当前位置:网站首页>Automatic, intelligent and visual! Deeply convinced of the eight designs behind sslo scheme
Automatic, intelligent and visual! Deeply convinced of the eight designs behind sslo scheme
2022-07-01 15:43:00 【51CTO】

With SSL/TLS Protocols are more used in web Website 、 Mail system 、FTP And the Internet of things , Traditional business “ Candied haws string ” Security architecture has also encountered challenges :
■ Business is not visible : Some security devices may not be able to decrypt and detect SSL/TLS Traffic , Become the safety blind spot of enterprises . Or safety equipment SSL After uninstalling , The processing performance of safety equipment is greatly reduced , Enterprise security needs cannot be met .
■ Resources are easily wasted : Under the traditional security architecture , There are many failure points under the deployment mode of sugar gourd string of many safety equipment , Low overall stability , It is difficult to adapt to the changes of network structure . At the same time, the safety equipment consumes unnecessary performance , bring IT Waste of resources .
■ Trouble shooting : Traditional network data centers often use a large number of different security manufacturers , In case of failure, it is often necessary to coordinate different safety manufacturers to assist in troubleshooting at the same time , This makes it more difficult to check .
■ Device expansion is difficult : Under the traditional security architecture ,FW、IPS、WAF And other security devices are generally deployed in the active and standby mode , It's hard to scale out . If the equipment performance is insufficient , Vertical expansion can only be achieved by replacing higher performance hardware .

↑ Traditional security architecture
Face these challenges , Deeply convinced to launch a new SSLO Solution , adopt Reshape the security architecture Help users realize the intelligent arrangement and management of traffic . The scheme has SSL Traffic Visualization 、 Security device pooling 、 Service chain arrangement Other characteristics , Based on the innovation of security equipment access mode and security service chain , The performance of safety equipment can be expanded 、 Equipment can be heterogeneous 、 Resource utilization can be improved and traffic can be intelligently arranged .
One 、 Security SSL Traffic is visible
Inbound SSL The flow is passing through SSLO Equipment time , It will unload the overall traffic : Decrypt first , Then arrange the flow intelligently , Then send it to the server ( Re encryptable ). This can not only eliminate the safety blind spot , be-all SSL The flow can also be clearly seen , At the same time, save safety equipment SSL Add 、 Decryption consumption , Avoid using SSL Bypass the safety risks of safety equipment .

Two 、 Security device pooling
Convinced SSLO Provide professional load balancing technology , It can realize the pooling of security devices , Avoid idle assets , Support smooth expansion and brand heterogeneity , Increase the flexibility of network architecture .

3、 ... and 、 Support multiple ways of accessing security devices
Convinced SSLO It can support access to safety equipment running in different working modes .
1. The security equipment is connected to the second floor
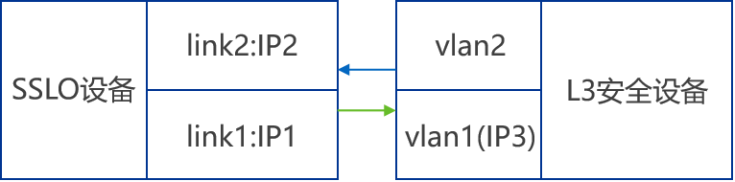
The two-layer access mode is similar to the network cable mode . In order to effectively distinguish different second floor safety equipment , Each layer-2 security device needs to monopolize two different links ( perhaps VLAN), stay SSLO The second link of the device is set with VIP(IP3) To carry out , this VIP And link 1 Of IP1 Same as segment , When IP3 Be able to receive IP1 At the flow rate of , We think the safety equipment on the second floor is in normal working condition , Otherwise, the equipment is abnormal .

Logic diagram
2. Three layer access of safety equipment
Layer 3 device access itself provides IP Address . Yes SSLO For equipment , At this time, the outlet interface of the traffic sent to the security device and the inlet interface of the traffic received from the security device do not need to be completely independent , There is one arm way , There are also two arm modes .
Single arm mode :L3 Only one route needs to be configured on the security device , Route packets in both the request direction and the reply direction to IP1, This method is simpler to configure .
Two arm mode :L3 Security devices need to be configured with multiple routes , Route request direction packets to IP2, At the same time, route the packets in the reply direction to IP1.
3.TAP Mirror device access
The image device itself only receives packets , By default, the monitor does not need to be configured .SSLO The device needs to assign a link to the image device (link1), If IP, And will respond SSLO Of ARP request , that SSLO You can directly use the image device IP that will do . If mirror Like the device does not respond ARP request , that SSLO You need to assign a IP, And for this IP Tying Fixed image device MAC Address .

Four 、 Session separation technology
Convinced SSLO Session separation technology provides a solid technical guarantee for intelligent traffic scheduling .
stay Linux In the system , Generally, the session information is recorded through the connection tracking mechanism , When the five tuple information is the same, the same session will be hit , In the flow through SSLO The flow returned from the safety equipment after the arrangement generally does not change the five tuple information , Then it will be impossible to arrange the traffic into different security devices .

