当前位置:网站首页>[web Audit - source code disclosure] obtain source code methods and use tools
[web Audit - source code disclosure] obtain source code methods and use tools
2022-07-05 03:36:00 【Black zone (rise)】
Catalog
1.3、 The whole station source code backup file
Two 、Git Let the cat out of the
2.4、 adopt .git Let the cat out of the
3、 ... and 、svn Let the cat out of the
Four 、hg、CVS、Bazaar/bzr Source leak
5、 ... and 、WEB-INF/web.xml Let the cat out of the
5.3、WEB-INF It mainly includes files or directories :
6、 ... and 、DS_Store Document leakage
7、 ... and 、 Exploit vulnerabilities to reveal
One 、 Backup file disclosure
1.1、 brief introduction :
Backup files are usually due to the negligence of maintenance personnel , Forget to delete the files left in the server .
Attackers enumerate common backup file names , To get the corresponding path , And get the key code , So as to audit the source code
In order to find these backup files , Generally, some sensitive file scanning tools will be used to detect .
Common backup files are : Text backup file 、 The whole station source code backup file
file extension :.rar .zip .7z .tar.gz .bak .swp .txt .sql etc.
1.2、 Text backup file
stay Linux The system will use such as vim or gedit Wait for the text editor , When the editor crashes or exits due to exceptions, it will automatically back up the current file ; Or back up the code after realizing a certain function and then carry out subsequent development .
Possible backup files (index.php For example ):
.index.php.swp
.index.php.swo
index.php~
index.php.bak
index.php.txt
index.php.old
...
1.3、 The whole station source code backup file
Will package the source code of the whole station , Then put it in the root directory of the website , At this time , As long as you find this package, you can start the source code audit .
Common full site backup file names :
www
wwwdata
wwwroot
web
webroot
backup
dist
...Various compressed file suffixes :
.zip
.tar
.tar.gz
.7z
.rar
...You can also use other sensitive files that may disclose the directory structure or file name to obtain the location of backup files , Such as “.xx_xxx”
Two 、Git Let the cat out of the
2.1、 Tools (GitHack):
GitHack It's a .git Leak using scripts , By leaking .git Files in the folder , Rebuild restore project source code .
Penetration tester 、 The attacker , You can further audit the code , mining : Upload files ,SQL Injection, etc web Security vulnerabilities .
GitHub - lijiejie/GitHack: A `.git` folder disclosure exploit
https://github.com/lijiejie/GitHack
Use :
python GitHack.py http://www.openssl.org/.git/
2.2、 produce :
web In the process of upgrading and maintenance , The site file will be modified , You need to back up the whole site or part of it
When you release code , If not deleted .git Catalog , Just publish it directly to the server , The attacker uses it to recover the source code
The backup files are placed in web Under the directory accessible by the server
2.3、 Search through features
When there is an obvious characteristic string in a website
It is possible to pass GitHub To search for the item
2.4、 adopt .git Let the cat out of the
Every git There is one under the root directory of the project .git Folder , The function is to store the relevant information of the project
Tools :GitHack And the source code
Analysis of the source code :
First, set up a local git Project and initialize , And then again commit once
Get into .git Under the table of contents , Look at the files in the directory
determine commit object , View objects
Input exists “.git” In the directory url
Then check HEAD File to get the location of the branch , Then we get the branched hash value
obtain hash Value and initialize a git, Then passed parseCommit Get all objects
Finally using reset Reset branch , Successfully re established the project locally
file :
Key documents ( Part of the ):
HEAD: Mark current git In which branch .
refs: Mark what each branch of the project points to commit.
objects:git All objects stored in the local warehouse .
git The object of :
commit: Mark a submission record of a project .
tree: Mark the directory or subdirectory of a project .
blob: Mark a project file .
tag: Name a submission .
Custom function
(1)parseCommit function :
effect : download commit object , Put it parent Download with
Code :
function parseCommit {
echo parseCommit $1
downloadBlob $1
tree=$(git cat-file -p $1| sed -n '1p' | awk '{print $2}')
parseTree $tree
parent=$(git cat-file -p $1 | sed -n '2p' | awk '{print $2}')
[ ${#parent} -eq 40 ] && parseCommit $parent
}(2)parseTree function :
effect : download tree object , And list tree All the objects under , Classified as tree perhaps blob post-processing
Code :
function parseTree {
echo parseTree $1
downloadBlob $1
while read line
do
type=$(echo $line | awk '{print $2}')
hash=$(echo $line | awk '{print $3}')
[ "$type" = "tree" ] && parseTree $hash || downloadBlob $hash
done < <(git cat-file -p $1)
}(3)downloadBlob function :
effect : Download and hash Corresponding file
function downloadBlob {
echo downloadBlob $1
mkdir -p ${1:0:2}
cd $_
wget -q -nc $domain/.git/objects/${1:0:2}/${1:2}
cd ..
}
3、 ... and 、svn Let the cat out of the
3.1、 brief introduction :
Subversion(SVN) It's an open source version control system , in other words Subversion Managing data that changes over time . The data is placed in a central repository (repository) in . This archive is very similar to a normal file server , But it remembers every file change . So you can restore the file to the old version , Or browse the history of file changes .
