当前位置:网站首页>Describe the process of key exchange
Describe the process of key exchange
2022-07-06 18:39:00 【JohnnyFang】
key exchange (IKE,Internet Key Exchange ) There are mainly two ways to implement , One is public key encryption , One is to make use of DH Algorithm encryption for key exchange .
- Public key encryption
1.1 Symmetric encryption
Suppose there are two people Alice and Bob,Alice As the sender, it is necessary to transmit data to the receiver Bob, The two directly discussed a secret key to encrypt the data ,Bob After receiving it, you can directly open the original data by using the negotiated secret key ( Here's the picture ).
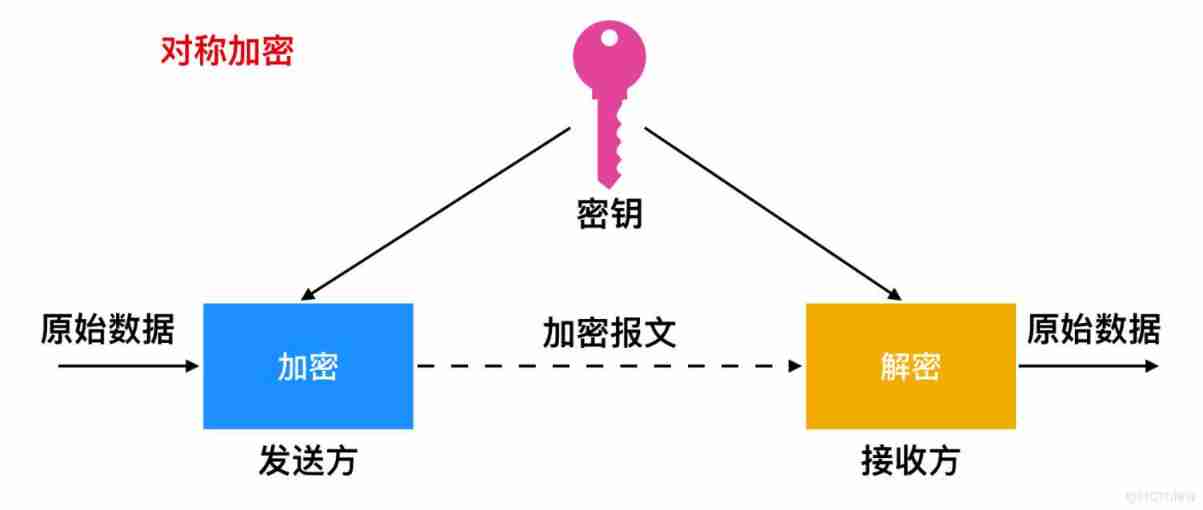
Of course, this is the ideal state , If someone else gets the secret key , And intercepted the data , You can also view data , Public key exchange can be improved on this basis .
1.2 Asymmetric encryption
Public key exchange is realized by asymmetric encryption , Both sender and receiver have their own public and private keys , And use in pairs . We still use Alice towards Bob Take data transmission as an example ,Bob The public key and private key of are P and S,Alice Before sending the data , utilize Bob The public key P To encrypt the data , And to decrypt , Only Bob The private key S To open , Even if others intercept the data , Can't view it ( Here's the picture ).
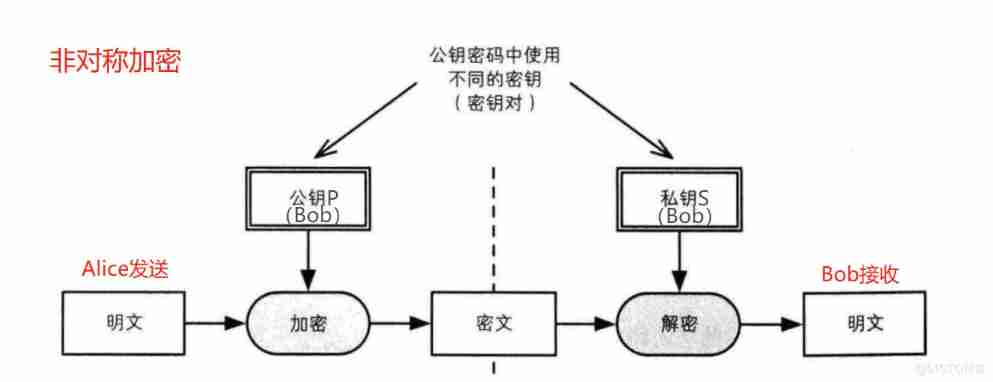
1.3 Asymmetric encryption realizes digital signature
Because the public key is public ,Alice You can give Bob To transmit data , Others can also , To ensure that the data received by the receiver is transmitted by the agreed sender , The form of digital signature can be adopted on the basis of asymmetric encryption .
Because the secret key is used in pairs , Public key disclosure , And the secret key is confidential ,Alice You can encrypt data with your private key , Others intercepted it and don't know who sent it , and Bob know Alice There is an encrypted data transmission , use Alice Decrypt the public key to view the data ( Here's the picture ).
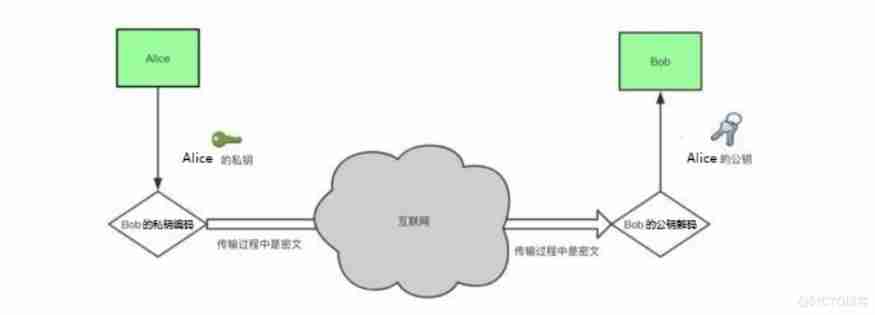
