 Can also deal with HTTP/1.0.
To configure SSL
To configure SSL It's a complicated process , In relation to keys、certificates、protocols and formats, It would be very helpful to have a major understanding of these , The following links provide some information for reference : 1)Certificates SSL Certificates HOWTO(http://en.tldp.org/HOWTO/SSL%20Certificates%20HOWTO) Mindprod Java Glossary: Certificates(http://mindprod.com/jgloss/certificate.html) 2)Keytool Keytool for Unix(http://docs.oracle.com/javase/7/docs/technotes/tools/solaris/keytool.html) Keytool for Windows(http://docs.oracle.com/javase/7/docs/technotes/tools/windows/keytool.html) 3)Other tools IBM Keyman(http://www.openssl.org/docs/HOWTO/) OpenSSL FAQ(http://www.openssl.org/support/faq.html)
OpenSSL vs. Keytool
To test , And JDK The binding of keytool Tools provide the easiest way to generate what you need key and cetificate. You can also use OpenSSL Tools produce key and certificate, Or transform those you use for Apache Or other servers Of . because Apache And other servers It's all used OpenSSL Tool set generation and operation keys and certificates. You may already have some passing OpenSSL Created keys and certificates, Or you might like it better OpenSSL The resulting format . Suppose you want to talk to Jetty Or a web server( such as Apache, Not with Java Realization ) Use the same cetificate. You might prefer to use OpenSSL Generate your private key and certificate.
by Jetty To configure SSL
In order to be in Jetty To configure SSL, You need to run the following tasks : 1) produce key Value pair sum certificates; 2) Ask for a trusted certificate. 3) load keys and certificates. 4) To configure SslContextFactory. The following will introduce one by one .
produce Key Value pair sum certificate
The simplest way to produce keys and certificates The way is to use JDK Self contained keytool, He produced keys and certificates Go straight into keystore. Suppose you already have keys and certificates. You can load them into JSSE keystore( Look at the following “ load keys and certificates”), Or replace the expired certificate. The following example will produce only the main keys and certificates. You should read the specific manual of the tool , Suppose you want to specify : 1)key Size ; 2)certificate Due time ; 3) Alternate security providers .
Use JDK Of keytool produce keys and certificates
Here are the USES keystore produce keys and certificates Example :
$ keytool -keystore keystore -alias jetty -genkey -keyalg RSAThe command line prompts you for information . It should be noted that ”first and last name” The prompt answer must provide server Valid host name for . Here's an example :
$ keytool -keystore keystore -alias jetty -genkey -keyalg RSA
Enter keystore password: password
What is your first and last name?
[Unknown]: jetty.eclipse.org
What is the name of your organizational unit? [Unknown]: Jetty What is the name of your organization? [Unknown]: Mort Bay Consulting Pty. Ltd. What is the name of your City or Locality? [Unknown]: What is the name of your State or Province? [Unknown]: What is the two-letter country code for this unit? [Unknown]: Is CN=jetty.eclipse.org, OU=Jetty, O=Mort Bay Consulting Pty. Ltd., L=Unknown, ST=Unknown, C=Unknown correct? [no]: yes Enter key password for <jetty> (RETURN if same as keystore password): $Use OpenSSL produce Keys and Certificates
The following command is in the file jetty.key To create a key It's worth it :
$ openssl genrsa -des3 -out jetty.keyThe following command is key Produce a certificate, File in jetty.crt:
$ openssl req -new -x509 -key jetty.key -out jetty.crtHere's a complete example . Be careful “Common Name” Asked to provide server The full host name of :
$ openssl genrsa -des3 -out jetty.key
Generating RSA private key, 512 bit long modulus
...........................++++++++++++
..++++++++++++
e is 65537 (0x10001)
Enter pass phrase for jetty.key:
Verifying - Enter pass phrase for jetty.key:
$ openssl req -new -x509 -key jetty.key -out jetty.crt
Enter pass phrase for jetty.key:
You are about to be asked to enter information to be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there is a default value,
If you enter '.', the field is left blank.
