当前位置:网站首页>Personal developed penetration testing tool Satania v1.2 update
Personal developed penetration testing tool Satania v1.2 update
2022-07-05 05:32:00 【Ba1_ Ma0】
Satania v1.2

Github Project address :
https://github.com/baimao-box/satania
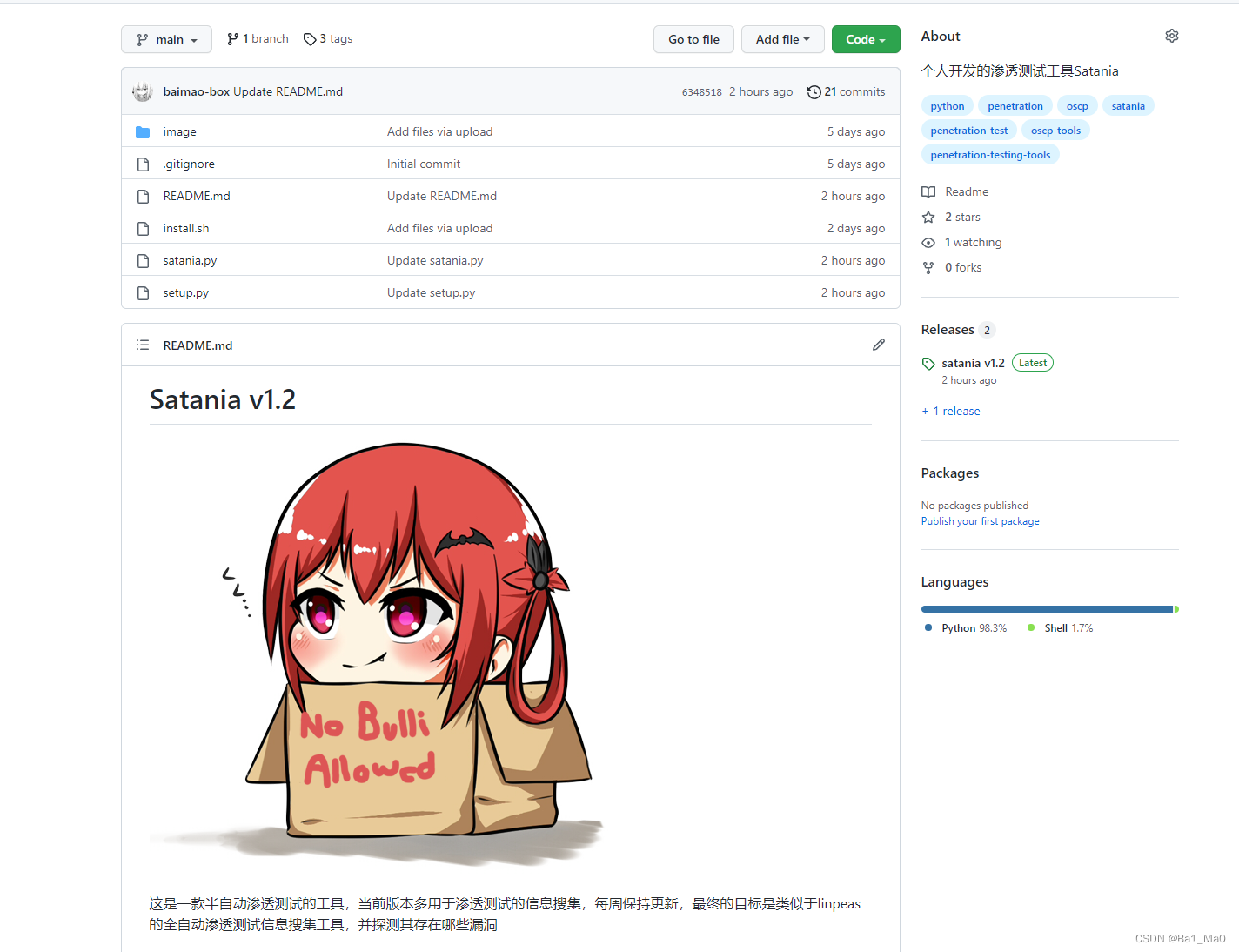
This is a semi-automatic penetration testing tool , The current version is mainly used for information collection of penetration test , Keep updated weekly , The ultimate goal is something like linpeas Automatic penetration test information collection tool , And detect what vulnerabilities exist
Major updates
BUG Repair
smb Specify an account to log in to the folder