Given the complexity of the transmission environment on the Internet , Public key encryption will also be used RSA Algorithm 、DSA Algorithm 、 Combination of hash algorithm and Algorithm , To ensure the reliability of data encryption transmission .
- DH Algorithm encryption
In addition to the form of public key encryption to achieve key exchange , You can also use DH Algorithm to achieve encryption .
2.1 DH Introduction to algorithm encryption
①DH Secret key exchange by Whitfield · Di fe (Bailey Whitfield Diffie) Martin · Herman (Martin Edward Hellman) stay 1976 In published .
② It's a security protocol , Let both parties establish a key through an insecure channel without any prior information of the other party , This key is generally used as “ Symmetric encryption ” The key is used by both parties in subsequent data transmission .
③DH The mathematical principle is base Discrete logarithm problem , There are asymmetric encryption algorithms that do similar things , Such as :RSA.
④ It is widely used , stay SSH、VPN、Https... All have applications , Modern mi Code cornerstone .
2.2 DH Implementation process
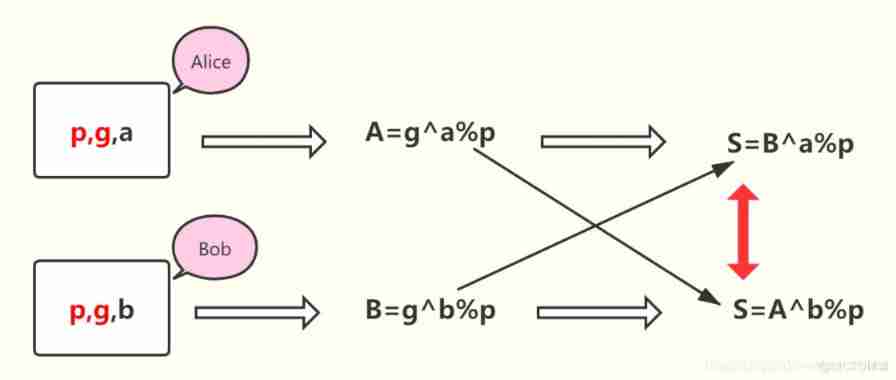
With Alice and Bob For example :
First step :Alice and Bob Negotiate to generate a public integer g And large prime numbers p;
The second step : Privacy data exchange
①Alice Generate privacy data a(a<p), calculated g^a%p, Send to Bob
②Bob Generate privacy data b(b<p), calculated g^b%p, Send to Alice
The third step : Realize secret key exchange
①Alice calculated [(g^b%p)^a]%p = g^ab%p, Generate as key
②Bob calculated [(g^a%p)^b]%p = g^ab%p, Generate as key
At the third step , We can see ,Alice and Bob The secret key obtained is the same , All are g^ab%p, Thus realizing the exchange of secret keys . The implementation process is shown in the following figure :
2.3 DH Example of algorithm encryption
hypothesis Alice and Bob Encrypt the transmitted data , The agreed integer g by 23, Large prime number p by 17,Alice and Bob The privacy data generated respectively are 6 and 11, namely g=23,p=17,a=6,b=11.
① Privacy data exchange link
Alice Send to Bob For the g^a%p=23^6%17=8( Here's the picture ).