-----
Country Name (2 letter code) [AU]:.
State or Province Name (full name) [Some-State]:.
Locality Name (eg, city) []:.
Organization Name (eg, company) [Internet Widgets Pty Ltd]:Mort Bay Consulting Pty. Ltd.
Organizational Unit Name (eg, section) []:Jetty
Common Name (eg, YOUR name) []:jetty.eclipse.org
Email Address []:
$Other ways to get keys and certificates
You can also get it in other ways keys and certificates.
Ask for a credible certificate
Use keytool and OpenSSL Produced keys and certificates It's enough to perform a SSL The connector . However, browsers will not trust what you produce certificate, It will prompt the user certificate Unbelievable . In order to get a place that most browsers trust certificate, You need to ask for a well-known certificate authority(CA) For you key/certificate Signature . such CA contain :AddTrust,Entrust,GeoTrust,RSA Data Security,Thawte,VISA,ValiCert,Verisign. and beTRUSTed, wait . every last CA Each has its own guidebook ( see JSSE perhaps OpenSSL The section ). But all of them CA They all want to produce a certificate signing request(CSR).
use keytool produce CSR
The following command is already in keystore Medium key/cert produce jetty.csr file :
$ keytool -certreq -alias jetty -keystore keystore -file jetty.csruse OpenSSL produce CSR
The following command is jetty.key Medium key produce jetty.csr file :
$ openssl req -new -key jetty.key -out jetty.csrNote that this command only uses jetty.key Medium key. No, jetty.crt Medium certificate. You need to enter certificate The details of the .
load keys and certificates
once CA I gave you a certificate. Or suppose you don't use keytool Produce your own certificate, You need to load it into JSSE keystore.
Use keytool load certificates
You can use keytool Load a PEM Format certificate To keystore,PEM The format is the text encoding of a certificate . It passes through OpenSSL produce , By some CA Back to you . following PEM An example of a file :
jetty.crt
-----BEGIN CERTIFICATE-----
MIICSDCCAfKgAwIBAgIBADANBgkqhkiG9w0BAQQFADBUMSYwJAYDVQQKEx1Nb3J0
IEJheSBDb25zdWx0aW5nIFB0eS4gTHRkLjEOMAwGA1UECxMFSmV0dHkxGjAYBgNV
BAMTEWpldHR5Lm1vcnRiYXkub3JnMB4XDTAzMDQwNjEzMTk1MFoXDTAzMDUwNjEz
MTk1MFowVDEmMCQGA1UEChMdTW9ydCBCYXkgQ29uc3VsdGluZyBQdHkuIEx0ZC4x
DjAMBgNVBAsTBUpldHR5MRowGAYDVQQDExFqZXR0eS5tb3J0YmF5Lm9yZzBcMA0G
CSqGSIb3DQEBAQUAA0sAMEgCQQC5V4oZeVdhdhHqa9L2/ZnKySPWUqqy81riNfAJ
7uALW0kEv/LtlG34dOOcVVt/PK8/bU4dlolnJx1SpiMZbKsFAgMBAAGjga4wgasw
HQYDVR0OBBYEFFV1gbB1XRvUx1UofmifQJS/MCYwMHwGA1UdIwR1MHOAFFV1gbB1
XRvUx1UofmifQJS/MCYwoVikVjBUMSYwJAYDVQQKEx1Nb3J0IEJheSBDb25zdWx0
aW5nIFB0eS4gTHRkLjEOMAwGA1UECxMFSmV0dHkxGjAYBgNVBAMTEWpldHR5Lm1v
cnRiYXkub3JnggEAMAwGA1UdEwQFMAMBAf8wDQYJKoZIhvcNAQEEBQADQQA6NkaV
OtXzP4ayzBcgK/qSCmF44jdcARmrXhiXUcXzjxsLjSJeYPJojhUdC2LQKy+p4ki8
Rcz6oCRvCGCe5kDB
-----END CERTIFICATE-----The following command loads a PEM Encoded Certificate (jetty.crt) To JSSE keystore:
$ keytool -keystore keystore -import -alias jetty -file jetty.crt -trustcacertsSuppose you CA The certificate received is not kertool The format of understanding , You can use openssl Command conversion format :
$ openssl x509 -in jetty.der -inform DER -outform PEM -out jetty.crtadopt PKCS12 load keys and certificates
Suppose your key And Certificate in a different file , You need to merge them into PKCS12 Format . And then load it into keystore. Certificates can be generated by yourself , Or from CA Got . Following OpenSSL The command is used to merge jetty.key Medium key and jetty.crt Certificate in to jetty.pkcs12 file :
