当前位置:网站首页>A brief understanding of white box encryption technology
A brief understanding of white box encryption technology
2022-07-01 19:31:00 【Infinitesimal pawn】
Monologue :
When I first came into contact with white box encryption technology last year , After reading some relevant documents , Do some sorting on the generated output . Completely understand from a little white's perspective , Maybe the understanding of white box encryption technology is not particularly good , But I hope it can help Xiaobai understand white box .

problem :
I read the document with three simple questions .
One 、 What is a white box ?
Two 、 What can a white box do ?
3、 ... and 、 What are the advantages of white box technology ?
Cryptographic concepts :
Cryptography , seeing the name of a thing one thinks of its function , Is trying to hide sensitive data through various methods , To prevent others from seeing this information . In real life, due to the influence of many factors and environmental conditions , The protection strength of the key is weakened . In a white box environment , Traditional password technology lacks enough protection , In the face of various attacks against its inherent defects, it can't completely deal with
Therefore, in order to deal with the attack in the white box environment , New encryption technologies have emerged —— White box encryption .
What is a white box :
White box cryptography assumes that the attacker has completely controlled the entire encryption process and is completely visible , In this case, deal with the serious threat . Hackers can observe the running process of dynamic passwords without restrictions ( Have the sample key ), And the details of the internal algorithm are completely visible , Be free to change .
Although the method of white box cryptography is completely transparent , But it combines passwords so that the key is not easy to extract . To make a long story short , White box encryption is an encryption technology that can resist white box attacks .
The key plaintext will be protected after being encrypted by white box , It will not appear directly in memory , So it will not be extracted .
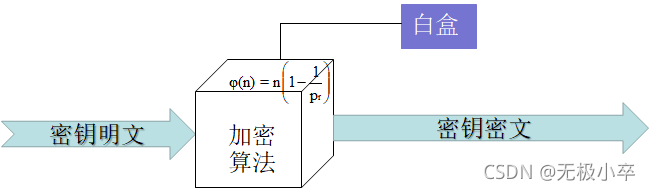
Decryption functions can be performed inside distributed applications , But the key cannot be extracted , And decryption can not be reverse operation to encrypt . The attacker has no feasible way to create the correct encrypted data , Therefore, reverse decryption cannot be used to generate the desired key value .

When the information transmission channel is affected by hardware equipment ( For example, hardware protection token ) When protecting , White box encryption is quite effective . Because hackers cannot extract the key of the secure channel , So they can neither decrypt the data flowing through the transmission channel , It is also impossible to inject data into the transmission channel .
What can a white box do :
Cover many fields in life , vehicle 、 Finance 、 Communications, etc , In terms of technical implementation, each field involves the three-tier architecture of the Internet of things , Involving specific sensing devices 、 Move APP、 Cloud 、 Communication and security .
Advantages of white box encryption :
1、 White box cryptography provides a method of encryption in a completely transparent environment . Although it is completely transparent , Encryption and decryption programs protect sensitive data from disclosure .
Besides , Although I know that hackers may be observing the executed code , White box encryption technology can also realize strong encryption mechanism ( Combined with other technologies )
2、 White box cipher algorithm is a new cipher algorithm , The difference between it and the traditional cryptographic algorithm is that it can resist the attack in the white box attack environment . White box password enables key information to be fully hidden 、 To prevent prying , Therefore, it ensures the safe application of the original password system in the sensing device , Greatly improved security .
3、 Protect sensing devices 、 There are also corresponding hardware solutions to protect key security , But in this competitive landscape , Hardware solutions will inevitably increase the cost burden of manufacturers , It even leads to the neglect of safety problems because of the cost . White box password as a software solution , The corresponding hardware scheme naturally has the advantage of low cost .
4、 White box cryptography, as a software defined security, has entered the lower level of the basic chip security field . Compare hardware to provide security , White box cryptography is constantly breaking through and studying by using confusion technology and various mathematical theories , There is still much room for development in the future ; At the same time, new attacks against Internet of things devices emerge in endlessly , White box password as a software can be more flexible dynamic response , Other security measures can be integrated , Updating and upgrading are also more convenient and fast .
5、 White box password application does not need the participation of various providers , And it can be enjoyed exclusively by one application , Data and security can be better controlled by application developers , At present HCE Cloud payment adopts the white box protection scheme . White box encryption technology, whether from management or technology , Have built a more simplified 、 A more pure trusted relationship .
summary :
The overall security of a protected application is highly dependent on the application itself , in other words , When the encryption algorithm is not used in the environment it is designed , Strong encryption algorithm alone cannot provide any security —— Not in white White box encryption technology is used in box applications , It will make hackers reverse operate the protected software . Most common attacks attempt to exploit vulnerabilities in password security rather than weaknesses in encryption algorithms —— But recently, hackers have realized that classical cryptography is open PC Vulnerable characteristics in the environment .
without doubt , Special attention must be paid to software protection in the design and application stages , In addition, it should be continuously strengthened throughout the product life cycle and the new version released . In addition to white box cryptography , Additional supplementary safety measures should also be adopted to further strengthen the overall protection scheme .
边栏推荐
- Lake Shore 连续流动低温恒温器传输线
- More information about M91 fast hall measuring instrument
- Les canaux de culture intensive s'efforcent de développer Fu Xin et Wei Shi jiajie pour organiser une conférence de formation sur les nouveaux produits
- MFC中如何重绘CListCtrl的表头
- [6.24-7.1] review of wonderful technical blog posts in the writing community
- Learning notes - steps of JDBC connection database operation
- Lake shore optimag superconducting magnet system om series
- 【To .NET】C#集合类源码解析
- 物联网平台thingsboard搭建学习记录
- 【6.24-7.1】写作社区精彩技术博文回顾
猜你喜欢

原生js打造日程表-支持鼠标滚轮滚动选择月份-可以移植到任何框架中
Dlib+Opencv库实现疲劳检测

B2B e-commerce platform solution for fresh food industry to improve the standardization and transparency of enterprise transaction process

寶,運維100+服務器很頭疼怎麼辦?用行雲管家!

智慧防疫系统为建筑工地复工复产提供安全保障

Lake Shore 连续流动低温恒温器传输线
Once the SQL is optimized, the database query speed is increased by 60 times

The intelligent epidemic prevention system provides safety guarantee for the resumption of work and production at the construction site
案例分享:QinQ基本组网配置

Helium transmission line of lake shore cryostat
随机推荐
Superoptimag superconducting magnet system - SOM, Som2 series
Specification of lumiprobe reactive dye indocyanine green
PMP是被取消了吗??
【pytorch记录】模型的分布式训练DataParallel、DistributedDataParallel
Cdga | if you are engaged in the communication industry, you should get a data management certificate
论文泛读【FiLM: Visual Reasoning with a General Conditioning Layer】
数字化转型企业成功的关键,用数据创造价值
transform + asm资料
Transform + ASM data
Instagram 为何从内容共享平台变成营销工具?独立站卖家如何利用该工具?
为什么一定要从DevOps走向BizDevOps?
简版拼多多商品数据
【英语语法】Unit1 冠词、名词、代词和数词
Lake Shore—CRX-EM-HF 型低温探针台
What must be done in graduation season before going to Shanhai
原生js打造日程表-支持鼠标滚轮滚动选择月份-可以移植到任何框架中
Bao, what if the O & M 100+ server is a headache? Use Xingyun housekeeper!
Dom4J解析XML、Xpath检索XML
703. 数据流中的第 K 大元素
Collation of open source protocols of open source frameworks commonly used in Web Development