当前位置:网站首页>Naoqi robot summary 26
Naoqi robot summary 26
2022-07-05 23:25:00 【hiyaaa】
Basic algorithm
#include<bits/stdc++.h>
using namespace std;
const int N=1100;
int size[N];
char s[N][N];
int vis[N][N];
int dx[8]={0,1,0,-1,-1,1,1,-1};
int dy[8]={1,0,-1,0,1,1,-1,-1};
int m,cnt;
int a[N],b[N],tot,tot1;
void dfs(int x,int y,int &ans,int k)
{// For every cannon attacked , So it's centered 3*3 The squares will be affected , So find the connected block , The number of each connected block , And the number of cannons in each connected block .
if(s[x][y]=='.') return ;
vis[x][y]=true;
for(int i=0;i<8;i++)
{
int xx=dx[i]+x;
int yy=dy[i]+y;
if(xx<k||xx>=k+4||yy<0||y>=m||vis[xx][yy]) continue;
vis[xx][yy]=true;
if(s[xx][yy]=='*') ans++;
dfs(xx,yy,ans,k);
}
}
int main()
{
cin>>m;
for(int i=0;i<8;i++) cin>>s[i];
for(int i=0;i<4;i++)
{
for(int j=0;j<m;j++)
{
if(s[i][j]=='*'&&!vis[i][j])
{
cnt=1;
dfs(i,j,cnt,0);
a[++tot]=cnt;
}
}
}
for(int i=4;i<8;i++)
{
for(int j=0;j<m;j++)
{
if(s[i][j]=='*'&&!vis[i][j])
{
cnt=1;
dfs(i,j,cnt,4);
b[++tot1]=cnt;
}
}
}
if(tot1<tot) cout<<-1<<endl;
else
{
sort(b+1,b+1+tot1);
int ans=0;
for(int i=tot;i<=tot1;i++) ans+=b[i];
cout<<ans<<endl;
}
}
#include <bits/stdc++.h>
const int maxn = 510;
const int MaxN = 0x3f3f3f3f;
const int MinN = 0xc0c0c00c;
typedef long long ll;
const int mod = 100000000;
using namespace std;
char a[maxn][maxn];
bool visited[maxn][maxn];
bool flag=false;
int n,m;
int dx[4]={0,0,1,-1};
int dy[4]={1,-1,0,0};
void dfs(int x,int y){
if(a[x][y]=='E'){
flag=true;
return ;
}
if(flag==true) return ;
for(int i=0;i<4;i++){
int nx=x+dx[i];
int ny=y+dy[i];
if((a[nx][ny]=='.'||a[nx][ny]=='E')&&!visited[nx][ny]){
visited[nx][ny]=true;
dfs(nx,ny);
}
}
}
int main()
{
while(cin>>n>>m){
memset(visited,false,sizeof(visited));
memset(a,-1,sizeof(a));
for(int i=1;i<=n;i++){
scanf("%s",a[i]+1);
}
for(int i=1;i<=n;i++){
for(int j=1;j<=m;j++){
if(a[i][j]=='S'){
flag=false;
visited[i][j]=true;
dfs(i,j);
break;
}
}
}
if(flag) cout<<"Yes"<<endl;
else cout<<"No"<<endl;
}
return 0;
}
边栏推荐
- Hj16 shopping list
- Multi sensor fusion of imu/ optical mouse / wheel encoder (nonlinear Kalman filter)
- Hainan Nuanshen tea recruits warmhearted people: recruitment of the product experience recommender of Nuanshen multi bubble honey orchid single cluster
- Difference between out of band and in band
- Multi sensor fusion of imu/ electronic compass / wheel encoder (Kalman filter)
- Attacking technology Er - Automation
- 6-axis and 9-axis IMU attitude estimation
- 424. 替换后的最长重复字符 ●●
- Realize reverse proxy client IP transparent transmission
- Leecode learning notes
猜你喜欢

