当前位置:网站首页>Model analysis of establishment time and holding time
Model analysis of establishment time and holding time
2022-07-06 00:23:00 【Silly boy: CPU】
Build time and hold time model analysis
The starting point is the source trigger D1 Sampling time of , The destination is the destination trigger D2 Sampling time of , It is assumed that the starting point has met the requirements of establishment time and holding time , Now analyze whether the end-point sampling time also meets the requirements .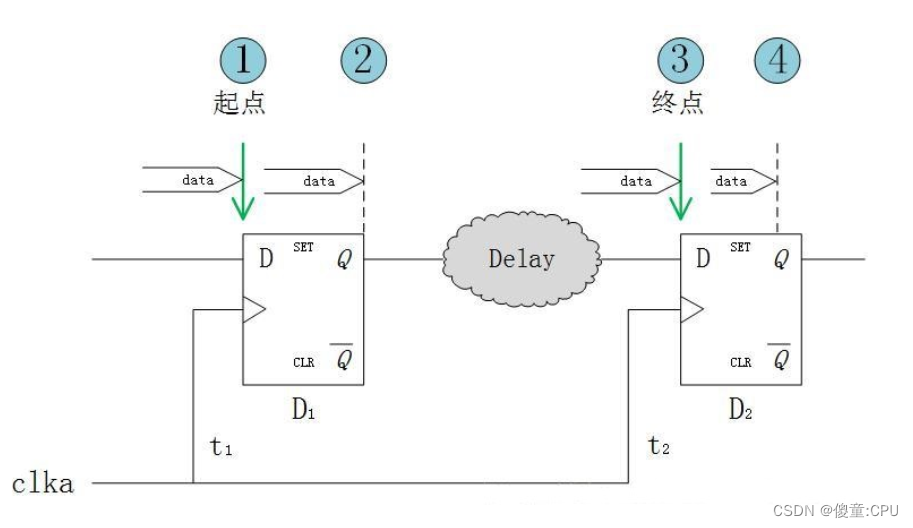
among
- Tco: The data is sampled correctly from D End arrival Q The delay of the end , Trigger intrinsic properties , It can't be changed .
- TDelay:D1 Output to D2 Combinational logic delay and wiring delay at the input .
- Tsu: Trigger setup time , Inherent properties of triggers , It can't be changed .
- Th: Hold time of trigger , Inherent properties of triggers , It can't be changed .
- Tclk: Clock cycle .
- t1: Assume that the source clock is clka,clka arrive D1 Time delay of .
- t2:clka arrive D2 Time delay of .
The behavior of triggers : Sampling data when the clock edge arrives D, Deposit the collected data , And output to the Q End , All if no new clock comes along , be Q The output of the terminal is always the last sampled data , Every clock edge , Sample the data once D.
hypothesis clk There is no delay in transmission : Then the rising edge of each clock will arrive at the same time D1 and D2. The beginning of time , The first clock edge D1 Sampling time of , The end of time , The second clock edge D2 Sampling time of . Physical starting point ,D1 The input end of the , Physical end point ,D2 The input end of the .
Set up time to meet ( Focus on data headers ): When the first clock comes , data data From the starting point ① Start transmitting , after Tco arrive ②, after TDelay
边栏推荐
- LeetCode 6005. The minimum operand to make an array an alternating array
- STM32 configuration after chip replacement and possible errors
- Pointer pointer array, array pointer
- Leetcode:20220213 week race (less bugs, top 10% 555)
- The difference of time zone and the time library of go language
- Detailed explanation of APP functions of door-to-door appointment service
- Room cannot create an SQLite connection to verify the queries
- 2022.7.5-----leetcode. seven hundred and twenty-nine
- FFMPEG关键结构体——AVFrame
- wx. Getlocation (object object) application method, latest version
猜你喜欢
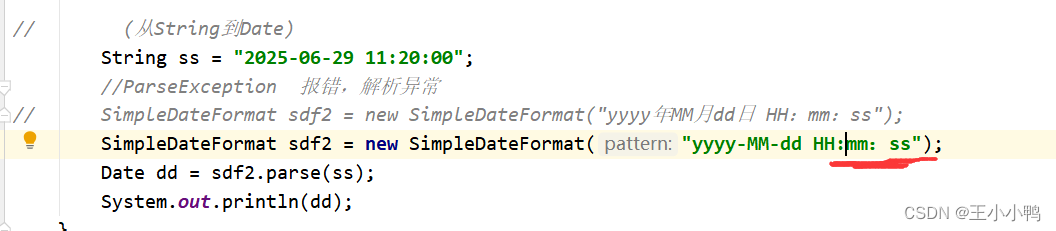
Problems and solutions of converting date into specified string in date class
FFMPEG关键结构体——AVFrame
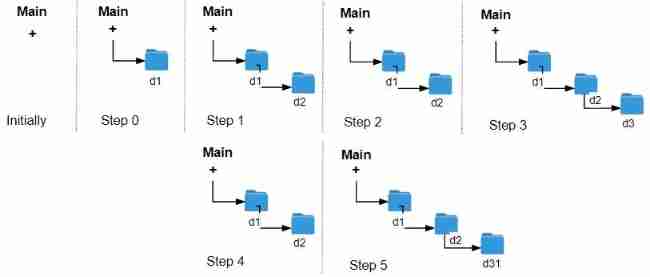
LeetCode 1598. Folder operation log collector
AtCoder Beginner Contest 254【VP记录】
Start from the bottom structure and learn the introduction of fpga---fifo IP core and its key parameters
![[noi simulation] Anaid's tree (Mobius inversion, exponential generating function, Ehrlich sieve, virtual tree)](/img/d6/c3128e26d7e629b7f128c551cd03a7.png)
[noi simulation] Anaid's tree (Mobius inversion, exponential generating function, Ehrlich sieve, virtual tree)
Hudi of data Lake (2): Hudi compilation
MySQL存储引擎
![Go learning --- structure to map[string]interface{}](/img/e3/59caa3f2ba5bd3647bdbba075ee60d.jpg)
Go learning --- structure to map[string]interface{}
What are Yunna's fixed asset management systems?
随机推荐
Huawei equipment is configured with OSPF and BFD linkage
Gd32f4xx UIP protocol stack migration record
从底层结构开始学习FPGA----FIFO IP核及其关键参数介绍
Shardingsphere source code analysis
Power query data format conversion, Split Merge extraction, delete duplicates, delete errors, transpose and reverse, perspective and reverse perspective
Intranet Security Learning (V) -- domain horizontal: SPN & RDP & Cobalt strike
The difference of time zone and the time library of go language
JS can really prohibit constant modification this time!
Yolov5, pychar, Anaconda environment installation
Problems and solutions of converting date into specified string in date class
MySql——CRUD
Pointer - character pointer
Detailed explanation of APP functions of door-to-door appointment service
Codeforces gr19 D (think more about why the first-hand value range is 100, JLS yyds)
Calculate sha256 value of data or file based on crypto++
2022-02-13 work record -- PHP parsing rich text
Leetcode:20220213 week race (less bugs, top 10% 555)
N1 # if you work on a metauniverse product [metauniverse · interdisciplinary] Season 2 S2
7.5模拟赛总结
FFMPEG关键结构体——AVFormatContext