当前位置:网站首页>(1) The standard of performance tuning and the correct posture for tuning - if you have performance problems, go to the heapdump performance community!
(1) The standard of performance tuning and the correct posture for tuning - if you have performance problems, go to the heapdump performance community!
2022-07-04 14:30:00 【Cute Xiaoxin @ Yuanjie】
List of articles
- @[toc]
- 1. When do I start to get involved in tuning
- 2. Basic steps and Strategies of performance tuning
- 3. The common performance pit of strings
- 3.4 String.intern Case study : Memory effect after optimization
- 5. java serialize : Native serialization
- 6 NIO principle
- 7.HashMap Blood cases and ConcurrentHashMap The correct use of
List of articles
- @[toc]
- 1. When do I start to get involved in tuning
- 2. Basic steps and Strategies of performance tuning
- 3. The common performance pit of strings
- 3.4 String.intern Case study : Memory effect after optimization
- 5. java serialize : Native serialization
- 6 NIO principle
- 7.HashMap Blood cases and ConcurrentHashMap The correct use of
Performance issues , On HeapDump Performance community !
1. When do I start to get involved in tuning
· The initial stage of project development , Too concerned about performance optimization , Instead, it will make us tired of wasting energy , Not only can it not bring great improvement to the system performance , It will also affect the development progress , Even get the opposite effect , Bring new problems to the system
We only need to consider the basic scenario programming performance problems at the code level ︰ Reduce disk I/О operation 、 Reduce the use of contention locks and handle external service calls carefully
· After development , Generally, the system will be tested . Product managers usually provide online expected data , We conduct pressure test on the reference platform provided , Through performance analysis 、 Statistical tools to count performance indicators , See if it's within expectations .
· After the project goes online , We need to consider the actual situation online , According to the monitoring indicators and statistical logs , To observe system performance problems , Find the problem , Fix the problem . Performance concerns core dimensions
CPU、 Memory 、 disk I/O、 The Internet 、 response time 、 throughput TPS、QPS
2. Basic steps and Strategies of performance tuning
Give priority to ensuring that the program is available , Then repair, troubleshooting and tuning
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-a6a3DuKQ-1656732438622)(E:\markdown note \java\ performance tuning .assets\image-20220702101602677.png)]](/img/23/ee21c0d98863dd46df7bfd489156b1.png)
3. The common performance pit of strings
String、StringBuffer、StringBuilder、intern
Java9 In the program , Most strings only contain characters such as alphanumeric characters , Use Latin-1 code , One character takes up one Byte. Use Char, One Char It takes two hours Byte, It takes up twice as much memory
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-TkrFtlZP-1656732438623)(E:\markdown note \java\ performance tuning .assets\image-20220702102307075.png)]](/img/eb/a188daac35654fa772451b41fc568e.png)
6 -> 7/8 Improper operation by developers may lead to error in offset statistics , Cause stack overflow . So cancel offset,count Variable
7/8 -> 9 Characters are generally alphabetic , Performance considerations use byte[]
3.1 Source code analysis StringBuffer、StringBuilder performance
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-386Irizg-1656732438623)(E:\markdown note \java\ performance tuning .assets\image-20220702102528558.png)]](/img/90/1b8fc7bb7d68c8e374db599c7f6b05.png)
StringBuffer Thread safety , But a lot of Synchronized lock .
StringBuilder It is suitable for the scenario of non competitive character resources in the concurrent environment : For example, common tool class methods .