$ openssl pkcs12 -inkey jetty.key -in jetty.crt -export -out jetty.pkcs12Suppose you have a chain of certificates . Use the following method to generate PKCS12:
$ cat example.crt intermediate.crt [intermediate2.crt] ... rootCA.crt > cert-chain.txt
$ openssl pkcs12 -export -inkey example.key -in cert-chain.txt -out example.pkcs12The certificate command must be from server To rootCA. according to RFC2246 pass the civil examinations 7.4.2 Description and narration . OpenSSL Request an exported password, The next step needs a non empty password. Next use keytool load PKCS12 Document entry JSSE keystore:
$ keytool -importkeystore -srckeystore jetty.pkcs12 -srcstoretype PKCS12 -destkeystore keystoreTo configure SslContextFactory
In order to make SSL The certificate is configured to Jetty. We need to inject SslContextFactory Object to the connector SslConnectionFactory, stay Jetty In publication SslConnectionFactory stay jetty-https.xml and jetty-spdy.xml Middle configuration .
because SPDY Can also deal with HTTPS, So you usually need to configure one of the two profiles . But you can also use the command line or edit start.ini file . The following configuration creates a SslContextFactory Example ,ID by ”sslContextFactory”:
<New id="sslContextFactory" class="org.eclipse.jetty.util.ssl.SslContextFactory">
<Set name="KeyStorePath"><Property name="jetty.home" default="." />/etc/keystore</Set>
<Set name="KeyStorePassword">OBF:1vny1zlo1x8e1vnw1vn61x8g1zlu1vn4</Set>
<Set name="KeyManagerPassword">OBF:1u2u1wml1z7s1z7a1wnl1u2g</Set>
<Set name="TrustStorePath"><Property name="jetty.home" default="." />/etc/keystore</Set>
<Set name="TrustStorePassword">OBF:1vny1zlo1x8e1vnw1vn61x8g1zlu1vn4</Set>
</New>Here we use the following jetty released keystore. In order to use your own keystore. You need to update at least two pieces of information : 1)KeyStorePath: You can use your own keystore Replace the... Provided here keystore, Or change the configuration to point to a new file .
Pay attention because keystore It's very important security information . therefore keystore The directory where the file is located should have strict permission restrictions . 2)KeyStorePassword:keystore Of password Can be saved in plain text , Also can do some protection , It can be disturbed , By using Password class. Truststore Usually set to the same keystore, In the verification of client Use... When using a certificate .
keyManagerPassword As password Parameters are passed to KeyManagerFactory.init(…), Suppose there is no keymanagerpassword. Then use keystorepassword replace . Suppose there is no trustmanager, that keystore Be used for truststore,keystorepassword Be used for TrustStorePassword. There's no need to create a new SslContextFactory example , Because in jetty-ssl.xml There is already . stay jetty-ssl.xml Edit path and password Information , And make sure you add the following lines in start.ini in , stay jetty.dump.stop= Then add :
etc/jetty-ssl.xml
etc/jetty-https.xmlYou can also choose to be in jetty-https.xml Middle configuration httpsport:
<Set name=”port”>8443</Set>
Or set it on the command line , such as :
$ java -jar start.jar https.port=8443Disabling/Enabling designated password Group
For example, to avoid BEAST attack , You need to configure a specific set of password Group . This can be done through SslContext.setIncludeCipherSuites(java.lang.String…) Or by SslContext.setExcludeCipherSuites(java.lang.String…) Realization . setIncludeCipherSuites and setExcludeCipherSuites Can be used in JDK Used in password Group name , You can also use regular expressions .
