当前位置:网站首页>What is CSRF (Cross Site Request Forgery)?
What is CSRF (Cross Site Request Forgery)?
2022-07-06 08:29:00 【Liu Chu, Ge Nian】
1. CSRF What is it? ?
CSRF(Cross-site request forgery), Also known as :one click attack/session riding, Chinese name : Cross-site request forgery , Abbreviation for :CSRF/XSRF. It is a kind of coercion that users are currently logged in Web An attack method that performs unintended operations on an application . With cross site scripting (XSS) comparison ,XSS Using the user's trust in the designated website ,CSRF Using the trust of the website to the user's web browser .
1.1 CSRF Attack details
Generally speaking , The attacker forges the user's browser request , Send it to a website that a user has authenticated to visit , Make the target website receive and mistakenly think it is the real operation of the user to execute the command . It's often used to steal accounts 、 Transfer accounts 、 Send false messages, etc . The attacker uses the website to verify the request vulnerability to achieve such an attack , The website can confirm that the request comes from the user's browser , But it can't verify whether the request originates from the operation behavior under the real intention of the user .
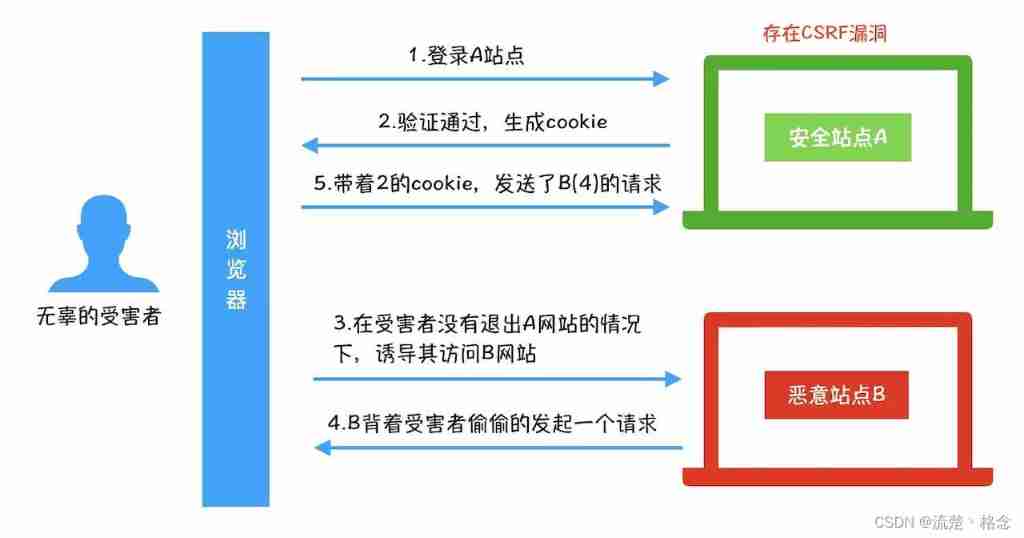
The following specific attack examples :
among Web A For existence CSRF Loopholes in the website ,Web B Malicious websites built for attackers ,User C by Web A Legitimate users of the site .
CSRF The attack principle and process are as follows :
- user C Open the browser , Visit trusted sites A, Enter the user name and password to log in to the website A;
- After the user information has been verified , Website A produce Cookie Information and return it to the browser , At this time, the user logs into the website A success , Can send request to website normally A;
- The user did not exit the website A Before , In the same browser , Open one TAB Page visit website B;
- Website B After receiving the user's request , Return some offensive code , And send a request to visit a third-party site A;
- After the browser receives the attack code , According to the website B Request , Carry... Without the user's knowledge Cookie Information , To the website A Request . Website A I don't know that the request was actually made by B Sponsored , So according to the user C Of Cookie Information to C Permission to process the request , Lead from website B The malicious code was executed .
2. CSRF Vulnerability detection
testing CSRF Loophole is a more complicated work , The easiest way is to grab a normal request packet , Get rid of Referer Field and resubmit , If the submission is still valid , So it's basically certain that there is CSRF Loophole .
As for CSRF The research of loopholes is going deep , There's been a constant stream of specific targets for CSRF Vulnerability detection tools , Such as CSRFTester,CSRF Request Builder etc. .
With CSRFTester Tools, for example ,CSRF The testing principle of vulnerability detection tool is as follows :
Use CSRFTester When testing , First, we need to grab all the links we have visited in the browser and all the forms and other information , And then through the CSRFTester Modify the corresponding forms and other information , To resubmit , This is equivalent to a fake client request . If the modified test request is accepted by the web server successfully , It means that there is CSRF Loophole , Of course, this tool can also be used to CSRF attack .
3. defense CSRF attack :
Current defense CSRF There are three main strategies to attack :
verification HTTP Referer Field ;
Add... To the request address token And verify ;
stay HTTP Custom properties in the header and verify .
