当前位置:网站首页>Planning and design of double click hot standby layer 2 network based on ENSP firewall
Planning and design of double click hot standby layer 2 network based on ENSP firewall
2022-07-07 02:36:00 【Ape net】
author :BSXY_19 Family planning _ Chen Yongyue BSXY_ School of information notes : It is forbidden to forward any content without permission
be based on ensp Firewall double click hot standby layer 2 network planning and design
- Preface and resources download
- One 、 Design topo And requirements (15 Requirements )
- Two 、 episode : be based on eNSP A medium-sized campus with a firewall / Enterprise network planning and design
- 3、 ... and 、 Configuration process and corresponding commands
- 1、Eth-Trunk link bundling
- 2、vlan The underlying configuration
- 3、MSTP More trees
- 4、VRRP Gateway configuration
- 5、VRRP Network redundancy verification
- 6、 test PC Through gateway
- 7、DHCP relay
- 8、dhcp snooping To configure
- 9、 Firewall basic configuration and double click hot standby
- 10、OSPF To configure
- 11、RIP To configure
- 12、 A firewall NAT Strategy ( I forgot to configure )
- 13、telnet Remote management configuration
- 14、 Wireless network configuration
Preface and resources download
If you have any questions, you can explain your situation in the comment area , Bloggers will reply as soon as they see it , I hope other people can also reply to other people's questions ,.
It can be realized step by step according to the following design and implementation steps ( Every command is a key command ); However, if necessary, you can also download the complete... According to the following address topo Figure and complete configuration for reference , If you get topo Tukeduo display Check the configuration , Check the corresponding command , The supporting resources are connected as follows
be based on ensp Firewall double click hot standby layer 2 network planning and design ( Orders are complete )_ Reference article _ Configure experimental command notes 
If the above article is not convenient to consult , You can click the link to register the note taking platform
( It's really a good habit to take notes )
First step : First click the following link to register the note taking platform
flowus Note platform registration link
The second step : Click below to refer to this note
( Notes can be copied to your own space with one click to save ) ( All the orders are here )
Share and view notes & Copy Links
Prevent link invalidation , Please save the shared links to your personal space as soon as possible
If it doesn't work , There's nothing we can do about it , Make do with this article
In addition, double-click hot standby is also three-tier , The exit of the firewall is usually the router , All may change in the near future topo chart , It will appear in other articles , Please be patient
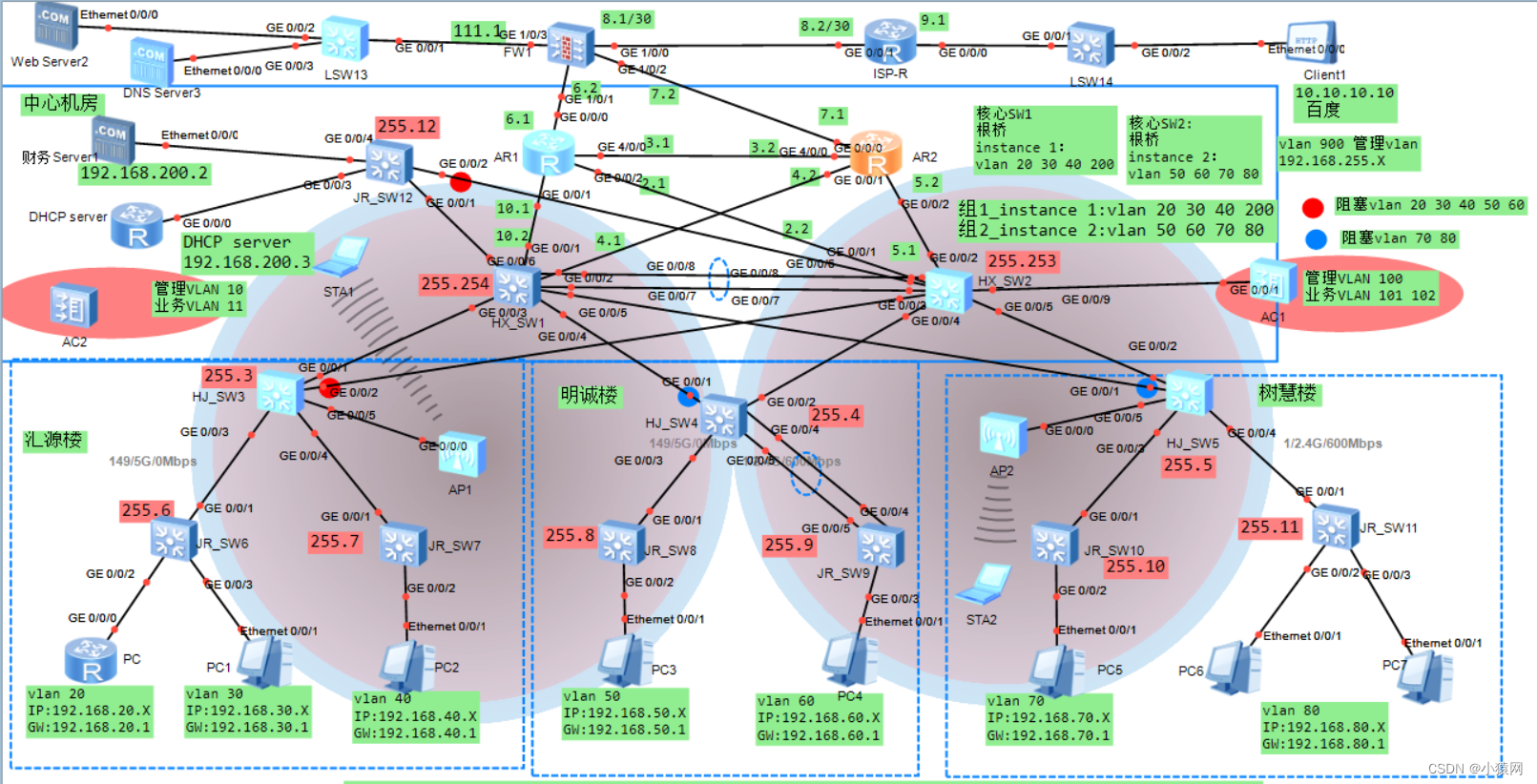
One 、 Design topo And requirements (15 Requirements )
topo chart 01: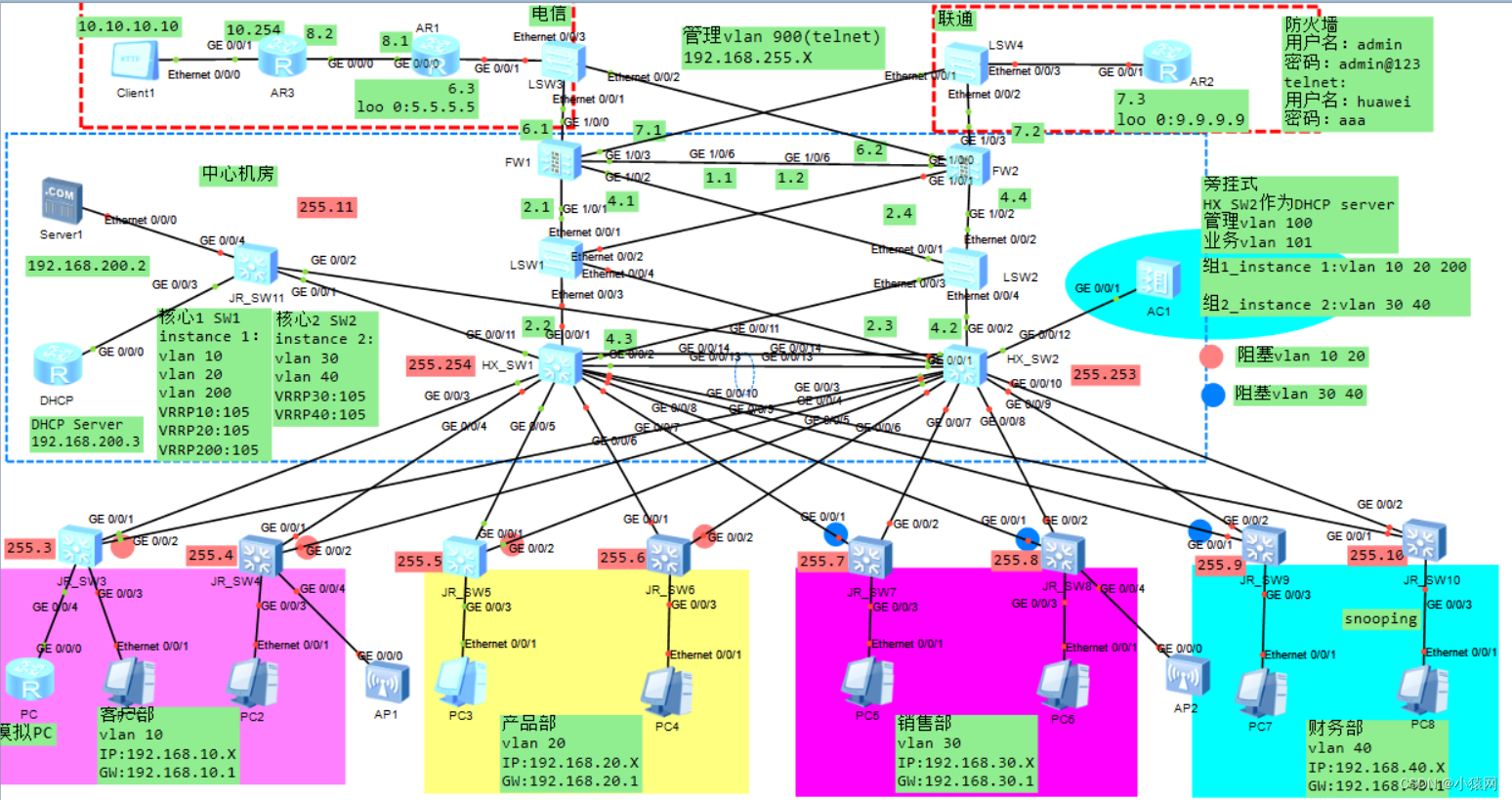
topo chart 02: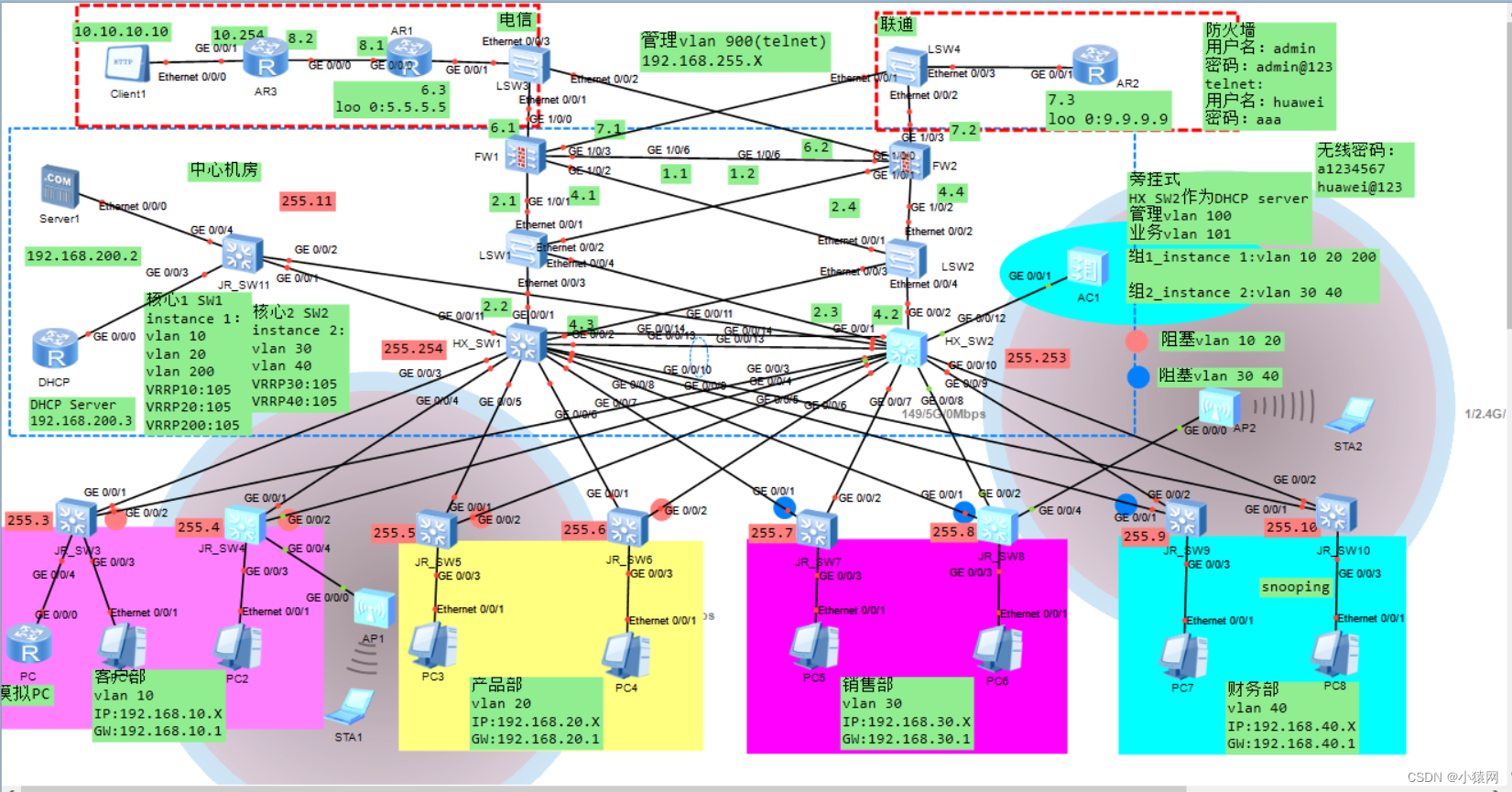
The design requirements :
requirement :
* Finish the server 、 A firewall 、 Configuration of interface addresses such as routers
* To configure Eth-Trunk The link realizes link redundancy
* The enterprise is divided into multiple vlan, Reduce the broadcast domain size , Improve the reliability of the network
* To configure MSTP+VRRP Realize traffic load sharing , At the same time, redundancy is realized , And configure the corresponding stp Optimization techniques stp convergence , And reduce stp Shock
* For the convenience of users surfing the Internet , All users are automatically retrieved IP Address
* To configure DHCP Snooing Isolation is illegal DHCP server
* To configure OSPF Realize three-layer routing interworking with static routing
* Configure in the operator area RIP Enable users to access the corresponding client (10.10.10.10)
* Firewall configuration NAT Policies and security policies , So that users can access the Internet
* The firewall needs to be configured with double-click hot standby to realize redundancy
* By default, access the left ( telecommunication network )
* Users can use the domain name (www.baidu.com) Visit Baidu
* LSW1-LSW12 Switches can be telnet(huawei 5555)
* The network needs to be configured with wireless WLAN, And business vlan 101 102 management vlan 100
* wireless WLAN The network can use the domain name (www.baidu.com) Visit Baidu
Two 、 episode : be based on eNSP A medium-sized campus with a firewall / Enterprise network planning and design
episode 2:
following topo yes be based on eNSP A medium-sized campus with a firewall / Enterprise network planning and design ( All configuration commands are attached ), But there is no explanation and introduction in this article , If necessary, you can click this connection to check ,topo The drawings and requirements are as follows :
15 The requirements are as follows :
- Finish the server 、 A firewall 、 Configuration of interface addresses such as routers
- To configure Eth-Trunk Link bundling enables link redundancy
- The enterprise is divided into multiple vlan, Reduce the broadcast domain size , Improve the reliability of the network