3.2 String、StringBuffer、StringBuilder Performance pressure test
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-wh5yeE3s-1656732438623)(E:\markdown note \java\ performance tuning .assets\image-20220702102817457.png)]](/img/95/49735224441c3e322e89a4ec9c2247.png)
3.3 String.intern The magic of
Twitter Every time the status of a message is released , Will generate an address message . at that time Twitter Size of users , Server needs 32G To store address information . Later call String.intern, Memory becomes hundreds of megabytes
intern Method : Query whether the current string exists from the string constant pool , If it does not exist, put the current string into the constant pool
intern Method : Query whether the current string exists from the string constant pool , If it does not exist, put the current string into the constant pool
intern Method : Query whether the current string exists from the string constant pool , If it does not exist, put the current string into the constant pool
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-HSJ7UMBt-1656732438624)(E:\markdown note \java\ performance tuning .assets\image-20220702103200952.png)]](/img/4a/bb53468ec1b7d8c45662b8950d0850.png)
jdk6: The constant pool of strings is on the heap Perm District
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Lqi7kVg8-1656732438624)(E:\markdown note \java\ performance tuning .assets\image-20220702103411818.png)]](/img/a3/3a45c1705b7053c0e678a0d4330307.png)
JDK7、JDK8: String constant pool already from Perm Move the area to normal Java Heap Regional .Perm The area is too small is a major reason . Often encountered OOM situation .JDK8 It has been cancelled directly Perm Area , Create a new meta region MetaSpace
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-R2Z8EEKX-1656732438624)(E:\markdown note \java\ performance tuning .assets\image-20220702103733003.png)]](/img/5d/0cf14ae6f5cc66b9e306fcdf3d5785.png)
3.4 String.intern Case study : Memory effect after optimization
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-Bs4TVt6E-1656732438624)(E:\markdown note \java\ performance tuning .assets\image-20220702104333113.png)]](/img/45/0e3c9fa53f33cd44767a6db2a4f02b.png)
4 Regular expression pit
use NFA Automata implement more complex regular expressions , In the process of matching, it often causes backtracking problem . A lot of backtracking takes up for a long time CPU, This leads to system performance overhead
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-A2FSXqi7-1656732438625)(E:\markdown note \java\ performance tuning .assets\image-20220702104359487.png)]](/img/40/ad189df58ea74e28a7d8ad2417aa4a.png)
Greedy mode (Greedy)
seeing the name of a thing one thinks of its function , It's in quantity matching , If used alone +、?、* or [min.max] Equivalent words , Regular expressions match as much as possible . For example, the previous example : text= “abbc”regex= “ab[ 1 ,3]c” In greedy mode ,NFA The automaton reads the maximum matching range , Match 3 individual b character . The match failed once , It caused a retrospective . If the match turns out to be “abbbc”, It will match
Exclusive mode (Possessive)
Exclusive mode will match more content as much as possible ; The difference is , In exclusive mode , Failure to match will end the match , There will be no backtracking problem . Previous examples , Add a... After the character “+”, Open exclusive mode .
text=“abbc”regex= “"ab[1,3]+bc The result is a mismatch . End match , There will be no backtracking problem
Previous cases are suitable for exclusive mode . Summarize regular expression skills
Use less greedy mode , Multi use exclusive mode and greedy mode will cause backtracking problems , We can use exclusive mode to avoid backtracking 2. Reduce branch selection types “(X|Y|Z)” Regular expressions that are used in this way can degrade performance , When we develop, we should try to reduce the use. If we must use , There are several ways to optimize :
First , Put the more common options in the front , So that they can be matched quickly ;
secondly , We can try to extract common patterns , for example , take “(abcd|abef)” Replace with “ab(cd|ef)"
5. java serialize : Native serialization
Java Provides a serialization mechanism , This mechanism can serialize an object into binary form ( Byte array )
Used to write to disk or output to the network , It can also read byte arrays from the network or disk , Anti serialization into objects , Use... In the program
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-hVwupQOh-1656732438625)(E:\markdown note \java\ performance tuning .assets\image-20220702105347143.png)]](/img/87/af1c77580f3f27f3410af9a40e08dc.png)
6 NIO principle
An asynchronous non blocking I/O Model , It's also I/O The foundation of multiplexing , It has been applied to large application servers more and more , To solve the problem of high concurrency and a large number of connections 、I/O The effective way to deal with problems comes from Linux epoll Communication model
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-mqrQYqVF-1656732438625)(E:\markdown note \java\ performance tuning .assets\image-20220702105932756.png)]](/img/06/de5604c64242c8908ed0df8bcf069c.png)
6.1 NIO Concurrent IO scene
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-LZyzHWW4-1656732438625)(E:\markdown note \java\ performance tuning .assets\image-20220702110321861.png)]](/img/eb/0ce92de2a4acc8e4d7068e5879602a.png)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ABwBhEwW-1656732438626)(E:\markdown note \java\ performance tuning .assets\image-20220702110703124.png)]](/img/d7/2cf6e5a7ad5a862bf60c31107c69ff.png)
6.2 NIO Under what circumstances can not use ?
Data communication is very frequent Don't suggest , There will be more context switches .
