当前位置:网站首页>Leetcode notes: Weekly contest 300
Leetcode notes: Weekly contest 300
2022-07-05 17:59:00 【Espresso Macchiato】
- Match Links :https://leetcode.com/contest/weekly-contest-300/
1. Topic 1
The link to question 1 is as follows :
1. Their thinking
This question is actually a little long , The idea is very direct , Build a character mapping correspondence according to the meaning of the topic , Then decode it .
2. Code implementation
give python The code implementation is as follows :
class Solution:
def decodeMessage(self, key: str, message: str) -> str:
cipher = {
" ": " "}
idx = 0
for ch in key:
if ch != " " and ch not in cipher.keys():
cipher[ch] = chr(ord('a') + idx)
idx += 1
res = [cipher[ch] for ch in message]
return "".join(res)
The submitted code was evaluated : Time consuming 49ms, Take up memory 13.9MB.
2. Topic two
The link to question 2 is as follows :
1. Their thinking
This problem is not much different from the general solution of rotation matrix , Just fill in the data by constantly changing the direction .
2. Code implementation
give python The code implementation is as follows :
# Definition for singly-linked list.
# class ListNode:
# def __init__(self, val=0, next=None):
# self.val = val
# self.next = next
class Solution:
def spiralMatrix(self, m: int, n: int, head: Optional[ListNode]) -> List[List[int]]:
res = [[-1 for _ in range(n)] for _ in range(m)]
direction = [(0, 1), (1, 0), (0, -1), (-1, 0)]
x, y, idx = 0, 0, 0
while head:
res[x][y] = head.val
nx, ny = x + direction[idx][0], y + direction[idx][1]
if not(0 <= nx < m and 0 <= ny < n and res[nx][ny] == -1):
idx = (idx+1) % 4
nx, ny = x + direction[idx][0], y + direction[idx][1]
x, y = nx, ny
head = head.next
return res
The submitted code was evaluated : Time consuming 2593ms, Take up memory 66.2MB.
3. Topic three
The link to question 3 is as follows :
1. Their thinking
In fact, the idea of this question is quite direct , It's a recursive algorithm , Then use dynamic programming to optimize the calculation efficiency .
So we just need to write a recursive formula , Its recurrence relation is actually easy to calculate , That is, the number of people who knew the secret the day before minus the number of people who would forget the secret that day , Plus the number of new people who will know the secret that day .
And the number of people who will forget the secret that day is forget On the critical day, the new number of people who know Mimi , Then the number of people added on that day is from the current date delay Day to forget The number of all new people between the critical day .
thus , We can write the final recursive formula .
2. Code implementation
give python The code implementation is as follows :
class Solution:
def peopleAwareOfSecret(self, n: int, delay: int, forget: int) -> int:
MOD = 10**9 + 7
@lru_cache(None)
def fp(idx):
return np(idx-forget)
@lru_cache(None)
def np(idx):
if idx == 1:
return 1
elif idx <= delay:
return 0
res = 0
for i in range(idx-forget+1, idx-delay+1):
res += np(i)
return res % MOD
@lru_cache(None)
def dp(idx):
if idx <= 0:
return 0
elif idx <= delay:
return 1
return (dp(idx-1) - fp(idx) + np(idx)) % MOD
return dp(n)
The submitted code was evaluated : Time consuming 993ms, Take up memory 17.1MB.
4. Topic four
The link to question 4 is as follows :
1. Their thinking
This question is actually more direct than the previous one , It's just a dynamic planning .
The number of routes that can be formed by each point is 1 Add the number of adjacent paths greater than this point .
thus , We can get our final answer quickly .
2. Code implementation
give python The code implementation is as follows :
class Solution:
def countPaths(self, grid: List[List[int]]) -> int:
MOD = 10**9 + 7
n, m = len(grid), len(grid[0])
@lru_cache(None)
def dp(i, j):
res = 1
for x, y in [(i-1, j), (i+1, j), (i, j-1), (i, j+1)]:
if 0 <= x < n and 0 <= y < m and grid[x][y] > grid[i][j]:
res += dp(x, y)
return res % MOD
s = sum(dp(i, j) for i in range(n) for j in range(m))
return s % MOD
The submitted code was evaluated : Time consuming 3547ms, Take up memory 107.4MB.
边栏推荐
- LeetCode每日一题:合并两个有序数组
- 小白入门NAS—快速搭建私有云教程系列(一)[通俗易懂]
- Sophon base 3.1 launched mlops function to provide wings for the operation of enterprise AI capabilities
- VC编程入门浅谈「建议收藏」
- 使用Jmeter虚拟化table失败
- Ten capabilities that cyber threat analysts should have
- Compared with the loss of Wenxin, the performance is improved a lot
- 星环科技数据安全管理平台 Defensor重磅发布
- 怎么选择外盘期货平台最正规安全?
- "Xiaodeng in operation and maintenance" is a single sign on solution for cloud applications
猜你喜欢

