当前位置:网站首页>Six bad safety habits in the development of enterprise digitalization, each of which is very dangerous!
Six bad safety habits in the development of enterprise digitalization, each of which is very dangerous!
2022-07-05 17:44:00 【Software testing network】

Recently, cyber crime is on the rise , The attack becomes more and more rapid 、 More and more complex . The number of data leaks caused by network attacks is 2021 Year on year 27%, There is no sign of slowing down . Some neglected safety habits ( For example, use the same password multiple times ) It may seem harmless , But it will indeed cause huge losses to the organization .
This paper introduces the six most common safety habits in enterprises and their correction methods , The security team needs to check whether these bad habits exist in their own enterprises as soon as possible . Most security threats and risks can be prevented , You can use common sense methods 、 Continuous compliance testing 、 assessment 、 Audit and measurement to solve .
1、 Password management is ignored
60% The above data leakage events involve login information theft or poor security . Use the same password 、 Share password 、 Write down the password on the note , These bad password practices are common . Don't let the attacker succeed easily !
Method : Develop a password policy throughout the organization , Use password manager , And enable multifactor authentication , To reduce the risk of unauthorized account access . Password policies should clarify how to create strong passwords 、 How often do I update my password , And how to share passwords securely among employees .
2、 Superficial safety process
The security process covers everything from the induction checklist to the privacy policy , These documents should reflect how the security team of the enterprise organization can effectively complete the work , And implement it in daily work , Instead of being drafted and thrown into a folder . These policies must be considered regularly , Improve according to the challenges and risks found .
Method : Require the safety team to regularly review and accept the safety policy . Take the initiative to ask for feedback , To ensure that the policies and processes reflect that the team is actually doing a good job , And get the support of the whole organization .
3、 Unsafe terminal application system
Telecommuting has become more and more popular , This is where the enterprise team works 、 Great changes have taken place in time and manner in the past two years . Although working from home has many advantages , But this trend also brings major security challenges .
Nowadays, more people use unsafe Wi-Fi、 Mix office equipment and personal equipment 、 Ignore regular data backup and software updates . No one wants to become the weakest link that eventually leads to the plight of the organization .
Method : Use device management solutions to ensure automatic software updates and patches , Develop mobile device policies , Employees are encouraged to use only company equipment and secure network channels to access sensitive data .
4、 Ignore internal safety audit
Even if the organization has developed appropriate safety policies and procedures , Nor can they be regarded as unchanging . Understand how the organization's safety plan is improving ( Or not perfect ), And keep abreast of emerging new threats , Continuous testing and regular internal audits are essential .
Method : Develop internal audit plan , Review the safety status of the organization at least once a year , And find opportunities to improve . This will also ensure that your organization is kept informed of any changes in the threat area that need to be addressed .
5、 Do not pay attention to the training of employees' safety awareness
Phishing and malware are the causes of security incidents ( Including blackmail software events ) The most common inducement , Regularly train employees on safety best practices , Ensuring that everyone knows that safety is a priority for the entire organization .
Method : Enterprises should carry out safety awareness training at least once a year , And conduct irregular random tests on employees or users , To ensure that they really understand and follow the company's safety management requirements .
6、 Lack of awareness of the consequences of cyber threats
Too many organizations think that data leakage or security incidents will not happen to them . Ensuring safety and compliance is more than IT Issues of concern to the Department . From management team and board of directors to new employees , Everyone in the whole organization should understand the threats faced by the organization , And their respective roles and responsibilities in protecting customer and organizational data security .
Method : Strive to create an organizational culture that focuses on safety and understands its importance . Ensure that all employees understand their roles and responsibilities in protecting customer and business information security , And clearly communicate the benefits of following established policies and procedures .
Reference link
https://threatpost.com/six-bad-habits-break/180082/.
边栏推荐
- Troubleshooting - about clip not found Visual Studio
- 漫画:寻找无序数组的第k大元素(修订版)
- MySQL queries the latest qualified data rows
- Debug kernel code through proc interface
- flask接口响应中的中文乱码(unicode)处理
- C (WinForm) the current thread is not in a single threaded unit, so ActiveX controls cannot be instantiated
- 提高應用程序性能的7個DevOps實踐
- Cloud security daily 220705: the red hat PHP interpreter has found a vulnerability of executing arbitrary code, which needs to be upgraded as soon as possible
- Machine learning 01: Introduction
- 漫画:有趣的海盗问题 (完整版)
猜你喜欢
IDEA 项目启动报错 Shorten the command line via JAR manifest or via a classpath file and rerun.

7 pratiques devops pour améliorer la performance des applications
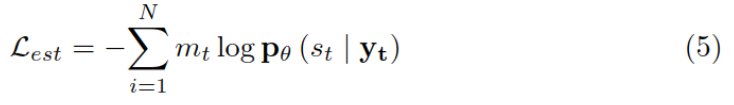
论文阅读_医疗NLP模型_ EMBERT
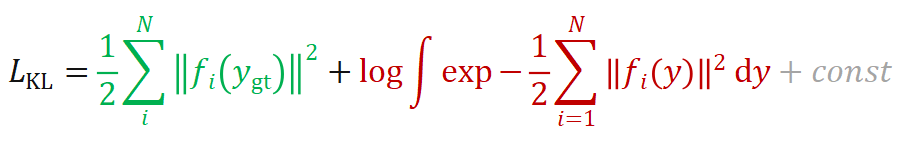
CVPR 2022最佳学生论文:单张图像估计物体在3D空间中的位姿估计
Use of ThinkPHP template
Beijing internal promotion | the machine learning group of Microsoft Research Asia recruits full-time researchers in nlp/ speech synthesis and other directions

Which is more cost-effective, haqu K1 or haqu H1? Who is more worth starting with?
十个顶级自动化和编排工具
Machine learning 02: model evaluation
thinkphp3.2.3
随机推荐
Design of electronic clock based on 51 single chip microcomputer
Machine learning 02: model evaluation
Tita 绩效宝:如何为年中考核做准备?
Force deduction solution summary 1200 minimum absolute difference
thinkphp3.2.3
Ordinary programmers look at the code, and top programmers look at the trend
Oracle缩表空间的完整解决实例
Clickhouse (03) how to install and deploy Clickhouse
Force deduction solution summary 729- my schedule I
CVPR 2022最佳学生论文:单张图像估计物体在3D空间中的位姿估计
十个顶级自动化和编排工具
哈趣K1和哈趣H1哪个性价比更高?谁更值得入手?
Oracle Recovery Tools ----oracle数据库恢复利器
漫画:如何实现大整数相乘?(下)
Flask solves the problem of CORS err
How to save the trained neural network model (pytorch version)
Flow characteristics of kitchen knife, ant sword, ice scorpion and Godzilla
毫无章法系列
Which platform of outer disk gold is regular and safe, and how to distinguish it?
Alpha conversion from gamma space to linner space under URP (II) -- multi alpha map superposition