当前位置:网站首页>Method of C language self defining function
Method of C language self defining function
2022-07-02 16:56:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
One 、C Call of custom function of language
1. Declare a custom function :
void fun(void);// Declaration of functions
You can also write custom functions before the main function ;
2. Call the user-defined function in the main function :
int main(void)
{
fun();// call fun function ;
return 0;
}
3. The function of writing custom functions :
void fun(void)
{
int a=12;
printf(“a=%d”,a); Output a
}
The source code is as follows :
#include "stdio.h"
void fun(void);// Declare custom functions
int main(void)// The main function {fun();// call fun function “
return 0;}
void fun(void){int a=12;// Define an integer constant a=12;printf("a=%d",a);// Output a;}
shipment Line program results :
a=12
Two 、 Functions with parameters
1, Declare a custom function :
void fun(uchar a);
2, Call function
int main(void)// The main function { int i; for(i=0;i<8;i++) { fun(i);// call fun function There must be parameters in brackets , Otherwise, an error will be reported printf(“\n”);// Line break }
return 0;}
3. Write custom functions
void fun(char a)// fun The function takes a char Parameters of type { int i=0; char b=’*’; for(i=8;i>0;i–) printf(“%c”,b);// Output a; }
Source program :
#include "stdio.h"
void fun(char a);// Declare custom functions
int main(void)// The main function {int i;for(i=0;i<8;i++){fun(i);// call fun function printf("\n");// Line break }
return 0;}
void fun(char a){int i=0;char b='*';for(i=8;i>0;i--)printf("%c",b);// Output a;}
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/147813.html Link to the original text :https://javaforall.cn
边栏推荐
- 上传代码到远程仓库报错error: remote origin already exists.
- Unity Json 编写
- 618 reprise en profondeur: la méthode gagnante de la famille Haier Zhi
- Global and Chinese markets of stainless steel surgical suture 2022-2028: Research Report on technology, participants, trends, market size and share
- sql解决连续登录问题变形-节假日过滤
- Bib | graph representation based on heterogeneous information network learning to predict drug disease association
- 亚马逊云科技 Community Builder 申请窗口开启
- 2322. 从树中删除边的最小分数(异或和&模拟)
- LeetCode 1. Sum of two numbers
- What is normal distribution? What is the 28 law?
猜你喜欢

PCL point cloud image transformation
![L'explosion de John utilise l'encodage d'entrée par défaut: UTF - 8 Loaded 1 password Hash (bcrypt [blowfish 32 / 64 X3])](/img/4c/ddf7f8085257d0eb8766dbec251345.png)
L'explosion de John utilise l'encodage d'entrée par défaut: UTF - 8 Loaded 1 password Hash (bcrypt [blowfish 32 / 64 X3])

Exploration and practice of integration of streaming and wholesale in jd.com
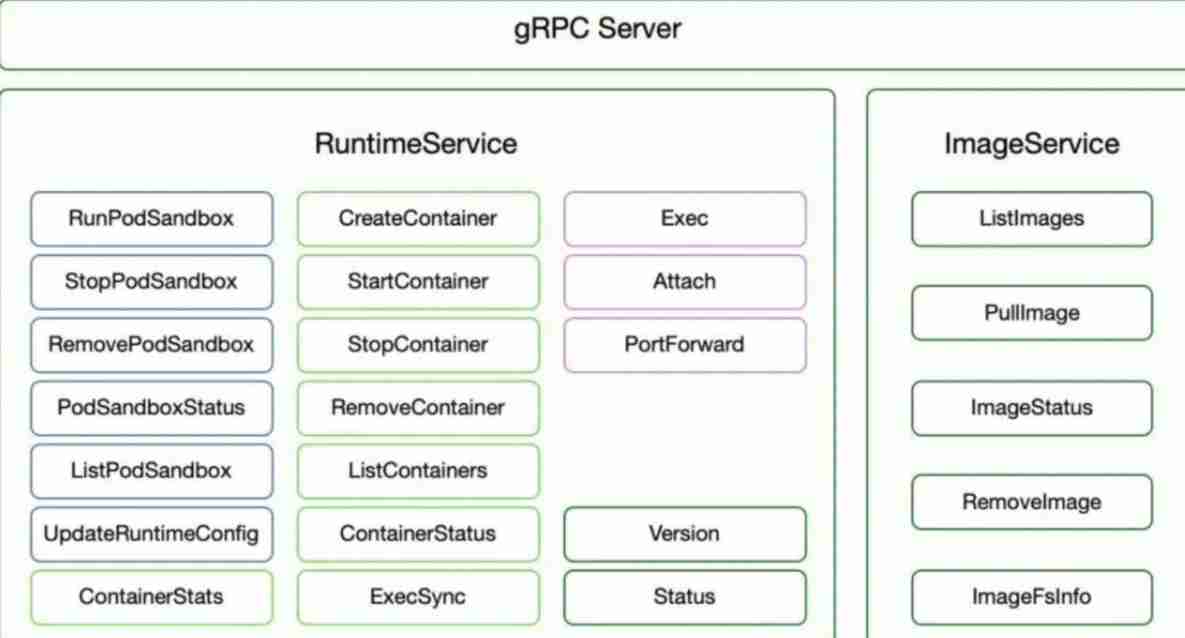
Kubernetes three open interfaces first sight