- To configure MSTP+VRRP Realize traffic load sharing , At the same time, redundancy is realized , And configure the corresponding stp Optimization techniques stp convergence , And reduce stp Shock
- All users are automatically retrieved IP Address
- Configure corresponding DHCP snooping Isolation is illegal DHCP server
- To configure OSPF Realize three-layer routing interworking with static routing
- Firewall configuration security policy , Release the intranet area to dmz Flow in the zone
- Firewall configuration NAT Policies and security policies , So that users can access the Internet Baidu
- Firewall configuration server mapping and security policy , Allow Internet users Client Through the public address 100.100.100.100 visit web The server
- Configure corresponding policies for firewall , Allow Internet users Client Through the public network http://100.100.100.100 Access login web The server
- Users can use the domain name (www.baidu.com) Visit Baidu
- The internal financial server only allows vlan 50 User access
- LSW1-LSW12 Switches can be telent(huawei 5555)
- wireless WLAN To configure , And business vlan 101 102 You can also use the domain name (www.baidu.com) Visit Baidu
3、 ... and 、 Configuration process and corresponding commands
1、Eth-Trunk link bundling
HX_SW1:
<Huawei>system-view
[Huawei]un in en
[Huawei]sysname HX_SW1
[HX_SW1]int Eth-Trunk 1
[HX_SW1-Eth-Trunk1]mode lacp-static
[HX_SW1-Eth-Trunk1]trunkport g0/0/13
[HX_SW1-Eth-Trunk1]trunkport g0/0/14
------------------------------------
HX_SW2:
<Huawei>sys
[Huawei]un in en
[Huawei]sysname HX_SW2
[HX_SW2]int Eth-Trunk 1
[HX_SW2-Eth-Trunk1]mode lacp-static
[HX_SW2-Eth-Trunk1]trunkport g0/0/13
[HX_SW2-Eth-Trunk1]trunkport g0/0/14
[HX_SW2-Eth-Trunk1]qui
2、vlan The underlying configuration
[HX_SW1]vlan batch 10 20 30 40 2 4 200 900
[HX_SW1]int g0/0/3
[HX_SW1-GigabitEthernet0/0/3]port link-type trunk
[HX_SW1-GigabitEthernet0/0/3]port trunk allow-pass vlan 10 900
[HX_SW1-GigabitEthernet0/0/3]int g0/0/4
[HX_SW1-GigabitEthernet0/0/4]port link-type trunk
[HX_SW1-GigabitEthernet0/0/4]port trunk allow-pass vlan 10 900
[HX_SW1-GigabitEthernet0/0/4]int g0/0/5
[HX_SW1-GigabitEthernet0/0/5]port link-type trunk
[HX_SW1-GigabitEthernet0/0/5]port trunk allow-pass vlan 20 900
[HX_SW1-GigabitEthernet0/0/5]int g0/0/6
[HX_SW1-GigabitEthernet0/0/6]port link-type trunk
[HX_SW1-GigabitEthernet0/0/6]port trunk allow-pass vlan 20 900
[HX_SW1-GigabitEthernet0/0/6]int g0/0/7
[HX_SW1-GigabitEthernet0/0/7]port link-type trunk
[HX_SW1-GigabitEthernet0/0/7]port trunk allow-pass vlan 30 900
[HX_SW1-GigabitEthernet0/0/7]int g0/0/8
[HX_SW1-GigabitEthernet0/0/8]port link-type trunk
[HX_SW1-GigabitEthernet0/0/8]port trunk allow-pass vlan 30 900
[HX_SW1-GigabitEthernet0/0/8]int g0/0/9
[HX_SW1-GigabitEthernet0/0/9]port link-type trunk
[HX_SW1-GigabitEthernet0/0/9]port trunk allow-pass vlan 40 900
[HX_SW1-GigabitEthernet0/0/9]int g0/0/10
[HX_SW1-GigabitEthernet0/0/10]port link-type trunk
[HX_SW1-GigabitEthernet0/0/10]port trunk allow-pass vlan 40 900
[HX_SW1-GigabitEthernet0/0/10]int g0/0/11
[HX_SW1-GigabitEthernet0/0/11]port link-type trunk
[HX_SW1-GigabitEthernet0/0/11]port trunk allow-pass vlan 200 900
[HX_SW1-GigabitEthernet0/0/11]int g0/0/1
[HX_SW1-GigabitEthernet0/0/1]port link-type access
[HX_SW1-GigabitEthernet0/0/1]port default vlan 2
[HX_SW1-GigabitEthernet0/0/1]int g0/0/2
[HX_SW1-GigabitEthernet0/0/2]port link-type access
[HX_SW1-GigabitEthernet0/0/2]port default vlan 3
[HX_SW1-GigabitEthernet0/0/2]qui
[HX_SW1]int Eth-Trunk 1
[HX_SW1-Eth-Trunk1]port link-type trunk
[HX_SW1-Eth-Trunk1]port trunk allow-pass vlan all
[HX_SW1-Eth-Trunk1]qui
------------------------------------
HX_SW2:
[HX_SW2]vlan batch 10 20 30 40 2 4 200 900
[HX_SW2]int g0/0/3
[HX_SW2-GigabitEthernet0/0/3]port link-type trunk
[HX_SW2-GigabitEthernet0/0/3]port trunk allow-pass vlan 10 900
[HX_SW2-GigabitEthernet0/0/3]int g0/0/4
[HX_SW2-GigabitEthernet0/0/4]port link-type trunk
[HX_SW2-GigabitEthernet0/0/4]port trunk allow-pass vlan 10 900
[HX_SW2-GigabitEthernet0/0/4]int g0/0/5
[HX_SW2-GigabitEthernet0/0/5]port link-type trunk
[HX_SW2-GigabitEthernet0/0/5]port trunk allow-pass vlan 20 900
[HX_SW2-GigabitEthernet0/0/5]int g0/0/6
[HX_SW2-GigabitEthernet0/0/6]port link-type trunk
[HX_SW2-GigabitEthernet0/0/6]port trunk allow-pass vlan 20 900
[HX_SW2-GigabitEthernet0/0/6]int g0/0/7
[HX_SW2-GigabitEthernet0/0/7]port link-type trunk
[HX_SW2-GigabitEthernet0/0/7]port trunk allow-pass vlan 30 900
[HX_SW2-GigabitEthernet0/0/7]int g0/0/8
[HX_SW2-GigabitEthernet0/0/8]port link-type trunk
[HX_SW2-GigabitEthernet0/0/8]port trunk allow-pass vlan 30 900
[HX_SW2-GigabitEthernet0/0/8]int g0/0/9
[HX_SW2-GigabitEthernet0/0/9]port link-type trunk
[HX_SW2-GigabitEthernet0/0/9]port trunk allow-pass vlan 40 900
[HX_SW2-GigabitEthernet0/0/9]int g0/0/10
[HX_SW2-GigabitEthernet0/0/10]port link-type trunk
[HX_SW2-GigabitEthernet0/0/10]port trunk allow-pass vlan 40 900
[HX_SW2-GigabitEthernet0/0/10]int g0/0/11
[HX_SW2-GigabitEthernet0/0/11]port link-type trunk
[HX_SW2-GigabitEthernet0/0/11]port trunk allow-pass vlan 200 900
[HX_SW2-GigabitEthernet0/0/11]int g0/0/1
[HX_SW2-GigabitEthernet0/0/1]port link-type access
[HX_SW2-GigabitEthernet0/0/1]port default vlan 7
[HX_SW2-GigabitEthernet0/0/1]int g0/0/2