Suitable for use NIO Of : Long connection time , High concurrency , Communication is not very frequent
7.HashMap Blood cases and ConcurrentHashMap The correct use of
HashMap The cause of the dead cycle is one : Map It's expanding 、 Multithreading Put operation
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-6ZmnaAiX-1656732438626)(E:\markdown note \java\ performance tuning .assets\image-20220702111453138.png)]](/img/73/be81bb49a058e36e23717a49ceb67a.png)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-bXcX0H13-1656732438626)(E:\markdown note \java\ performance tuning .assets\image-20220702111510902.png)]](/img/66/4ee4b099d744af01ca059f1407e88c.png)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-QPbHHGds-1656732438626)(E:\markdown note \java\ performance tuning .assets\image-20220702111715993.png)]](/img/5d/900138f892d337b070b91a23e20aef.png)
Thread safety scheme :ConcurrentHashMap
· avoid HashMap The problem of concurrent reading and writing dirty data
·JDK 1.7 ConcurrentHashmap Sectional lock , performance Synchronized Too much
·JDK1.8 Use Synchronized and CAS、Volatile、 The combination of red and black trees , Replace distributed locks
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-y0leDAPn-1656732438627)(E:\markdown note \java\ performance tuning .assets\image-20220702111938984.png)]](/img/42/1a53cedec9ed6051a7b788be9d2dbe.png)
![[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-N7XsrdNz-1656732438627)(E:\markdown note \java\ performance tuning .assets\image-20220702112206464.png)]](/img/04/a162e950f1db933ebe316c40cae162.png)
边栏推荐
- SqlServer函数,存储过程的创建和使用
- R language uses bwplot function in lattice package to visualize box plot and par Settings parameter custom theme mode
- AI与生命科学
- 10.(地图数据篇)离线地形数据处理(供Cesium使用)
- ViewModel 初体验
- 数据埋点的一些问题和想法
- R language uses follow up of epidisplay package The plot function visualizes the longitudinal follow-up map of multiple ID (case) monitoring indicators, and uses stress The col parameter specifies the
- Industrial Internet has greater development potential and more industry scenarios
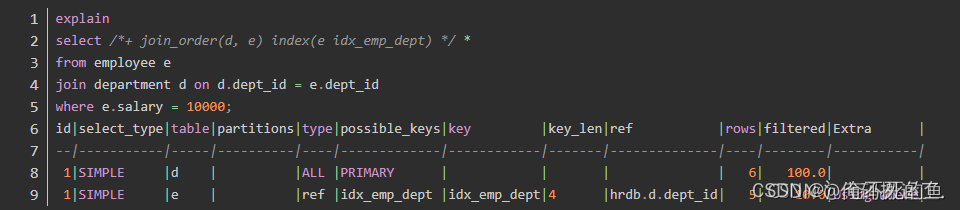
- sql优化之explain
- STM32F1与STM32CubeIDE编程实例-MAX7219驱动8位7段数码管(基于GPIO)
猜你喜欢
Innovation and development of independent industrial software
数据中台概念

Nowcoder rearrange linked list
数据湖(十三):Spark与Iceberg整合DDL操作
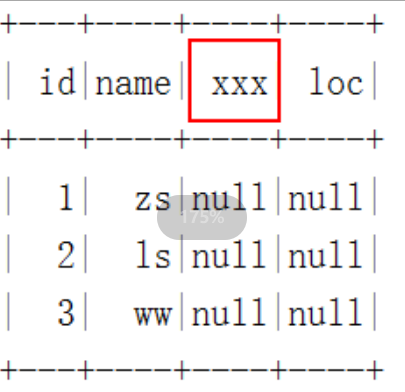
Query optimizer for SQL optimization
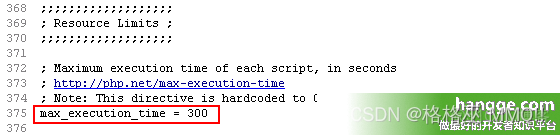
Count the running time of PHP program and set the maximum running time of PHP

Xcode 异常图片导致ipa包增大问题
电商系统中红包活动设计

Data Lake (13): spark and iceberg integrate DDL operations

软件测试之测试评估
随机推荐
Opencv3.2 and opencv2.4 installation
数据中台概念
LifeCycle
数据湖(十三):Spark与Iceberg整合DDL操作
Digi restarts XBee Pro S2C production. Some differences need to be noted
An overview of 2D human posture estimation
一种架构来完成所有任务—Transformer架构正在以一己之力统一AI江湖
【信息检索】分类和聚类的实验
LiveData
R language uses bwplot function in lattice package to visualize box plot and par Settings parameter custom theme mode
Detailed index of MySQL
leetcode:6109. Number of people who know the secret [definition of DP]
电商系统中红包活动设计
MySQL之详解索引
Vscode common plug-ins summary
Test process arrangement (2)
MySQL stored procedure exercise
Ml: introduction, principle, use method and detailed introduction of classic cases of snap value
Chapter 16 string localization and message Dictionary (2)
gin集成支付宝支付