当前位置:网站首页>Chapter V - message authentication and digital signature
Chapter V - message authentication and digital signature
2022-06-12 07:34:00 【bugmaker.】
- Message authentication : The process by which the message receiver verifies that the received message is from a trusted source and has not been tampered with , Used to prevent active attacks , Including camouflage 、 Content modification 、 Sequential modification 、 Timing modification .
Purpose : Ensure the authenticity and integrity of the message , Enable the receiver to identify the source of the message 、 Authenticity of content and validity of time .
Message authentication model : A triple (K,T,V)
Authentication function : Three types of : Message encryption function 、 Message authentication code 、 Hash function - Hash function :h = H(M)
Input : Messages of any length M
Output : Fixed length hash value H(M)
One way function : Forward calculation is easy , Reverse calculation is difficult
news M Functions of all bits of : Any change in one or more bits in the message will cause the hash value to change
Hash Function general structure : Almost all hash Function USES : Send the original message M Divide into blocks of fixed length ; The last piece is filled ; Set the initial value CV0
Compression function f, CVi=f(CVi-1,Yi-1); the last one CVi by hash value . - digital signature : Authentication techniques to prevent source or destination denial
Put forward the reason : Message authentication protects the data exchange between communication parties from being infringed by a third party , But there is no guarantee that both parties will cheat each other .
The basic requirements : Can be physically inseparable from the signed document ; The signer cannot deny his signature ; Signatures cannot be forged ; Easy to verify
classification : It can be divided into direct digital signature and arbitration digital signature ; It can be divided into unconditional digital signature and computationally secure digital signature ; It can be divided into one-time digital signature and multiple digital signature - Arbitration digital signature : The sender sends the signed message to the arbiter first , The arbiter tests the message and its signature , To check its source and content , Then time stamp the message , And send it to the receiver together with the instruction of arbitration verification .
requirement : The arbiter plays a key and sensitive role , All participants must have great confidence in the normal operation of this arbitration mechanism - Blind signature steps
(1) The message sender first blinds the message
(2) Let the signer sign the blind message
(3) The message owner removes the blind factor from the signature , Get the signer's signature on the original message
边栏推荐
- 私有协议的解密游戏:从秘文到明文
- Detailed explanation of 14 registers in 8086CPU
- 【高考那些事】准大学生看过来,选择方向和未来,自己把握
- Demonstrate "topic communication, action communication, service communication and parameter server" with a small turtle case
- Adaptive personalized federated learning paper interpretation + code analysis
- R语言使用epiDisplay包的summ函数计算dataframe中指定变量在不同分组变量下的描述性统计汇总信息并可视化有序点图、使用dot.col参数设置不同分组数据点的颜色
- R语言caTools包进行数据划分、scale函数进行数据缩放、class包的knn函数构建K近邻分类器、比较不同K值超参数下模型准确率(accuracy)
- 我人生中的第一个需求——Excel数据批量上传到数据库
- Shortcut key modification of TMUX and VIM
- Modelarts培训任务1
猜你喜欢

modelarts二
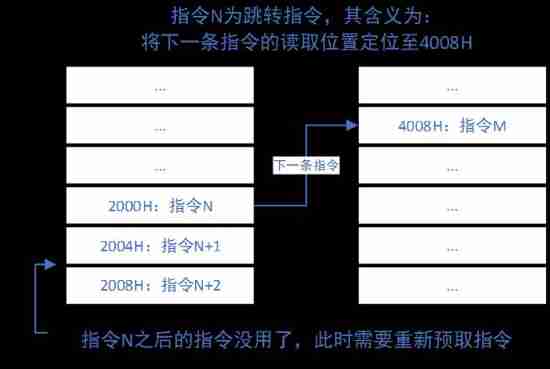
Detailed explanation of 14 registers in 8086CPU

Exploring shared representations for personalized federated learning paper notes + code interpretation
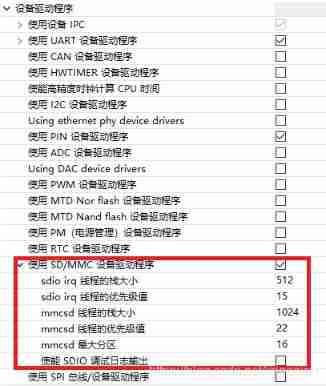
RT thread studio learning (IX) TF Card File System

Construction of running water lamp experiment with simulation software proteus

MySQL索引(一篇文章轻松搞定)
Voice assistant - Measurement Indicators

Day 6 of pyhon

Bi skills - beginning of the month

Knife4j first use
随机推荐
Static coordinate transformation in ROS (analysis + example)
R语言rnorm函数生成正太分布数据、使用epiDisplay包的summ函数计算向量数据的描述性统计汇总信息并可视化有序点图(名称、有效值个数、均值、中位数、标准差、最大值、最小值)
2022R2移动式压力容器充装试题模拟考试平台操作
Acwing - 4269 school anniversary
R语言使用RStudio将可视化结果保存为pdf文件(export--Save as PDF)
Improved schemes for episodic memory based lifelong learning
How to stop MySQL service under Linux
【WAX链游】发布一个免费开源的Alien Worlds【外星世界】脚本TLM
Test manager defines and implements test metrics
Principle and application of PWM
Class as a non type template parameter of the template
Source code learning - [FreeRTOS] privileged_ Understanding of function meaning
Detailed explanation of multi coordinate transformation in ROS (example + code)
Nine project management issues that PM should understand
Pyhon的第四天
Modelarts training task 1
Formatting the generalization forgetting trade off in continuous learning
Decryption game of private protocol: from secret text to plaintext
Summary of machine learning + pattern recognition learning (V) -- Integrated Learning
Hongmeng OS first training