Interface optimization , Program optimization
Generate shellcode And connect
Joined the WPScan Tools
install
git library :
git clone https://github.com/baimao-box/satania.git
After downloading the tool , Enter the directory where the tool exists to install
chmod 777 setup.py
python3 setup.py

It takes a few minutes , During this period, you need to manually select some things , The default can be
After installation , Will prompt whether to install searchsploit Tools , This tool is very big , So ask here , If the network is good, you can install
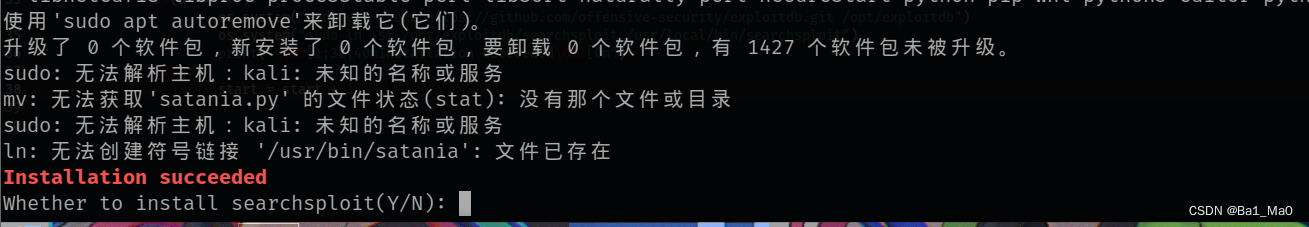
Then directly enter satania You can run the tool
Tool module introduction