In order to be able to distinguish between different sessions , Deeply convinced of the innovative design :
(1) Ensure that each security device uses different links , Then different security devices can be distinguished according to the traffic input interface .
(2) Record the incoming interface link information into the session information , Traffic entering from different interfaces can hit different sessions , Realize session isolation .
(3) On the basis of session isolation , Connect the safety devices through which the flow passes in series , On the one hand, it is used to determine the sequence of flow through safety equipment , On the other hand, it is used to realize the security device according to this information when the security device is abnormal bypass, Ensure the continuity of flow .
5、 ... and 、 Health inspection of safety equipment
Convinced SSLO It can provide a variety of health examination methods , In order to ensure that the traffic is forwarded to the normal working security equipment . The more common way of health examination is through icmp Protocol for network detection , except icmp The way , You can also send four layers / Check the seven layer data .
6、 ... and 、 Security service chain scheduling
Convinced SSLO Through the scheduling of the security service chain to achieve intelligent traffic scheduling , Security service chain scheduling is very flexible , It can meet the needs of various business scenarios , Including virtual service reference security service chain 、 The pre policy refers to the security service chain 、ipro Reference security service chain .

7、 ... and 、 Dual mode security deployment
For the operation and maintenance of safety equipment and business characteristics , Develop flexible deployment strategies , Realize dual-mode security deployment . Based on a business , Adopt gray drainage , Specify different service chains . Such as stable chain and sensitive chain , Steady state chain focuses on business stability and reliability , The sensitive chain focuses on the business gray level online 、 Sensitivity adjustment .
8、 ... and 、 fault bypass( escape ) Mechanism
To ensure the normal operation of business , Even in extreme cases , All security devices in a security resource pool fail ,SSLO The device can still be flexibly scheduled through traffic , Automatic execution Bypass Mechanism , Actively bypass the failed safety device group , Avoid affecting the whole business due to the failure of safety equipment .
The above is about deep conviction SSLO Introduction of the solution , Focus on “ Shenxin Technology ” Get more technical dry goods on official account .
边栏推荐
- 6.2 normalization 6.2.6 BC normal form (BCNF) 6.2.9 normalization summary
- 将ABAP On-Premises系统连接到中央检查系统以进行自定义代码迁移
- 【显存优化】深度学习显存优化方法
- Sort out the four commonly used sorting functions in SQL
- 你TM到底几点下班?!!!
- Pico,能否拯救消费级VR?
- 雷神科技冲刺北交所,拟募集资金5.4亿元
- 点云重建方法汇总一(PCL-CGAL)
- Wechat official account subscription message Wx open subscribe implementation and pit closure guide
- 《QT+PCL第六章》点云配准icp系列2
猜你喜欢
MySQL backup and restore single database and single table
Photoshop插件-HDR(二)-脚本开发-PS插件

Stm32f4-tft-spi timing logic analyzer commissioning record
【STM32学习】 基于STM32 USB存储设备的w25qxx自动判断容量检测

Hardware design guide for s32k1xx microcontroller

采集数据工具推荐,以及采集数据列表详细图解流程

Microservice tracking SQL (support Gorm query tracking under isto control)

Wechat official account subscription message Wx open subscribe implementation and pit closure guide
![[stm32-usb-msc problem help] stm32f411ceu6 (Weact) +w25q64+usb-msc flash uses SPI2 to read out only 520kb](/img/ec/fa51b21468708609f998de1b2b84fe.jpg)
[stm32-usb-msc problem help] stm32f411ceu6 (Weact) +w25q64+usb-msc flash uses SPI2 to read out only 520kb

综述 | 激光与视觉融合SLAM
随机推荐
Task.Run(), Task.Factory.StartNew() 和 New Task() 的行为不一致分析
微信小程序01-底部导航栏设置
What are the EN ISO 20957 certification standards for common fitness equipment
Pnas: brain and behavior changes of social anxiety patients with empathic embarrassment
ABAP-调用Restful API
工厂高精度定位管理系统,数字化安全生产管理
swiper 轮播图,最后一张图与第一张图无缝衔接
[Cloudera][ImpalaJDBCDriver](500164)Error initialized or created transport for authentication
《QT+PCL第六章》点云配准icp系列2
《QT+PCL第九章》点云重建系列2
Samsung took the lead in putting 3nm chips into production, and Shanghai's fresh master students can settle directly. Nankai has established a chip science center. Today, more big news is here
【云动向】6月上云新风向!云商店热榜揭晓
Create employee data in SAP s/4hana by importing CSV
软件测试的可持续发展,必须要学会敲代码?
[STM32 learning] w25qxx automatic judgment capacity detection based on STM32 USB storage device
Raytheon technology rushes to the Beijing stock exchange and plans to raise 540million yuan
Using swiper to make mobile phone rotation map
Équipe tensflow: Nous ne sommes pas abandonnés
Redis秒杀demo
Qt+pcl Chapter 6 point cloud registration ICP Series 5