破解湖+仓混合架构顽疾,星环科技推出自主可控云原生湖仓一体平台
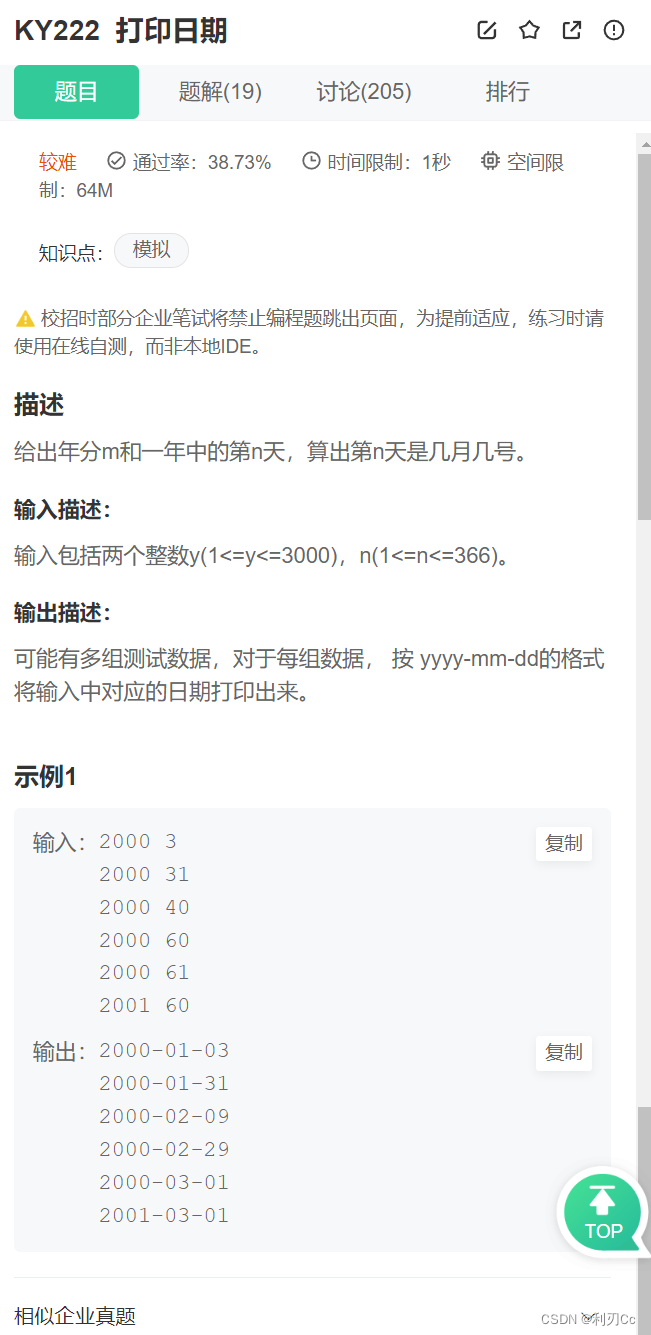
每日一练:关于日期的一系列
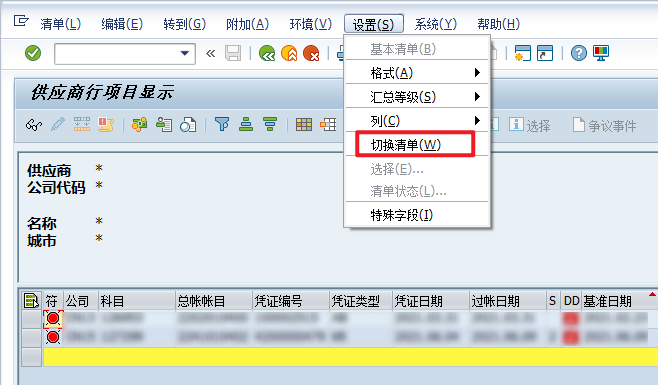
VBA drives SAP GUI to realize office automation (II): judge whether elements exist