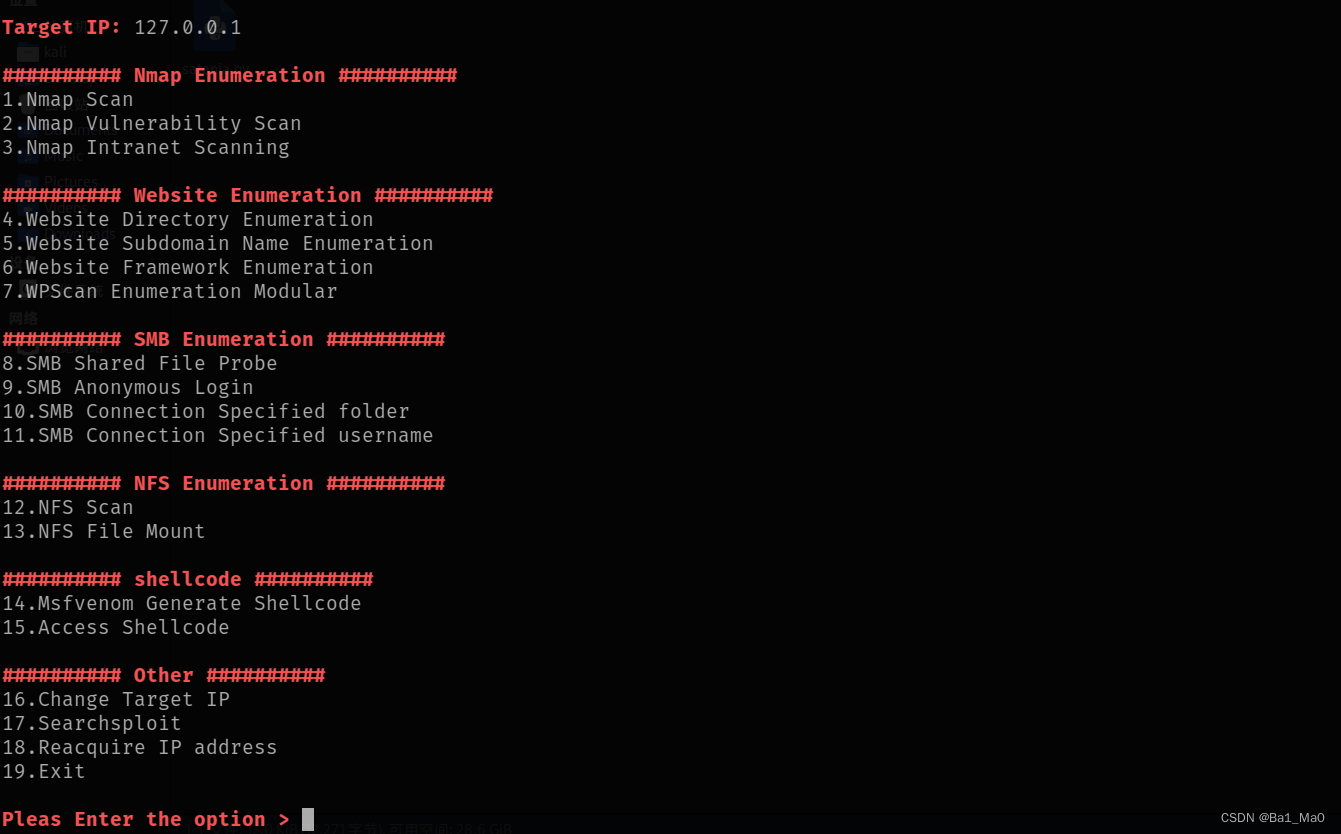
nmap enumeration
1.nmap enumeration
2.nmap Regular vulnerability scanning
3.nmap Intranet survival host detection
Site enumeration
4. Website root directory file scanning
5. Website subdomain name enumeration
6. Website framework enumeration
7.wpscan enumeration
1.WPScan Vulnerability scanning
2.WPScan User name enumeration
3.WPScan Account blasting
smb enumeration
8.smb Shared directory enumeration
9. Anonymous logins
10.smb Specify folder login
11.smb Specify the user name to log in
MFS enumeration
12.nfs scanning
13.nfs Local mount
shellcode
14.msfvenom Generate shellcode
1.aspx Of shellcode