[HX_SW2-GigabitEthernet0/0/2]port link-type access
[HX_SW2-GigabitEthernet0/0/2]port default vlan 4
[HX_SW2-GigabitEthernet0/0/2]qui
[HX_SW2]int Eth-Trunk 1
[HX_SW2-Eth-Trunk1]port link-type trunk
[HX_SW2-Eth-Trunk1]port link-type trunk
[HX_SW2-Eth-Trunk1]port trunk allow-pass vlan all
[HX_SW2-Eth-Trunk1]qui
------------------------------------
JR_SW3:
<Huawei>sy
[Huawei]un in en
[Huawei]sys
[Huawei]sysname JR_SW2
[JR_SW3]vlan batch 10 20 30 40 900
[JR_SW3]int g0/0/1
[JR_SW3-GigabitEthernet0/0/1]port link-type trunk
[JR_SW3-GigabitEthernet0/0/1]port trunk allow-pass vlan 10 900
[JR_SW3-GigabitEthernet0/0/1]int g0/0/2
[JR_SW3-GigabitEthernet0/0/2]port link-type trunk
[JR_SW3-GigabitEthernet0/0/2]port trunk allow-pass vlan 10 900
[JR_SW3-GigabitEthernet0/0/2]int g0/0/3
[JR_SW3-GigabitEthernet0/0/3]port link-type access
[JR_SW3-GigabitEthernet0/0/3]port default vlan 10
[JR_SW3-GigabitEthernet0/0/3]int g0/0/4
[JR_SW3-GigabitEthernet0/0/4]port link-type access
[JR_SW3-GigabitEthernet0/0/4]port default vlan 10
[JR_SW3-GigabitEthernet0/0/4]qui
[JR_SW3]qui
------------------------------------
JR_SW4:
<Huawei>sy
[Huawei]un in en
[Huawei]sysname JR_SW4
[JR_SW4]vlan batch 10 20 30 40 900
[JR_SW4]int g0/0/1
[JR_SW4-GigabitEthernet0/0/1]port link-type trunk
[JR_SW4-GigabitEthernet0/0/1]port trunk allow-pass vlan 10 900
[JR_SW4-GigabitEthernet0/0/1]int g0/0/2
[JR_SW4-GigabitEthernet0/0/2]port link-type trunk
[JR_SW4-GigabitEthernet0/0/2]port trunk allow-pass vlan 10 900
[JR_SW4-GigabitEthernet0/0/2]int g0/0/3
[JR_SW4-GigabitEthernet0/0/3]port link-type access
[JR_SW4-GigabitEthernet0/0/3]port default vlan 10
[JR_SW4-GigabitEthernet0/0/3]qui
------------------------------------
JRS_SW5:
<Huawei>SY
[Huawei]un in en
[Huawei]sysname JR_SW5
[JR_SW5]vlan batch 10 20 30 40 900
[JR_SW5]int g0/0/1
[JR_SW5-GigabitEthernet0/0/1]port link-type trunk
[JR_SW5-GigabitEthernet0/0/1]port trunk allow-pass vlan 20 900
[JR_SW5-GigabitEthernet0/0/1]int g0/0/2
[JR_SW5-GigabitEthernet0/0/2]port link-type trunk
[JR_SW5-GigabitEthernet0/0/2]port trunk allow-pass vlan 20 900
[JR_SW5-GigabitEthernet0/0/2]int g0/0/3
[JR_SW5-GigabitEthernet0/0/3]port link-type access
[JR_SW5-GigabitEthernet0/0/3]port default vlan 20
[JR_SW5-GigabitEthernet0/0/3]qui
------------------------------------
JR_SW6:
<Huawei>sys
[Huawei]un in en
[Huawei]sysname JR_SW6
[JR_SW6]vlan batch 10 20 30 40 900
[JR_SW6]int g0/0/1
[JR_SW6-GigabitEthernet0/0/1]port link-type trunk
[JR_SW6-GigabitEthernet0/0/1]port trunk allow-pass vlan 20 900
[JR_SW6-GigabitEthernet0/0/1]int g0/0/2
[JR_SW6-GigabitEthernet0/0/2]port link-type trunk
[JR_SW6-GigabitEthernet0/0/2]port trunk allow-pass vlan 20 900
[JR_SW6-GigabitEthernet0/0/2]int g0/0/3
[JR_SW6-GigabitEthernet0/0/3]port link-type access
[JR_SW6-GigabitEthernet0/0/3]port default vlan 20
[JR_SW6-GigabitEthernet0/0/3]qui
------------------------------------
JR_SW7:
<Huawei>SY
[Huawei]un in en
[Huawei]sysname JR_SW7
[JR_SW7]vlan batch 10 20 30 40 900
[JR_SW7]int g0/0/1
[JR_SW7-GigabitEthernet0/0/1]port link-type trunk
[JR_SW7-GigabitEthernet0/0/1]port trunk allow-pass vlan 30 900
[JR_SW7-GigabitEthernet0/0/1]int g0/0/2
[JR_SW7-GigabitEthernet0/0/2]port link-type trunk
[JR_SW7-GigabitEthernet0/0/2]port trunk allow-pass vlan 30 900
[JR_SW7-GigabitEthernet0/0/2]int g0/0/3
[JR_SW7-GigabitEthernet0/0/3]port link-type access
[JR_SW7-GigabitEthernet0/0/3]port default vlan 30
[JR_SW7-GigabitEthernet0/0/3]qui
------------------------------------
JR_SW8: A little
JR_SW9: A little
JR_SW10: A little
------------------------------------
JR_11:
<Huawei>SY
[Huawei]un in en
[Huawei]sysname JR_SW11
[JR_SW11]vlan batch 10 20 30 40 200 900
[JR_SW11]int g0/0/1
[JR_SW11-GigabitEthernet0/0/1]port link-type trunk
[JR_SW11-GigabitEthernet0/0/1]port trunk allow-pass vlan 200 900
[JR_SW11-GigabitEthernet0/0/1]int g0/0/2
[JR_SW11-GigabitEthernet0/0/2]port link-type trunk
[JR_SW11-GigabitEthernet0/0/2]port trunk allow-pass vlan 200 900
[JR_SW11-GigabitEthernet0/0/2]int g0/0/3
[JR_SW11-GigabitEthernet0/0/3]port link-type access
[JR_SW11-GigabitEthernet0/0/3]port default vlan 200
[JR_SW11-GigabitEthernet0/0/3]int g0/0/4
[JR_SW11-GigabitEthernet0/0/4]port link-type access
[JR_SW11-GigabitEthernet0/0/4]port default vlan 200
[JR_SW11-GigabitEthernet0/0/4]qui
3、MSTP More trees
HX_SW1:
<HX_SW1>sys
[HX_SW1]stp region-configuration
[HX_SW1-mst-region]region-name aaa
[HX_SW1-mst-region]revision-level 1
[HX_SW1-mst-region]instance 1 vlan 10 20 200
[HX_SW1-mst-region]instance 2 vlan 30 40
[HX_SW1-mst-region]active region-configuration
[HX_SW1-mst-region]dis this
#
stp region-configuration
region-name aaa
revision-level 1
instance 1 vlan 10 20 200
instance 2 vlan 30 40
active region-configuration
#
return
[HX_SW1-mst-region]qui
[HX_SW1]stp instance 1 root primary
[HX_SW1]stp instance 2 root secondary
------------------------------------
HX_SW2:
[HX_SW2]stp region-configuration
[HX_SW2-mst-region]region-name aaa
[HX_SW2-mst-region]revision-level 1
[HX_SW2-mst-region]instance 1 vlan 10 20 200
[HX_SW2-mst-region]instance 2 vlan 30 40
[HX_SW2-mst-region]active region-configuration
[HX_SW2-mst-region]qui
[HX_SW2]stp instance 2 root primary
[HX_SW2]stp instance 1 root secondary
------------------------------------
JR_SW3:
