当前位置:网站首页>[BMZCTF-pwn] 12-csaw-ctf-2016-quals hungman
[BMZCTF-pwn] 12-csaw-ctf-2016-quals hungman
2022-07-06 10:43:00 【Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi Shi】
Guess this question or 2.23 ( I'm not going to do it , None of the above questions has a remote environment , And these seem to have been done )
This is a silly word game. The data structure is like this :
- chunk0 Write the largest name you enter 0xf8( It can be small )
- Program record :4 Byte record ,4 Byte name length ,8 Byte name chunk0 The pointer to
- A random number as long as its name
Enter your name first , Then line it into random numbers , Then wait for characters , If there is the same score , altogether 26 How can it be the same if you lose all , When the maximum record is exceeded, the name can be modified ( There is an overflow )
puts("High score! change name?");
__isoc99_scanf(" %c", &v3);
if ( v3 == 121 )
{
s = malloc(0xF8uLL);
memset(s, 0, 0xF8uLL);
v8 = read(0, s, 0xF8uLL);
*(_DWORD *)(a1 + 4) = v8;
v14 = strchr((const char *)s, 10);
if ( v14 )
*v14 = 0;
memcpy(*(void **)(a1 + 8), s, v8); // Name length is less than F8 when , You can enter F8 Overflow to record
free(s);
It's easy to control the overflow to the pointer
Overflow first, write the pointer as got An address of the table , The following output will output the value , So you get libc Address .
The question is which to write , According to the later function call, you can use snprintf and strchr, After looking at the original one, I used libc_start_main
strchr Just use it here once , Let's start with the leak libc Change it to system, Enter next time /bin/sh
Write libc_start_main Then there is gmon_start and memcpy Write here /bin/sh\0,0,system In fact, it uses system cover memcpy In execution memcpy The inner parameter is exactly /bin/sh( This is a coincidence )
If you use snprintf You can also restore the whole got Watch then turn /bin/sh writes 602100
printf Words , Didn't try to write one_gadget Maybe it's ok
边栏推荐
- CSDN问答标签技能树(一) —— 基本框架的构建
- 保姆级手把手教你用C语言写三子棋
- Mysql27 index optimization and query optimization