2.php Of shellcode
3.exe Of shellcode
4.netcat monitor
5. Change the local settings ip And port
15. Connect the uploaded shellcode
other
16. Change target ip
17.searchsploit
18. Get this machine again IP
19. sign out
During the execution of the command , It still works linux command
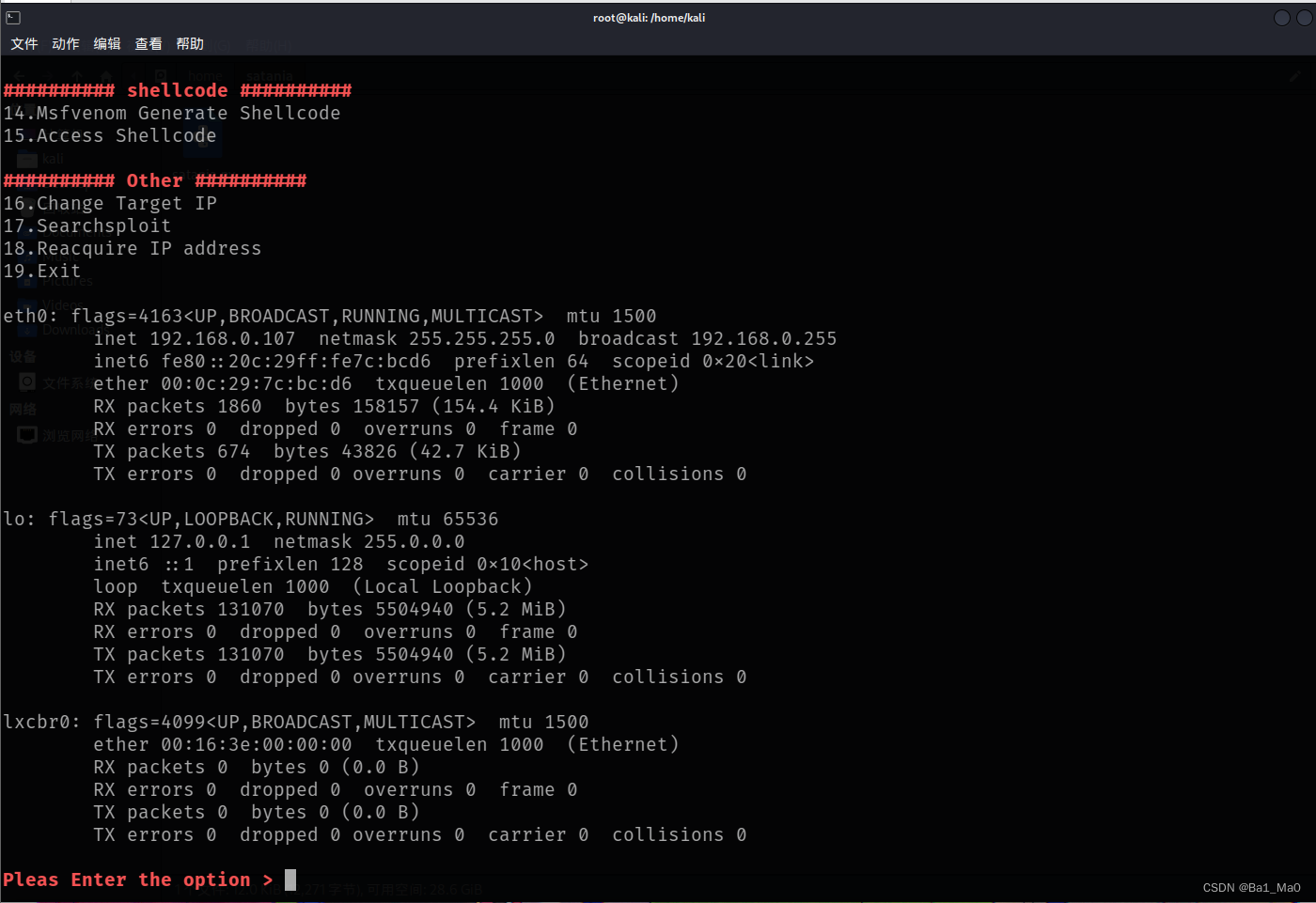
Some demos for this update
Update as follows :
BUG Repair
smb Specify an account to log in to the folder
Interface optimization , Program optimization
Generate shellcode And connect
Joined the WPScan Tools
Use wpscan Enumeration module , Perform default vulnerability scanning
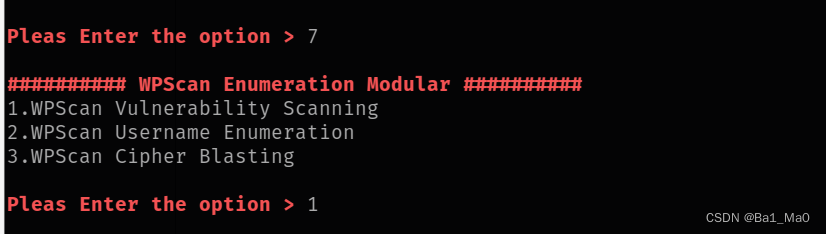
