当前位置:网站首页>(4) Web security | penetration testing | network security web site source code and related analysis
(4) Web security | penetration testing | network security web site source code and related analysis
2022-07-06 07:07:00 【Black zone (rise)】
as everyone knows :
web Source code is a very important source of information in security testing , It can be used for code audit vulnerabilities and information breakthrough , among WEB There are many technologies in the source code that need concise analysis .
eg: obtain ASP The source code can be downloaded from the default database , To obtain the source code vulnerability of some other script, you can conduct code audit, mine or analyze its business logic, etc , Therefore, the acquisition of source code will provide more ideas for later security testing
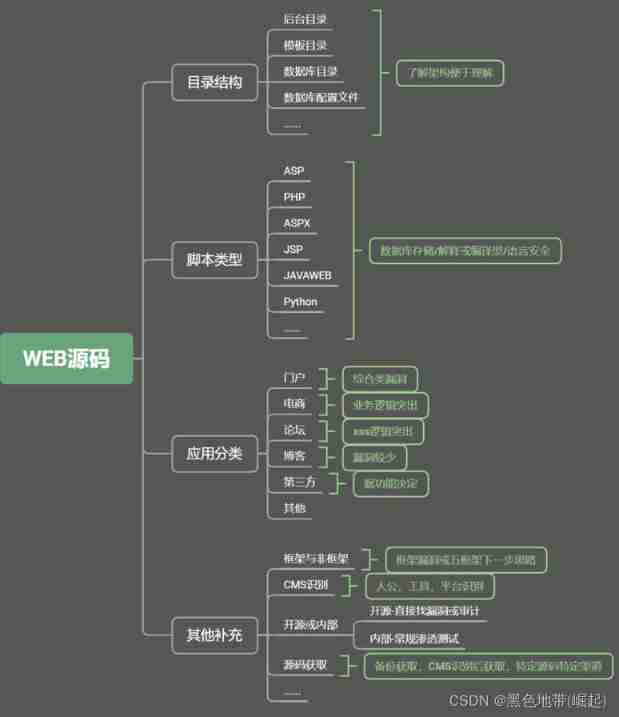
Web Source directory structure
Database configuration file , Background Directory , The template directory , Database directory, etc
admin---------------------------------- Website background Directory
data------------------------------------ Database related directories
install---------------------------------- The installation directory
member------------------------------- Membership directory
template------------------------------ The template directory ( Build an overall architecture related to the website )
data(confing.php)-------------- Database configuration file , Communication information of website and database , Connection account password , You can connect to each other's database , From the database to get the source code of this website, which involves the administrator's account and password .
You can see how to open a source code of Baidu online , Some small ones may only have some directories
Web Source script type
ASP,PHP,ASPX,JSP,JAVAWEB And other script type source code security issues
Check the type of website through the file directory
About Web Source application classification
Portal site --------------------------- comprehensive
Online retailers --------------------------------- Business logic
Forum ---------------------------------XSS
Blog --------------------------------- Less
The third party ------------------------------ Look at its function
Access to source code : Search for , Free fish Taobao , Third party source station , Corresponding to various industries .
Open source : You can search the vulnerability related articles on the Internet .
Inside : Routine penetration tests , Use scanning tools to judge .
