当前位置:网站首页>Leetcode force buckle (Sword finger offer 36-39) 36 Binary search tree and bidirectional linked list 37 Serialize binary tree 38 Arrangement of strings 39 Numbers that appear more than half of the tim
Leetcode force buckle (Sword finger offer 36-39) 36 Binary search tree and bidirectional linked list 37 Serialize binary tree 38 Arrangement of strings 39 Numbers that appear more than half of the tim
2022-07-07 19:57:00 【Wood White CPP】
The finger of the sword Offer 36. Binary search tree and double linked list
Answer key :
The idea is simple , It is a medium order traversal , Connect nodes while traversing .
Code :
class Solution {
public:
Node *pre,*head;
void dfs(Node* root){
if(root==nullptr) return;
dfs(root->left);
if(pre==nullptr) head=root;// This is a header node
else
pre->right=root;
root->left=pre;
pre=root;
dfs(root->right);
}
Node* treeToDoublyList(Node* root) {
if(root == nullptr) return root;
dfs(root);
head->left=pre;
pre->right=head;
return head;
}
};result :
The finger of the sword Offer 37. Serialize binary tree
Answer key :
Serialization generally adopts pre order , Middle preface , In the following order , Here we use the preface .
serialize , Use preorder traversal to save the nodes of the binary tree into a string , Between each node ’,‘ separate . It is worth noting that , In the process of traversal, we need to treat the binary tree as a full binary tree , Blank nodes with ’null‘ Express .
Deserialization , Put the string in the queue que in , use ’,‘ Judge and push into the queue . Traverse through the preamble , While traversing the preorder, establish a binary tree node .
Code :
class Codec {
public:
// Encodes a tree to a single string.
string serialize(TreeNode* root) {
if(root==nullptr) return "null,";
string str=to_string(root->val)+',' ;
str+=serialize(root->left);
str+=serialize(root->right);
return str;
}
// Decodes your encoded data to tree.
TreeNode* deserialize(string data) {
queue<string> que;
string str;
for(auto i:data){
if(i==','){
que.push(str);
str.clear();
}
else
str.push_back(i);
}
return rdeserialize(que);
}
TreeNode* rdeserialize(queue<string> &que){
if (que.front() == "null") {
que.pop();
return nullptr;
}
TreeNode* root = new TreeNode(stoi(que.front()));
que.pop();
root->left = rdeserialize(que);
root->right = rdeserialize(que);
return root;
}
};result :
The finger of the sword Offer 38. Arrangement of strings
Answer key :
The key is to repeat , Because there are repeated characters . You can use a flag bit , Judge whether the current character appears in the previous string .
Code :
class Solution {
public:
vector<string> res;
void dfs(string &s,int sz,int pos){
if(pos==sz) res.push_back(s);
for(int i=pos;i<sz;++i){
bool flag=true;
for(int j=pos;j<i;++j){
if(s[j]==s[i]) flag=false;
}
if(flag){
swap(s[i],s[pos]);
dfs(s,sz,pos+1);
swap(s[i],s[pos]);
}
}
}
vector<string> permutation(string s) {
dfs(s,s.size(),0);
return res;
}
};result :
The finger of the sword Offer 39. A number that appears more than half the times in an array
There is a number in an array that appears more than half the length of the array , Please find out the number .
You can assume that the array is not empty , And there are always many elements in a given array .
Answer key :
Method 1 : Sort
If there are more than half of the repeated characters , After sorting, it must be in the middle of the array .
Code :
class Solution {
public:
int majorityElement(vector<int>& nums) {
sort(nums.begin(),nums.end());
return nums[nums.size()/2];
}
};result :
Method 2 : Hash
Store with hash , Once the value is greater than half the length of the array, the value is returned .
Code :
class Solution {
public:
int majorityElement(vector<int>& nums) {
unordered_map<int,int>map;
for(auto i:nums){
++map[i];
if(map[i]>nums.size()/2) return i;
}
return -1;
}
};result :
边栏推荐
- 一张图深入的理解FP/FN/Precision/Recall
- mock.js从对象数组中任选数据返回一个数组
- Responsibility chain model - unity
- R语言ggplot2可视化:使用ggpubr包的ggecdf函数可视化分组经验累积密度分布函数曲线、linetype参数指定不同分组曲线的线型
- 杰理之开机自动配对【篇】
- 微信公众号OAuth2.0授权登录并显示用户信息
- 华南X99平台打鸡血教程
- R language ggplot2 visualization: use the ggqqplot function of ggpubr package to visualize the QQ graph (Quantitative quantitative plot)
- 模拟实现string类
- PMP對工作有益嗎?怎麼選擇靠譜平臺讓備考更省心省力!!!
