当前位置:网站首页>Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
Onespin | solve the problems of hardware Trojan horse and security trust in IC Design
2022-07-07 20:27:00 【Maihexong】
stride across 5G, Artificial intelligence , The Internet of things and the automotive sector 40 Several organizations have expressed the importance of trust and security dilemmas .
Electronic systems have increasingly become the core of products and services . From power plants to cars , Medical equipment to the plane , From smart phones to home appliances , Complex electronic systems have achieved unprecedented Automation , performance , Safety and security level . The integrated circuit (IC) It is the foundation of electronic system , And the most important thing is , Need to ensure that they operate in full compliance with specifications and Certification , In this regard, it is trustworthy . but IC The design of the , Production and distribution are vulnerable to attacks by malicious agents , These malicious agents may penetrate devices with poor performance and reliability , Even infiltrate into the hardware Trojan horse , Other hidden functions designed for malicious purposes .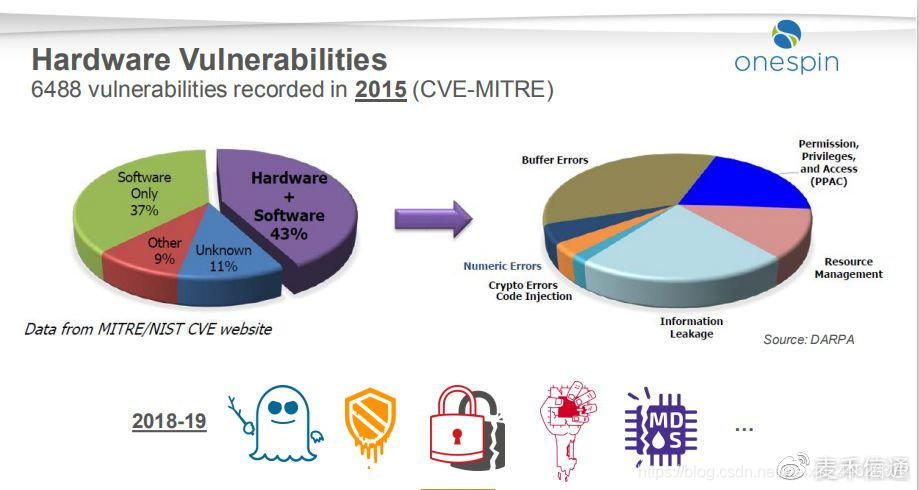
A well-designed hardware Trojan horse , Can respond to triggers known to the attacker , Thus causing significant damage . It may expose “ Security ” data , Cause serious product failure , Even damage the chip . In modern times , Highly configurable hardware is a backdoor 、 Time bomb 、 Provide a good hiding place for the switch to stop or degrade . Like a Trojan horse program being inserted into a third party IP And threats in the design and implementation steps before production , It is increasingly attracting extensive attention in the hardware industry . Networked driverless cars , Medical equipment , A smart phone , Defense and aerospace systems , nuclear power plant ,5G The Internet , Internet of things devices and cloud computing , Everything is at risk here .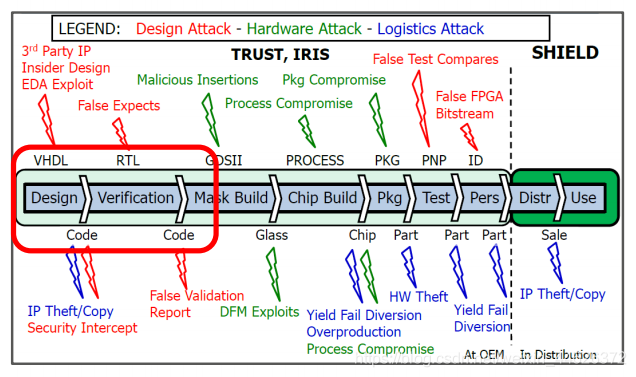
The company is obliged to ensure that electronic equipment is protected from security attacks that may cause great harm .OneSpin Hardware trust and security challenges illustrate , Face hidden in the whole IC Trojans in the development phase , How fragile the design is , meanwhile , It also tells us how to fight it .
 About OneSpin Solutions for
About OneSpin Solutions for
OneSpin President and CEO Raik Brinkmann mention : Now more and more companies realize that , The importance of protecting hardware design from trust and security risks . The loopholes left in the design , Whether unintentional or malicious , Can have disastrous consequences . Be able to fully detect these in the design “ Loophole ”, For delivering security to the market , Reliable and trustworthy equipment is essential . As IC Part of integrity , In terms of ensuring trust and security at the hardware level ,OneSpin The technical services provided have always been at the forefront of the industry .”
More details and white papers :http://www.softtest.cn
边栏推荐
- With st7008, the Bluetooth test is completely grasped
- 微服务远程Debug,Nocalhost + Rainbond微服务开发第二弹
- 华为CE交换机下载文件FTP步骤
- Is it safe to open a stock account at present? Can I open an account online directly.
- How C language determines whether it is a 32-bit system or a 64 bit system
- 取两个集合的交集
- Solve the problem of incomplete display around LCD display of rk3128 projector
- Implement secondary index with Gaussian redis
- Lingyun going to sea | yidiantianxia & Huawei cloud: promoting the globalization of Chinese e-commerce enterprise brands
- AADL Inspector 故障树安全分析模块
猜你喜欢
CodeSonar通过创新型静态分析增强软件可靠性
H3C S7000/S7500E/10500系列堆叠后BFD检测配置方法

H3C s7000/s7500e/10500 series post stack BFD detection configuration method

OneSpin | 解决IC设计中的硬件木马和安全信任问题
Cantata9.0 | 全 新 功 能
让这个CRMEB单商户微信商城系统火起来,太好用了!
Network principle (1) - overview of basic principles
最新版本的CodeSonar改进了功能安全性,支持MISRA,C ++解析和可视化
With st7008, the Bluetooth test is completely grasped
一键部署Redis任意版本
随机推荐
Phoenix JDBC
Micro service remote debug, nocalhost + rainbow micro service development second bullet
开发那些事儿:Go加C.free释放内存,编译报错是什么原因?
使用 BR 备份 TiDB 集群数据到 Azure Blob Storage
九度 1201 -二叉排序数遍历- 二叉排序树「建议收藏」
TS quick start - Generic
Airiot helps the urban pipe gallery project, and smart IOT guards the lifeline of the city
kubernetes之创建mysql8
Lingyun going to sea | saihe & Huawei cloud: jointly help the sustainable development of cross-border e-commerce industry
guava多线程,futurecallback线程调用不平均
4G设备接入EasyGBS平台出现流量消耗异常,是什么原因?
How to choose financial products? Novice doesn't know anything
【解决】package ‘xxxx‘ is not in GOROOT
怎样用Google APIs和Google的应用系统进行集成(1)—-Google APIs简介
恢复持久卷上的备份数据
微服务远程Debug,Nocalhost + Rainbond微服务开发第二弹
字符串中数据排序
取两个集合的交集
One click deployment of any version of redis
想杀死某个端口进程,但在服务列表中却找不到,可以之间通过命令行找到这个进程并杀死该进程,减少重启电脑和找到问题根源。