Ten capabilities that cyber threat analysts should have

Career advancement Guide: recommended books for people in big factories
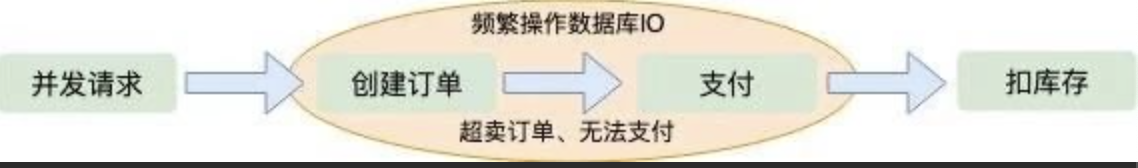
“12306” 的架构到底有多牛逼?

PMP认证需具备哪些条件啊?费用多少啊?
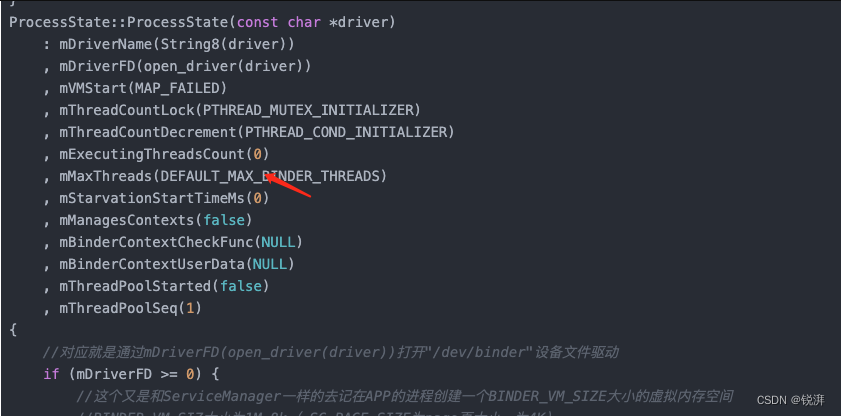
Binder开辟线程数过多导致主线程ANR异常

IDC report: Tencent cloud database ranks top 2 in the relational database market!
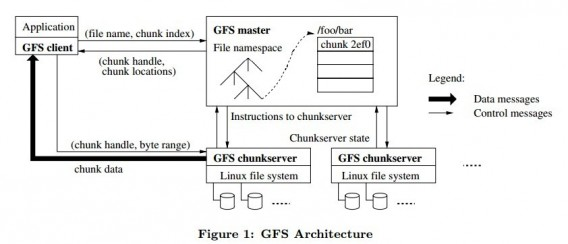
GFS distributed file system
随机推荐
职场进阶指南:大厂人必看书籍推荐
从类生成XML架构
删除数组中的某几个元素
Oracle recovery tools -- Oracle database recovery tool
Data access - entityframework integration
Sentinel flow guard
Zabbix
Sophon KG升级3.1:打破数据间壁垒,解放企业生产力
Daily exercise: a series of dates
Server configuration jupyter environment
Ant financial's sudden wealth has not yet begun, but the myth of zoom continues!
Ten capabilities that cyber threat analysts should have
Sophon kg upgrade 3.1: break down barriers between data and liberate enterprise productivity
How to modify MySQL fields as self growing fields
记一次使用Windbg分析内存“泄漏”的案例
[performance test] full link voltage test
Leetcode daily practice: rotating arrays
神经网络自我认知模型
Career advancement Guide: recommended books for people in big factories
Tencent music launched its new product "quyimai", which provides music commercial copyright authorization