If you can't get the source code, you can find the same type of source code analysis
Identify the cms, Here's a asp Script written website

The bottom display technical support is GOOMAY company-developed ,
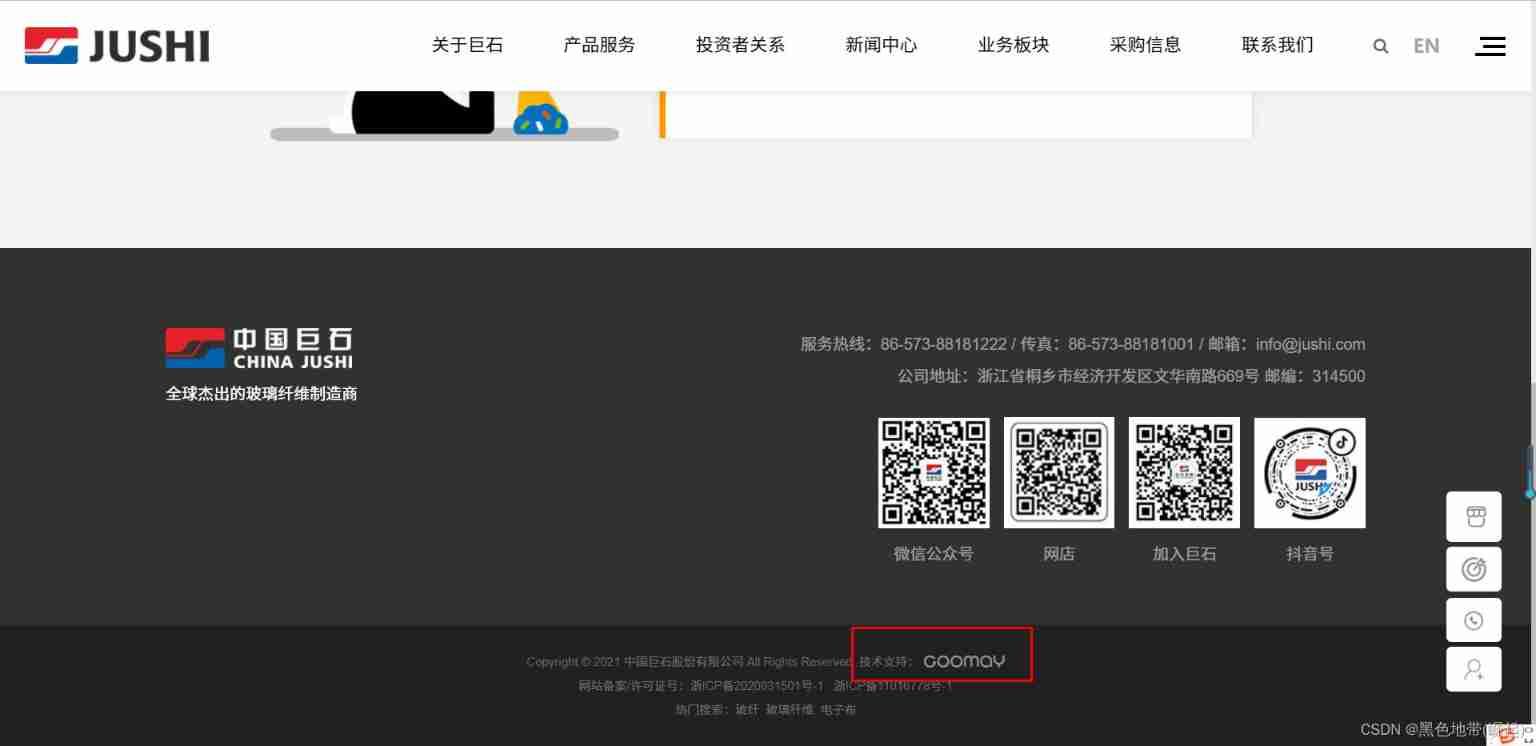
Then I want to find out if he is using cms Developed , Developed by ourselves
Add /robots.txt See if you can see
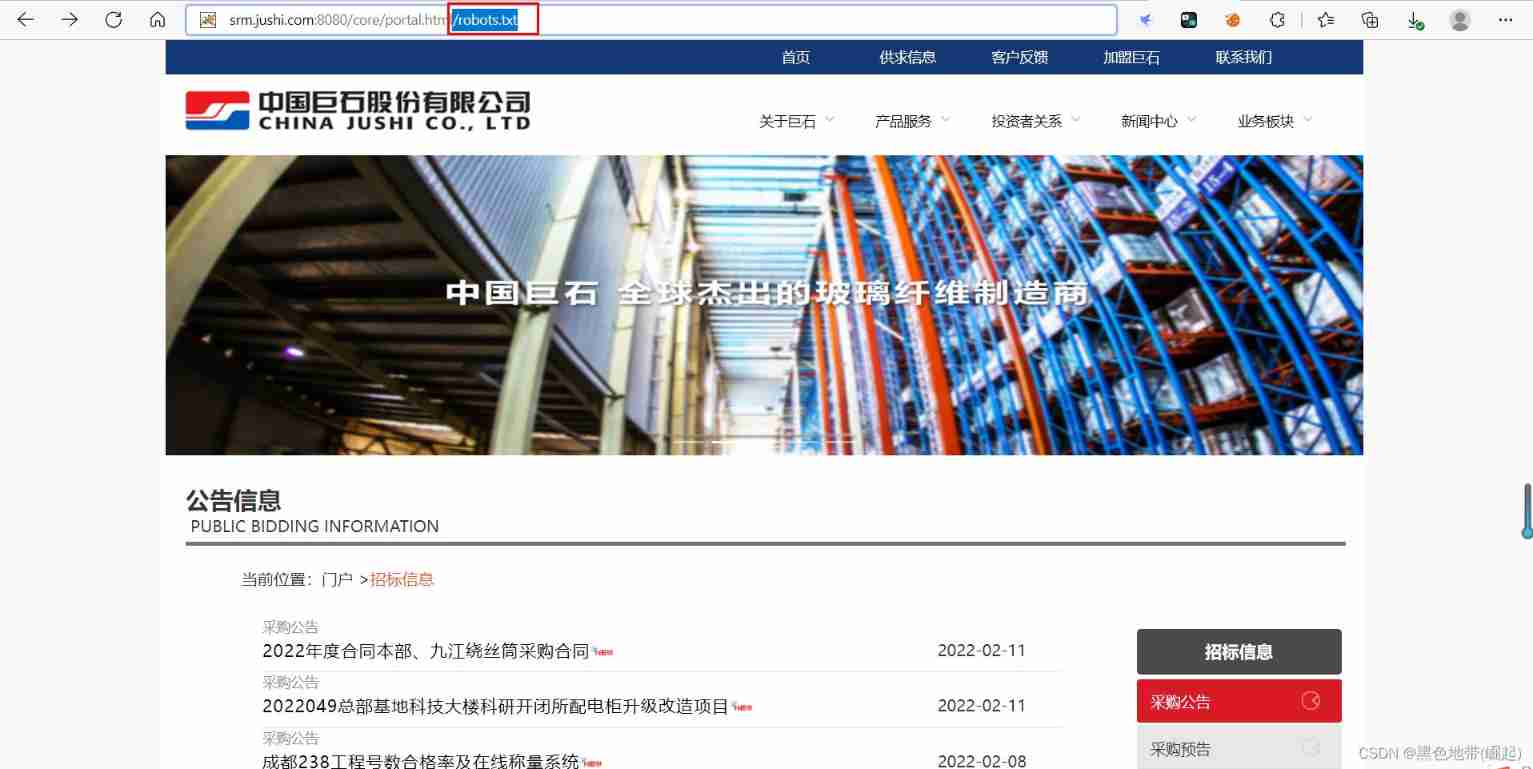
The result is the login page

Now I'm going to try this one that provides technical support , It is developed by ourselves , still cms Developed
① If we analyze the used cms edition , You can find the vulnerability of the corresponding version of Baidu online
② If the website has been patched , Then consider scanning tools and related source code for analysis
