当前位置:网站首页>Leetcode 701 insertion operation in binary search tree -- recursive method and iterative method
Leetcode 701 insertion operation in binary search tree -- recursive method and iterative method
2022-07-06 05:46:00 【Hello, I'm Boger】
source : Power button (LeetCode)
link :https://leetcode-cn.com/problems/insert-into-a-binary-search-tree
The question :
Given a binary search tree (BST) The root node root And the value to be inserted into the tree value , Insert values into a binary search tree . Return to the root node of the binary search tree after insertion . input data Guarantee , The new value is different from any node value in the original binary search tree .
Be careful , There may be many effective insertion methods , As long as the tree remains a binary search tree after insertion . You can go back to Any valid result .
Example 1: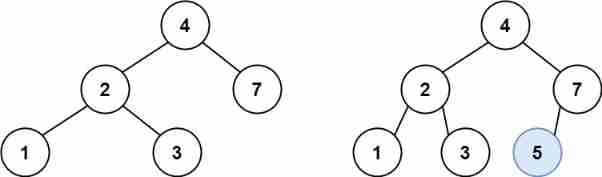
Input :root = [4,2,7,1,3], val = 5
Output :[4,2,7,1,3,5]
explain : Another tree that meets the requirements of the topic is :
Example 2:
Input :root = [40,20,60,10,30,50,70], val = 25
Output :[40,20,60,10,30,50,70,null,null,25]
Example 3:
Input :root = [4,2,7,1,3,null,null,null,null,null,null], val = 5
Output :[4,2,7,1,3,5]
Tips :
The number of nodes in the tree will be [0, 104] Within the scope of .
-108 <= Node.val <= 108
All worth Node.val yes unique Of .
-108 <= val <= 108
Guarantee val In primitive BST Does not exist in the .
Ideas :
In fact, I don't quite understand why this problem is classified as medium difficulty , Quite a simple question .
As long as you understand the concept of binary search tree , Search from the root node of the binary search tree , Until the location found is an empty node , Let's replace this empty node with a node with the value to be inserted .
We use recursive method and iterative method to solve this problem .
Recursive method Java Code :
class Solution {
public TreeNode insertIntoBST(TreeNode root, int val) {
if (root == null) {
TreeNode node = new TreeNode(val);
return node;
}
if (root.val > val) root.left = insertIntoBST(root.left, val);
if (root.val < val) root.right = insertIntoBST(root.right, val);
return root;
}
}
Iterative method Java Code :
class Solution {
public TreeNode insertIntoBST(TreeNode root, int val) {
if (root == null) return new TreeNode(val);
TreeNode parent = root;
TreeNode cur = root;
while (cur != null) {
parent = cur;
if (cur.val > val) cur = cur.left;
else if (cur.val < val) cur = cur.right;
}
if (parent.val > val) parent.left = new TreeNode(val);
else if (parent.val < val) parent.right = new TreeNode(val);
return root;
}
}
边栏推荐
- 【经验】win11上安装visio
- 04. Project blog log
- Application Security Series 37: log injection
- 入侵检测领域数据集总结
- 应用安全系列之三十七:日志注入
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- ARTS Week 25
- Pytorch代码注意的细节,容易敲错的地方
- Garbage collector with serial, throughput priority and response time priority
- [force buckle]43 String multiplication
猜你喜欢

CoDeSys note 2: set coil and reset coil
05. Security of blog project
PDK process library installation -csmc

C Advanced - data storage (Part 1)
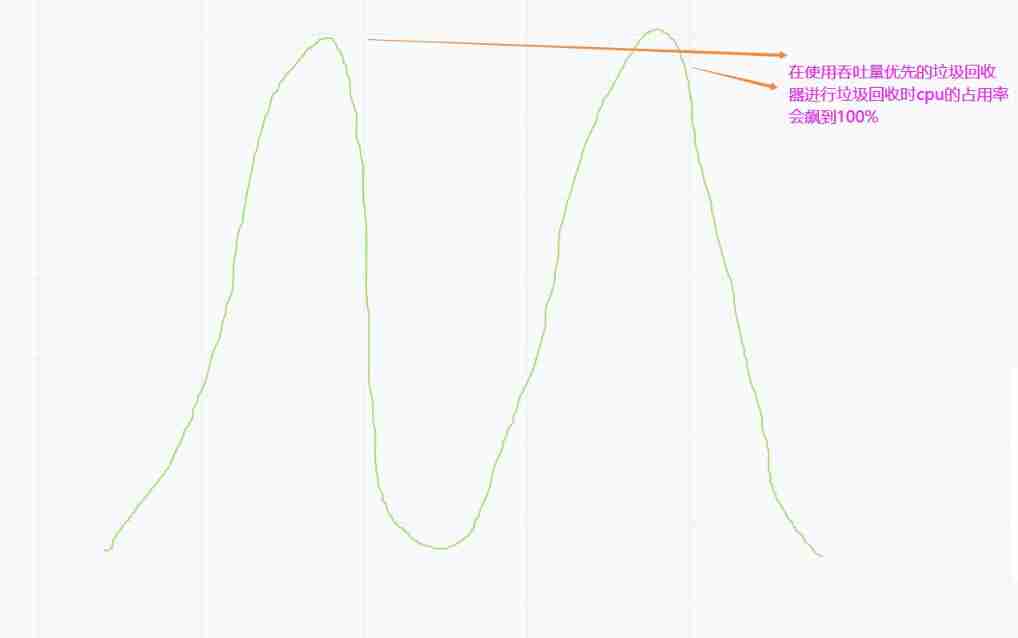
Garbage collector with serial, throughput priority and response time priority
High quality coding tool clion

Remember an error in MySQL: the user specified as a definer ('mysql.infoschema '@' localhost ') does not exist
Rustdesk builds its own remote desktop relay server

29io stream, byte output stream continue write line feed

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
随机推荐
算法-- 爬楼梯(Kotlin)
数字经济破浪而来 ,LTD是权益独立的Web3.0网站?
A master in the field of software architecture -- Reading Notes of the beauty of Architecture
Web Security (V) what is a session? Why do I need a session?
Game push: image / table /cv/nlp, multi-threaded start!
Station B, Master Liu Er - back propagation
Anti shake and throttling are easy to understand
After the project is released, index Html is cached
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Pytorch代码注意的细节,容易敲错的地方
无代码六月大事件|2022无代码探索者大会即将召开;AI增强型无代码工具推出...
CoDeSys note 2: set coil and reset coil
Detailed summary of SQL injection
P2802 回家
Jushan database appears again in the gold fair to jointly build a new era of digital economy
Station B Liu Erden softmx classifier and MNIST implementation -structure 9
Closure, decorator
Embedded interview questions (I: process and thread)
备忘一下jvxetable的各种数据集获取方法
清除浮动的方式