当前位置:网站首页>Zhongke panyun-2022 Guangdong Trojan horse information acquisition and analysis
Zhongke panyun-2022 Guangdong Trojan horse information acquisition and analysis
2022-07-04 04:59:00 【Beluga】
Trojan information acquisition
Need data package to be private
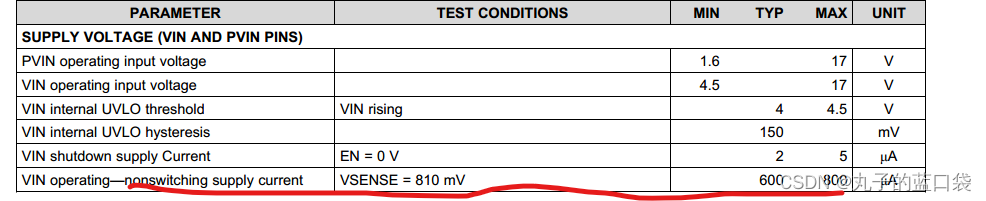
1. From the target server FTP Upload and download wire0077.pcap, Analyze the file , Find out the protocol used by hackers , Submit agreement name .
At the beginning, this question is about what agreement there is , But I didn't see much , When you do the second question, you know it is SMTP, This is also a problem-solving skill , When there is a relationship between the present and the future, it can be appropriately deduced from the back

2. Analyze the file , Find out what hackers got zip Compress package file , Submit the file name of the compressed package .
Because the answer of the first question is not determined , Nor can it be done directly through the application layer protocol , But you can use the transport layer , After all, the transport layer is UDP and TCP And they are basically used TCP
Filter out tcp The package contains keywords zip My bag , This is also a helpless move. After all, the first question can't be done

track TCP Stream finds suspicious target , The answer is correct after submission

3. Analyze the file , Find out the sensitive files obtained by hackers , The file name of the submitted sensitive file .
I learned that the agreement is SMTP, Look first , After reading for some time, I found a suspicious target agreement imf, This will filter out all the files
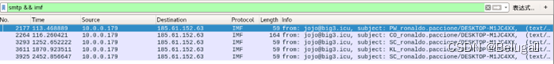
Then try to submit , But what's worse here is that the names of two image files are almost the same , Pay attention to
4. Analyze the file , Find out the sensitive files obtained by hackers , The time when the sensitive document was submitted for disclosure .
This bag that directly finds the last question , The head is time

5. Analyze the file , Find out the sensitive files obtained by hackers , Submit the folder name leaked in the sensitive file .
There is a little hole in this question , The title is the name of the folder leaked in the sensitive file , The sensitive file is actually a picture , After restoration, the answer is ready
Because we need to solve the problem of line feed and coding , So I write a simple program to solve
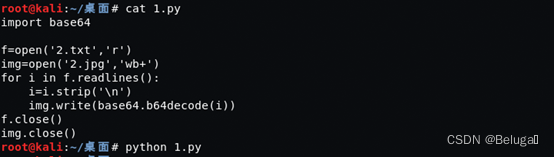
The folder name in the figure is the answer

边栏推荐
- @Feignclient comments and parameters
- Definition of DCDC power supply current
- appliedzkp zkevm(13)中的Public Inputs
- NTFS 安全权限
- 电子元器件商城与数据手册下载网站汇总
- Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it
- Network - vxlan
- Zhongke Panyun - 2022 Guangxi reverse analysis ideas
- Deep understanding of redis -- bloomfilter
- 分享一些我的远程办公经验
猜你喜欢
随机推荐
定制一个自己项目里需要的分页器
LeetCode136+128+152+148
【MATLAB】MATLAB 仿真数字基带传输系统 — 数字基带传输系统
20000 words will take you to master multithreading
Unity中RampTex介绍和应用: 溶解特效优化
简单g++和gdb调试
Capturing and sorting out external Fiddler -- Conversation bar and filter
qt下开发mqtt的访问程序
Qt QTableView数据列宽度自适应
【MATLAB】通信信号调制通用函数 — 带通滤波器
【MATLAB】MATLAB 仿真数字带通传输系统 — ASK、 PSK、 FSK 系统
CRS-4013: This command is not supported in a single-node configuration.
Change the background color of Kivy tutorial (tutorial includes source code)
在代碼中使用度量單比特,從而生活更美好
COMP1721 Creating Classes
加密和解密
Error response from daemon: You cannot remove a running container 8d6f0d2850250627cd6c2acb2497002fc3
Yolov6 practice: teach you to use yolov6 for object detection (with data set)
【MATLAB】通信信号调制通用函数 — 低通滤波器
Acwing game 58