In the use of SVN In the process of managing local code , Will automatically generate a file named .svn Hidden folders for , It contains important source code information .
3.2、 The reasons causing :
When the webmaster releases the code , Not used ‘ export ’ function , Instead, copy the code folder directly to WEB Server , This makes .svn Hidden folders are exposed to the Internet , You can use .svn/entries file , Get the server source code .
3.3、 Tools :
Seay-Svn( Simple )
dvcs-ripper
Download address :
Rip Web Accessible ( Distributed ) Version control system :SVN,GIT,Mercurial/hg,bzr,...
Even if directory browsing is turned off , It can also rip repositories .
Make sure you put yourself in the position you want to download / In the empty directory of the clone repository .
Four 、hg、CVS、Bazaar/bzr Source leak
4.1、 Tools :
dvcs-ripper
Download address :
Rip Web Accessible ( Distributed ) Version control system :SVN,GIT,Mercurial/hg,bzr,...
Even if directory browsing is turned off , It can also rip repositories .
Make sure you put yourself in the position you want to download / In the empty directory of the clone repository .
5、 ... and 、WEB-INF/web.xml Let the cat out of the
5.1、 brief introduction :
WEB-INF yes Java Of WEB Security directory of application , Client cannot access , Only the server can access , If you want to access the files directly in the page , Must pass web.xml The file can only be accessed by mapping the file to be accessed .
5.2、 The reasons causing :
When using network architecture , The mapping of directories or files of static resources is improperly configured , Thus causing safety problems , Lead to web.xml Wait until the file can be read
5.3、WEB-INF It mainly includes files or directories :
(1)/WEB-INF/web.xml :
Web Application configuration files ( describe servlet And other application component configuration and naming rules )
(2)/WEB-INF/database.properties:
Database configuration file
(3)/WEB-INF/classes/:
Deposit Java Class file (.class), All inclusive Servlet Class and other class files , The directory structure of class files matches their package name
(4)/WEB-INF/lib/ :
It's used to store packed warehouses (.jar), namely web Applications require a variety of JAR file
(5)/WEB-INF/src/ :
Source directory , Store source code (.asp and .php etc. )
5.4、 utilize :
By finding web.xml file , infer class Path to file , find class file , By decompiling class file , Get the source code of the website .
6、 ... and 、DS_Store Document leakage
6.1、 brief introduction :
.DS_Store yes Mac Next Finder Used to save how to display files / Folder Data files for ( That is, the display properties of the folder , Placement of the icon of the Hebi file ), Each folder corresponds to a
When uploading the code , Safe and correct operation should put .DS_Store File deletion , If not deleted ,.DS_Store Will upload and deploy to the server , May cause file leakage ( Directory structure 、 Backup file 、 Source code file )
6.2、 Tools :
ds_store_exp
It's a .DS_Store File leaks take advantage of scripts , It parses .DS_Store File and recursively download the file locally .
Download address :
7、 ... and 、 Exploit vulnerabilities to reveal
In combination with any File Inclusion Vulnerability or any file download vulnerability
It is possible to download to the source code , And audit it
边栏推荐
- Use UDP to send a JPEG image, and UPD will convert it into the mat format of OpenCV after receiving it
- Share the newly released web application development framework based on blazor Technology
- SQL performance optimization skills
- Why do some programmers change careers before they are 30?
- The perfect car for successful people: BMW X7! Superior performance, excellent comfort and safety
- Azkaban安装部署
- Talk about the SQL server version of DTM sub transaction barrier function
- Pat class a 1160 forever (class B 1104 forever)
- [安洵杯 2019]不是文件上传
- Kbp206-asemi rectifier bridge kbp206
猜你喜欢
2. Common request methods

端口,域名,协议。
Pat grade a 1119 pre- and post order traversals (30 points)
Mongodb common commands
Qrcode: generate QR code from text
Why do some programmers change careers before they are 30?