[JR_SW3]stp region-configuration
[JR_SW3-mst-region]region-name aaa
[JR_SW3-mst-region]revision-level 1
[JR_SW3-mst-region]instance 1 vlan 10 20 200
[JR_SW3-mst-region]instance 2 vlan 30 40
[JR_SW3-mst-region]active region-configuration
Info: This operation may take a few seconds. Please wait for a moment...done.
[JR_SW3-mst-region]qui
[JR_SW3]dis stp br
MSTID Port Role STP State Protection
1 GigabitEthernet0/0/1 ROOT FORWARDING NONE
1 GigabitEthernet0/0/2 ALTE DISCARDING NONE
// Find out g/0/2 It's a jam (DISCARDING) That's it
------------------------------------
JR_SW4:
[JR_SW4]stp region-configuration
[JR_SW4-mst-region]region-name aaa
[JR_SW4-mst-region]revision-level 1
[JR_SW4-mst-region]instance 1 vlan 10 20 200
[JR_SW4-mst-region]instance 2 vlan 30 40
[JR_SW4-mst-region]active region-configuration
Info: This operation may take a few seconds. Please wait for a moment...done.
[JR_SW4-mst-region]qui
[JR_SW4]dis stp br
MSTID Port Role STP State Protection
1 GigabitEthernet0/0/1 ROOT FORWARDING NONE
1 GigabitEthernet0/0/2 ALTE DISCARDING NONE
// Find out g/0/2 It's a jam (DISCARDING) That's it
------------------------------------
JR_SW5: A little
JR_SW6: A little
JR_SW7: A little
JR_SW8: A little
JR_SW9: A little
JR_SW10: A little
------------------------------------
JR_SW11:
[JR_SW11]stp region-configuration
[JR_SW11-mst-region]region-name aaa
[JR_SW11-mst-region]revision-level 1
[JR_SW11-mst-region]instance 1 vlan 10 20 200
[JR_SW11-mst-region]instance 2 vlan 30 40
[JR_SW11-mst-region]active region-configuration
Info: This operation may take a few seconds. Please wait for a moment...done.
[JR_SW11-mst-region]qui
[JR_SW11]dis stp br
MSTID Port Role STP State Protection
0 GigabitEthernet0/0/1 ALTE DISCARDING NONE
0 GigabitEthernet0/0/2 ROOT FORWARDING NONE
0 GigabitEthernet0/0/3 DESI DISCARDING NONE
1 GigabitEthernet0/0/1 ROOT FORWARDING NONE
1 GigabitEthernet0/0/2 ALTE DISCARDING NONE
1 GigabitEthernet0/0/3 DESI DISCARDING NONE
Find out g/0/2 It's a jam (DISCARDING) That's it
4、VRRP Gateway configuration
HX_SW1:
[HX_SW1]int vlan 10
[HX_SW1-Vlanif10]ip add 192.168.10.254 24
[HX_SW1-Vlanif10]vrrp vrid 10 virtual-ip 192.168.10.1
[HX_SW1-Vlanif10]vrrp vrid 10 priority 105
[HX_SW1-Vlanif10]dis this
#
interface Vlanif10
ip address 192.168.10.254 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.1
vrrp vrid 10 priority 105
#
return
[HX_SW1-Vlanif10]qui
[HX_SW1]int vlan 20
[HX_SW1-Vlanif20]ip add 192.168.20.254 24
[HX_SW1-Vlanif20]vrrp vrid 20 virtual-ip 192.168.20.1
[HX_SW1-Vlanif20]vrrp vrid 20 priority 105
[HX_SW1-Vlanif20]qui
[HX_SW1]int vlan 200
[HX_SW1-Vlanif200]ip add 192.168.200.254 24
[HX_SW1-Vlanif200]vrrp vrid 200 virtual-ip 192.168.200.1
[HX_SW1-Vlanif200]vrrp vrid 200 priority 105
[HX_SW1-Vlanif200]int vlan 30
[HX_SW1-Vlanif30]ip add 192.168.30.254 24
[HX_SW1-Vlanif30]vrrp vrid 30 virtual-ip 192.168.30.1
[HX_SW1-Vlanif30]int vlan 40
[HX_SW1-Vlanif40]ip add 192.168.40.254 24
[HX_SW1-Vlanif40]vrrp vrid 40 virtual-ip 192.168.40.1
------------------------------------
HX_SW2:
[HX_SW2]int vlan 30
[HX_SW2-Vlanif30]ip add 192.168.30.253 24
[HX_SW2-Vlanif30]vrrp vrid 30 virtual-ip 192.168.30.1
[HX_SW2-Vlanif30]vrrp vrid 30 priority 105
[HX_SW2-Vlanif30]dis this
#
interface Vlanif30
ip address 192.168.30.253 255.255.255.0
vrrp vrid 30 virtual-ip 192.168.30.1
vrrp vrid 30 priority 105
#
return
[HX_SW2-Vlanif30]qui
[HX_SW2]int vlan 40
[HX_SW2-Vlanif40]ip add 192.168.40.253 24
[HX_SW2-Vlanif40]vrrp vrid 40 virtual-ip 192.168.40.1
[HX_SW2-Vlanif40]vrrp vrid 40 priority 105
[HX_SW2-Vlanif40]qui
[HX_SW2]int vlan 200
[HX_SW2-Vlanif200]ip add 192.168.200.253 24
[HX_SW2-Vlanif200]vrrp vrid 200 virtual-ip 192.168.200.1
[HX_SW2-Vlanif200]int vlan 10
[HX_SW2-Vlanif10]ip add 192.168.10.253 24
[HX_SW2-Vlanif10]vrrp vrid 10 virtual-ip 192.168.10.1
[HX_SW2-Vlanif10]int vlan 20
[HX_SW2-Vlanif20]ip add 192.168.20.253 24
[HX_SW2-Vlanif20]vrrp vrid 20 virtual-ip 192.168.20.1
[HX_SW2-Vlanif20]qui
5、VRRP Network redundancy verification
HX_SW1:
<HX_SW1>dis vrrp br
VRID State Interface Type Virtual IP
----------------------------------------------------------------
10 Master Vlanif10 Normal 192.168.10.1
20 Master Vlanif20 Normal 192.168.20.1
30 Backup Vlanif30 Normal 192.168.30.1
40 Backup Vlanif40 Normal 192.168.40.1
200 Master Vlanif200 Normal 192.168.200.1
<HX_SW1>
------------------------------------
HX_SW2:
<HX_SW2>dis vrrp br
VRID State Interface Type Virtual IP
----------------------------------------------------------------
10 Backup Vlanif10 Normal 192.168.10.1
20 Backup Vlanif20 Normal 192.168.20.1
30 Master Vlanif30 Normal 192.168.30.1
40 Master Vlanif40 Normal 192.168.40.1
200 Backup Vlanif200 Normal 192.168.200.1
<HX_SW2>
6、 test PC Through gateway
/* Hand to PC To configure IP Address access gateway , If given vlan3 Under the PC To configure IP:192.168.30.3 GW:192.168.30.1 Test access gateway ,ping 192.168.30.1 Just pass */
/* Hand to PC To configure IP Address access gateway , If given vlan3 Under the PC To configure IP:192.168.70.7 GW:192.168.70.1 Test access gateway ,ping 192.168.70.1 Just pass */
7、DHCP relay
DHCP:
<Huawei>sys
[Huawei]un in en
[Huawei]sysname DHCP
[DHCP]dhcp enable
[DHCP]ip pool vlan10
Info: It's successful to create an IP address pool.