- Super detailed steps for pushing wechat official account H5 messages
- Implement sending post request with form data parameter
- [Julia] exit notes - Serial
- Chrome浏览器端跨域不能访问问题处理办法
- windows无法启动MYSQL服务(位于本地计算机)错误1067进程意外终止
- [untitled]
- Opencv uses freetype to display Chinese
猜你喜欢
Mysql32 lock
MySQL21-用户与权限管理
CSDN博文摘要(一) —— 一个简单的初版实现
使用OVF Tool工具从Esxi 6.7中导出虚拟机
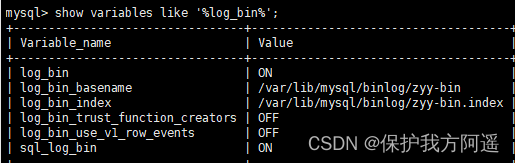
MySQL34-其他数据库日志
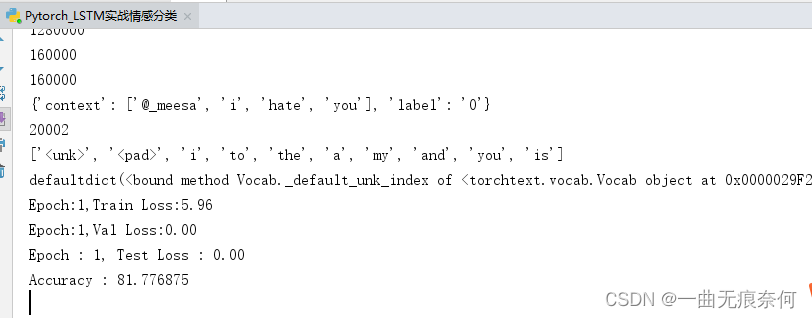
基于Pytorch的LSTM实战160万条评论情感分类
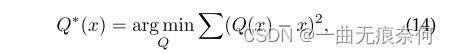
用于实时端到端文本识别的自适应Bezier曲线网络
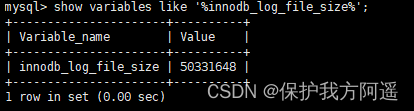
MySQL31-MySQL事务日志

ByteTrack: Multi-Object Tracking by Associating Every Detection Box 论文阅读笔记()
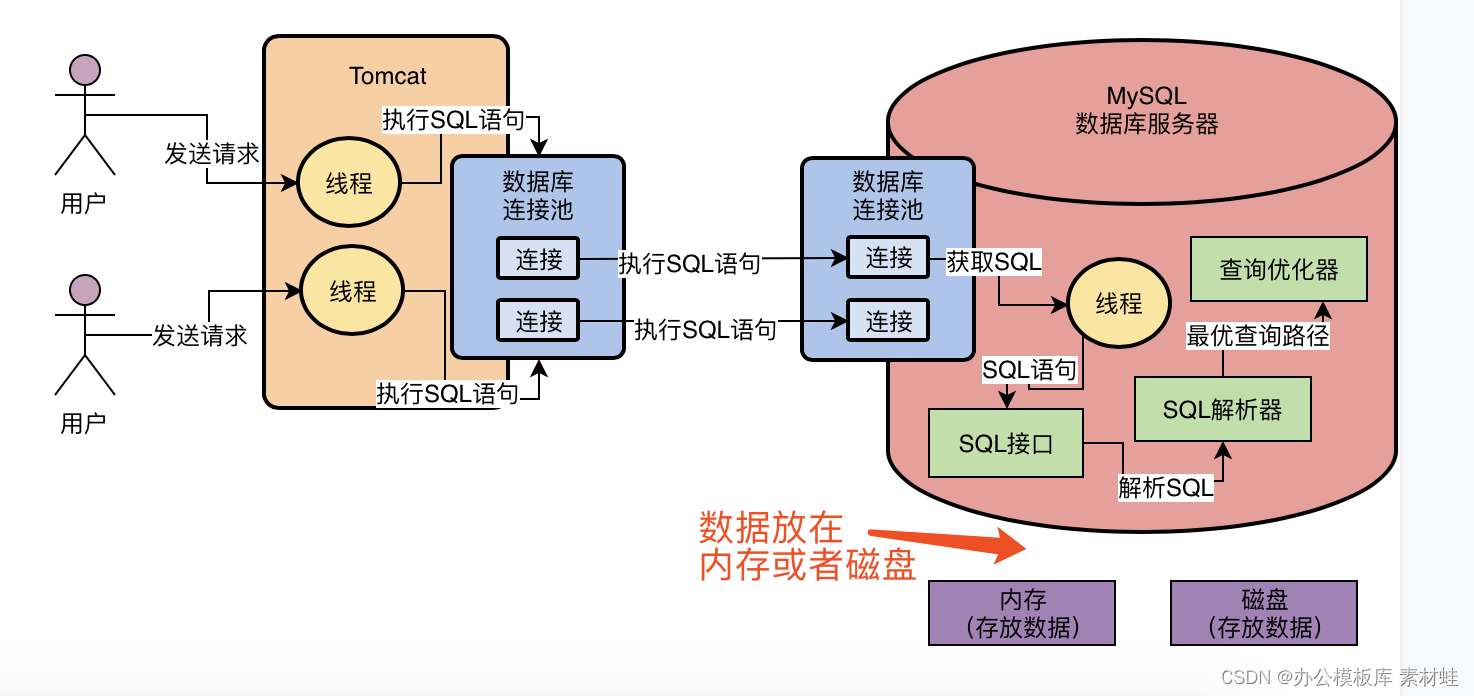
MySQL combat optimization expert 02 in order to execute SQL statements, do you know what kind of architectural design MySQL uses?
随机推荐
Time complexity (see which sentence is executed the most times)
Security design verification of API interface: ticket, signature, timestamp
Mysql26 use of performance analysis tools
Mysql21 - gestion des utilisateurs et des droits
CSDN博文摘要(一) —— 一个简单的初版实现
Timestamp with implicit default value is deprecated error in MySQL 5.6
基于Pytorch肺部感染识别案例(采用ResNet网络结构)
Global and Chinese market of transfer switches 2022-2028: Research Report on technology, participants, trends, market size and share
MySQL31-MySQL事务日志
In fact, the implementation of current limiting is not complicated
[Julia] exit notes - Serial
Breadth first search rotten orange
Valentine's Day is coming, are you still worried about eating dog food? Teach you to make a confession wall hand in hand. Express your love to the person you want
What is the current situation of the game industry in the Internet world?
Global and Chinese market of wafer processing robots 2022-2028: Research Report on technology, participants, trends, market size and share
MySQL18-MySQL8其它新特性
Super detailed steps to implement Wechat public number H5 Message push
Mysql25 index creation and design principles
Const decorated member function problem
Advantages and disadvantages of evaluation methods