当前位置:网站首页>Learn winpwn (2) -- GS protection from scratch
Learn winpwn (2) -- GS protection from scratch
2022-07-06 11:21:00 【azraelxuemo】
List of articles
GS protection mechanism
Study windows pwn The first protection mechanism to recognize is GS, He corresponds to linux Under the canary Protect .
His purpose is , stay old_ebp Insert a piece of data before , And then pop ebp Check the data before , If it's not right , Indicates that a stack overflow has occurred , Then end the execution
How to open GS Protect
Get into vs2022, Click item 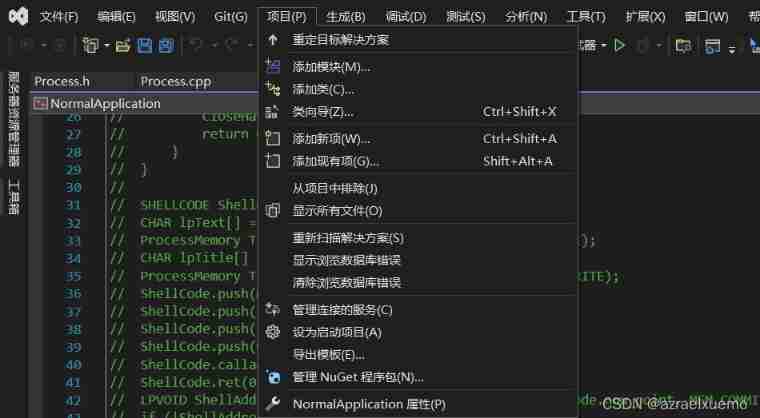
Select Properties , You can see that the security check is enabled 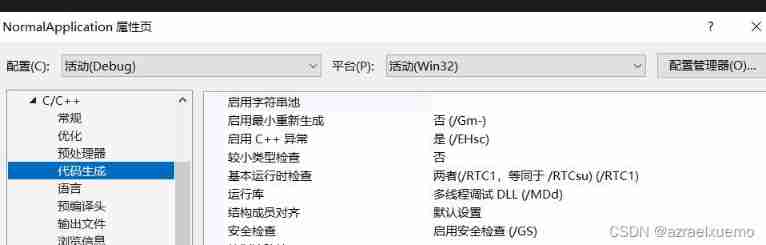
You can choose to disable checking 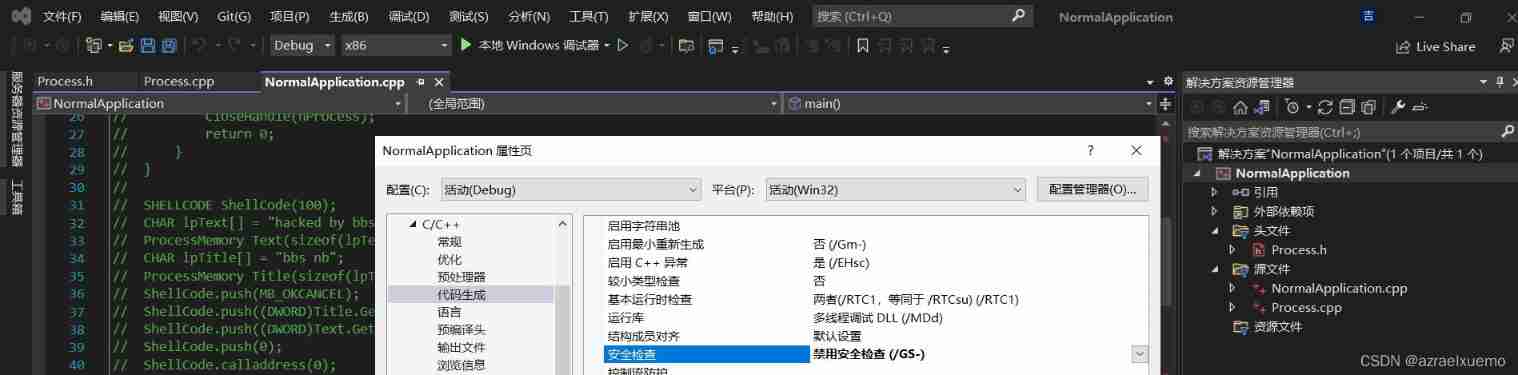
close GS Stack structure of
Take the following simple function as an example
( Be careful , Due to the problem of compilation optimization , The generated code may not be exactly the same , But generally consistent )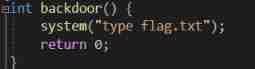
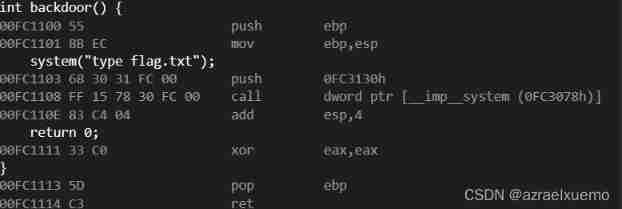
The corresponding general function call is
push ebp
mov ebp,esp
pop ebp
ret
When a function is called , First of all be push Parameters , then call, Corresponding stack structure 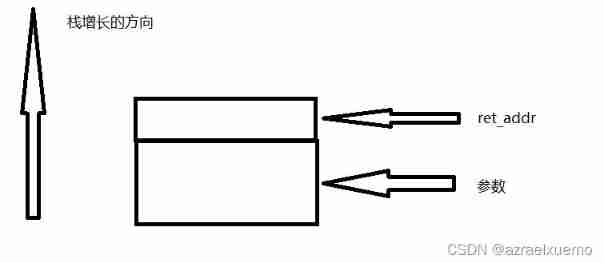
And then we push ebp, So the complete structure 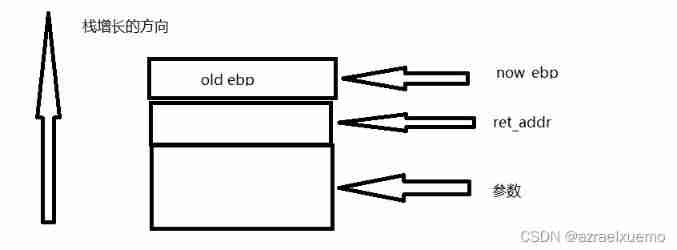
Turn on GS Stack structure of
First of all, make sure
Not all functions are applied GS, The following situations will not apply GS
- . Function does not contain a buffer
- Functions are marked with unprotected keywords
- Function contains embedded assembly code in the first statement
- Buffer is not 8 Byte type and size not greater than 4 Bytes
For example, our function above , Turn on GS after , There is no change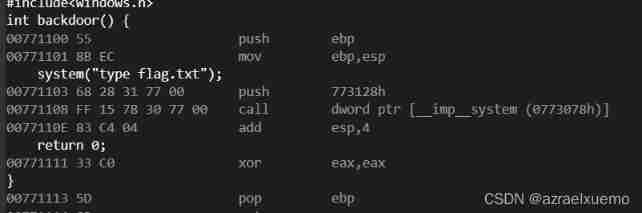
But introduce #pragma strict_gs_check(on) You can add... To any type of function Security Cookie.( But it proves that , Like ours backdoor Still won't be affected )
Then let's directly use the official example of Microsoft
#pragma strict_gs_check(on)
void** ReverseArray(void** pData,
size_t cData)
{
void* pReversed[20];
for (size_t j = 0, i = cData; i; --i, ++j)
pReversed[j] = pData[i];
for (size_t i = 0; i < cData; ++i)
pData[i] = pReversed[i];
return pData;
}
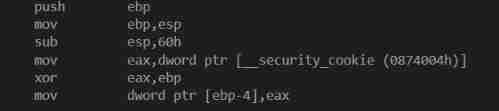
Here we first make a sub esp,60h Because our parameters ,gs Protection is used ebp To address , So as invisible
Here we can see through the compilation GS The algorithm of