Here is a brief analysis of these three defenses CSRF Attack methods :
3.1 verification HTTP Referer Field
according to HTTP agreement , stay HTTP There is a field in the header called Referer, It records the time to HTTP The source address of the request . In general , Requests to access a security restricted page come from the same website , For example, you need to visit http://bank.example/withdraw?account=bob&amount=1000000&for=Mallory, Users must log in first bank.example, Then trigger the transfer event by clicking the button on the page .
At this time , The transfer request Referer The value will be on the page where the transfer button is located URL, Usually with bank.example Address at the beginning of the domain name . And if the hackers want to implement the bank website CSRF attack , He can only build requests on his own website , When the user sends the request to the bank through the hacker's website , The requested Referer It's pointing to hackers' own websites .
therefore , Be defensive CSRF attack , The bank website only needs to verify each transfer request Referer value , If so bank.example Domain name at the beginning , It means that the request is from the bank's website , It's legal. . If Referer If it's another website , It could be hackers CSRF attack , Refuse the request .
3.1.1 advantage :
The obvious advantage of this method is its simplicity , The average developer of a website doesn't have to worry about CSRF A loophole in the , Just add an interceptor to all security sensitive requests at the end to check Referer The value of . Especially for the current system , There is no need to change any existing code and logic of the current system , There is no risk , Very convenient .
3.1.2 shortcoming :
However , This method is not foolproof .Referer The value of is provided by the browser , although HTTP There are clear requirements in the agreement , But every browser for Referer There may be differences in the specific implementation of , There's no guarantee that the browser itself doesn't have security holes . Use validation Referer The method of value , It is to rely on the third party for security ( Browser ) To protect , In theory , It's not safe . in fact , For some browsers , such as IE6 or FF2, At present, there are some methods that can be tampered with Referer value . If bank.example Site support IE6 browser , Hackers can put the user's browser Referer The value is set to bank.example Address at the beginning of the domain name , In this way, we can pass the verification , So as to carry out CSRF attack .
Even with the latest browsers , Hackers can't tamper with Referer value , There are still problems with this method . because Referer Value will record the user's access source , Some users think it would infringe their privacy rights , Especially some organizations are worried about Referer Value will leak some information in the internal network of the organization to the external network . therefore , The user can set up the browser to not provide any more when sending the request Referer. When they visit the bank's website normally , The website will not have Referer It's worth it CSRF attack , Deny access to legitimate users .
But in some cases , For example, the website itself provides payment API service , It is not suitable for such protection , It will be all false positives .
3.2 Add... To the request address token And verify
CSRF The attack was successful , Because hackers can completely fake users' requests , All user authentication information in this request exists in cookie in , So hackers can directly use users' own... Without knowing the authentication information cookie To pass security verification .
Resist CSRF, The key is to put information in the request that the hacker can't forge , And the information does not exist in cookie In . Can be in HTTP Was added a request in the form of randomly generated parameter token, And build an interceptor on the server side to verify this token, If not in the request token perhaps token The content is not correct , Think it might be CSRF Attack and reject the request .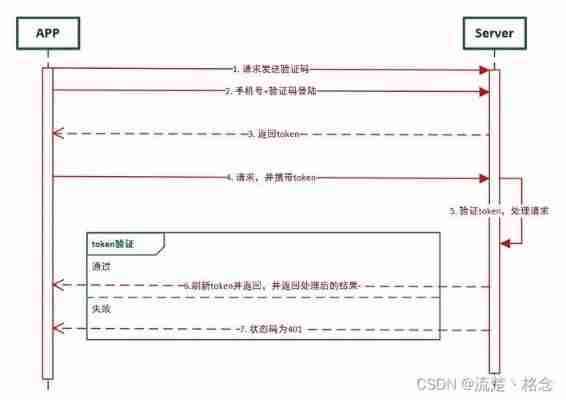
This method is better than inspection Referer Be safe ,token It can be produced and put on after the user logs session In , And then at every request put token from session Took out , With... In the request token compare , But the difficulty of this method is how to put token Add the request as a parameter . about GET request ,token Will be attached to the request address , such URL It becomes http://url?csrftoken=tokenvalue.
And for POST The request for , To be in form At the end of the sentence, add <input type=”hidden” name=”csrftoken” value=”tokenvalue”/>, This way token Added the request as a parameter . however , In a website , There are so many places to accept requests , Add... To every request token It's very troublesome , And it's easy to miss , The usual way to do this is to load each page , Use javascript Traverse the whole dom Trees , about dom All of the a and form Add... After the label token. This solves most of the requests , But for the dynamically generated html Code , This method has no effect , It also requires the programmer to manually add token.
