当前位置:网站首页>Ten capabilities that cyber threat analysts should have
Ten capabilities that cyber threat analysts should have
2022-07-05 17:44:00 【Software testing network】

Cyber threats are not static , New threats and attacks are emerging in endlessly , The damage is also getting bigger and bigger , Specifically, it includes social engineering attacks 、 Malware 、 Distributed denial of service (DDoS) attack 、 High level persistent threat (APT)、 Trojan horse 、 Content erasure attack and data destruction . According to Cisco prediction ,2022 year DDoS Or the total number of social engineering attacks will reach 1450 Ten thousand times .
But in the face of the above industry situation , After all, the functional scope of network defense products and technologies is limited , The development of network security cannot leave people , Only those who have both emotional intelligence and skills can understand the internal operation and motivation of the attacker . Network threat analyst is such a professional security talent , Be able to analyze and solve all kinds of network threats for enterprise organizations , They revealed the causes of cyber attacks through research , It can help enterprise organizations prevent and respond to attacks more effectively . This article discusses the job responsibilities of cyber threat analysts 、 Salary level and some work skills required to become a good cyber threat analyst .
The responsibility and value of cyber threat analysts
Cyber threat analysts need to protect organizations from digital threats , And actively formulate plans to respond to and contain cyber attacks . Cyber threat analysts are responsible for protecting the infrastructure of enterprise organizations ( Such as network ) And related software and hardware systems ( Such as server or workstation ), And try to keep the enterprise organization away from attackers who attempt to cause damage or steal sensitive information .
Cyber threat analysts focus on networks and IT Infrastructure security , They need a comprehensive understanding of cyber attacks 、 The nature of malware and cyber criminals , And spare no effort to prevent and stop these attacks . Besides , Cyber threat analysts are also known as threat intelligence analysts , They need to be able to analyze digital threats , Be able to clearly report any capture indicators it finds (IoC), And according to the analysis results , Take action to protect assets vulnerable to cyber attacks , The completion of these tasks requires the ability to pay high attention to details 、 Research and technical skills and creativity .
Cyber threat analysts play a vital role in protecting sensitive information of enterprises . They need to work across departments and processes , Find and repair defects in the organization's safety system and plan in a timely manner , And take effective strategies against these defects , This will help enterprises develop a network defense system 、 Preventing potential attacks is critical .
Besides , Cyber threat analysts are also responsible for protecting the hardware of enterprise organizations 、 Software and networks are protected from theft 、 Missing or unauthorized access . In small businesses , The responsibilities of cyber threat analysts may be broader , But for big companies , Cyber threat analysts are just part of the enterprise security team . The following is a more specific analysis of the responsibilities of cyber threat analysts :
1. Prevent data leakage
Data leakage events can be fatal to enterprise organizations , Data leakage may reduce the trust of the public and consumers in enterprise organizations , Lead to credit card fraud 、 Identity theft or other serious economic losses occur . Identity Theft Resource Center Report ,90% The above data leakage is related to network attack . The impact of these leaks may include : Database corruption 、 Intellectual property is stolen 、 Disclosure of secret information , Business organizations need to inform and compensate affected people .
Network threat analysts have the responsibility to carefully examine security vulnerabilities in enterprises and identify malicious attackers , And then improve the safety protection level of the enterprise organization . Besides , Cyber threat analysts are also responsible for digital forensics at digital crime scenes , To determine whether the leak really happened , At the same time, find out stubborn security vulnerabilities or residual malware , And try to recover the data .
2. Find security holes
One of the most important job responsibilities of cyber threat analysts is to find vulnerabilities , In order to plug the loophole in time , In order to avoid the occurrence of leakage . Cyber threat analysts should evaluate the potential vulnerabilities they find , And point out the potential risks faced by enterprise data and assets during the evaluation , And elaborate on why these vulnerabilities may lead to disclosure .
The successful implementation of this task lies in teamwork , This cooperation is not limited to enterprises IT Cooperation among other members of the team , And other non-technical personnel whose work may be affected by safety problems . Network security analysts need to establish open enterprise communication channels , In order to help colleagues in the non network security technology team understand how to use the updated network security program and how to stay away from external attacks .
3. Implement penetration test attack
Penetration test attack is another important responsibility of cyber threat analysts . This behavior is not intended to break through the security line to steal data , But to find and block the security back door before the attacker succeeds . Cyber threat analysts are in the process of conducting penetration testing through the use of software or manual programming skills , You can further crack and use the system , In order to determine how to repair the system once an attack occurs .