基于Impala的高性能数仓实践之执行引擎模块
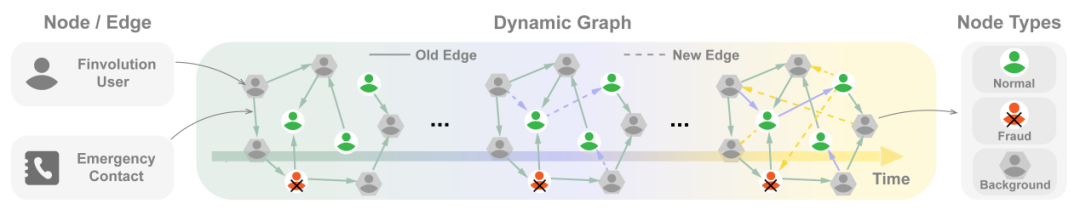
DGraph: 大规模动态图数据集

Cell:清华程功组揭示皮肤菌群的一种气味挥发物促进黄病毒感染宿主吸引蚊虫...

What is normal distribution? What is the 28 law?
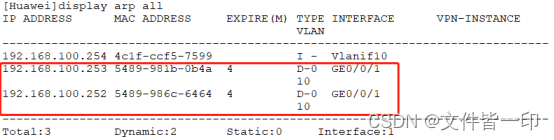
Configure ARP table entry restrictions and port security based on the interface (restrict users' private access to fool switches or illegal host access)

Atcoder beginer contest 169 (B, C, D unique decomposition, e mathematical analysis f (DP))
随机推荐
Download blender on Alibaba cloud image station
vscode设置删除行快捷键[通俗易懂]
ROW_NUMBER()、RANK()、DENSE_RANK区别
[North Asia data recovery] data recovery case of raid crash caused by hard disk disconnection during data synchronization of hot spare disk of RAID5 disk array
john爆破出現Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Yyds dry goods inventory # look up at the sky | talk about the way and principle of capturing packets on the mobile terminal and how to prevent mitm
PhD Debate-11 预告 | 回顾与展望神经网络的后门攻击与防御
MOSFET器件手册关键参数解读
Lampe respiratoire PWM
What is normal distribution? What is the 28 law?
[fluent] dart data type list set type (define set | initialize | generic usage | add elements after initialization | set generation function | set traversal)
In MySQL and Oracle, the boundary and range of between and precautions when querying the date
入行数字IC验证后会做些什么?
C语言中sprintf()函数的用法
Yyds dry inventory uses thread safe two-way linked list to realize simple LRU cache simulation
La boîte de connexion du hub de l'unit é devient trop étroite pour se connecter
js删除字符串中的子串
[error record] error -32000 received from application: there are no running service protocol
LeetCode 6. Z 字形变换 (N字形变换)
机器学习-感知机模型