当前位置:网站首页>App mobile terminal test [3] ADB command
App mobile terminal test [3] ADB command
2022-07-03 15:52:00 【Leo_ Eagle】
Adb(android Debug Bridge), It allows real machines and simulators ( Or mobile assistant ) communicate . This greatly improves the equipment ( Real machine ) Convenient operation .
1.ADB The cognitive
1.1 Adb The cognitive
Adb(android Debug Bridge), It allows real machines and simulators ( Or mobile assistant ) communicate . This greatly improves the equipment ( Real machine ) Convenient operation
The teacher's , Android sdk The path is as follows :D:\Program Files (x86)\Android\android-sdk\platform-tools, In this directory, you can see adb At the beginning 3 File ,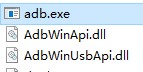
verification adb Whether the configuration is complete . stay Cmd Input in adb
Cmd
Adb
1.2 Adb How it works
start-up adb client , The client will communicate with the local TCP port (5037) binding , Then start listening adb All commands issued by the client , Then use the port 5037 And adb Server communication .
1.3 Enable adb debugging
It must be started on the mobile phone usb debugging , Only then can we carry on adb debugging ( If you don't know how to turn on your mobile phone usb debugging , Please check the previous article :uiautomator
++App Mobile Testing 【2】 Android simulator deployment ++).
1.4 Adb The basic order of
stay cmd The following is executed in
- see adb edition
C:\Users\Leo>adb version
- View device information
C:\Users\Leo>adb devices
List of devices attached
* daemon not running; starting now at tcp:5037
* daemon started successfully
GWY0217306003796 unauthorized
2. ADB The basic order of
2.1 Adb The basic order of
- see adb edition
C:\Users\Leo>adb version
- View device information
C:\Users\Leo>adb devices
List of devices attached
* daemon not running; starting now at tcp:5037
* daemon started successfully
GWY0217306003796 unauthorized
- Connect the simulator
C:\Users\Leo>adb connect 127.0.0.1:62001
matters needing attention : The first of the night God simulator 1 The port of the simulator is 62001, The first 2 The stage is 62025, The first 3 platform 62025+1.
C:\Users\Leo>adb connect 127.0.0.1:62001
adb server version (36) doesn't match this client (40); killing...
reason : The above (adb server version (36) doesn’t ….) The reason for the hint , Because android sdk Medium adb Version and simulator adb Different versions result in .
Solution :
hold android sdk Next 3 individual adb Opening file ( Here's the picture ), Copy to the simulator , Replace simulator (D:\Program Files\Nox\bin) Corresponding 3 File ( Here's the picture ).
- Adb shell
Adb shell
When there are multiple devices ( Simulator Links pc When )
C:\Users\Leo>adb -s 127.0.0.1:62001 shell
[email protected]:/ #
Format adb –s Simulator required ip And port shell
Test intensive video
If you don't find your article enjoyable , You can see the detailed video tutorial .
《 Necessary skills for Mobile Testing 》
UI automated testing :Selenium3 automated testing
【 Test the full series of video courses 】
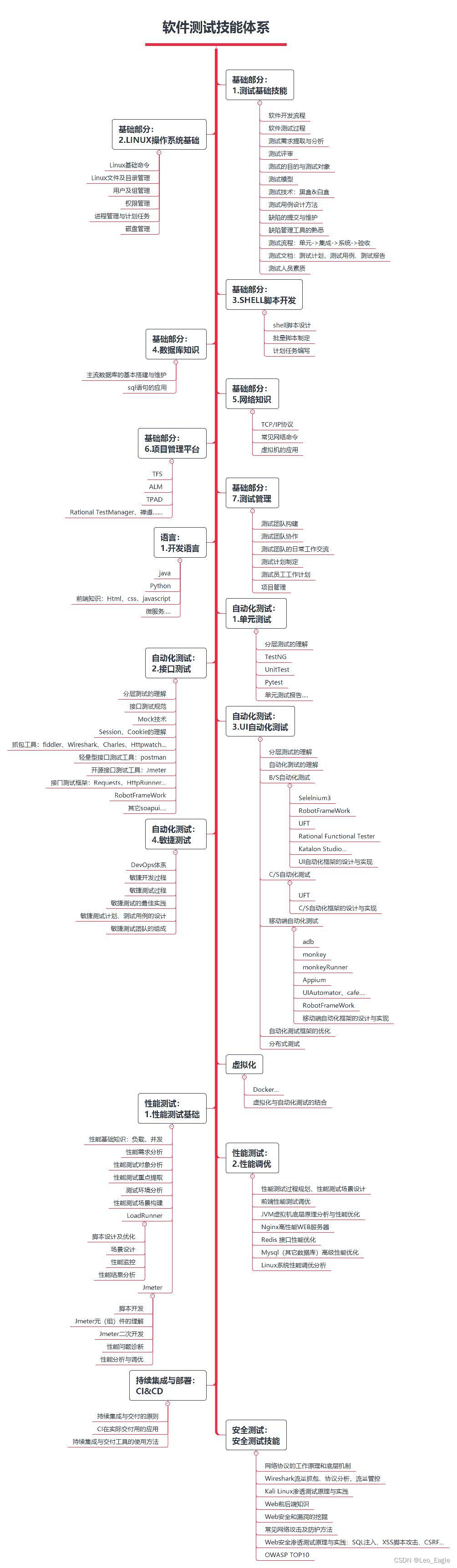
The learning route is as follows