4. Formulate and implement organizational safety protection process
Cyber threat analysts need to develop security processes for the entire enterprise organization and its digital ecosystem . Because security is closely related to everyone inside the enterprise , Therefore, everyone in the enterprise must understand and abide by the safety process , Cyber threat analysts must set relevant process standards , And focus on the weakest link in the process .
5. Use, operation and maintenance of security tools
management 、 Installing and using threat discovery software is another important responsibility of network threat analysts . Network threat security analysts may need to install software in the entire system of the enterprise organization to improve email or login security , To prevent malware from entering the network through personal terminals , And strengthen the security of mobile devices , To reduce the possibility of accidental threat penetration of network defense .
Besides , Cyber threat analysts need to ensure that only authorized employees in the enterprise can access sensitive data systems . Adopt identity and access management system (IAM) Can meet this requirement . But analysts are applying IAM Scenario time , We should ensure the IAM The system can correctly identify each user in the enterprise intranet , Ensure that these users have appropriate network access . The recent report of the world economic forum shows ,95% The leakage of network security is caused by human error , There are also some serious extortion software incidents caused by employees who do not know technology inadvertently downloading malware . So if IAM The procedure is implemented and used properly , This risk can be greatly reduced .
In addition to the above main responsibilities , Cyber threat analysts may also be involved in the following other duties :
- Develop a security strategy , To protect data systems from potential threats ;
- Analyze security leaks , Assess the extent of damage ;
- Keep up with current digital security trends , Suggest best practices for strengthening security for the organization ;
- Fix the detected vulnerability , Ensure that the penetration risk is very low or even zero ;
- Respond to network attacks quickly and effectively , In order to minimize damage ;
- Promote network security training , To ensure that all departments of the organization maintain high safety standards ;
- Liaise with stakeholders on cyber security issues , And provide suggestions for the future .
According to the U.S. Bureau of Labor Statistics (BLS) The latest statistics , The current average annual salary of U.S. cyber threat analysts is 103590 dollar . The level of salary depends on skills 、 Experience 、 Qualifications 、 Location, industry sector and other factors , This means that the more experienced you are in this field , The higher the salary level . Besides , If you have a good academic degree and professional skills , You may also enjoy higher salary .
Required skills of cyber threat analysts
Cyber threat analyst is a very professional job , To be a successful 、 Excellent cyber threat analyst , You should have the following ten skills :
1. Intrusion detection capability
Monitoring network activities is one of the important responsibilities of network threat analysts . Learn how to use intrusion detection software such as security information and event management (SIEM) product 、 intrusion detection system (IDS) And intrusion prevention system (IPS) Products such as , Discover possible intrusions , To help enterprises and organizations quickly find suspicious activities or security violations .
2. Safety incident response capability
Although prevention is the main goal of network security , However, in the event of a security incident, rapid response is essential to minimize the possible damage and loss to the enterprise organization . Effective handling of incidents requires understanding the incident response plan of the enterprise organization , It also requires skills in digital forensics and malware investigation .
3. Threat intelligence analysis capability
Cyber Threat Intelligence is a set of information , Through this information, enterprise organizations can understand the past 、 Threats now and in the future . Through Threat Intelligence , Business organizations can expect 、 Prevent and identify network threats that attempt to control important resources of the enterprise .
The Threat Intelligence survey results collect raw data about old and new threats from multiple sources , Then analyze and study these data , Generate threat intelligence sources and management reports , These reports contain information that computerized security control solutions can use . If cyber security analysts keep up with the trends in the threat field , Can become more valuable . Cyber threat analysts need to have the ability to collect and analyze cyber Threat Intelligence .
4. Understand regulatory requirements
Network security is designed to protect business organizations from attacks 、 Theft and loss and meet legal compliance requirements . If a cyber threat analyst works for a company that does business around the world , be familiar with 《 General data protection regulations 》(GDPR) It may help . Data privacy is becoming an integral part of enterprise security and compliance . Cyber threat analysts should understand the basic principles of data privacy and relevant regulations , such as GDPR、《 Health Insurance Portability and Liability Act 》(HIPAA) as well as 《 Children's online privacy protection act 》(COPPA).
5. Familiar with common operating systems
Almost all operating systems have security risks , Including computers and other portable devices , So very familiar MacOS、Windows and Linux And its command line interface , Is expected to become a successful cyber threat analyst , Besides , Research and iOS Threats and weaknesses related to mobile operating systems such as Android are also of great help to cyber threat analysts .