data Part of the securiy_cookie^now_ebp It's the current gs value
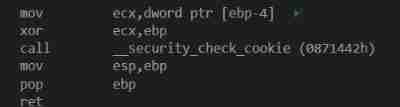
Similarly, at the end , Also put gs^now_ebp And then call __security_check_cookie()
This code is very concise , Just compare , If it's different, jump to failure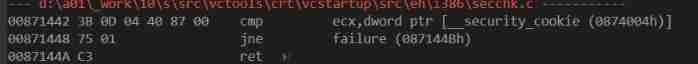
This is the addition of GS Protected stack structure 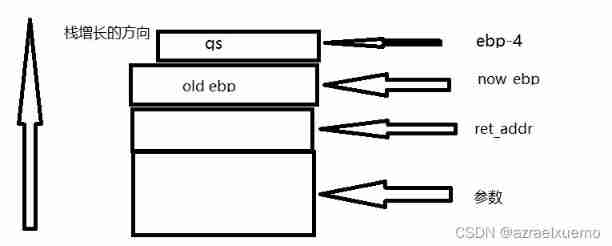
How to judge whether the program has GS Protect
Originally intended to use winchecksec
But it turns out , Not reliable at all
Or honestly see for yourself , Because some functions are on GS Protecting him is not necessarily necessary
The key is to look at disassembly
Is there any at the beginning xor register ,ebp( The register must be security cookie)push register
But should pay attention to , This GS The value of is not necessarily in ebp-4, If set seh Handle , This gs be located ebp-0x1c It's about
how bypass GS
Format string vulnerability
If you can see printf(buf),buf controllable
Then you can exploit the format string vulnerability , Introduce more than one %p( The quantity should be controlled ) that will do
···
#define _CRT_SECURE_NO_WARNINGS
#include<stdio.h>
int main()
{
char tmp[20];
scanf("%s",tmp);
printf(tmp);
return 0;
}
···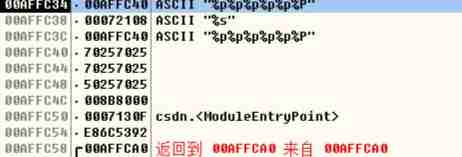
By debugging , find printf Stack when calling , You can see the top is us printf Parameters of , That's the address , So every item in it starts from the next address after the parameter , That is to say 00affc38 The content of corresponds to the first %p
that 00affc58 yes ebp, So it needs to leak to 00affc54 The location of , That's what we need 8 individual %p
Then rerun , Due to stack randomization , The address may be different 
When performing the push ebp after ,esp Point to the current parameter 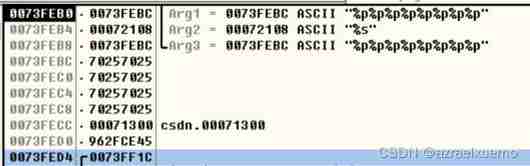
You can see this time gs yes 0073fed0 The value of the location , See if it can leak
Just the last one , At this time, you only need to intercept the string 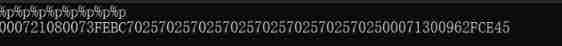
Then when the stack overflows , We can directly put the original gs Fill in the value of , Then jump to the address of the back door
Copy \x00 truncation
Here I use something similar web The direction of the \x00 truncation
Because we often see such copied code
int copy(char* a, int len) {
setbuf(stdout, 0);
setbuf(stdin, 0);
int i;
for (i = 0; i < len; i++) {
char tmp = getchar();
if (tmp == '\n') {
*(char*)(a + i) = '\0';
break;
}
else {
*(char *)(a + i )= tmp;
}
}
return i;
}
