当前位置:网站首页>How to test and decrypt the encryption interface
How to test and decrypt the encryption interface
2022-07-27 13:55:00 【Software testing old Joe】
First , We first need to know which interfaces have encryption requirements .
During business testing , Generally, there are many encryption situations involved in the login interface .
Interface test authentication test
How to test this kind of encrypted interface ?
We can analyze it like this :
First , When the front-end operates functions , Check whether the parameters transmitted from the front end to the interface have been encrypted by the front end .
If it is encrypted by the front end , We can ask front-end personnel , Encryption rules , Directly during interface testing , Pass in the parameters after encryption , Check whether the return result can be obtained correctly .
If it's not the front-end encryption , Then it may be the encryption after the back-end parameters are passed in .
This is the time , What we need to do is to pass in business parameters normally , After calling the interface , After checking the interface request , Whether the data stored in the database is encrypted by the interface , Compare the data encrypted in advance with the database .
Decrypt , In general , We don't test like this , We are more concerned about whether the incoming parameters are correct in the whole data flow .
For example, we will construct the passed in parameters , As long as the normal and abnormal conditions are tested in place in the whole process OK 了 .
边栏推荐
- Matlab digital image processing experiment 2: single pixel spatial image enhancement
- 深度置信网络(DBN)【经典的DBN网络结构是由若干层 RBM(受限波尔兹曼机)和一层 BP 组成的一种深层神经网络】
- Deep confidence network (DBN) [the classical DBN network structure is a deep neural network composed of several layers of RBM (restricted Boltzmann machine) and one layer of BP]
- 使用RecyclerView,实现列表左滑菜单
- 小程序毕设作品之微信校园洗衣小程序毕业设计成品(3)后台功能
- Construction and application of industrial knowledge atlas (I): overview of industrial knowledge atlas
- js回调函数(callback)
- [leetcode] 592. Fraction addition and subtraction
- [C Advanced] pointer array vs array pointer
- Seata's landing practice in ant International Banking
猜你喜欢

建议收藏,PMP应战篇(2)之易混淆知识点
We should learn to check the documented instructions of technical details
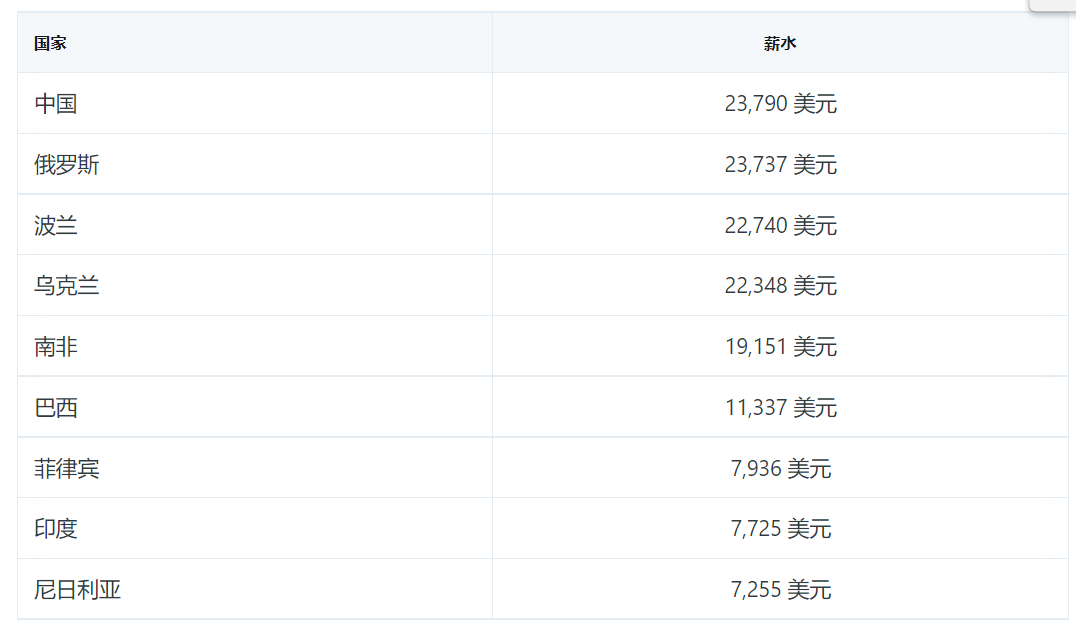
The salary level of programmers in various countries is a little miserable

现在还来得及参加9月份的PMP考试吗?
基于STM32的自由度云台运动姿态控制系统

Deliver temperature with science and technology, vivo appears at the digital China Construction Summit

Data enhancement in image processing

redis集群搭建-使用docker快速搭建一个测试redis集群
13. User web layer services (I)

【实习经验】Date工具类中添加自己实现的方法
随机推荐
English grammar_ Personal pronoun
The salary level of programmers in various countries is a little miserable
Li Hang, director of ByteDance AI Lab: past, present and future of language model
【图论】负环
What are the benefits of taking NPDP
For.. of can be used to traverse which data
[daily question] 1206. Design jump table
《C语言》函数栈帧的创建与销毁--(内功)
我们要学会查看技术细节点的文档化说明
ThinkPHP+宝塔运营环境实现定时任务
剑指Offer 07 重建二叉树 -- 从中序与后序遍历序列构造二叉树
SQL tutorial: introduction to SQL aggregate functions
Accuracy improvement method: efficient visual transformer framework of adaptive tokens (open source)
Software testing system architecture designer concise tutorial | software testing
【C语言入门】ZZULIOJ 1021-1025
网络异常流量分析系统设计
Construction and application of industrial knowledge atlas (3): commodity knowledge fusion
JWT login expiration - automatic refresh token scheme introduction
[leetcode] 592. Fraction addition and subtraction
基于C语言的LR1编译器设计