③ If they developed it bit by bit , No source code , It's time to scan bit by bit
边栏推荐
- supervisor 使用文档
- Attributeerror: can 't get attribute' sppf 'on < module' models. Common 'from' / home / yolov5 / Models / comm
- A method to measure the similarity of time series: from Euclidean distance to DTW and its variants
- Brief introduction to the curriculum differences of colleges and universities at different levels of machine human major -ros1/ros2-
- TS基础篇
- Uncaught typeerror: cannot red properties of undefined (reading 'beforeeach') solution
- Cookie Technology & session Technology & ServletContext object
- LeetCode Algorithm 2181. 合并零之间的节点
- 18.多级页表与快表
- Arduino tutorial - Simon games
猜你喜欢
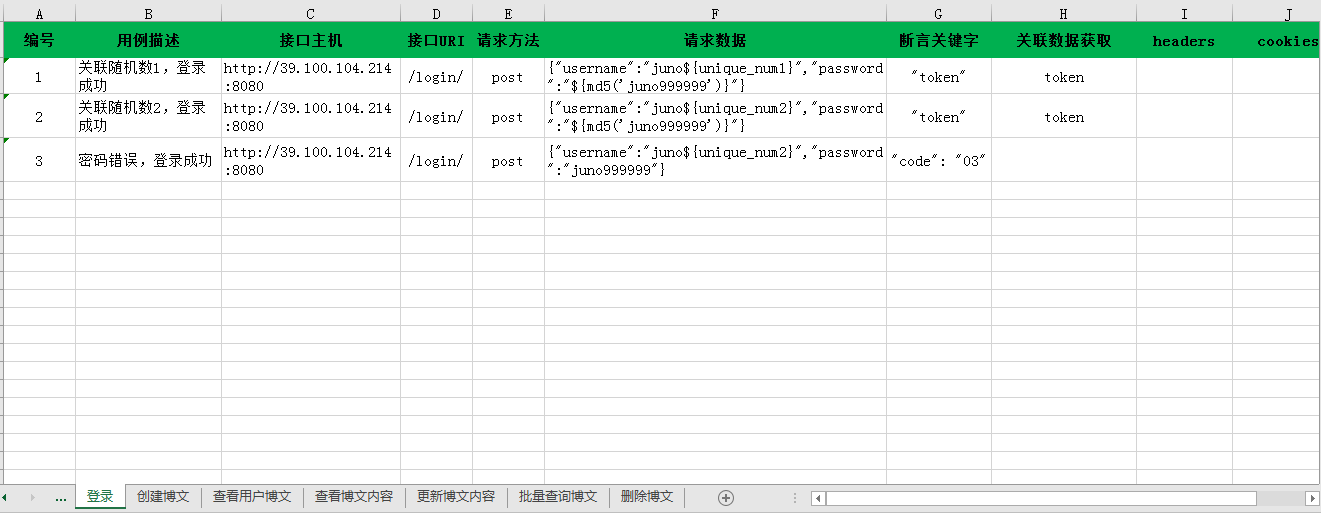
接口自动化测试框架:Pytest+Allure+Excel
![[daily question] 729 My schedule I](/img/6b/a9fef338ac09caafe628023f066e1f.png)