[DHCP-ip-pool-vlan10]network 192.168.10.0 mask 24
[DHCP-ip-pool-vlan10]gateway-list 192.168.10.1
[DHCP-ip-pool-vlan10]dns-list 192.168.200.2 8.8.8.8
[DHCP-ip-pool-vlan10]excluded-ip-address 192.168.10.250 192.168.10.254
[DHCP-ip-pool-vlan10]q
[DHCP]ip pool vlan20
Info: It's successful to create an IP address pool.
[DHCP-ip-pool-vlan20]network 192.168.20.0 mask 24
[DHCP-ip-pool-vlan20]gateway-list 192.168.20.1
[DHCP-ip-pool-vlan20]dns-list 192.168.200.2 8.8.8.8
[DHCP-ip-pool-vlan20]excluded-ip-address 192.168.20.250 192.168.20.254
[DHCP-ip-pool-vlan20]q
[DHCP]ip pool vlan30
Info: It's successful to create an IP address pool.
[DHCP-ip-pool-vlan30]gateway-list 192.168.30.1
[DHCP-ip-pool-vlan30]network 192.168.30.0 mask 255.255.255.0
[DHCP-ip-pool-vlan30]dns-list 192.168.200.2 8.8.8.8
[DHCP-ip-pool-vlan30]excluded-ip-address 192.168.30.250 192.168.30.254
[DHCP-ip-pool-vlan30]q
[DHCP]ip pool vlan40
Info: It's successful to create an IP address pool.
[DHCP-ip-pool-vlan40]gateway-list 192.168.40.1
[DHCP-ip-pool-vlan40]network 192.168.40.0 mask 255.255.255.0
[DHCP-ip-pool-vlan40]dns-list 192.168.200.2 8.8.8.8
[DHCP-ip-pool-vlan40]excluded-ip-address 192.168.40.250 192.168.40.254
[DHCP-ip-pool-vlan40]q
[DHCP]int g0/0/0
[DHCP-GigabitEthernet0/0/0]ip add 192.168.200.3 24
[DHCP-GigabitEthernet0/0/0]dhcp select global
[DHCP-GigabitEthernet0/0/0]dis this
[DHCP-GigabitEthernet0/0/0]quit
[DHCP]ip route-static 0.0.0.0 0 192.168.200.1
------------------------------------
HX_SW1:
<HX_SW1>sy
[HX_SW1]dhcp enable
[HX_SW1]int vlanif10
[HX_SW1-Vlanif10]dhcp select relay
[HX_SW1-Vlanif10]dhcp relay server-ip 192.168.200.3
[HX_SW1-Vlanif10]int vlanif20
[HX_SW1-Vlanif20]dhcp select relay
[HX_SW1-Vlanif20]dhcp relay server-ip 192.168.200.3
[HX_SW1-Vlanif20]int vlanif30
[HX_SW1-Vlanif30]dhcp select relay
[HX_SW1-Vlanif30]dhcp select relay
[HX_SW1-Vlanif30]dhcp relay server-ip 192.168.200.3
[HX_SW1-Vlanif30]int vlanif40
[HX_SW1-Vlanif40]dhcp select relay
[HX_SW1-Vlanif40]dhcp relay server-ip 192.168.200.3
[HX_SW1-Vlanif40]qui
[HX_SW1]qui
------------------------------------
HX_SW2:
<HX_SW2>sy
[HX_SW2]dhcp enable
[HX_SW2]int vlanif10
[HX_SW2-Vlanif10]dhcp select relay
[HX_SW2-Vlanif10]dhcp relay server-ip 192.168.200.3
[HX_SW2-Vlanif10]int vlanif20
[HX_SW2-Vlanif20]dhcp select relay
[HX_SW2-Vlanif20]dhcp relay server-ip 192.168.200.3
[HX_SW2-Vlanif20]int vlanif30
[HX_SW2-Vlanif30]dhcp select relay
[HX_SW2-Vlanif30]dhcp relay server-ip 192.168.200.3
[HX_SW2-Vlanif30]int vlanif40
[HX_SW2-Vlanif40]dhcp select relay
[HX_SW2-Vlanif40]dhcp relay server-ip 192.168.200.3
[HX_SW2-Vlanif40]qui
[HX_SW2]qui
8、dhcp snooping To configure
The function of isolation is illegal dhcp server, By configuring trusted and non trusted ports ; But it will also give PC obtain IP The speed of the address becomes slower
JR_SW3:
[JR_SW3]dhcp enable
[JR_SW3]dhcp snooping enable
[JR_SW3]vlan 10
[JR_SW3-vlan10]dhcp snooping enable
[JR_SW3-vlan10]qui
[JR_SW3]int g0/0/1
[JR_SW3-GigabitEthernet0/0/1]dhcp snooping trusted
[JR_SW3-GigabitEthernet0/0/1]int g0/0/2
[JR_SW3-GigabitEthernet0/0/2]dhcp snooping trusted
[JR_SW3-GigabitEthernet0/0/2]dis this
------------------------------------
JR_SW4:
[JR_SW4]dhcp enable
[JR_SW4]dhcp snooping enable
[JR_SW4]vlan 10
[JR_SW4-vlan10]dhcp snooping enable
[JR_SW4-vlan10]qui
[JR_SW4]int g0/0/1
[JR_SW4-GigabitEthernet0/0/1]dhcp snooping trusted
[JR_SW4-GigabitEthernet0/0/1]int g0/0/2
[JR_SW4-GigabitEthernet0/0/2]dhcp snooping trusted
[JR_SW4-GigabitEthernet0/0/2]dis this
------------------------------------
JR_SW5:
[JR_SW5]dhcp enable
[JR_SW5]dhcp snooping enable
[JR_SW5]vlan 20
[JR_SW5-vlan20]dhcp snooping enable
[JR_SW5-vlan20]qui
[JR_SW5]int g0/0/1
[JR_SW5-GigabitEthernet0/0/1]dhcp snooping trusted
[JR_SW5-GigabitEthernet0/0/1]int g0/0/2
[JR_SW5-GigabitEthernet0/0/2]dhcp snooping trusted
[JR_SW5-GigabitEthernet0/0/2]dis this
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20 900
dhcp snooping trusted
#
return
[JR_SW5-GigabitEthernet0/0/2]qui
------------------------------------
JR_SW6: A little
JR_SW7: A little
JR_SW8: A little
JR_SW9: A little
------------------------------------
JR_SW10:
[JR_SW10]dhcp enable
[JR_SW10]dhcp snooping enable
[JR_SW10]vlan 40
[JR_SW10-vlan40]dhcp snooping enable
[JR_SW10-vlan40]qui
[JR_SW10]int g0/0/1
[JR_SW10-GigabitEthernet0/0/1]dhcp snooping trusted
[JR_SW10-GigabitEthernet0/0/1]int g0/0/2
[JR_SW10-GigabitEthernet0/0/2]dhcp snooping trusted
[JR_SW10-GigabitEthernet0/0/2]dis this
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 20 900
dhcp snooping trusted
#
return
[JR_SW5-GigabitEthernet0/0/2]qui
9、 Firewall basic configuration and double click hot standby
FW1:
[FW1]un in en
[FW1]sysname FW1
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ip add 192.168.6.1 24
[FW1-GigabitEthernet1/0/0]service-manage all permit
[FW1-GigabitEthernet1/0/0]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 192.168.2.1 24
[FW1-GigabitEthernet1/0/1]service-manage all permit
[FW1-GigabitEthernet1/0/1]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip add 192.168.4.1 24
[FW1-GigabitEthernet1/0/2]service-manage all permit
[FW1-GigabitEthernet1/0/2]int g1/0/3
[FW1-GigabitEthernet1/0/3]ip add 192.168.7.1 24
[FW1-GigabitEthernet1/0/3]service-manage all permit
[FW1-GigabitEthernet1/0/3]int g1/0/6
[FW1-GigabitEthernet1/0/6]ip add 192.168.1.1 24
[FW1-GigabitEthernet1/0/6]service-manage all permit
[FW1-GigabitEthernet1/0/6]qui
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g1/0/0
[FW1-zone-untrust]add int g1/0/3
[FW1-zone-untrust]qui
[FW1]firewall zone trust
[FW1-zone-trust]add int g1/0/1
[FW1-zone-trust]add int g1/0/2
[FW1-zone-trust]qui
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g1/0/6
[FW1-zone-dmz]qui
[FW1]ip route-static 0.0.0.0 0 192.168.6.3
[FW1]ip route-static 0.0.0.0 0 192.168.7.3 preference 70
[FW1]security-policy
[FW1-policy-security]rule name permit_heat
[FW1-policy-security-rule-permit_heat]source-zone local
[FW1-policy-security-rule-permit_heat]destination-zone dmz
[FW1-policy-security-rule-permit_heat]action permit
[FW1-policy-security-rule-permit_heat]q
[FW1-policy-security]rule name permit_trust_untrust
[FW1-policy-security-rule-permit_trust_untrust]source-zone trust
