当前位置:网站首页>Object. Usage of keys()
Object. Usage of keys()
2022-07-04 16:45:00 【Elephants and ants】
Object.keys(obj)
- Parameters : To return an object that enumerates its own properties
- Return value : An array of strings representing all enumerable properties of a given object
1. Deal with people , Returns an enumerable array of properties
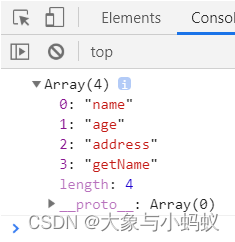
let person = {
name:" Zhang San ",age:25,address:" Shenzhen ",getName:function(){
}};
console.log(Object.keys(person));
Object.keys(item.alarmAttribute || {
}).length)
2. Handling arrays , Returns an array of index values
let arr = [1,2,3,4,5,6];
console.log(Object.keys(arr)); //["0", "1", "2", "3", "4", "5"]
3. Processing strings , Returns an array of index values
let str = "ikun Hello ";
console.log(Object.keys(str)); // ["0", "1", "2", "3", "4", "5"]
4. Common skills
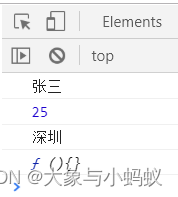
let person = {
name:" Zhang San ",age:25,address:" Shenzhen ",getName:function(){
}};
Object.keys(person).map((key)=>{
console.log(person[key]); // Get the corresponding value of the attribute , Do something about it
