当前位置:网站首页>[web source code code code audit method] audit skills and tools
[web source code code code audit method] audit skills and tools
2022-07-05 03:36:00 【Black zone (rise)】
Catalog
1.2、 There are binary programs :
1.3、 Source code 、 Binary program :
3.1、 Sensitive keyword backtracking parameter passing
3.3、 Modeling sensitive function points
3.5、 Restore security boundaries
5、 ... and 、 Large source code
6.1、Seay Source code audit system
One 、 Audit situation :
1.1、 Source code :
It usually does not include a complete compilation and test environment , And lack of necessary key dependent components , It's often impossible to build a running program
Generally, we can only use static analysis to audit
1.2、 There are binary programs :
Such as APK、EXE、jar package 、IoT System firmware, etc
The audit is usually carried out through dynamic analysis and reverse engineering
1.3、 Source code 、 Binary program :
Audit provides the most favorable access , Usually the goal is open source software , Contains a complete build environment and dependencies
1.4、 Complete black box :
Blind test can only be carried out through external interface ( More common )
Two 、 influence :
2.1、 Code language :
C/C++ This memory insecure language needs to pay more attention to the underlying details
Java、Python And other memory safe languages pay more attention to the implementation of upper logic ;
2.2、 Code style. :
Clean and tidy 、 Clearly annotated projects usually take less time to audit than other projects
3、 ... and 、 Audit ideas
3.1、 Sensitive keyword backtracking parameter passing
Most vulnerabilities are caused by improper use of functions
Search for corresponding sensitive keywords , You can quickly tap the desired vulnerabilities , Directional excavation , Efficient 、 High-quality
But because the code is not read through , Not enough in-depth understanding of the overall architecture of the program , It will take time to locate and exploit vulnerabilities , And logic vulnerability mining cannot cover
3.2、 Interface Analysis
Find controllable variables and their functions , Forward tracking variable transfer process
Data entry point , Parameters such as functions 、 Environmental variables, etc , Look for security vulnerabilities that can be triggered by malicious input
3.3、 Modeling sensitive function points
Search in blocks according to function points
File upload function 、 Payment function ……
The behavior of the module is restored by modeling the abstract behavior of the module , And look for potential logical and functional vulnerabilities
3.4、 Full text key code
Function set file : Public function file , By opening the index.php Or find some functional files
The configuration file : Generally including config keyword , There will be configuration options 、 Database and other configuration information
Secure filter files : Generally including filter、safe、check Other key words
index file : Program entry , Understand the architecture of the whole program 、 Running process 、 Files included in
3.5、 Restore security boundaries
Check the code by analyzing all safety related checksums
Restore the security boundary preset by the developer or security architect , So as to further audit the restored security boundary , Build a threat model of actual attack
Four 、 Small source code
The amount of code is generally small , It is relatively easy to find loopholes
4.1、 Audit steps :
(1) Input point : Find each input point .
(2) Protective measures : Find the filter for the input and try to bypass .
(3) Function vulnerability : Find the function that handles the input and check for vulnerabilities .
(4) utilize : Find the vulnerability and make the best use of it .
5、 ... and 、 Large source code
It's usually right CMS Type framework for auditing , The main problem is the need to quickly locate vulnerabilities from a large amount of code
5.1、 Audit steps :
(1) Look for the hazard function
(2) Go back up , Find available input points
(3) Bypass filtering for input points
(4) Construct trigger vulnerability
6、 ... and 、 Audit tools
6.1、Seay Source code audit system
download :
link :https://pan.baidu.com/s/1H51ez9BrYohDP4hXHJLReA?pwd=bgz1
Extraction code :bgz1
6.2、RIPS
link :https://pan.baidu.com/s/14RWI64sU8LU-z9qUeVUzBg?pwd=yot6
Extraction code :yot6
边栏推荐
- [105] Baidu brain map - Online mind mapping tool
- Sqoop安装
- Why are there fewer and fewer good products produced by big Internet companies such as Tencent and Alibaba?
- Pat class a 1162 postfix expression
- Share the newly released web application development framework based on blazor Technology
- Delphi read / write JSON format
- LeetCode 234. Palindrome linked list
- SQL injection exercise -- sqli Labs
- In MySQL Association query, the foreign key is null. What if the data cannot be found?
- What is the most effective way to convert int to string- What is the most efficient way to convert an int to a String?