![[groovy] groovy environment setup (download groovy | install groovy | configure groovy environment variables)](/img/99/bb05b6c48a9e70ca7ff77733d954b9.jpg)
[groovy] groovy environment setup (download groovy | install groovy | configure groovy environment variables)
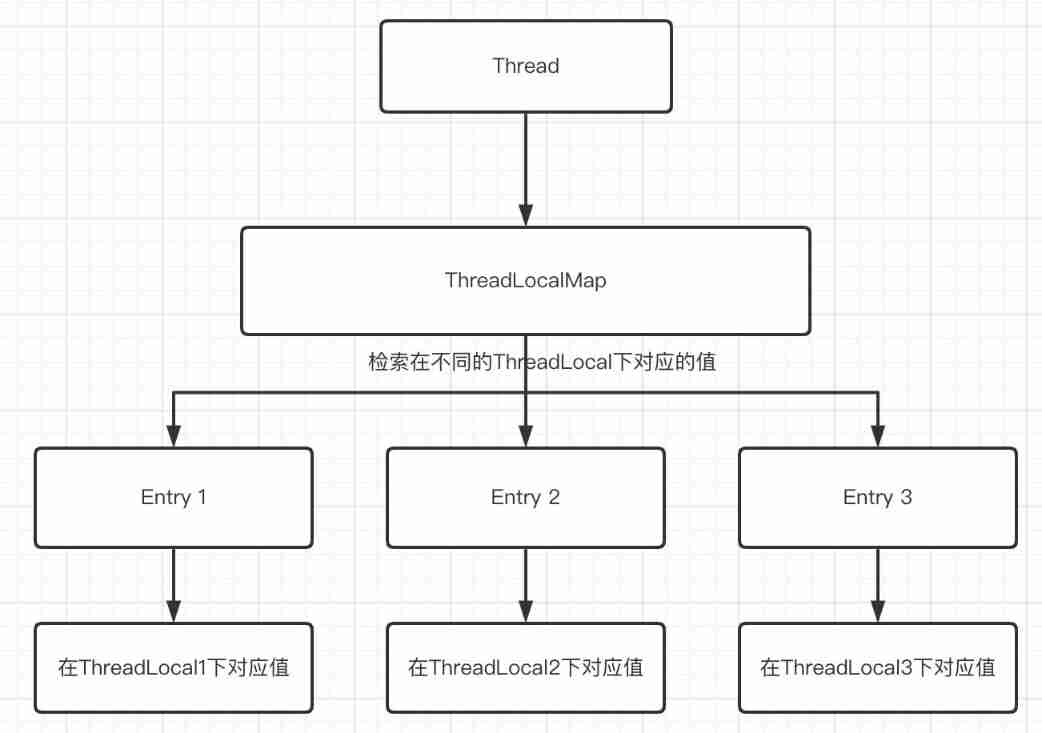
Hot knowledge of multithreading (I): introduction to ThreadLocal and underlying principles
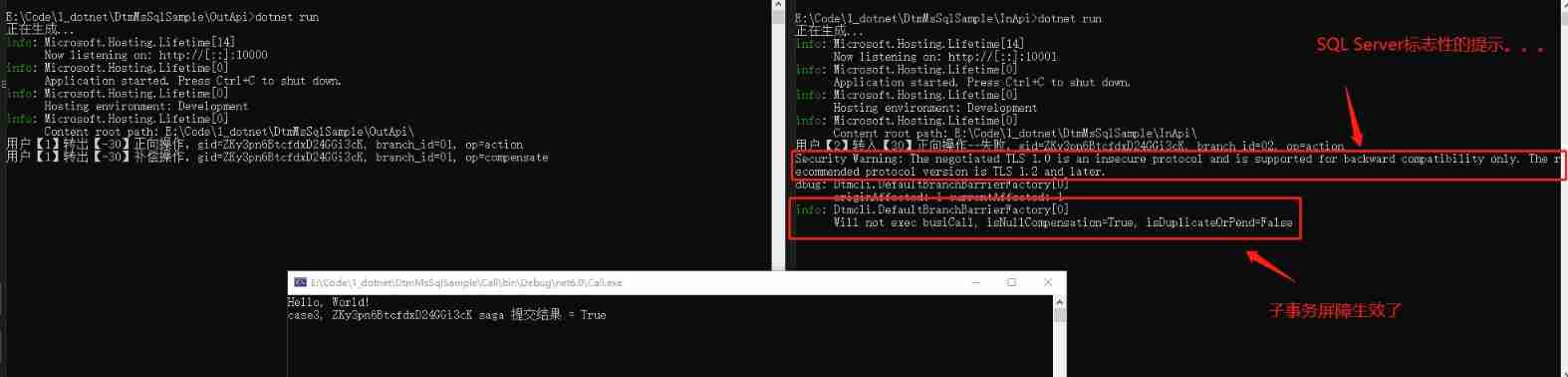
Talk about the SQL server version of DTM sub transaction barrier function
Kbp206-asemi rectifier bridge kbp206
随机推荐
Why do some programmers change careers before they are 30?
Flume configuration 4 - customize mysqlsource
Solve the problem that sqlyog does not have a schema Designer
Multi person online anonymous chat room / private chat room source code / support the creation of multiple chat rooms at the same time
【web源码-代码审计方法】审计技巧及审计工具
Kuboard
Pytest (4) - test case execution sequence
Anti debugging (basic principles of debugger Design & NT NP and other anti debugging principles)
SQL performance optimization skills
Necessary fonts for designers
SQL injection exercise -- sqli Labs
SQL performance optimization skills
Blue Bridge Cup single chip microcomputer -- PWM pulse width modulation
Anchor free series network yolox source code line by line explanation Part 2 (a total of 10, ensure to explain line by line, after reading, you can change the network at will, not just as a participan
Logstash、Fluentd、Fluent Bit、Vector? How to choose the appropriate open source log collector
IPv6 experiment
Kubernetes - identity and authority authentication
Basic knowledge of tuples
qrcode:将文本生成二维码
线程基础知识