[FW1-policy-security-rule-permit_trust_untrust]destination-zone untrust
[FW1-policy-security-rule-permit_trust_untrust]action permit
[FW1-policy-security-rule-permit_trust_untrust]q
[FW1-policy-security]q
[FW1]int g1/0/1
[FW1-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 192.168.2.100 active
[FW1-GigabitEthernet1/0/1]qui
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]vrrp vrid 6 virtual-ip 192.168.6.100 active
[FW1-GigabitEthernet1/0/0]qui
[FW1]int g1/0/2
[FW1-GigabitEthernet1/0/2]vrrp vrid 4 virtual-ip 192.168.4.100 active
[FW1-GigabitEthernet1/0/2]qui
[FW1]int g1/0/3
[FW1-GigabitEthernet1/0/3]vrrp vrid 7 virtual-ip 192.168.7.100 active
[FW1-GigabitEthernet1/0/3]qui
[FW1]hrp interface g1/0/6 remote 192.168.1.2
[FW1]hrp en
HRP_S[FW1]hrp auto-sync
HRP_S[FW1]dis hrp state
HRP_S[FW1]dis hrp int
------------------------------------
FW2:
[FW2]un in en
[FW2]sysname FW2
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]ip add 192.168.6.2 24
[FW2-GigabitEthernet1/0/0]service-manage all permit
[FW2-GigabitEthernet1/0/0]int g1/0/1
[FW2-GigabitEthernet1/0/1]ip add 192.168.2.4 24
[FW2-GigabitEthernet1/0/1]service-manage all permit
[FW2-GigabitEthernet1/0/1]int g1/0/2
[FW2-GigabitEthernet1/0/2]ip add 192.168.4.4 24
[FW2-GigabitEthernet1/0/2]service-manage all permit
[FW2-GigabitEthernet1/0/2]int g1/0/3
[FW2-GigabitEthernet1/0/3]ip add 192.168.7.2 24
[FW2-GigabitEthernet1/0/3]service-manage all permit
[FW2-GigabitEthernet1/0/3]int g1/0/6
[FW2-GigabitEthernet1/0/6]ip add 192.168.1.2 24
[FW2-GigabitEthernet1/0/6]service-manage all permit
[FW2-GigabitEthernet1/0/6]qui
[FW2]firewall zone untrust
[FW2-zone-untrust]add int g1/0/0
[FW2-zone-untrust]add int g1/0/3
[FW2-zone-untrust]qui
[FW2]firewall zone trust
[FW2-zone-trust]add int g1/0/1
[FW2-zone-trust]add int g1/0/2
[FW2-zone-trust]qui
[FW2]firewall zone dmz
[FW2-zone-dmz]add int g1/0/6
[FW2-zone-dmz]qui
[FW2]ip route-static 0.0.0.0 0 192.168.6.3
[FW2]ip route-static 0.0.0.0 0 192.168.7.3 preference 70
[FW2]security-policy
[FW2-policy-security]rule name permit_heat
[FW2-policy-security-rule-permit_heat]source-zone local
[FW2-policy-security-rule-permit_heat]destination-zone dmz
[FW2-policy-security-rule-permit_heat]action permit
[FW2-policy-security-rule-permit_heat]q
[FW2-policy-security]rule name permit_trust_untrust
[FW2-policy-security-rule-permit_trust_untrust]source-zone trust
[FW2-policy-security-rule-permit_trust_untrust]destination-zone untrust
[FW2-policy-security-rule-permit_trust_untrust]action permit
[FW2-policy-security-rule-permit_trust_untrust]q
[FW2-policy-security]q
[FW2]int g1/0/1
[FW2-GigabitEthernet1/0/1]vrrp vrid 2 virtual-ip 192.168.2.100 standby
[FW2-GigabitEthernet1/0/1]qui
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]vrrp vrid 6 virtual-ip 192.168.6.100 standby
[FW2-GigabitEthernet1/0/0]qui
[FW2]int g1/0/2
[FW2-GigabitEthernet1/0/2]vrrp vrid 4 virtual-ip 192.168.4.100 standby
[FW2-GigabitEthernet1/0/2]qui
[FW2]int g1/0/3
[FW2-GigabitEthernet1/0/3]vrrp vrid 7 virtual-ip 192.168.7.100 standby
[FW2-GigabitEthernet1/0/3]qui
[FW2]hrp interface g1/0/6 remote 192.168.1.1
[FW2]hrp en
HRP_S[FW2]hrp auto-sync
HRP_S[FW2]dis hrp state
HRP_S[FW2]dis hrp int
------------------------------------
AR1:
un in en
sysname AR1
int g0/0/1
ip add 192.168.6.3 24
int g0/0/0
ip add 192.168.8.1 24
qui
int loo 0
ip add 5.5.5.5 32
qui
qui
save
------------------------------------
AR2:
un in en
sysname AR2
int g0/0/1
ip add 192.168.7.3 24
qui
int loo 0
ip add 9.9.9.9 32
qui
qui
save
------------------------------------
HX_SW1:
int g0/0/1
port link-type access
port default vlan 2
qui
int g0/0/2
port link-type access
port default vlan 4
qui
int vlan 2
ip add 192.168.2.2 24
qui
int vlan 4
ip add 192.168.4.3 24
qui
ip route-static 0.0.0.0 0 192.168.2.10
ip route-static 0.0.0.0 0 192.168.4.100 preference 70
qui
save
------------------------------------
HX_SW2:
int g0/0/1
port link-type access
port default vlan 2
qui
int g0/0/2
port link-type access
port default vlan 4
qui
int vlan 2
ip add 192.168.2.3 24
qui
int vlan 4
ip add 192.168.4.2 24
qui
ip route-static 0.0.0.0 0 192.168.2.10
ip route-static 0.0.0.0 0 192.168.4.100 preference 70
qui
save
10、OSPF To configure
HX_SW1:
[HX_SW1]ospf
[HX_SW1-ospf-1]area 0
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.10.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.20.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.30.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.40.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.200.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.2.0 0.0.0.255
[HX_SW1-ospf-1-area-0.0.0.0]net 192.168.4.0 0.0.0.255
HX_SW2:
[HX_SW2]ospf
[HX_SW2-ospf-1]area 0
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.10.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.20.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.30.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.40.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.200.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.2.0 0.0.0.255
[HX_SW2-ospf-1-area-0.0.0.0]net 192.168.4.0 0.0.0.255
FW1:
HRP_M[FW1]ospf
HRP_M[FW1-ospf-1]area 0
HRP_M[FW1-ospf-1-area-0.0.0.0]net 192.168.2.0 0.0.0.255
HRP_M[FW1-ospf-1-area-0.0.0.0]net 192.168.4.0 0.0.0.255
FW2:
HRP_S[FW2]ospf
HRP_S[FW2-ospf-1]area 0
HRP_S[FW2-ospf-1-area-0.0.0.0]net 192.168.2.0 0.0.0.255
HRP_S[FW2-ospf-1-area-0.0.0.0]net 192.168.4.0 0.0.0.255
// Now? PC Can ping 5.5.5.5 了 , And can ping through
11、RIP To configure
AR3:
<Huawei>sys
[Huawei]un in en
[Huawei]sysname AR3
[AR3]int g0/0/0
[AR3-GigabitEthernet0/0/0]ip add 192.168.8.2 24
[AR3-GigabitEthernet0/0/0]int g0/0/1
[AR3-GigabitEthernet0/0/1]ip add 10.10.10.254 24
[AR3-GigabitEthernet0/0/1]qui
[AR3]rip
[AR3-rip-1]
[V200R003C00]version 2
[AR3-rip-1]net 192.168.8.0
[AR3-rip-1]net 10.0.0.0
[AR3-rip-1]qui
[AR3]
AR1:
[AR1]rip
[AR1-rip-1]version 2
[AR1-rip-1]network 192.168.6.0
[AR1-rip-1]network 192.168.8.0
[AR1-rip-1]qui
[AR1]
12、 A firewall NAT Strategy ( I forgot to configure )
Because the dual machine hot standby function has been enabled, now you only need to configure it on the main firewall ( Synchronize to the standby firewall )
HRP_M<FW1>sys
Enter system view, return user view with Ctrl+Z.