猜你喜欢
Redis master-slave and sentinel master-slave switchover are built step by step
Jürgen Schmidhuber回顾LSTM论文等发表25周年:Long Short-Term Memory. All computable metaverses. Hierarchical reinforcement learning (RL). Meta-RL. Abstractions in generative adversarial RL. Soccer learn
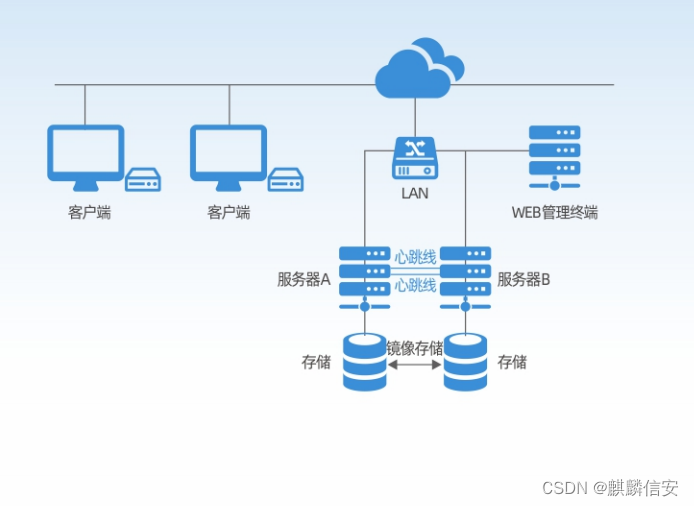
Empowering smart power construction | Kirin Xin'an high availability cluster management system to ensure the continuity of users' key businesses
Is PMP beneficial to work? How to choose a reliable platform to make it easier to prepare for the exam!!!
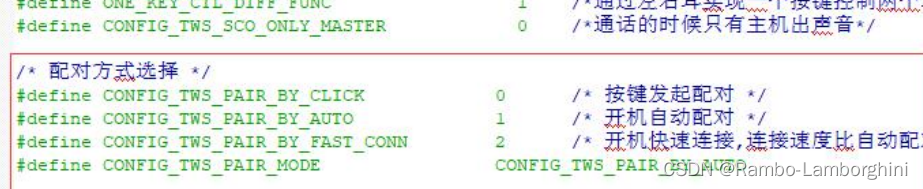
杰理之关于 TWS 配对方式配置【篇】
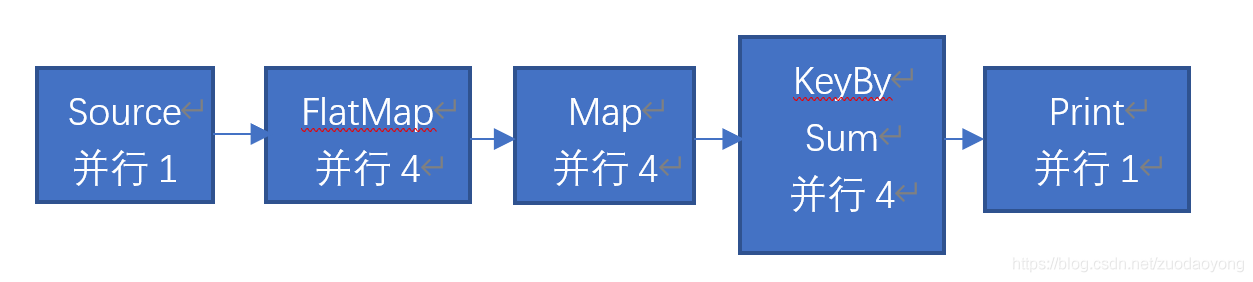
Detailed explanation of Flink parallelism and slot

AD域组策略管理
Automatic classification of defective photovoltaic module cells in electroluminescence images-论文阅读笔记
mock.js从对象数组中任选数据返回一个数组
编译器优化那些事儿(4):归纳变量
随机推荐
Responsibility chain model - unity
8 CAS
Netease Yunxin participated in the preparation of the standard "real time audio and video service (RTC) basic capability requirements and evaluation methods" issued by the Chinese Academy of Communica
多个线程之间如何协同
what‘s the meaning of inference
2022如何评估与选择低代码开发平台?
浏览积分设置的目的
Interpretation of transpose convolution theory (input-output size analysis)
ant desgin 多选
R language ggplot2 visualization: use the ggstripchart function of ggpubr package to visualize the dot strip plot, set the position parameter, and configure the separation degree of different grouped
Specify the version of OpenCV non-standard installation
关于ssh登录时卡顿30s左右的问题调试处理
使用高斯Redis实现二级索引
Mysql, sqlserver Oracle database connection mode
R语言fpc包的dbscan函数对数据进行密度聚类分析、查看所有样本的聚类标签、table函数计算聚类簇标签与实际标签构成的二维列联表
UCloud是基础云计算服务提供商
LeetCode力扣(剑指offer 36-39)36. 二叉搜索树与双向链表37. 序列化二叉树38. 字符串的排列39. 数组中出现次数超过一半的数字
Redis——基本使用(key、String、List、Set 、Zset 、Hash、Geo、Bitmap、Hyperloglog、事务 )
Semantic SLAM源码解析
歌单11111