边栏推荐
- Microservice API gateway zuul
- nifi从入门到实战(保姆级教程)——flow
- Visual upper system design and development (Halcon WinForm) -4 Communication management
- Visual host system design and development (Halcon WinForm)
- 工资3000,靠“视频剪辑”月入40000:会赚钱的人,从不靠拼命!
- 通过进程PID获取可执行文件路径(QueryFullProcessImageName)
- Visual upper system design and development (Halcon WinForm) -3 Image control
- 《微服务设计》读书笔记(下)
- Brush questions -- sword finger offer
- Reentrantlock usage and source code analysis
猜你喜欢

半监督学习

深度学习之三维重建
WinDbg analysis dump file

How are integer and floating-point types stored in memory

从 flask 服务端代码自动生成客户端代码 -- flask-native-stubs 库介绍

“用Android复刻Apple产品UI”(3)—优雅的数据统计图表

Tensorflow realizes verification code recognition (I)

Jvm-08-garbage collector
![[系统安全] 四十三.Powershell恶意代码检测系列 (5)抽象语法树自动提取万字详解](/img/cd/00954b9c592c253d42e6a3b8298999.jpg)
[系统安全] 四十三.Powershell恶意代码检测系列 (5)抽象语法树自动提取万字详解
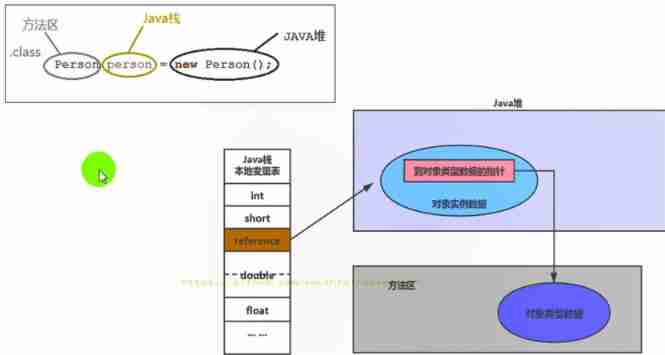
Jvm-04-runtime data area heap, method area
随机推荐
需要知道的字符串函数
Jvm-04-runtime data area heap, method area
Win32 create window and button (lightweight)
“用Android复刻Apple产品UI”(3)—优雅的数据统计图表
Distributed task scheduling XXL job
Brush questions -- sword finger offer
Please be prepared to lose your job at any time within 3 years?
The difference between mutually exclusive objects and critical areas
Jvm-08-garbage collector
socket. IO build distributed web push server
Qt常用语句备忘
CString在多线程中的问题
A Fei's expectation
软件逆向破解入门系列(1)—xdbg32/64的常见配置及功能窗口
Under VC, Unicode and ANSI are converted to each other, cstringw and std:: string are converted to each other
How to use annotations such as @notnull to verify and handle global exceptions
Using optimistic lock and pessimistic lock in MySQL to realize distributed lock
Large CSV split and merge
QT use qzxing to generate QR code
Microservice - Nacos registration center and configuration center