Here you will be asked to enter api token
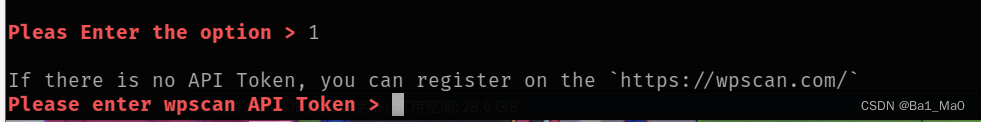
We usually use wpscan when , Each scan requires input api token, Using this tool , You can put your api token Store it , Then the call does not need to enter
Then you can perform various scans
We enter msfvenom modular
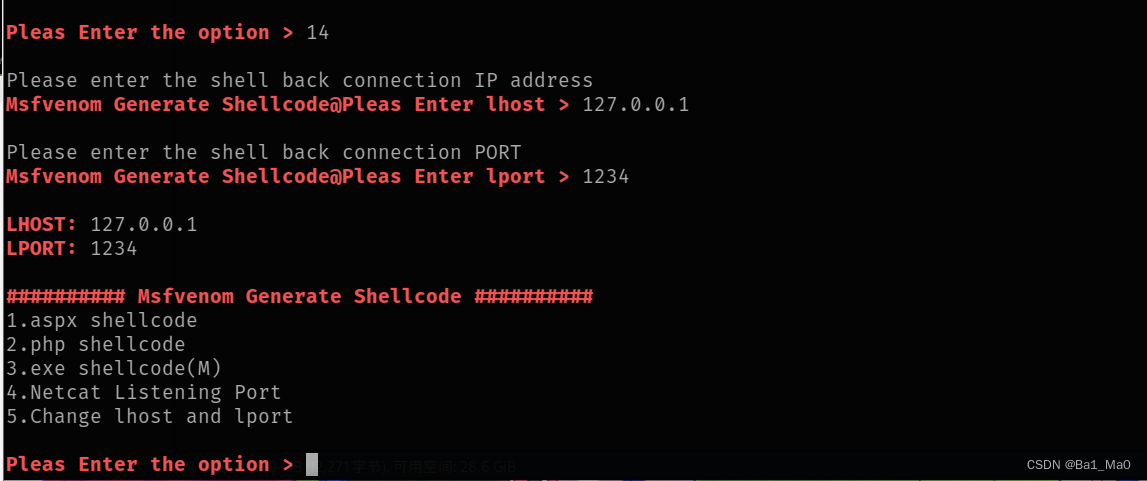
The tool will prompt you to enter local ip And listening port , For the following shellcode Generate , Now we generate a shellcode
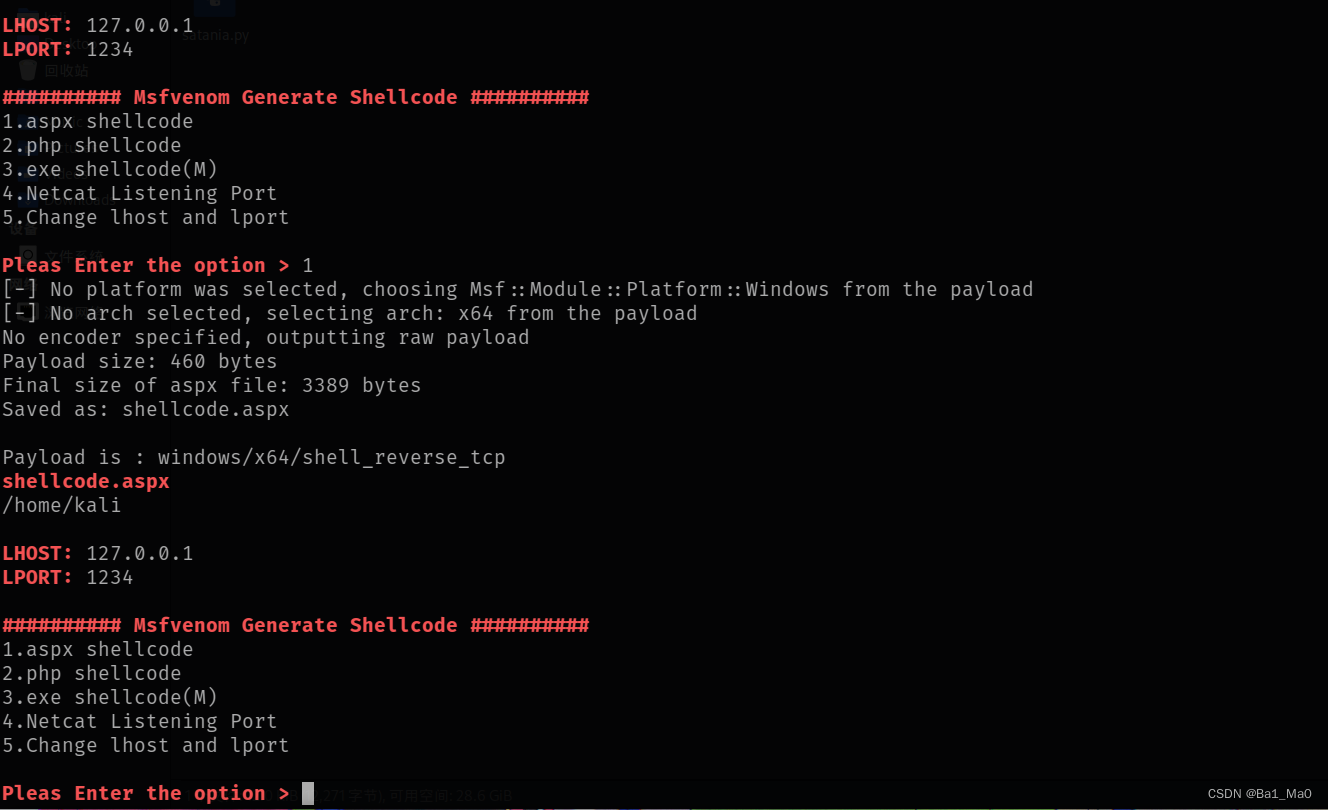
The tool will enter the file name , Storage address , And the use of payload
This update will execute linux The command is placed below
Keep updating every week