[daily question] 729 My schedule I
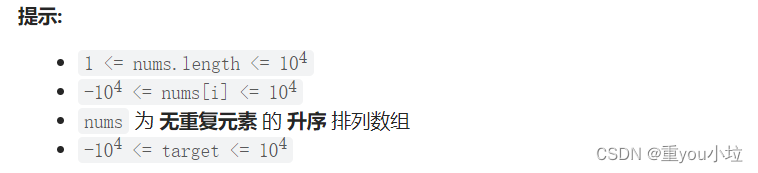
Leetcode35. search the insertion position (simple, find the insertion position, different writing methods)
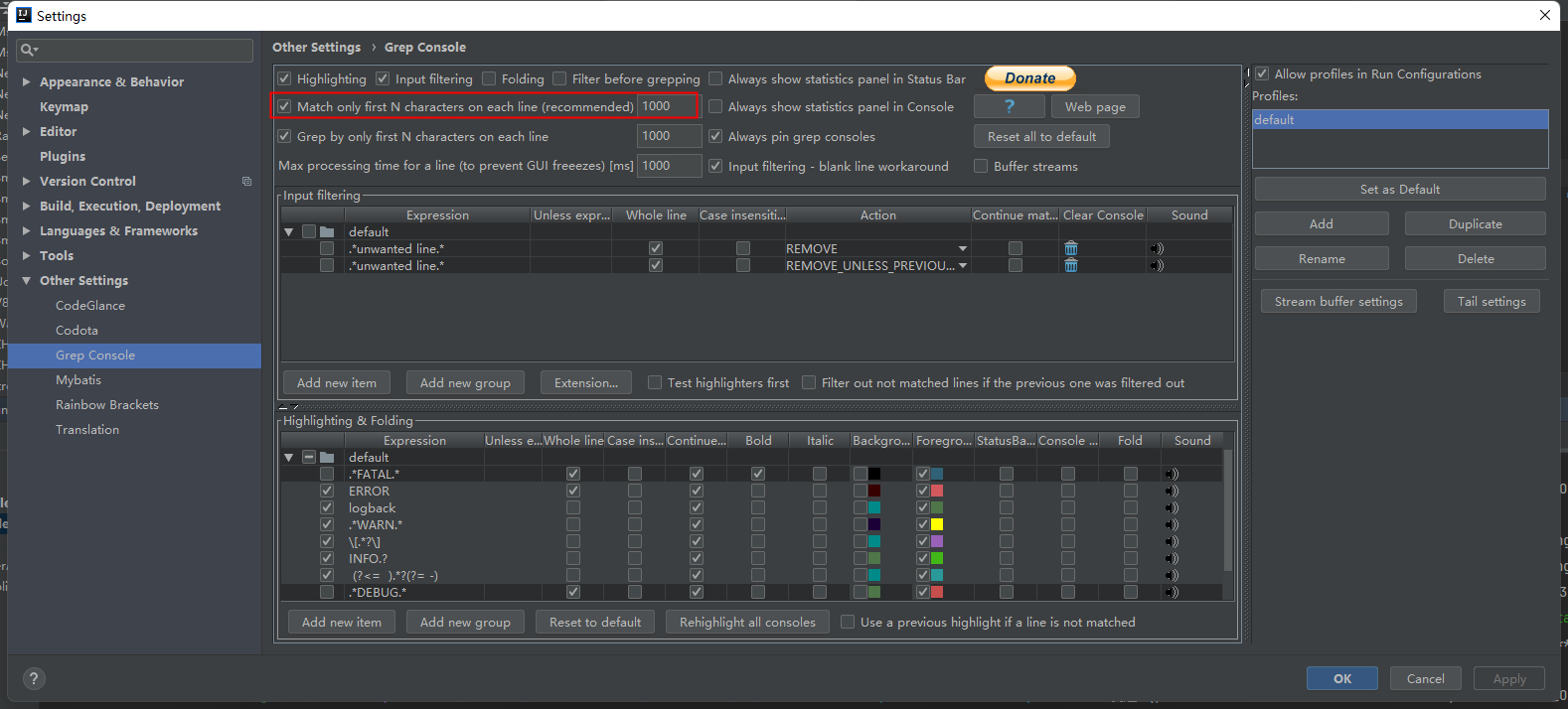
idea控制台彩色日志
Supporting title of the book from 0 to 1: ctfer's growth road (Zhou Geng)

因高额网络费用,Arbitrum 奥德赛活动暂停,Nitro 发行迫在眉睫
Proteus -- Serial Communication parity flag mode
leetcode6109. 知道秘密的人数(中等,周赛)
Kubernetes cluster builds ZABBIX monitoring platform
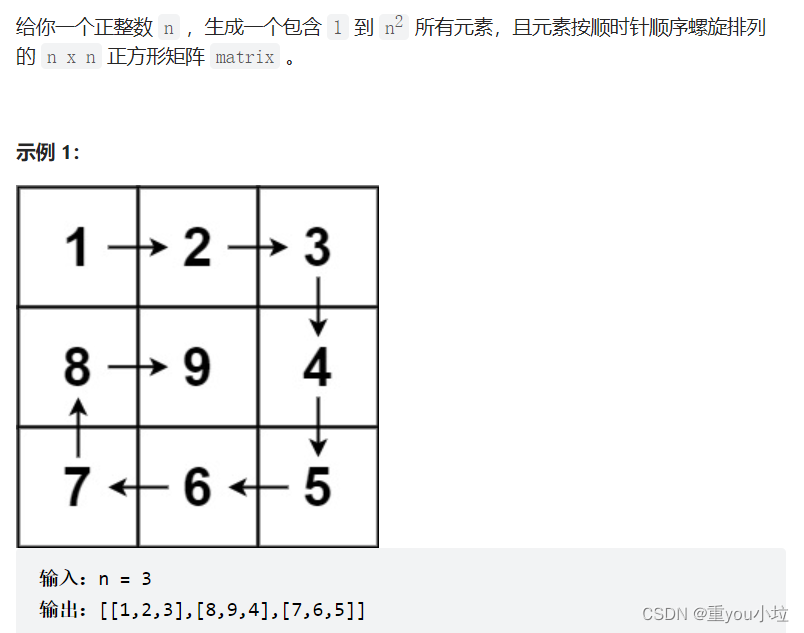
Leetcode59. spiral matrix II (medium)
随机推荐
How to find a medical software testing institution? First flight software evaluation is an expert
ROS learning_ Basics
supervisor 使用文档
巴比特 | 元宇宙每日必读:中国互联网企业涌入元宇宙的群像:“只有各种求生欲,没有前瞻创新的雄心”...
OpenGL ES 学习初识(1)
Cookie Technology & session Technology & ServletContext object
Missing monitoring: ZABBIX monitors the status of Eureka instance
Leetcode 78: subset
指尖上的 NFT|在 G2 上评价 Ambire,有机会获得限量版收藏品
Setting and using richview trvstyle template style
简单描述 MySQL 中,索引,主键,唯一索引,联合索引 的区别,对数据库的性能有什么影响(从读写两方面)
Librosa audio processing tutorial
Simple use of MySQL database: add, delete, modify and query
[some special grammars about C]
[daily question] 729 My schedule I
The author is dead? AI is conquering mankind with art
软件测试外包到底要不要去?三年真实外包感受告诉你
ROS2安装及基础知识介绍
After sharing the clone remote project, NPM install reports an error - CB () never called! This is an error with npm itself.
Wechat official account infinite callback authorization system source code, launched in the whole network