Bob Send to Alice For the g^b%p=23^11%17=5( Here's the picture ).

② Realize secret key exchange
Alice Calculation [(g^b%p)^a]%p =5^6%17=2,g^ab%p=23^66%17=2, These two results are the same , If Bob The calculated result is also 2, It shows that secret key exchange is realized ( Here's the picture ).

Bob Calculation [(g^a%p)^b]%p = 8^11%17=2=g^ab%p=23^66%17=2( Here's the picture ).

Here we are ,Alice and Bob It forms a common secret key 2, That is to realize the exchange of secret keys .
Of course ,DH Algorithm encryption also has its own lou hole , For example, private data of both parties a and b Will be discarded , The existence of too long will lead to the risk of leakage . meanwhile , because DH In the transport p、g There is no authentication , So there is an opportunity to be implemented as a middleman gong blow , Replace the data transmitted by both parties . Use some CA Certificates and security protocols , It can effectively enhance the safety and reliability of communication or transmission , However, I won't describe more in this article .
边栏推荐
猜你喜欢

SAP Fiori 应用索引大全工具和 SAP Fiori Tools 的使用介绍
On time and parameter selection of asemi rectifier bridge db207
Breadth first traversal of graph

Excellent open source fonts for programmers
TOP命令详解

Introduction to the use of SAP Fiori application index tool and SAP Fiori tools
