当前位置:网站首页>Nine degree 1201 - traversal of binary sort number - binary sort tree "suggestions collection"
Nine degree 1201 - traversal of binary sort number - binary sort tree "suggestions collection"
2022-07-07 21:24:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm the king of the whole stack .
This is an orthodox tree construction and traversal problem . At the beginning, I also wanted to use array construction to replace the past , But I can't find it , Just use the pointer honestly . If the binary sort tree and traversal method are not clearly defined . It's best to read the data structure book and review .
#include<stdio.h>
struct node{
node *l;
node *r;
int val;
node(int a):val(a),l(NULL),r(NULL){};
};
node *root;
int n;
void qian(node *p){
printf("%d ",p->val);
if(p->l!=NULL)qian(p->l);
if(p->r!=NULL)qian(p->r);
}
void zhong(node *p){
if(p->l!=NULL)zhong(p->l);
printf("%d ",p->val);
if(p->r!=NULL)zhong(p->r);
}
void hou(node *p){
if(p->l!=NULL)hou(p->l);
if(p->r!=NULL)hou(p->r);
printf("%d ",p->val);
}
int main(){
int val;
node *p;
while(~scanf("%d",&n)){
root=NULL;
for(int i=0;i<n;i++){
scanf("%d",&val);
if(i==0){
root=new node(val);
continue;
}
p=root;
while(1){
if(val==p->val)break;
else if(val<p->val){
if(p->l==NULL){
p->l=new node(val);
break;
}
else{
p=p->l;continue;
}
}
else if(val>p->val){
if(p->r==NULL){
p->r=new node(val);
break;
}
else{
p=p->r;continue;
}
}
}
}
qian(root);
printf("\n");
zhong(root);
printf("\n");
hou(root);
printf("\n");
}
return 0;
}Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/116527.html Link to the original text :https://javaforall.cn
边栏推荐
- 【C语言】指针进阶---指针你真的学懂了吗?
- Unity3d 4.3.4f1执行项目
- Écrivez une liste de sauts
- The new version of onespin 360 DV has been released, refreshing the experience of FPGA formal verification function
- Solve the problem of using uni app mediaerror mediaerror errorcode -5
- MySQL约束之默认约束default与零填充约束zerofill
- Postgresql数据库character varying和character的区别说明
- How to choose financial products? Novice doesn't know anything
- DataTable数据转换为实体
- 【OpenCV 例程200篇】223. 特征提取之多边形拟合(cv.approxPolyDP)
猜你喜欢
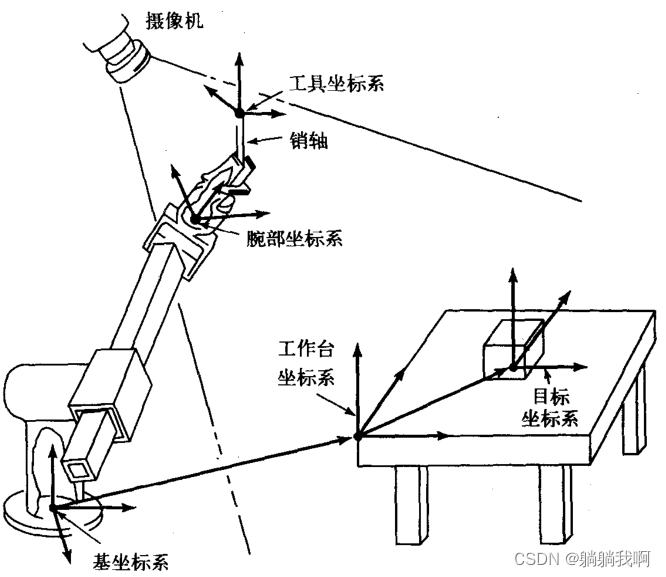
Small guide for rapid formation of manipulator (11): standard nomenclature of coordinate system
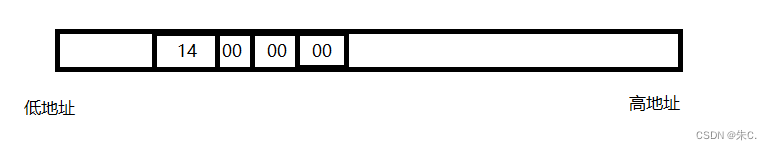
Details of C language integer and floating-point data storage in memory (including details of original code, inverse code, complement, size end storage, etc.)
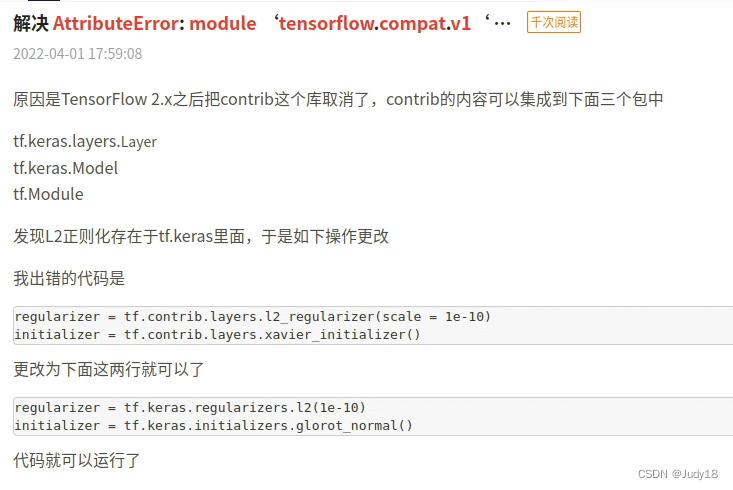
Tensorflow2. How to run under x 1 Code of X
Make this crmeb single merchant wechat mall system popular, so easy to use!
![Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]](/img/af/61b384b1b6ba46aa1a6011f8a30085.png)
Is embedded system really safe? [how does onespin comprehensively solve the IC integrity problem for the development team]
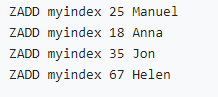
使用高斯Redis实现二级索引

【OpenCV 例程200篇】223. 特征提取之多边形拟合(cv.approxPolyDP)

Tensorflow2.x下如何运行1.x的代码

The little money made by the program ape is a P!
MySQL storage expression error
随机推荐
margin 等高布局
Demon daddy C
Default constraint and zero fill constraint of MySQL constraint
[matrix multiplication] [noi 2012] [cogs963] random number generator
gridView自己定义做时间排版「建议收藏」
Datatable data conversion to entity
C语言多角度帮助你深入理解指针(1. 字符指针2. 数组指针和 指针数组 、数组传参和指针传参3. 函数指针4. 函数指针数组5. 指向函数指针数组的指针6. 回调函数)
201215-03-19—cocos2dx内存管理–具体解释「建议收藏」
Validutil, "Rethinking the setting of semi supervised learning on graphs"
Problems encountered in installing mysql8 for Ubuntu and the detailed installation process
Addition, deletion, modification and query of sqlhelper
寫一下跳錶
Alibaba cloud award winning experience: how to mount NAS file system through ECS
恶魔奶爸 B3 少量泛读,完成两万词汇量+
FatMouse&#39; Trade(杭电1009)
Codeforces round 275 (Div. 2) C – diverse permutation (construction) [easy to understand]
部署、收回和删除解决方式—-STSADM和PowerShell「建议收藏」
AADL inspector fault tree safety analysis module
HOJ 2245 浮游三角胞(数学啊 )
Micro service remote debug, nocalhost + rainbow micro service development second bullet