Here are some examples of how to configure RC4password Group . They can all protect server Free from BEAST attack . Contains a set of priority password Group :
<Set name="IncludeCipherSuites">
<Array type="String">
<Item>TLS_RSA_WITH_RC4_128_MD5</Item>
<Item>TLS_RSA_WITH_RC4_128_SHA</Item>
<Item>TLS_ECDHE_RSA_WITH_RC4_128_SHA</Item>
</Array>
</Set>Include all... By using regular expressions RC4password Group :
<Set name="IncludeCipherSuites">
<Array type="String">
<Item>.*RC4.*</Item>
</Array>
</Set>Exclude all non RC4password Group :
<Set name="ExcludeCipherSuites">
<Array type="String">
<Item>SSL_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_DSS_WITH_DES_CBC_SHA</Item>
<Item>SSL_RSA_EXPORT_WITH_RC4_40_MD5</Item>
<Item>SSL_RSA_EXPORT_WITH_DES40_CBC_SHA</Item>
<Item>SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA</Item>
<Item>SSL_DHE_DSS_EXPORT_WITH_DES40_CBC_SHA</Item>
<Item>TLS_DHE_RSA_WITH_AES_128_CBC_SHA256</Item>
<Item>TLS_RSA_WITH_AES_128_CBC_SHA</Item>
<Item>TLS_DHE_RSA_WITH_AES_128_CBC_SHA</Item>
<Item>TLS_RSA_WITH_AES_128_CBC_SHA256</Item>
<Item>TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA</Item>
<Item>TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256</Item>
<Item>TLS_RSA_WITH_3DES_EDE_CBC_SHA</Item>
<Item>TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA</Item>
<Item>TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA</Item>
<Item>RSA_WITH_3DES_EDE_CBC_SHA</Item>
</Array>
</Set>Note that you should give priority to using regular expressions IncludeCipherSuites, This is more conducive to expansion .
To configure SSL Connectors and port
Created above SslContextFactory Instances are injected into SslConnectionFactory example , When receiving a network connection, it will be injected in turn ServerConnector example . For example, the following jetty-https.xml Examples in :
<Call id="sslConnector" name="addConnector">
<Arg>
<New class="org.eclipse.jetty.server.ServerConnector">
<Arg name="server"><Ref refid="Server" /></Arg>
<Arg name="factories">
<Array type="org.eclipse.jetty.server.ConnectionFactory">
<Item>
<New class="org.eclipse.jetty.server.SslConnectionFactory">
<Arg name="next">http/1.1</Arg>
<Arg name="sslContextFactory"><Ref refid="sslContextFactory"/></Arg>
</New>
</Item>
<Item>
<New class="org.eclipse.jetty.server.HttpConnectionFactory">
<Arg name="config"><Ref refid="tlsHttpConfig"/></Arg>
</New>
</Item>
</Array>
</Arg>
<Set name="host"><Property name="jetty.host" /></Set>
<Set name="port"><Property name="jetty.tls.port" default="8443" /></Set>
<Set name="idleTimeout">30000</Set>
</New>
</Arg>
</Call>Be careful SSL The connector port Is set directly in ServerConnector example .
Renew Certificate
Suppose you are updating your configuration with a new certificate ( Maybe because the old certificate has expired ). You just have to follow “ load keys and certificates” Section describes the process of loading a new certificate . Suppose you use PKCS12 Method to import the original key and certificate, You should use aliases “1” instead of “jetty”, Because that's PKCS12 Process into keystore Another name for .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116449.html Link to the original text :https://javaforall.cn
边栏推荐
- Measure the height of the building
- Mysql子查询关键字的使用方式(exists)
- What are the official stock trading apps in the country? Is it safe to use
- Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
- 恶魔奶爸 A3阶段 近常速语流初接触
- How to choose fund products? What fund is suitable to buy in July 2022?
- Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
- SQL注入报错注入函数图文详解
- 解决使用uni-app MediaError MediaError ErrorCode -5
- Referrer和Referrer-Policy简介
猜你喜欢

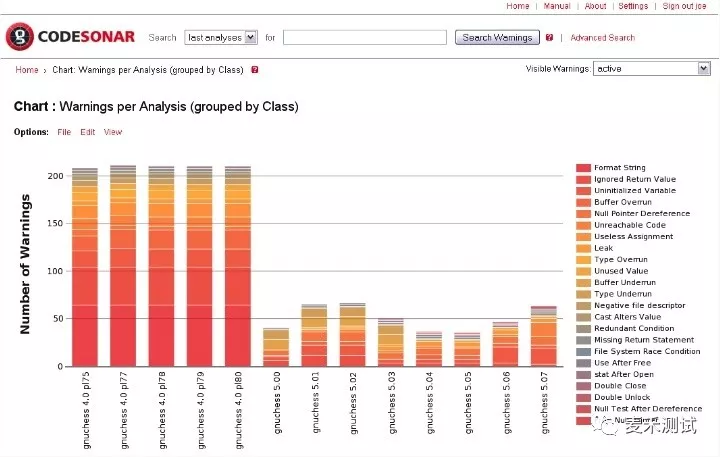
Helix QAC 2020.2新版静态测试工具,最大限度扩展了标准合规性的覆盖范围

OneSpin | 解决IC设计中的硬件木马和安全信任问题
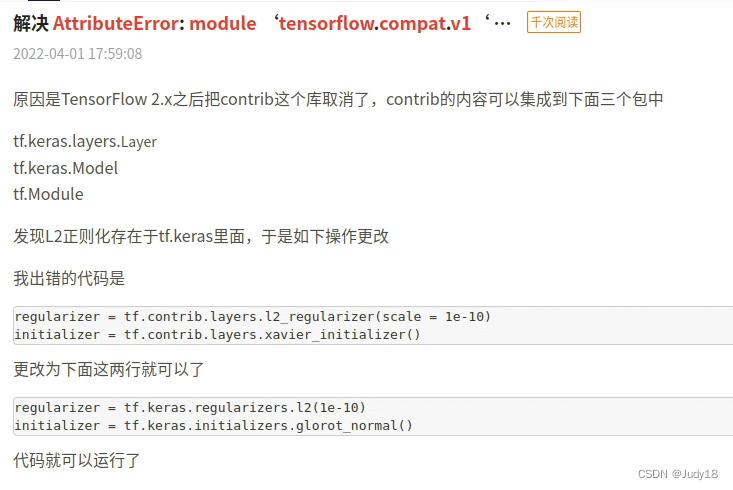
Tensorflow2.x下如何运行1.x的代码

如何满足医疗设备对安全性和保密性的双重需求?
Apifox interface integrated management new artifact
【C语言】指针进阶---指针你真的学懂了吗?