Hainan Nuanshen tea recruits warmhearted people: recruitment of the product experience recommender of Nuanshen multi bubble honey orchid single cluster
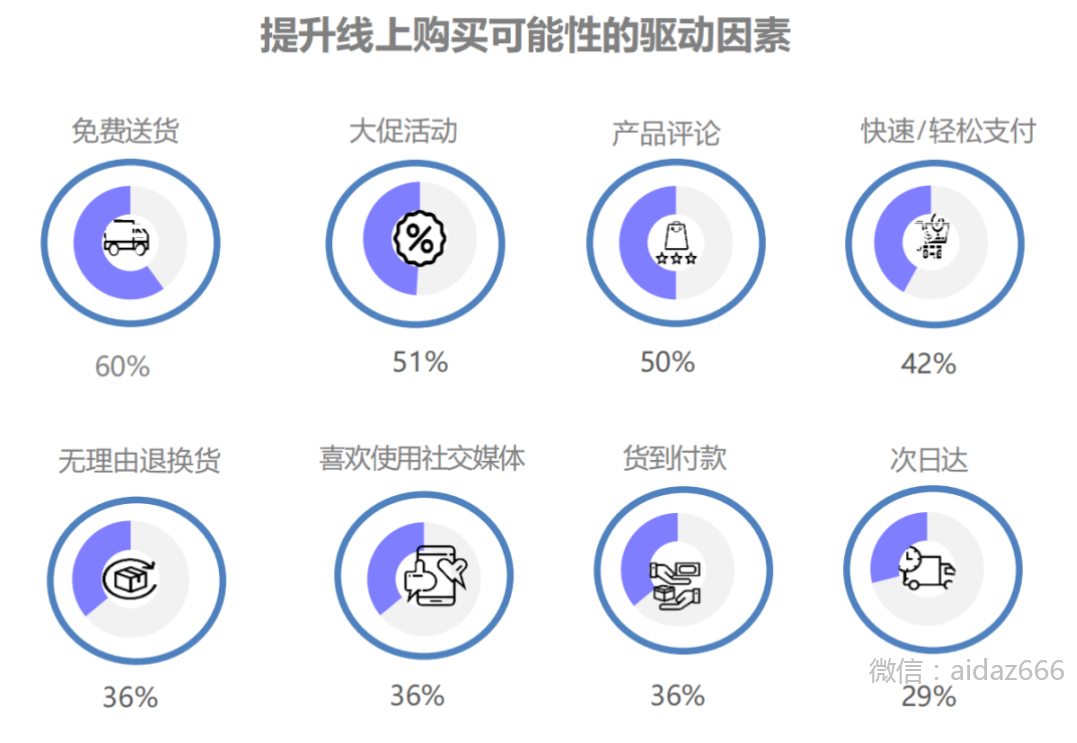
Southeast Asia e-commerce guide, how do sellers layout the Southeast Asia market?
Practice of concurrent search
Getting started stm32--gpio (running lantern) (nanny level)

数学公式截图识别神器Mathpix无限使用教程

视频标准二三事

Non rigid / flexible point cloud ICP registration
2022 registration examination for safety management personnel of hazardous chemical business units and simulated reexamination examination for safety management personnel of hazardous chemical busines
TVS管 与 稳压二极管参数对比
TypeError: this. getOptions is not a function
随机推荐
Creative mode 1 - single case mode
LeetCode102. Sequence traversal of binary tree (output by layer and unified output)
Xinyuan & Lichuang EDA training camp - brushless motor drive
数据库基础知识(面试)
Golang code checking tool
视频标准二三事
并查集实践
两数之和、三数之和(排序+双指针)
ORB_ SLAM2/3
LeetCode145. Post order traversal of binary tree (three methods of recursion and iteration)
MySQL (1) -- related concepts, SQL classification, and simple operations
UART Application Design and Simulation Verification 2 - TX Module Design (Stateless machine)
Introduction to JVM
Detailed explanation of pointer and array written test of C language
Différence entre hors bande et en bande
Use the rewrite rule to rewrite all accesses to the a domain name to the B domain name
Multi sensor fusion of imu/ electronic compass / wheel encoder (Kalman filter)
Neural structured learning 4 antagonistic learning for image classification
Southeast Asia e-commerce guide, how do sellers layout the Southeast Asia market?
Use of grpc interceptor