})
Project use
Object.keys(dvehicleInfo).forEach(key => {
if (key === "containervolume" && dvehicleInfo[key] === "") {
this.Volume_Static = 1;
if (dvehicleInfo.container) {
dvehicleInfo.container.split(",").map((item, index) => {
this.containerOptions[index].len = item;
});
}
}
边栏推荐
- Opencv learning -- geometric transformation of image processing
- Will the memory of ParticleSystem be affected by maxparticles
- Market trend report, technical innovation and market forecast of electrochromic glass and devices in China and Indonesia
- Research Report on market supply and demand and strategy of China's well completion equipment industry
- Hair and fuzz interceptor Industry Research Report - market status analysis and development prospect forecast
- 跳跃表实例
- 中位数与次序统计量
- Detailed process of DC-2 range construction and penetration practice (DC range Series)
- APOC自定义函数和过程
- What does IOT engineering learn and work for?
猜你喜欢

AI system content recommendation issue 24
Using celery in projects
![[hcie TAC] question 5 - 1](/img/e0/1b546de7628695ebed422ae57942e4.jpg)
[hcie TAC] question 5 - 1
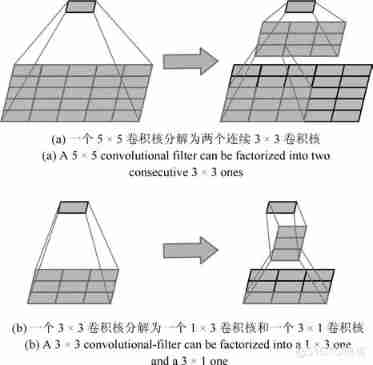
Overview of convolutional neural network structure optimization
Working group and domain analysis of Intranet
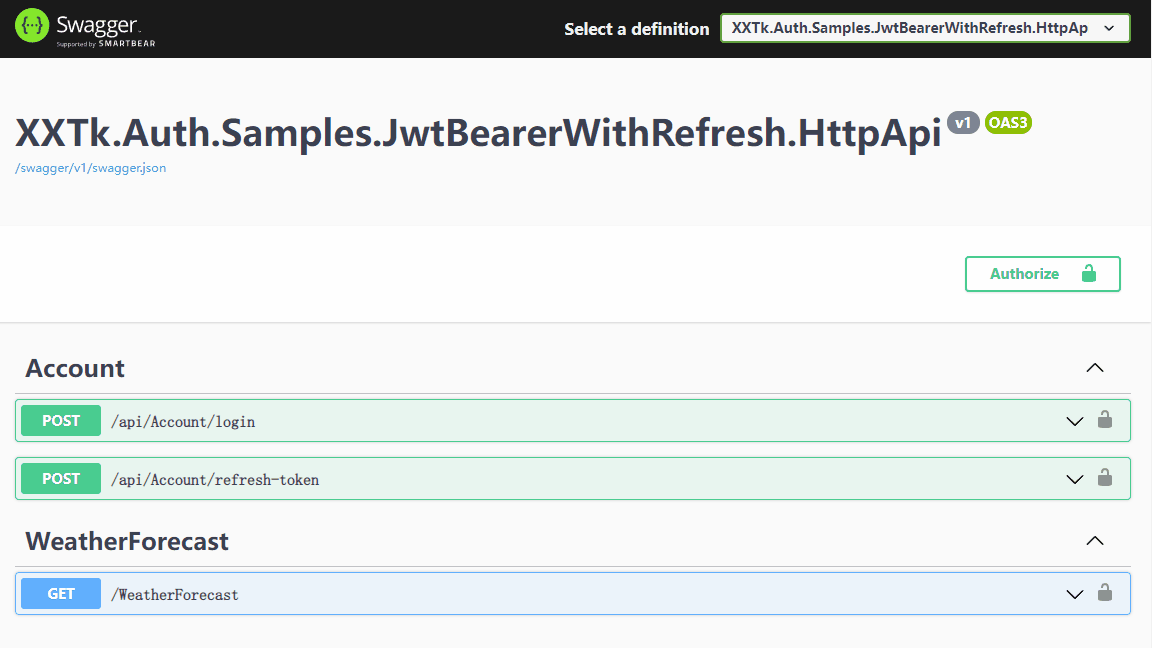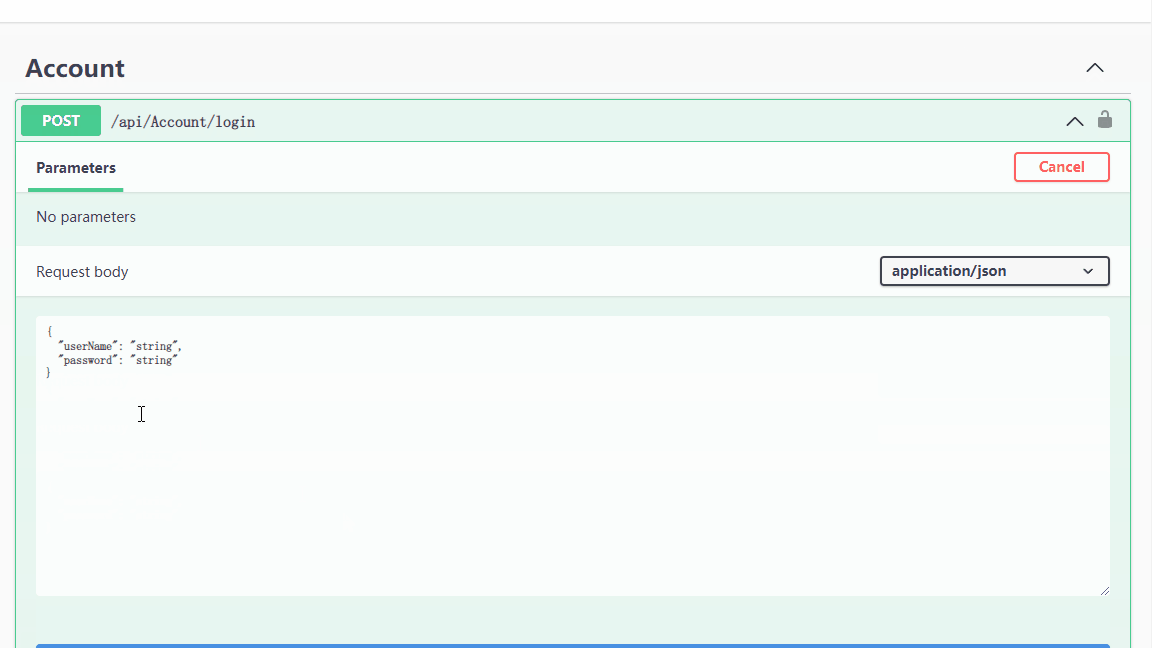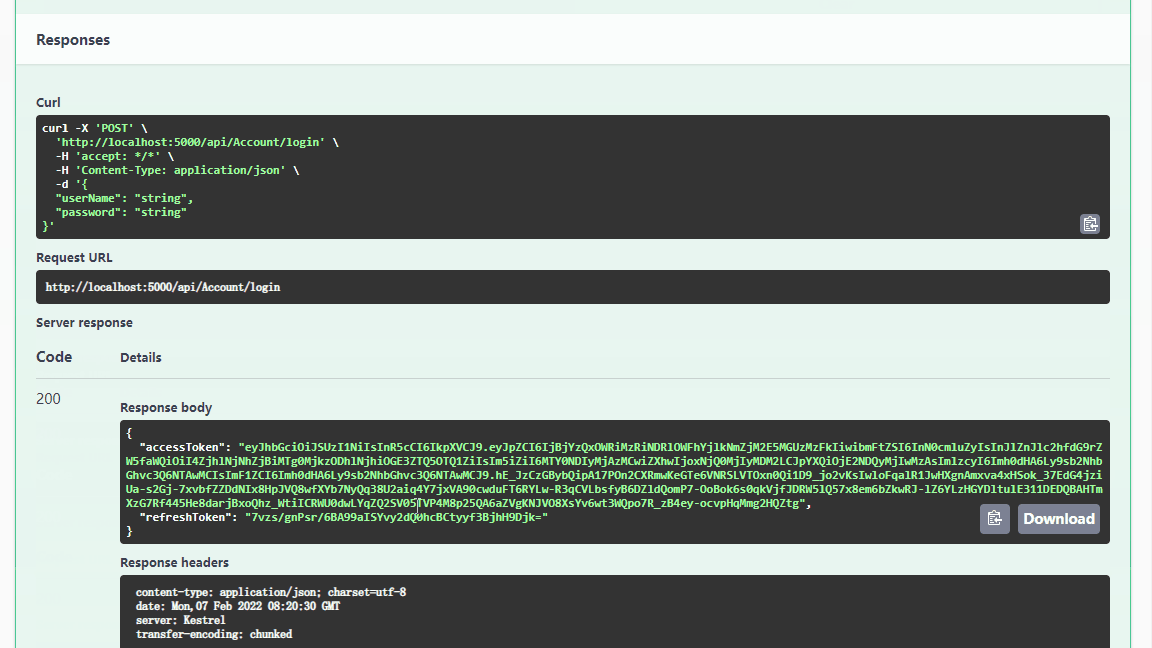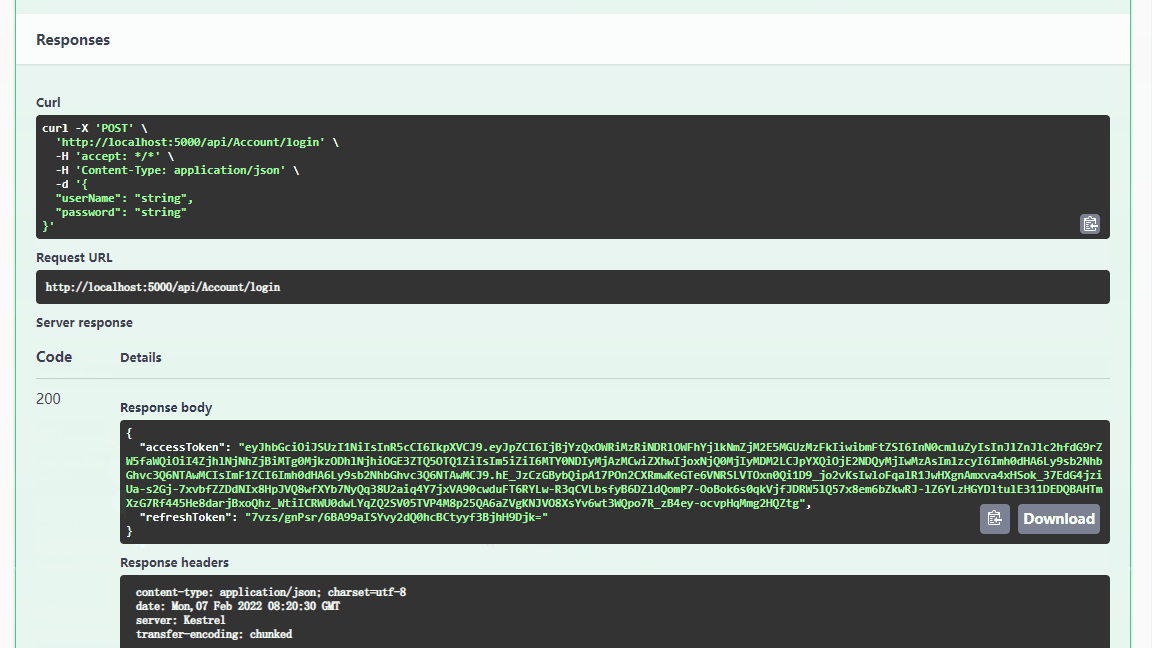
Understand asp Net core - Authentication Based on jwtbearer
![[North Asia data recovery] a database data recovery case where the disk on which the database is located is unrecognized due to the RAID disk failure of HP DL380 server](/img/79/3fab19045e1ab2f5163033afaa4309.jpg)
[North Asia data recovery] a database data recovery case where the disk on which the database is located is unrecognized due to the RAID disk failure of HP DL380 server
D3D11_ Chili_ Tutorial (2): draw a triangle

overflow:auto与felx结合的用法
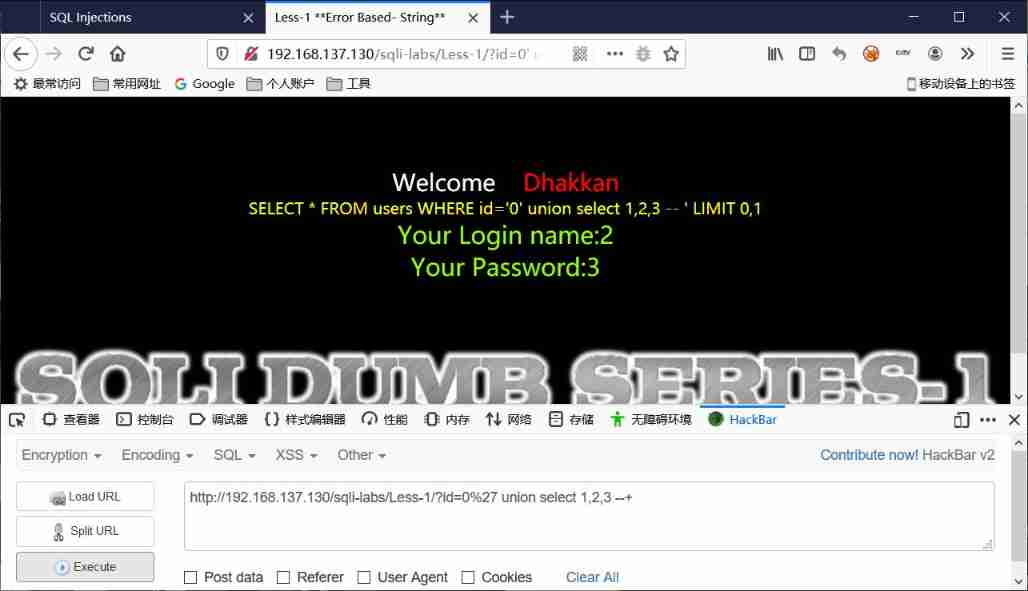
Principle and general steps of SQL injection
随机推荐
. Net applications consider x64 generation
Accounting regulations and professional ethics [7]
After the eruption of Tonga volcano, we analyzed the global volcanic distribution and found that the area with the most volcanoes is here!
Market trend report, technical innovation and market forecast of taillight components in China
Some fields of the crawler that should be output in Chinese are output as none
Interpretation of the champion scheme of CVPR 2020 night target detection challenge
线程池的使用和原理
What does IOT engineering learn and work for?
[tutorial] yolov5_ DeepSort_ The whole process of pytoch target tracking and detection
Integration of ongdb graph database and spark
2021 Google vulnerability reward program review
How to contribute to the source code of ongdb core project
Understand asp Net core - Authentication Based on jwtbearer
《吐血整理》保姆级系列教程-玩转Fiddler抓包教程(2)-初识Fiddler让你理性认识一下
Research Report on market supply and demand and strategy of China's Sodium Tetraphenylborate (cas+143-66-8) industry
Change the mouse pointer on ngclick - change the mouse pointer on ngclick
Visual Studio 2019 (LocalDB)MSSQLLocalDB SQL Server 2014 数据库版本为852无法打开,此服务器支持782
What is the catalog of SAP commerce cloud
What should ABAP do when it calls a third-party API and encounters garbled code?
Filtered off site request to