边栏推荐
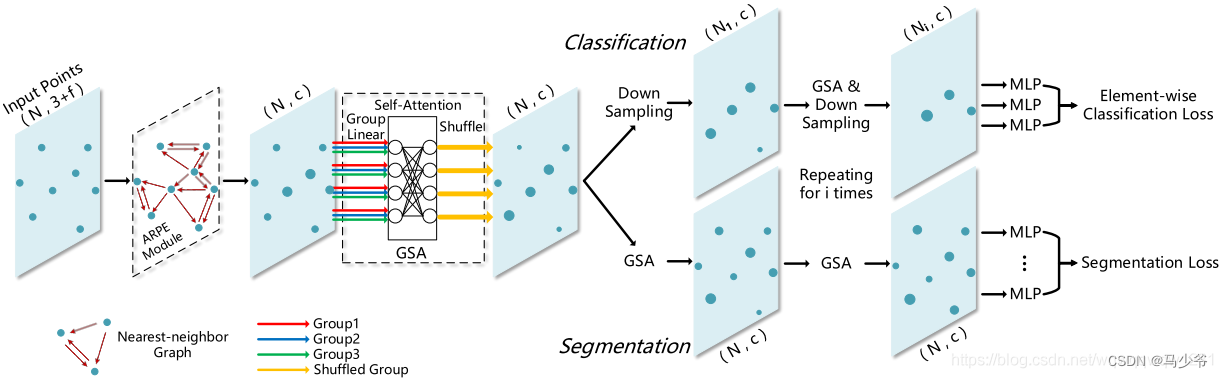
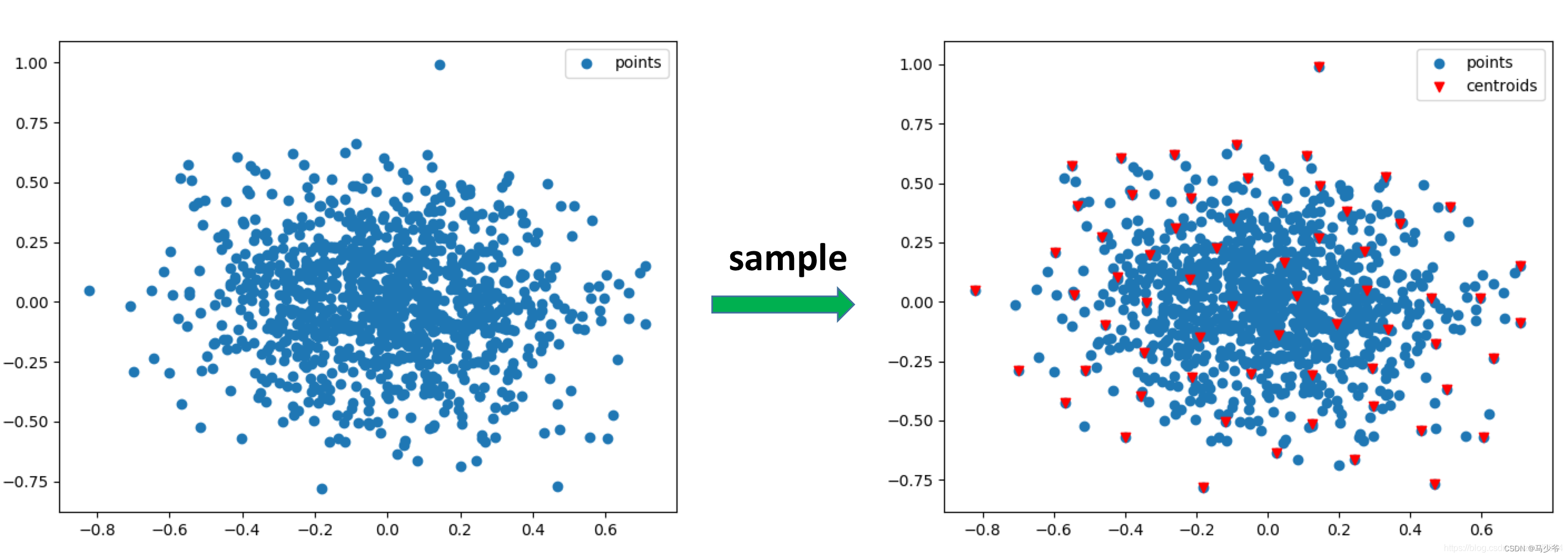
- Improvement of pointnet++
- SAP method of modifying system table data
- 26、 File system API (device sharing between applications; directory and file API)
- Introduction to tools in TF-A
- Double pointer Foundation
- sync.Mutex源码解读
- 利用HashMap实现简单缓存
- 游戏商城毕业设计
- Zzulioj 1673: b: clever characters???
- In this indifferent world, light crying
猜你喜欢
Sword finger offer 53 - I. find the number I in the sorted array
On-off and on-off of quality system construction
Romance of programmers on Valentine's Day
SAP method of modifying system table data
