当前位置:网站首页>[blackmail virus data recovery] suffix Hydra blackmail virus
[blackmail virus data recovery] suffix Hydra blackmail virus
2022-07-02 08:35:00 【qq_ thirty-eight million five hundred and thirteen thousand thr】
1. suffix .HYDRA Blackmail virus introduction ?
HYDRA yes A high-risk ransomware , Designed to encrypt data and require payment for decryption . let me put it another way , This ransomware makes files inaccessible , And ask the victim to pay - To restore access to its data . After successfully penetrating the system ,HYDRA Will encrypt most stored files , Make it unusable .
Besides ,HYDRA Added “ .HYDRA ” Extension ( for example ,“ sample.jpg ” Turn into “ sample.jpg.HYDRA ”).
Once the file is completely destroyed ,HYDRA A pop-up window will open , It contains a message asking for ransom .
Screenshots of messages encouraging users to pay ransom to decrypt their damaged data :

2. suffix .HYDRA How the blackmail virus infected my computer ?
Such as HYDRA Ransomware infections like this usually use fake software updates and “ Crack ”、 Trojan horse 、 Third party software download sources and spam activities to spread . Most fake updates take advantage of outdated software errors / Defect or just download / Install malware instead of promising / Expected updates to infect the computer .
Cyber criminals use third-party download sources ( Point to point [P2P] The Internet 、 Free software download sites 、 Free file hosting website, etc ) Spread malware by presenting malware as legitimate software . such , Users will eventually manually download and install malware .
Last , Cyber criminals use spam to send hundreds of thousands of malicious attachments ( link / file ) E-mails and messages that encourage recipients to open them . These attachments can also be used as “ Important documents ”( for example , invoice 、 bill 、 Receipts or similar documents ) present .
This is to give people an impression of legitimacy . All in all , The main causes of computer infection are inadequate understanding of these threats and careless behavior .
HYDRA Screenshot of encrypted file :

Windows In task manager HYDRA Blackmail software process (“ Firefox ”—— Disguised as a Mozilla Firefox Web browser ):

3. How to restore .HYDRA Blackmail virus ?
This suffix virus file is due to the encryption algorithm , Every infected computer has different server files , It is necessary to independently detect and analyze the virus characteristics and encryption of encrypted files , To determine the most appropriate recovery plan .
Considering the time required for data recovery 、 cost 、 Risk and other factors , If the data is not important , It is recommended to scan the whole disk directly, format and reload the system after antivirus , Follow up system security work can be done . If the infected data does have the value and necessity of recovery , You can add our technical service number (data966) Consult for free to get help with data recovery .
4. How to avoid .crylock Blackmail virus attack ?
- Ignore all emails from unknown mailboxes , These emails have strange unknown addresses , Or the content may have nothing to do with what you are waiting for ( Can you win the prize without participating ?). If the subject of the email may be what you are waiting for , Please carefully check all elements of the suspicious letter . Fake e-mail must contain errors .
- Do not use cracked or untrusted programs . Trojans are usually distributed as part of cracking software , Maybe “ Patch ” In the name of blocking license checks . But untrusted programs are hard to distinguish from trusted software , Because the Trojan horse may also have the functions you need . You can try to find information about this program on the anti malware Forum , But the best solution is not to use such programs .
- To ensure the security of the files you download , Please use safe and reliable anti extortion software . This program will definitely become the perfect protective cover for your personal computer .
边栏推荐
- 文件上传-upload-labs
- Use the kaggle training model and download your own training model
- OpenShift构建镜像
- 2022 Heilongjiang's latest eight member (Safety Officer) simulated test question bank and answers
- Makefile基本原理
- 群辉 NAS 配置 iSCSI 存储
- web安全--逻辑越权
- Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)
- Longest isometric subsequence
- Sentinel 简单使用
猜你喜欢

Use Wireshark to grab TCP three handshakes

St-link connection error invalid ROM table of STM32 difficult and miscellaneous diseases
Openfeign is easy to use
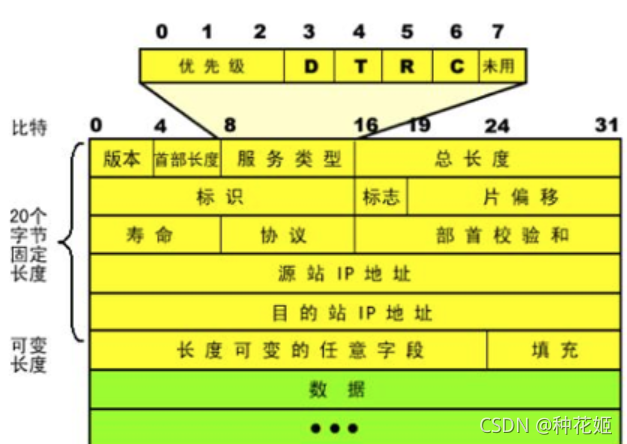
IP protocol and IP address

Solid principle: explanation and examples

2022 Heilongjiang's latest eight member (Safety Officer) simulated test question bank and answers
Sqli labs Level 2

Jumping | Blue Bridge Cup

HCIA - application layer

Realization of basic function of sequence table
随机推荐
链表经典面试题(反转链表,中间节点,倒数第k个节点,合并分割链表,删除重复节点)
web安全--逻辑越权
On November 24, we celebrate the "full moon"
Using C language to realize MySQL true paging
IP protocol and IP address
Classes and objects (instantiation of classes and classes, this, static keyword, encapsulation)
Call Stack
Web security -- core defense mechanism
Causes of laptop jam
STM32-新建工程(参考正点原子)
Pointer initialization
TCP/IP—传输层
Static library and dynamic library
STL quick reference manual
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Use the numbers 5, 5, 5, 1 to perform four operations. Each number should be used only once, and the operation result value is required to be 24
Implementation of bidirectional linked list (simple difference, connection and implementation between bidirectional linked list and unidirectional linked list)
HCIA—應用層
Openfeign is easy to use
使用wireshark抓取Tcp三次握手