6. Understand the network system
Many network attacks occur on the network of networked devices , But other applications that allow enterprises to collaborate can also lead to security vulnerabilities , Therefore, in order to ensure the safety of the enterprise organization , Analysts need to understand wired and wireless networks and develop targeted protection schemes .
7. Familiar with common security frameworks
The network security framework provides a set of best policies 、 Software 、 Tools and safety procedures , Designed to help organizations protect data and business processes . Security management is a measure used by companies to protect themselves from vulnerabilities and intrusion . The choice of security framework varies from company to company and industry , Therefore, familiarity with some of the most common network security frameworks may be helpful to network threat analysts .
8. Endpoint Management
With the normalization of home office , Enterprise organizations protect many endpoints ( Like computers 、 Phones and IOT devices ) The demand for safety professionals is increasing . Therefore, network threat analysts can pass through the firewall 、 Antivirus software 、 Network access control and virtual private network (VPN) And other tools to improve the ability in this regard .
9. Data security
Data has provided valuable help to many organizations . So cyber threat analysts want to know how to protect data , You need to master data encryption 、 Access management 、 Transmission control and Internet Protocol (TCP and IP) as well as CIA Three elements ( Confidentiality 、 Integrity and accessibility ) The content such as .
10. Programming ability
Although technological advances have enabled cyber threat analysts to handle their work without writing code , But yes. JavaScript、Python and C/C++ A basic understanding of programming languages such as can also bring competitive advantages to cyber threat analysts .
It should be noted that , Although cyber threat analysts are a technical job , But technology alone is not enough , In addition to the above ten professional abilities , Some important career skills are also important for the growth of analysts :
- communicate : Threat analysts need to communicate with others often , And cooperate with the team responsible for safety . When a security incident occurs , Need to contact the security team , And clarify the investigation and retrieval process . Besides , Analysts may also be responsible for training colleagues , Let them know best safety practices .
- Pay attention to the details : Threat analysts need to pay attention to detail to be qualified for this role , Pay special attention to the most subtle adjustments and modifications in the organizational network , Because noticing subtle anomalies may mean that organizations avoid serious data loss .
- critical thinking : Whether responding to threats 、 Fix vulnerabilities or develop new security regulations , Critical thinking skills enable cyber threat analysts to make decisions based on data .
边栏推荐
- 提高應用程序性能的7個DevOps實踐
- Cartoon: interesting pirate problem (full version)
- WR | Jufeng group of West Lake University revealed the impact of microplastics pollution on the flora and denitrification function of constructed wetlands
- 一文了解Go语言中的函数与方法的用法
- Simple query cost estimation