Another disadvantage of this method is that it is difficult to guarantee token Own safety . Especially in some forums and other websites that support users to publish their own content , Hackers can post the address of their own website on it . Because the system will also add token, Hackers can get this on their own websites token, And we can start it right away CSRF attack . To avoid that , The system can add token Add a judgment , If this link is linked to your own site , Just add token, If it's going to the Internet, it's not going to add . however , Even if this csrftoken Not attached to the request as a parameter , Hackers' websites can also be accessed through Referer To get this token It's worth starting CSRF attack . This is also some users like to close the browser manually Referer The reason for the function .
3.3 stay HTTP Custom properties in the header and verify
This method is also used token And verify that , Different from the previous method , It's not about token In the form of parameters HTTP In request , But put it in HTTP In the custom attribute in the header . adopt XMLHttpRequest This class , You can add... To all such requests at once csrftoken This HTTP Head properties , And put token Value in it . This solves the problem of adding token The inconvenience of , meanwhile , adopt XMLHttpRequest The requested address will not be recorded in the browser's address bar , And don't worry about it token Through Referer Leaked to other websites .
However, the limitation of this method is very large .XMLHttpRequest Requests are usually used for Ajax Method for local asynchronous refresh of the page , Not all requests are suitable to be initiated with this class , And the page obtained by such request cannot be recorded by the browser , To move forward , back off , Refresh , Collection and other operations , Inconvenience to users . in addition , For not doing CSRF In terms of protected legacy systems , Use this method to protect , Change all requests to XMLHttpRequest request , It's almost like rewriting the entire site , The price is certainly unacceptable .
边栏推荐
- Image fusion -- challenges, opportunities and Countermeasures
- Migrate data from SQL files to tidb
- From monomer structure to microservice architecture, introduction to microservices
- 指针进阶---指针数组,数组指针
- 【MySQL】数据库的存储过程与存储函数通关教程(完整版)
- vulnhub hackme: 1
- Ruffian Heng embedded bimonthly, issue 49
- Nacos Development Manual
- synchronized 解决共享带来的问题
- Grayscale upgrade tidb operator
猜你喜欢
JVM performance tuning and practical basic theory - Part 1
2022.02.13 - NC002. sort
Online yaml to CSV tool
Sort according to a number in a string in a column of CSV file
Zhong Xuegao, who cannot be melted, cannot escape the life cycle of online celebrity products
JVM performance tuning and practical basic theory - Part 1
Use Alibaba icon in uniapp
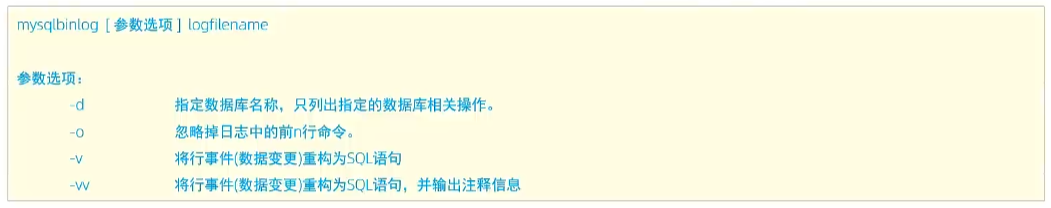
【MySQL】日志
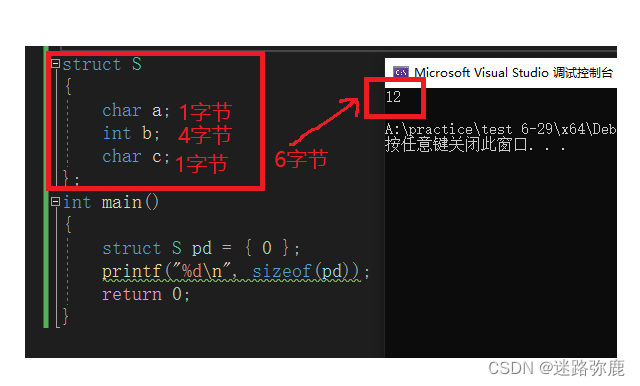
C language custom type: struct

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
随机推荐
pcd转ply后在meshlab无法打开,提示 Error details: Unespected eof
2022.02.13 - NC001. Reverse linked list
Introduction to number theory (greatest common divisor, prime sieve, inverse element)
C语言自定义类型:结构体
指针和数组笔试题解析
Colorlog结合logging打印有颜色的日志
2. File operation - write
Unified ordering background interface product description Chinese garbled
Restore backup data on S3 compatible storage with tidb lightning
2022.02.13 - 238. Maximum number of "balloons"
Research Report on Market Research and investment strategy of microcrystalline graphite materials in China (2022 Edition)
matplotlib. Widgets are easy to use
MySQL learning record 07 index (simple understanding)
Yyds dry goods inventory three JS source code interpretation eventdispatcher
On the day of resignation, jd.com deleted the database and ran away, and the programmer was sentenced
[MySQL] database stored procedure and storage function clearance tutorial (full version)
Deep learning: derivation of shallow neural networks and deep neural networks
Modify the video name from the name mapping relationship in the table
1202 character lookup
C language - bit segment