![[interval problem] 435 Non overlapping interval](/img/a3/2911ee72635b93b6430c2efd05ec9a.jpg)
[interval problem] 435 Non overlapping interval
![[to be continued] [UE4 notes] L1 create and configure items](/img/20/54ba719be2e51b7db5b7645b361e26.jpg)
[to be continued] [UE4 notes] L1 create and configure items
Improvement of pointnet++
Pointnet++ learning
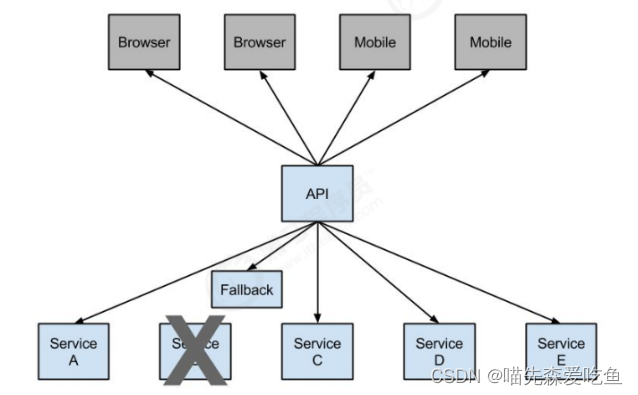
Service fusing hystrix
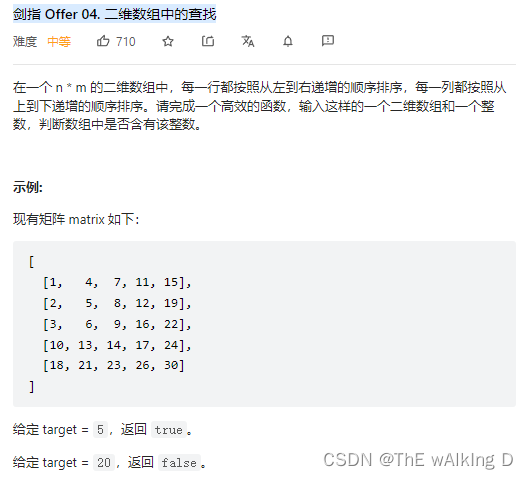
Sword finger offer 04 Search in two-dimensional array
随机推荐
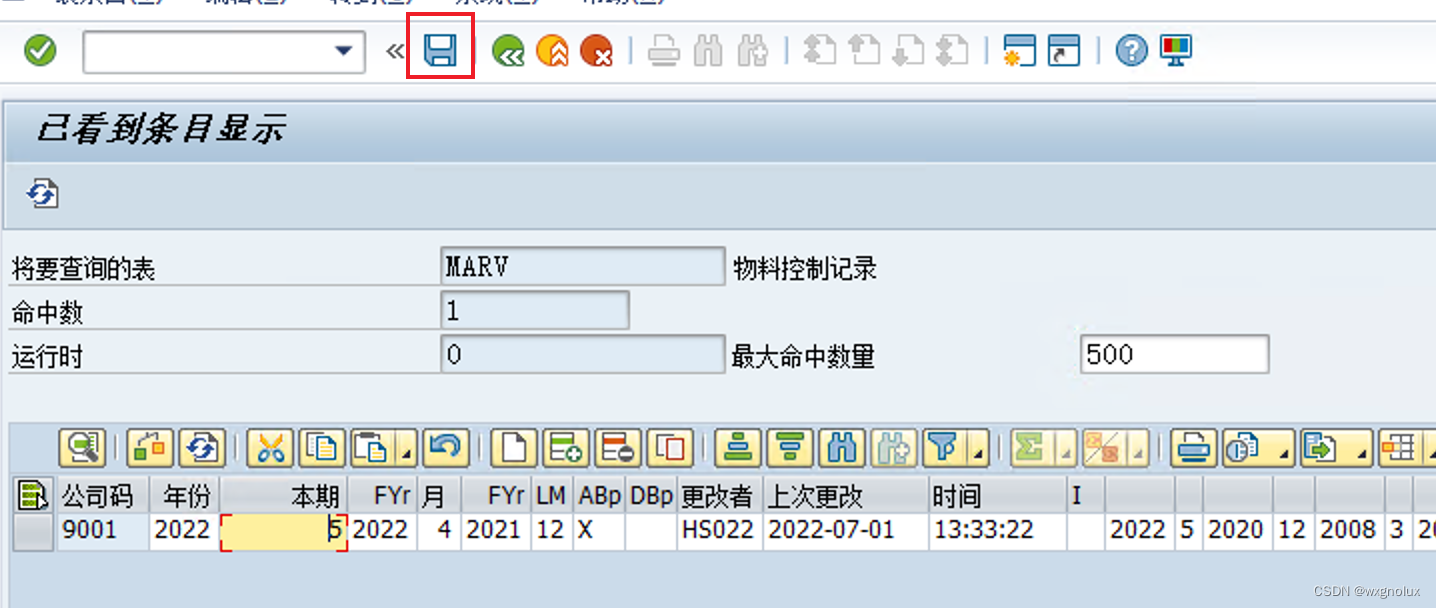
SAP-修改系统表数据的方法
剑指 Offer 58 - II. 左旋转字符串
[allocation problem] 455 Distribute cookies
Drawing dynamic 3D circle with pure C language
【Jailhouse 文章】Look Mum, no VM Exits
Sword finger offer 35 Replication of complex linked list
Daily question - longest substring without repeated characters
Fried chicken nuggets and fifa22
[depth first search] 695 Maximum area of the island
In this indifferent world, light crying
Codeforces Round #716 (Div. 2) D. Cut and Stick
Romance of programmers on Valentine's Day
Kubedm series-00-overview
How many checks does kubedm series-01-preflight have
过拟合与正则化
sync. Interpretation of mutex source code
Hang wait lock vs spin lock (where both are used)
Reflection summary of Haut OJ freshmen on Wednesday
Yolov5 adds attention mechanism
第六章 数据流建模—课后习题