- Disabling and enabling inspections pycharm
- 神经网络自我认知模型
- Cmake tutorial step6 (add custom commands and generate files)
- SQL Server(2)
- QT控制台打印输出
猜你喜欢
Beijing internal promotion | the machine learning group of Microsoft Research Asia recruits full-time researchers in nlp/ speech synthesis and other directions
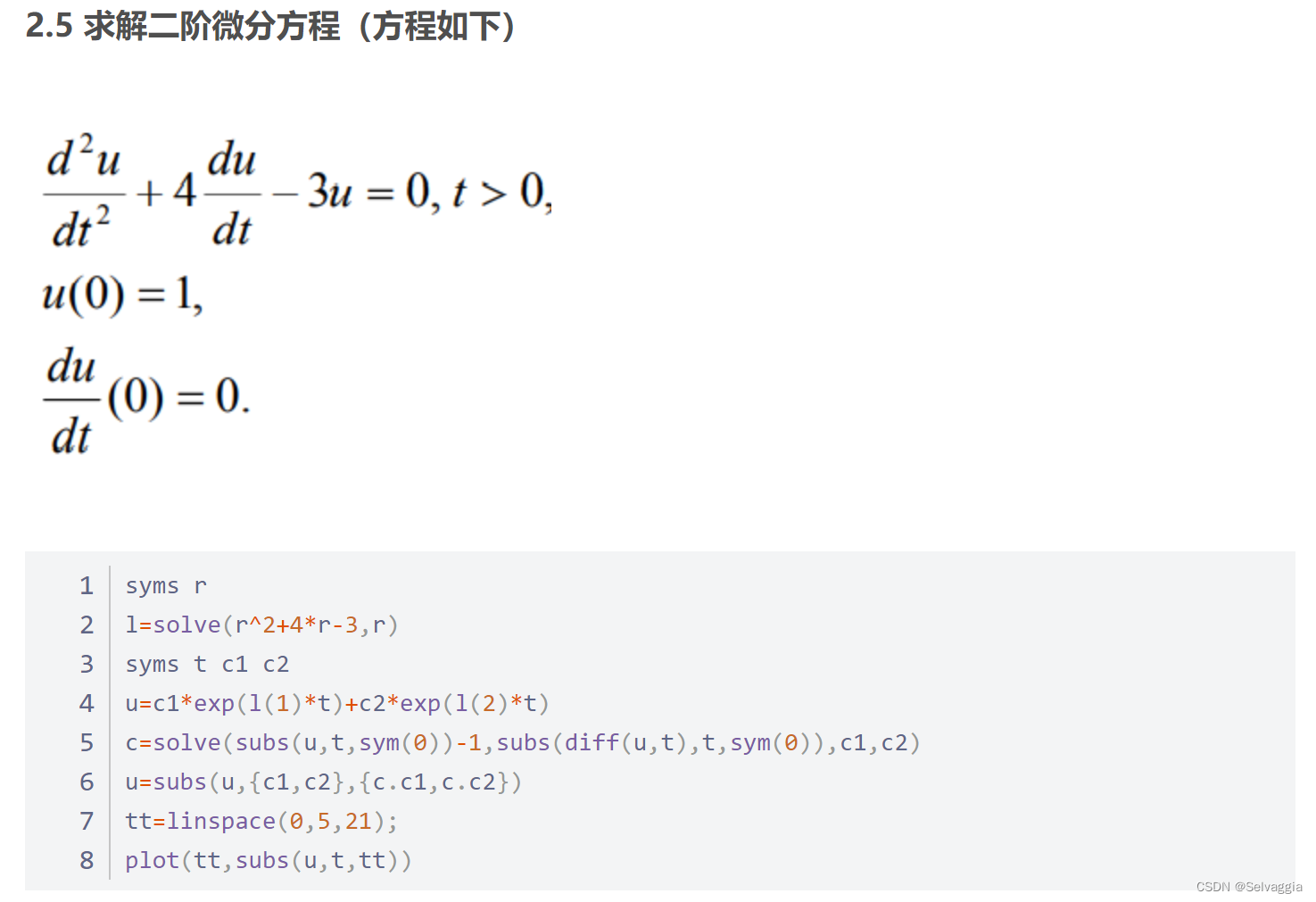
Matlab reference
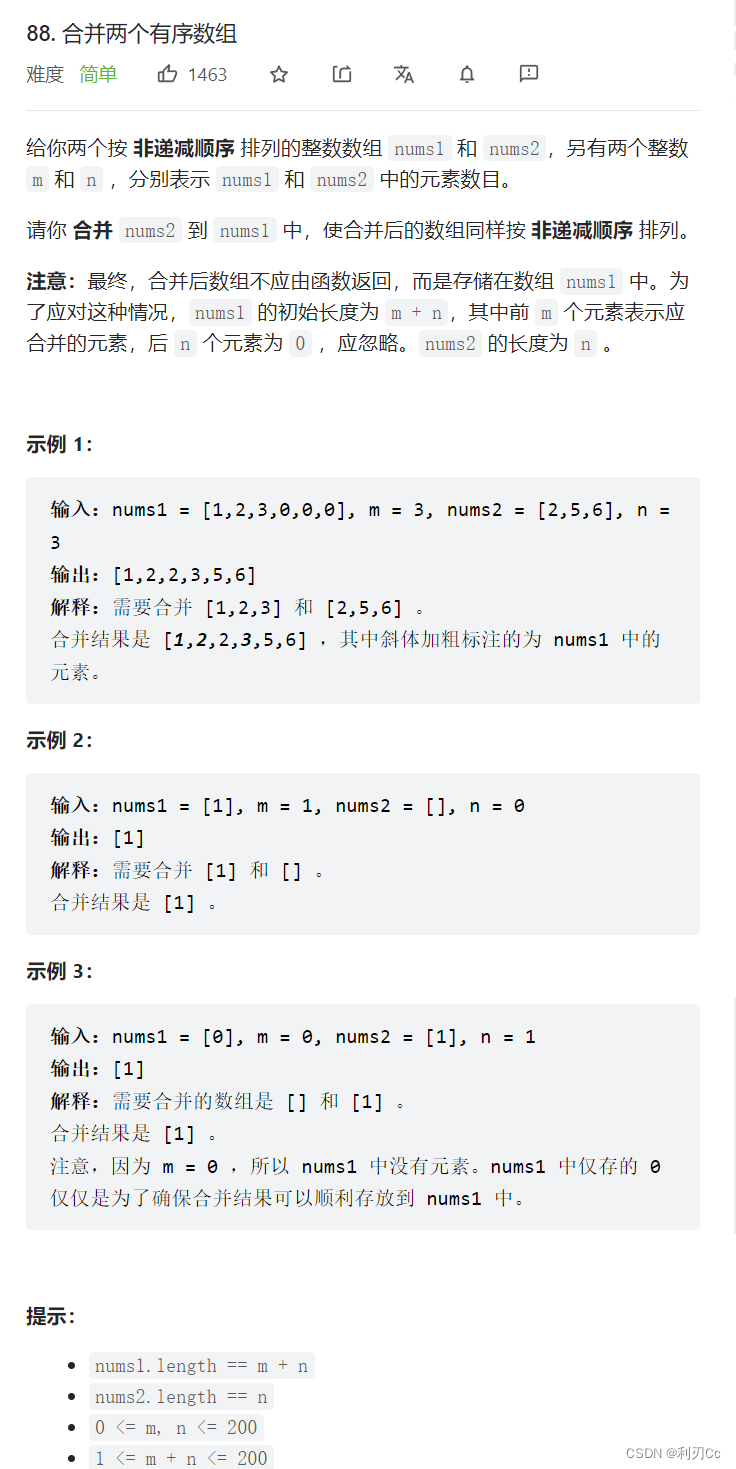
LeetCode每日一题:合并两个有序数组
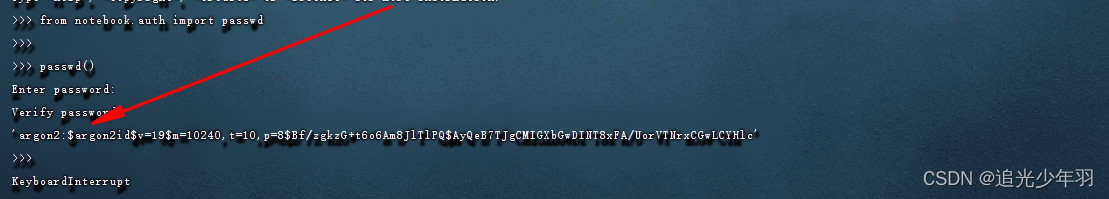
服务器配置 jupyter环境

Why is all (()) true and any (()) false?
解决“双击pdf文件,弹出”请安装evernote程序
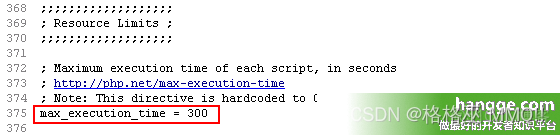
Count the running time of PHP program and set the maximum running time of PHP
ICML 2022 | Meta提出魯棒的多目標貝葉斯優化方法,有效應對輸入噪聲

北京内推 | 微软亚洲研究院机器学习组招聘NLP/语音合成等方向全职研究员

Seven Devops practices to improve application performance
随机推荐
How MySQL uses JSON_ Extract() takes JSON value
统计php程序运行时间及设置PHP最长运行时间
漫画:有趣的【海盗】问题
Anaconda中配置PyTorch环境——win10系统(小白包会)
Short the command line via jar manifest or via a classpath file and rerun
Which is more cost-effective, haqu K1 or haqu H1? Who is more worth starting with?
MySQL之知识点(七)
Is it safe to open an account online? What is the general interest rate of securities financing?
Cartoon: looking for the best time to buy and sell stocks
BigDecimal除法的精度问题
VBA驱动SAP GUI实现办公自动化(二):判断元素是否存在
Winedt common shortcut key modify shortcut key latex compile button
To solve the problem of "double click PDF file, pop up", please install Evernote program
求解为啥all(())是True, 而any(())是FALSE?
论文阅读_中文NLP_LTP
mongodb(快速上手)(一)
解读:如何应对物联网目前面临的安全问题?
使用QT设计师界面类创建2个界面,通过按键从界面1切换到界面2
Clickhouse (03) how to install and deploy Clickhouse
北京内推 | 微软亚洲研究院机器学习组招聘NLP/语音合成等方向全职研究员