![[Matlab] Simulink 同一模块的输入输出的变量不能同名](/img/99/adfe50075010916439cd053b8f04c7.png)
[Matlab] Simulink 同一模块的输入输出的变量不能同名
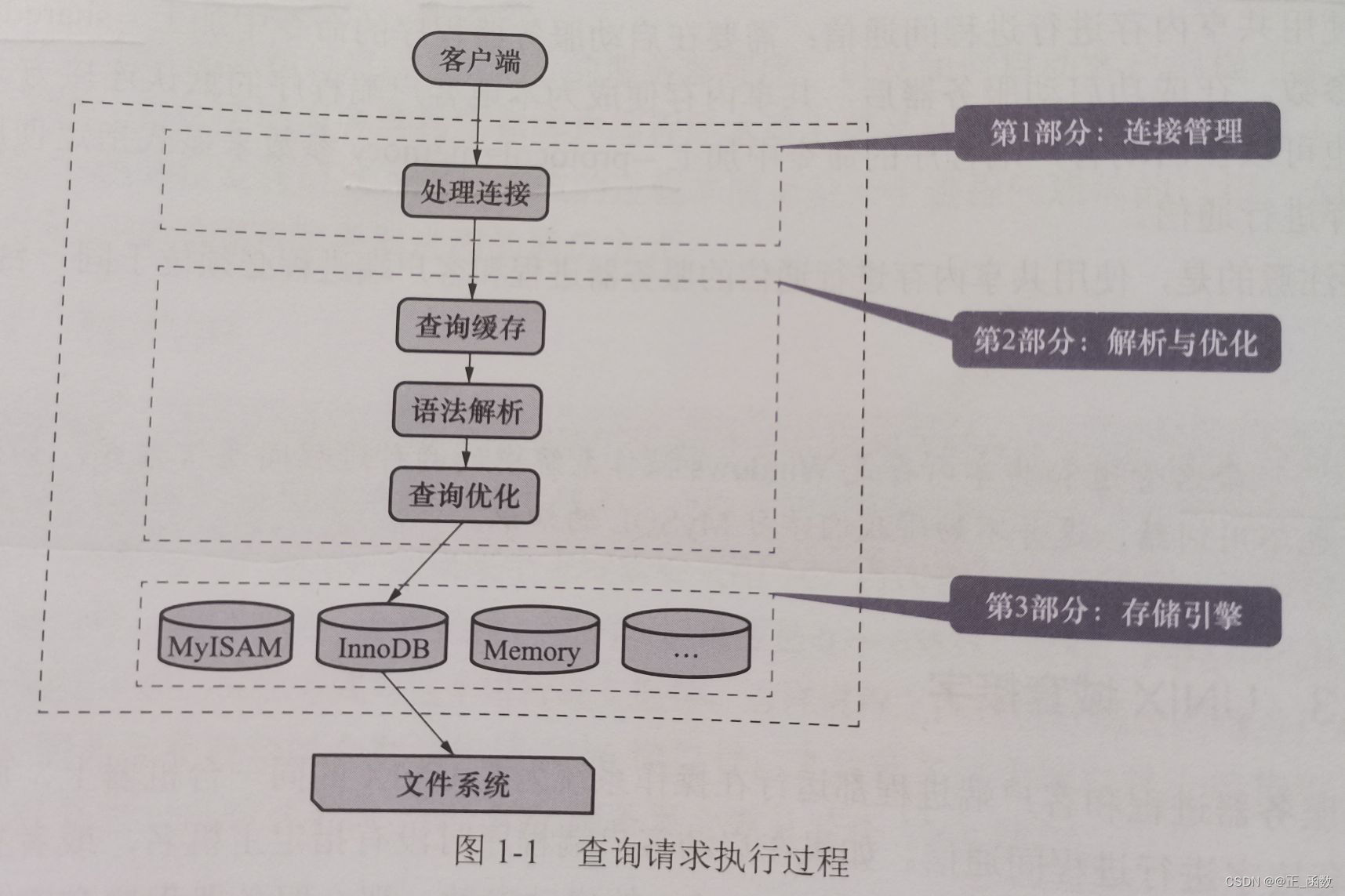
MySQL查询请求的执行过程——底层原理
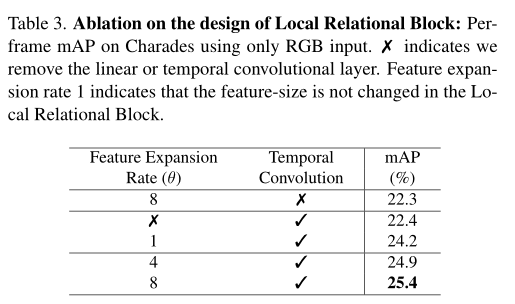
Ms-tct: INRIA & SBU proposed a multi-scale time transformer for motion detection. The effect is SOTA! Open source! (CVPR2022)...
Alibaba cloud international ECS cannot log in to the pagoda panel console
随机推荐
DOM简要
Celery best practices
CRMEB 商城系统如何助力营销?
On time and parameter selection of asemi rectifier bridge db207
MySQL查询请求的执行过程——底层原理
Penetration test information collection - CDN bypass
AFNetworking框架_上传文件或图像server
Reprint: defect detection technology of industrial components based on deep learning
44 colleges and universities were selected! Publicity of distributed intelligent computing project list
Splay
测试行业的小伙伴,有问题可以找我哈。菜鸟一枚~
10、 Process management
Recommend easy-to-use backstage management scaffolding, everyone open source
從交互模型中蒸餾知識!中科大&美團提出VIRT,兼具雙塔模型的效率和交互模型的性能,在文本匹配上實現性能和效率的平衡!...
There is a sound prompt when inserting a USB flash disk under win10 system, but the drive letter is not displayed
Maixll dock camera usage
Windows connects redis installed on Linux
The role of applet in industrial Internet
287. 寻找重复数
阿里云国际版ECS云服务器无法登录宝塔面板控制台