![[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System](/img/76/b725788272ba2dcdf866b28cbcc897.jpg)
[paper reading] maps: Multi-Agent Reinforcement Learning Based Portfolio Management System
CodeSonar通过创新型静态分析增强软件可靠性
Mongodb learn from simple to deep
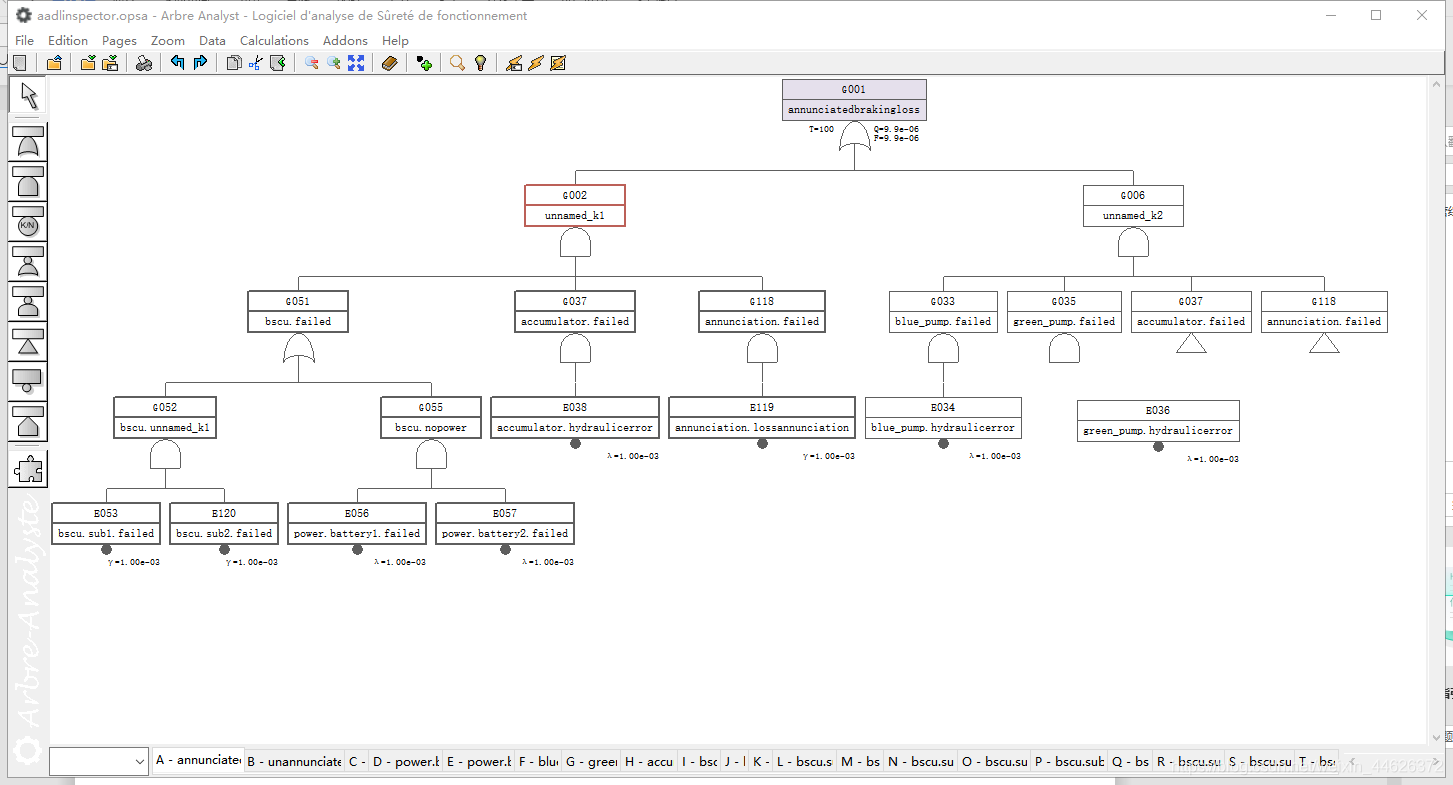
AADL Inspector 故障树安全分析模块
随机推荐
Is it safe to open a stock account at present? Can I open an account online directly.
浅解ARC中的 __bridge、__bridge_retained和__bridge_transfer
【奖励公示】第22期 2022年6月奖励名单公示:社区明星评选 | 新人奖 | 博客同步 | 推荐奖
Implement secondary index with Gaussian redis
写一下跳表
H3C s7000/s7500e/10500 series post stack BFD detection configuration method
FatMouse&#39; Trade(杭电1009)
数值法求解最优控制问题(〇)——定义
CodeSonar如何帮助无人机查找软件缺陷?
Lex & yacc of Pisa proxy SQL parsing
Object-C programming tips timer "suggestions collection"
论文解读(ValidUtil)《Rethinking the Setting of Semi-supervised Learning on Graphs》
最新版本的CodeSonar改进了功能安全性,支持MISRA,C ++解析和可视化
Introduction to referer and referer policy
HOJ 2245 浮游三角胞(数学啊 )
Cantata9.0 | new features
Spark judges that DF is empty
Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
Le capital - investissement est - il légal en Chine? C'est sûr?
Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)