当前位置:网站首页>EVM proof in appliedzkp zkevm (11)
EVM proof in appliedzkp zkevm (11)
2022-07-04 04:58:00 【mutourend】
1. introduction
EVM Proof Used to prove :
- state trie root The change is correct , By verifying that the transactions contained in a block have correct execution results .
EVM circuit Will be re implemented EVM, But it is verified from the perspective of verification , That means ,Prover Can help provide clues , As long as these clues do not contradict the results . Such as ,Prover Can provide information about call Whether or not to revert A clue to , Or something opcode Will you encounter the wrong clue , And then the EVM circuit It can be verified that the execution result is correct .
Transactions contained within a block can be simple ether transfers、contraction creation or contract interactions, Because every transaction has variable execution trace, Cannot use fixed circuit layout To verify specific region Specific to logic, So , We need to a chip To verify all possible logics, The chip Repeat yourself to achieve the whole circuit.
2. Custom type
The following types are customized for clues :
| Name | Type | Description |
|---|---|---|
GlobalCounter | int | Order of random access to BusMapping, which should be in sequence |
BusMapping | List[Tuple[int, ...]] | List of random read-write access data in sequence with GlobalCounter as index |
3. Random Accessible Data
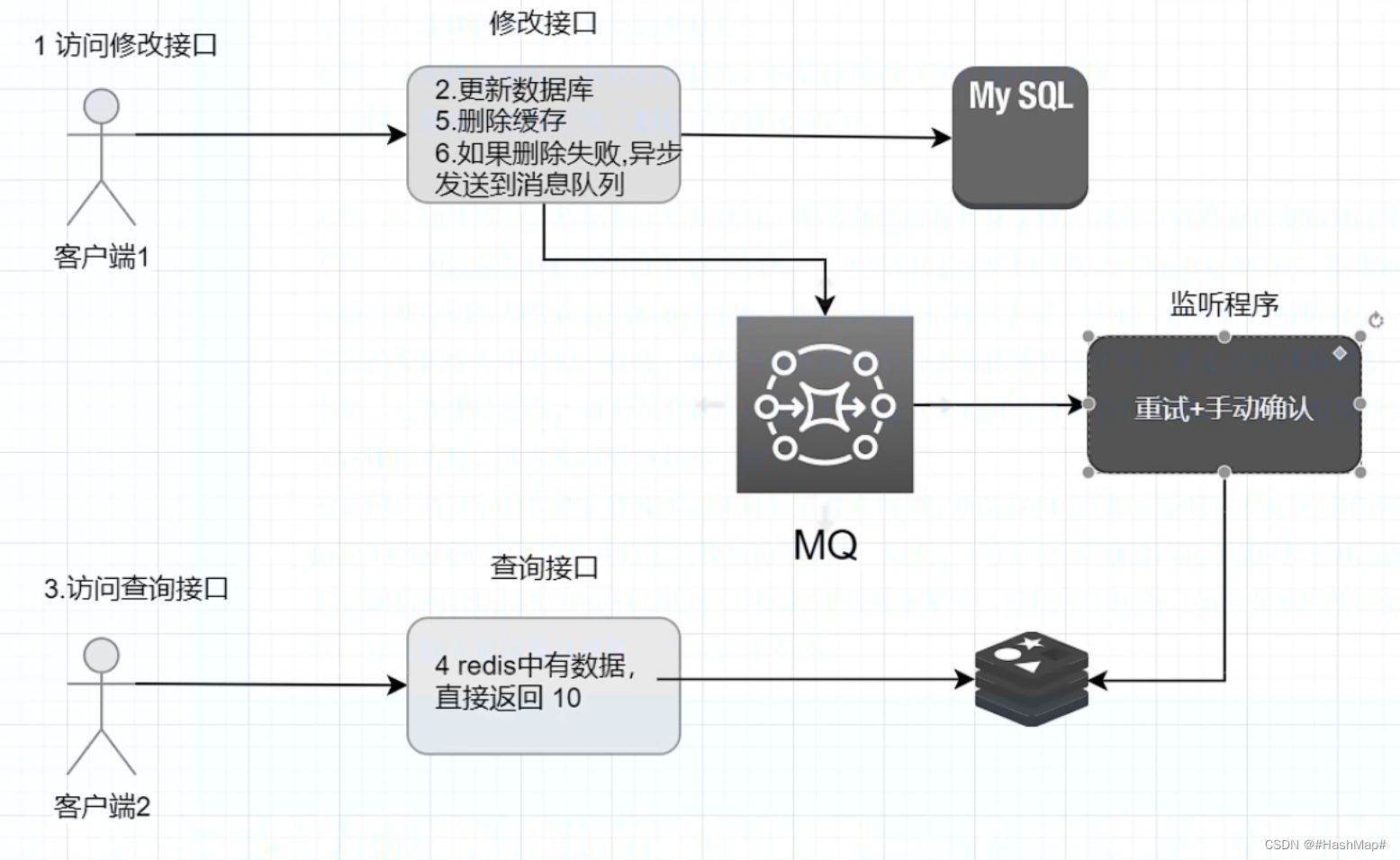
EVM The parser can do any random access to data Similar to account balance、account storage、stack in current scope、memeory in current scope, But for EVM circuit Come on , It is difficult to track these data to ensure the real-time consistency of these data .