HRP_M[FW1]nat-p
HRP_M[FW1]nat-policy (+B)
HRP_M[FW1-policy-nat]rule name to_isp (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-zone trust (+B)
HRP_M[FW1-policy-nat-rule-to_isp]destination-zone untrust (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.10.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.20.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.30.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.40.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.100.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.101.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]source-address 192.168.102.0 24 (+B)
HRP_M[FW1-policy-nat-rule-to_isp]action source-nat easy-ip (+B)
HRP_M[FW1-policy-nat-rule-to_isp]qui
HRP_M[FW1-policy-nat]qui
HRP_M[FW1]qui
HRP_M<FW1>save
13、telnet Remote management configuration
HX_SW1:
[HX_SW1]aaa
[HX_SW1-aaa]local-user huawei privilege level 3 password cipher 5555
[HX_SW1-aaa]local-user huawei service-type telnet
[HX_SW1-aaa]qui
[HX_SW1]user-interface vty 0 4
[HX_SW1-ui-vty0-4]authentication-mode aaa
[HX_SW1-ui-vty0-4]protocol inbound telnet
[HX_SW1-ui-vty0-4]qui
[HX_SW1]int vlanif 900
[HX_SW1-Vlanif900]ip add 192.168.255.254 24
[HX_SW1-Vlanif900]vrrp vrid 255 virtual-ip 192.168.255.1
[HX_SW1-Vlanif900]dis this
#
interface Vlanif900
ip address 192.168.255.254 255.255.255.0
vrrp vrid 255 virtual-ip 192.168.255.1
#
return
[HX_SW1-Vlanif900]q
------------------------------------
HX_SW2:
[HX_SW2]aaa
[HX_SW2-aaa]local-user huawei privilege level 3 password cipher 5555
[HX_SW2-aaa]local-user huawei service-type telnet
[HX_SW2-aaa]qui
[HX_SW2]user-interface vty 0 4
[HX_SW2-ui-vty0-4]authentication-mode aaa
[HX_SW2-ui-vty0-4]protocol inbound telnet
[HX_SW2-ui-vty0-4]qui
[HX_SW2]int vlanif 900
[HX_SW2-Vlanif900]ip add 192.168.255.253 24
[HX_SW2-Vlanif900]vrrp vrid 255 virtual-ip 192.168.255.1
[HX_SW2-Vlanif900]dis this
#
interface Vlanif900
ip address 192.168.255.253 255.255.255.0
vrrp vrid 255 virtual-ip 192.168.255.1
#
return
[HX_SW2-Vlanif900]q
------------------------------------
HJ_SW3:
[JR_SW3]aaa
[JR_SW3-aaa]local-user huawei privilege level 3 password cipher 5555
[JR_SW3-aaa]local-user huawei service-type telnet
[JR_SW3-aaa]qui
[JR_SW3]user-interface vty 0 4
[JR_SW3-ui-vty0-4]authentication-mode aaa
[JR_SW3-ui-vty0-4]protocol inbound telnet
[JR_SW3-ui-vty0-4]qui
[JR_SW3]int vlanif 900
[JR_SW3-Vlanif900]ip add 192.168.255.3 24
[JR_SW3-Vlanif900]qui
[JR_SW3]ip route-s 0.0.0.0 0 192.168.255.1
------------------------------------
JR_SW11:
<JR_SW11>sys
[JR_SW11]aaa
[JR_SW11-aaa]local-user huawei privilege level 3 password cipher 5555
[JR_SW11-aaa]local-user huawei service-type telnet
[JR_SW11-aaa]qui
[JR_SW11]user-interface vty 0 4
[JR_SW11-ui-vty0-4]authentication-mode aaa
[JR_SW11-ui-vty0-4]protocol inbound telnet
[JR_SW11-ui-vty0-4]qui
[JR_SW11]int vlanif 900
[JR_SW11-Vlanif900]ip add 192.168.255.11 24
[JR_SW11-Vlanif900]qui
[JR_SW11]ip route-s 0.0.0.0 0 192.168.255.1
[JR_SW11]qui
<JR_SW11>save
// The other switches have the same configuration , It's not worthy to omit
// Now you can simulate PC The router g0/0/0 Enable automatic address acquisition on the port , After getting the address, you can go through telnet Remote
/*<PC>telnet 192.168.255.254 Press CTRL_] to quit telnet mode Trying 192.168.255.254 ... Connected to 192.168.255.254 ... Username:huawei Password: Info: The max number of VTY users is 5, and the number of current VTY users on line is 1. The current login time is 2022-06-29 18:56:26. <HX_SW1>*/
14、 Wireless network configuration

HX_SW2:
<HX_SW2>sys
[HX_SW2]vlan batch 100 101 102
[HX_SW2]int g0/0/12
[HX_SW2-GigabitEthernet0/0/12]port link-type trunk
[HX_SW2-GigabitEthernet0/0/12]port trunk allow-pass vlan all
[HX_SW2-GigabitEthernet0/0/12]int g0/0/4
[HX_SW2-GigabitEthernet0/0/4]port trunk allow-pass vlan 100 101 102
[HX_SW2-GigabitEthernet0/0/4]int g0/0/8
[HX_SW2-GigabitEthernet0/0/8]port trunk allow-pass vlan 100 101 102
[HX_SW2-GigabitEthernet0/0/8]qui
[HX_SW2]int vlan 100
[HX_SW2-Vlanif100]ip add 192.168.100.1 24
[HX_SW2-Vlanif100]int vlan 101
[HX_SW2-Vlanif101]ip add 192.168.101.1 24
[HX_SW2-Vlanif101]int vlan 102
[HX_SW2-Vlanif102]ip add 192.168.102.1 24
[HX_SW2-Vlanif102]qui
[HX_SW2]dhcp enable
[HX_SW2]ip pool ap_pool
Info:It's successful to create an IP address pool.
[HX_SW2-ip-pool-ap_pool]gateway-list 192.168.100.1
[HX_SW2-ip-pool-ap_pool]network 192.168.100.0 mask 24
[HX_SW2-ip-pool-ap_pool]excluded-ip-address 192.168.100.100
[HX_SW2-ip-pool-ap_pool]dns-list 192.168.200.2
[HX_SW2-ip-pool-ap_pool]qui
[HX_SW2]ip pool hua_1
Info:It's successful to create an IP address pool.
[HX_SW2-ip-pool-hua_1]gateway-list 192.168.101.1
[HX_SW2-ip-pool-hua_1]network 192.168.101.0 mask 24
[HX_SW2-ip-pool-hua_1]dns-list 192.168.200.2
[HX_SW2-ip-pool-hua_1]qui
[HX_SW2]ip pool hua_2
Info:It's successful to create an IP address pool.
[HX_SW2-ip-pool-hua_2]gateway-list 192.168.102.1
[HX_SW2-ip-pool-hua_2]network 192.168.102.0 mask 24
[HX_SW2-ip-pool-hua_2]dns-list 192.168.200.2
[HX_SW2-ip-pool-hua_2]qui
[HX_SW2]int vlan 100
[HX_SW2-Vlanif100]dhcp select global
[HX_SW2-Vlanif100]int vlan 101
[HX_SW2-Vlanif101]dhcp select global
[HX_SW2-Vlanif101]int vlan 102
[HX_SW2-Vlanif102]dhcp select global
[HX_SW2-Vlanif102]qui
[HX_SW2]qui
<HX_SW2>save
------------------------------------
JR_SW4:
<JR_SW4>sys
[JR_SW4]vlan batch 100 101 102
[JR_SW4]int g0/0/2
[JR_SW4-GigabitEthernet0/0/2]port trunk allow-pass vlan 100 101 102
[JR_SW4-GigabitEthernet0/0/2]int g0/0/4
[JR_SW4-GigabitEthernet0/0/4]port link-type trunk
[JR_SW4-GigabitEthernet0/0/4]port trunk pvid vlan 100
[JR_SW4-GigabitEthernet0/0/4]port trunk allow-pass vlan 100 101
[JR_SW4-GigabitEthernet0/0/4]qui
[JR_SW4]qui
<JR_SW4>save
------------------------------------
JR_SW8:
<JR_SW8>sys
[JR_SW8]vlan batch 100 101 102
[JR_SW8]int g0/0/2