猜你喜欢
Blue Bridge Cup single chip microcomputer -- PWM pulse width modulation
1.五层网络模型
Smart pointer shared_ PTR and weak_ Difference of PTR
![Yuancosmic ecological panorama [2022 latest]](/img/55/0901109e4c865b77137610b4fe0624.jpg)
Yuancosmic ecological panorama [2022 latest]
![[groovy] string (string injection function | asBoolean | execute | minus)](/img/ea/bf1e6aa713cf54e29653e35b164560.jpg)
[groovy] string (string injection function | asBoolean | execute | minus)
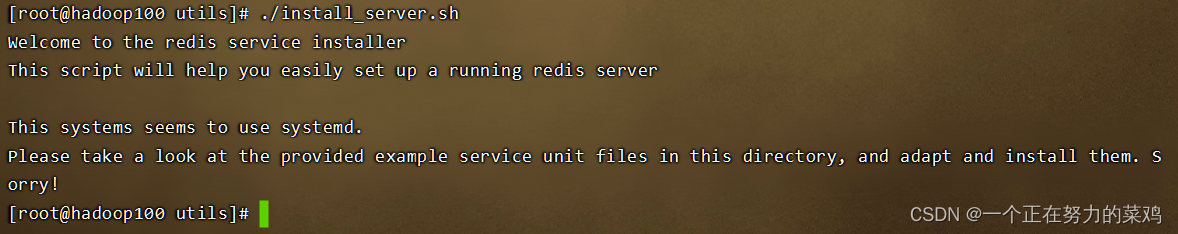
Linux安装Redis
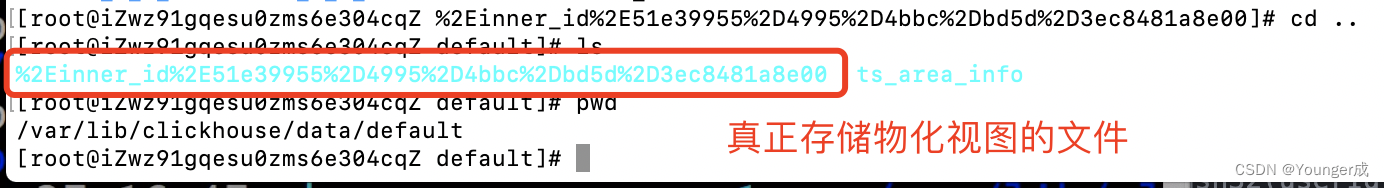
Clickhouse物化视图
v-if VS v-show 2.0
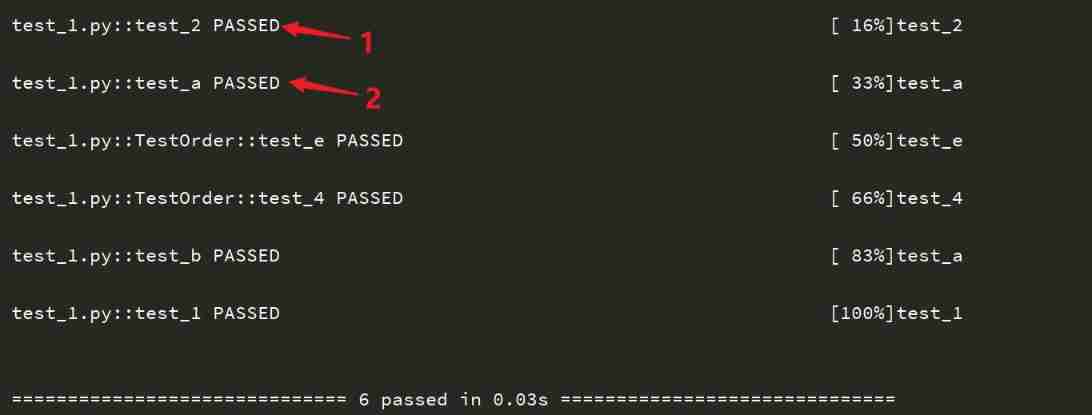
Pytest (4) - test case execution sequence
Redis6-01nosql database
随机推荐
Talk about the SQL server version of DTM sub transaction barrier function
Watch the online press conference of tdengine community heroes and listen to TD hero talk about the legend of developers
Three line by line explanations of the source code of anchor free series network yolox (a total of ten articles, which are guaranteed to be explained line by line. After reading it, you can change the
Machine learning experiment report 1 - linear model, decision tree, neural network part
LeetCode 237. Delete nodes in the linked list
When sqlacodegen generates a model, how to solve the problem that the password contains special characters?
Simple use of devtools
Class inheritance in C #
There is a question about whether the parallelism can be set for Flink SQL CDC. If the parallelism is greater than 1, will there be a sequence problem?
Hot knowledge of multithreading (I): introduction to ThreadLocal and underlying principles
Leetcode92. reverse linked list II
Devtools的简单使用
[groovy] string (string splicing | multi line string)
What is the most effective way to convert int to string- What is the most efficient way to convert an int to a String?
The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
Yuancosmic ecological panorama [2022 latest]
How to learn to get the embedding matrix e # yyds dry goods inventory #
Quick start of UI component development of phantom engine [umg/slate]
Why do some programmers change careers before they are 30?
Kuboard