therefore ,EVM proof have State proof To provide a valid list of random read-write access records indexed by the GlobalCounter as a lookup table to do random access at any moment.
take random read-write access records list be called BusMapping, Because its function is similar to that in computers bus, Used to transmit data between different parts . Allied ,read-only The data to random access The way is from lookup table load .
| Target | Index | Accessible By | Description |
|---|---|---|---|
Block | {enum} | Read | Block constant decided before executing the block |
BlockHash | {index} | Read | Previous 256 block hashes as a encoded word array |
AccountNonce | {address} | Read, Write | Account’s nonce |
AccountBalance | {address} | Read, Write | Account’s balance |
AccountCodeHash | {address} | Read, Write | Account’s code hash |
AccountStorage | {address}.{key} | Read, Write | Account’s storage as a key-value mapping |
Code | {hash}.{index} | Read | Executed code as a byte array |
Call | {id}.{enum} | Read | Call’s context decided by caller (includes EOA and internal calls) |
CallCalldata | {id}.{index} | Read | Call’s calldata as a byte array (only for EOA calls) |
CallSignature | {id}.{index} | Read | Call’s signature as a byte array (only for EOA calls) |
CallState | {id}.{enum} | Read, Write | Call’s internal state |
CallStateStack | {id}.{index} | Read, Write | Call’s stack as a encoded word array |
CallStateMemory | {id}.{index} | Read, Write | Call’s memory as a byte array |
3. Circuit Constraints
This repetition chip have 2 individual main states, A call initializes , Another one for bytecode execution.
Reference material
[1] EVM Proof
边栏推荐
- Flutter ‘/usr/lib/libswiftCore.dylib‘ (no such file)
- [Yugong series] go teaching course 001 in July 2022 - Introduction to go language premise
- Sample template of software design document - learning / practice
- [wechat applet] good looking carousel map component
- Headache delayed double deletion
- (pointer) write function void fun (int x, int *pp, int *n)
- cmake
- 关于solidworks standard无法获得许可 8544问题的总结
- 软件设计文档示例模板 - 学习/实践
- Sécurité du réseau dans les écoles professionnelles secondaires - preuve de mémoire
猜你喜欢
随机推荐
Using jsts in esmodule environment
Notes on the paper "cross view transformers for real time map view semantic segmentation"
附件三:防守方评分标准.docx
【MATLAB】MATLAB 仿真模拟调制系统 — DSB 系统
Zhongke panyun-d module analysis and scoring standard
中科磐云—2022广西逆向解析思路
【MATLAB】通信信号调制通用函数 — 带通滤波器
Error response from daemon: You cannot remove a running container 8d6f0d2850250627cd6c2acb2497002fc3
Annex 4: scoring criteria of the attacker docx
全国职业院校技能大赛(中职组)网络安全竞赛试题—解析
抓包整理外篇fiddler———— 会话栏与过滤器
The paddlehub face recognition scheme is deployed, and the trained model is deployed and applied in pytchrom
Asahi Kasei participated in the 5th China International Import Expo (5th ciie) for the first time
Kivy tutorial 07 component and attribute binding implementation button button click to modify the label component (tutorial includes source code)
MySQL indexes and transactions
Share some of my telecommuting experience
MAUI 入门教程系列(5.XAML及页面介绍)
YoloV6实战:手把手教你使用Yolov6进行物体检测(附数据集)
Beipiao programmer, 20K monthly salary, 15W a year, normal?
附件六:防守工作簡報.docx


![[wechat applet] good looking carousel map component](/img/66/4ae6a72fff419c7ed1ca015eb94c03.jpg)