[JR_SW8-GigabitEthernet0/0/2]port trunk allow-pass vlan 100 101 102
[JR_SW8-GigabitEthernet0/0/2]int g0/0/4
[JR_SW8-GigabitEthernet0/0/4]port link-type trunk
[JR_SW8-GigabitEthernet0/0/4]port trunk pvid vlan 100
[JR_SW8-GigabitEthernet0/0/4]port trunk allow-pass vlan 100 102
[JR_SW8-GigabitEthernet0/0/4]qui
[JR_SW8]qui
<JR_SW8>SAVE
------------------------------------
AC:
<AC6605>sys
[AC6605]un in en
[AC6605]sysname AC1
[AC1]vlan batch 100 to 102
[AC1]int g0/0/1
[AC1-GigabitEthernet0/0/1]port link-type trunk
[AC1-GigabitEthernet0/0/1]port trunk allow-pass vlan all
[AC1-GigabitEthernet0/0/1]qui
[AC1]int vlan 100
[AC1-Vlanif100]ip add 192.168.100.100 24
[AC1-Vlanif100]qui
[AC1]capwap source int vlanif100
[AC1]wlan
[AC1-wlan-view]ap-group name CYY
[AC1-wlan-ap-group-CYY]qui
[AC1-wlan-view]regulatory-domain-profile name domain1
[AC1-wlan-regulate-domain-domain1]country-code cn
[AC1-wlan-regulate-domain-domain1]qui
[AC1-wlan-view]ap-group name CYY
[AC1-wlan-ap-group-CYY]regulatory-domain-profile domain1
Warning: Modifying the country code will clear channel, power and antenna gain c
onfigurations of the radio and reset the AP. Continue?[Y/N]:y
[AC1-wlan-ap-group-CYY]qui
[AC1-wlan-view]qui
[AC1]wlan
[AC1-wlan-view]ap-group name YYC
[AC1-wlan-ap-group-YYC]qui
[AC1-wlan-view]regulatory-domain-profile name domain2
[AC1-wlan-regulate-domain-domain2]country-code cn
[AC1-wlan-regulate-domain-domain2]q
[AC1-wlan-view]ap-group name YYC
[AC1-wlan-ap-group-YYC]regulatory-domain-profile domain2
Warning: Modifying the country code will clear channel, power and antenna gain c
onfigurations of the radio and reset the AP. Continue?[Y/N]:y
[AC1-wlan-ap-group-YYC]qui
[AC1-wlan-view]ap auth-mode mac-auth
[AC1-wlan-view]ap-id 0 ap-mac 00e0-fc35-17d0
[AC1-wlan-ap-0]ap-name area_0
[AC1-wlan-ap-0]ap-group CYY
Warning: This operation may cause AP reset. If the country code changes, it will
clear channel, power and antenna gain configurations of the radio, Whether to c
ontinue? [Y/N]:y
[AC1-wlan-ap-0]qui
[AC1-wlan-view]ap auth-mode mac-auth
[AC1-wlan-view]ap-id 1 ap-mac 00e0-fc5f-17a0
[AC1-wlan-ap-1]ap-name area_1
[AC1-wlan-ap-1]ap-group YYC
Warning: This operation may cause AP reset. If the country code changes, it will
clear channel, power and antenna gain configurations of the radio, Whether to c
ontinue? [Y/N]:y
[AC1-wlan-ap-1]qui
[AC1-wlan-view]qui
[AC1]wlan
[AC1-wlan-view]security-profile name A
[AC1-wlan-sec-prof-A]security wpa2 psk pass-phrase a1234567 aes
[AC1-wlan-sec-prof-A]q
[AC1-wlan-view]security-profile name X
[AC1-wlan-sec-prof-X]security wpa2 psk pass-phrase huawei@123 aes
[AC1-wlan-sec-prof-X]qui
[AC1-wlan-view]ssid-profile name B
[AC1-wlan-ssid-prof-B]ssid CYY-CY
[AC1-wlan-ssid-prof-B]q
[AC1-wlan-view]ssid-profile name Y
[AC1-wlan-ssid-prof-Y]ssid YYC-YC
[AC1-wlan-ssid-prof-Y]q
[AC1-wlan-view]vap-profile name C
[AC1-wlan-vap-prof-C]forward-mode tunnel
[AC1-wlan-vap-prof-C]service-vlan vlan-id 101
[AC1-wlan-vap-prof-C]security-profile A
[AC1-wlan-vap-prof-C]ssid-profile B
[AC1-wlan-vap-prof-C]qui
[AC1-wlan-view]vap-profile name Z
[AC1-wlan-vap-prof-Z]forward-mode tunnel
[AC1-wlan-vap-prof-Z]service-vlan vlan-id 102
[AC1-wlan-vap-prof-Z]security-profile X
[AC1-wlan-vap-prof-Z]ssid-profile Y
[AC1-wlan-vap-prof-Z]qui
[AC1-wlan-view]ap-group name CYY
[AC1-wlan-ap-group-CYY]vap-profile C wlan 1 radio 0
[AC1-wlan-ap-group-CYY]vap-profile C wlan 1 radio 1
[AC1-wlan-ap-group-CYY]qui
[AC1-wlan-view]ap-group name YYC
[AC1-wlan-ap-group-YYC]vap-profile Z wlan 1 radio 0
[AC1-wlan-ap-group-YYC]vap-profile Z wlan 1 radio 1
[AC1-wlan-ap-group-YYC]qui
[AC1-wlan-view]qui
[AC1]qui
<AC1>save
边栏推荐
- 一本揭秘字节万台节点ClickHouse背后技术实现的白皮书来了!
- MySQL
- 牛客编程题--必刷101之双指针篇
- fiddler的使用
- Halcon实例转OpenCvSharp(C# OpenCV)实现--瓶口缺陷检测(附源码)
- Infrared camera: juge infrared mag32 product introduction
- 1 -- Xintang nuc980 nuc980 porting uboot, starting from external mx25l
- 【Node学习笔记】chokidar模块实现文件监听
- [leetcode]Search for a Range
- HAVE FUN | “飞船计划”活动最新进展
猜你喜欢
Lidar: introduction and usage of ouster OS
Alibaba cloud middleware open source past

【森城市】GIS数据漫谈(二)
![[unity] upgraded version · Excel data analysis, automatically create corresponding C classes, automatically create scriptableobject generation classes, and automatically serialize asset files](/img/20/f7fc2204ca165dcea4af25cb054e9b.png)
[unity] upgraded version · Excel data analysis, automatically create corresponding C classes, automatically create scriptableobject generation classes, and automatically serialize asset files
unity 自定义webgl打包模板
用全连接+softmax对图片的feature进行分类
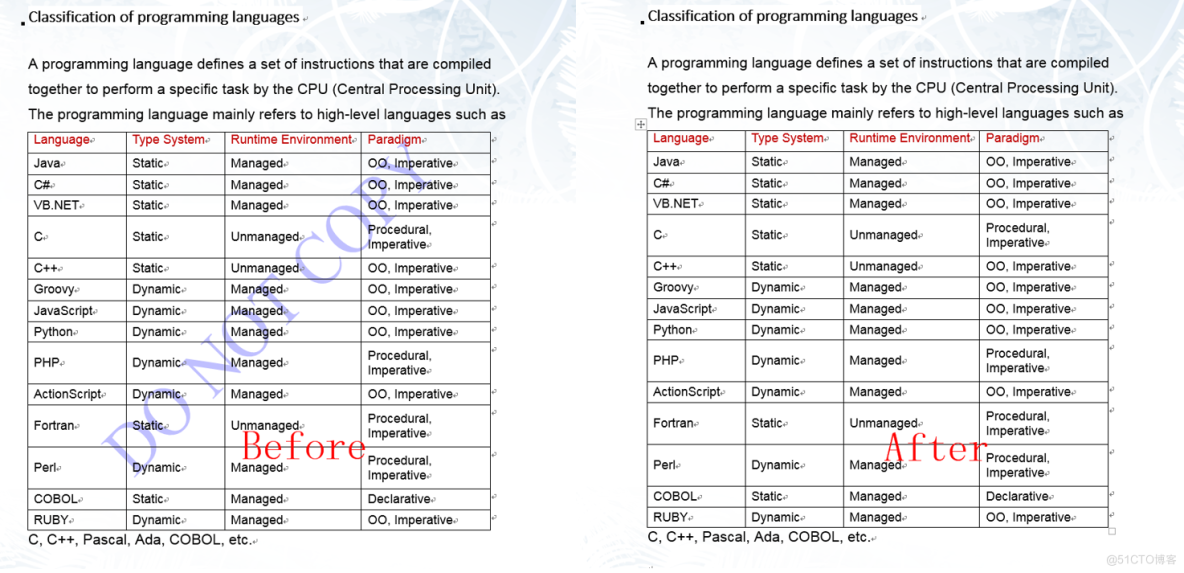
C#/VB. Net to delete watermarks in word documents
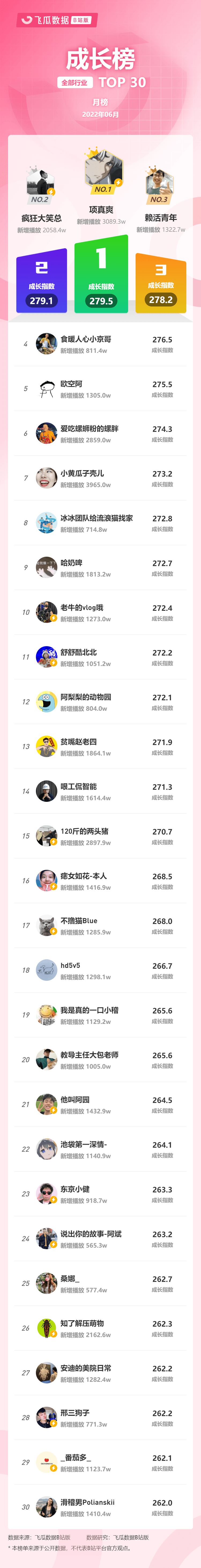
Station B's June ranking list - feigua data up main growth ranking list (BiliBili platform) is released!

你不可不知道的Selenium 8种元素定位方法,简单且实用
进程管理基础
随机推荐
真实项目,用微信小程序开门编码实现(完结)
Summer Challenge database Xueba notes (Part 2)~
The boss is quarantined
Argo workflows source code analysis
#夏日挑战赛#数据库学霸笔记(下)~
Data connection mode in low code platform (Part 1)
Overall query process of PostgreSQL
差异与阵列和阵列结构和链表的区别
Halcon instance to opencvsharp (C openCV) implementation -- bottle mouth defect detection (with source code)
Web3的先锋兵:虚拟人
[unity] upgraded version · Excel data analysis, automatically create corresponding C classes, automatically create scriptableobject generation classes, and automatically serialize asset files
Draco - glTF模型压缩利器
[paper reading | deep reading] graphsage:inductive representation learning on large graphs
CSDN summer camp course project analysis
C#/VB.NET 删除Word文檔中的水印
数论 --- 快速幂、快速幂求逆元
[paper reading | deep reading] rolne: improving the quality of network embedding with structural role proximity
Increase 900w+ playback in 1 month! Summarize 2 new trends of top flow qiafan in station B
阿里云易立:云原生如何破解企业降本提效难题?
HAVE FUN | “飞船计划”活动最新进展