This code is copying , And then if \n It's over and replaced with \0, There seems to be no leak on the surface
Let's actually take a look
#define _CRT_SECURE_NO_WARNINGS
#include<stdio.h>
int copy(char* a, int len) {
setbuf(stdout, 0);
setbuf(stdin, 0);
int i;
for (i = 0; i < len; i++) {
char tmp = getchar();
if (tmp == '\n') {
*(char*)(a + i) = '\0';
break;
}
else {
*(char*)(a + i) = tmp;
}
}
return i;
}
int main()
{
char tmp[20];
copy(tmp, 20);
printf("%s", tmp);
return 0;
}
When the input 20 individual 0 after , You can see , Finally, there are many garbled codes , What's going on , Let's debug 
When the input 20 individual 61 after , Found the stack full , But no 00 truncation , So once printf(*
%s") Because I can't see \x00, He will always output , Output all the following data , Until I met the first one \x00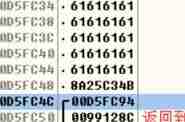
This can be used winpwn Of u32 To convert
The code looks like this
io.sendline("a"*19+"@")
io.recvuntil("@")
u32(io.recv(4))
Now that I know gs, Then it can be disclosed casually
边栏推荐
- Principes JDBC
- Deoldify项目问题——OMP:Error#15:Initializing libiomp5md.dll,but found libiomp5md.dll already initialized.
- 安全测试涉及的测试对象
- 01 project demand analysis (ordering system)
- Project practice - background employee information management (add, delete, modify, check, login and exit)
- Attention apply personal understanding to images
- QT creator runs the Valgrind tool on external applications
- AcWing 179.阶乘分解 题解
- [AGC009D]Uninity
- Ansible practical Series II_ Getting started with Playbook
猜你喜欢
Windows下安装MongDB教程、Redis教程
Some problems in the development of unity3d upgraded 2020 VR
Did you forget to register or load this tag 报错解决方法
![[free setup] asp Net online course selection system design and Implementation (source code +lunwen)](/img/ac/b518796a92d00615cd374c0c835f38.jpg)
[free setup] asp Net online course selection system design and Implementation (source code +lunwen)
Generate PDM file from Navicat export table
安装numpy问题总结
How to build a new project for keil5mdk (with super detailed drawings)
图像识别问题 — pytesseract.TesseractNotFoundError: tesseract is not installed or it‘s not in your path
Windows cannot start the MySQL service (located on the local computer) error 1067 the process terminated unexpectedly
![[C language foundation] 04 judgment and circulation](/img/59/4100971f15a1a9bf3527cbe181d868.jpg)
[C language foundation] 04 judgment and circulation
随机推荐
Install mysql5.5 and mysql8.0 under windows at the same time
[recommended by bloggers] asp Net WebService background data API JSON (with source code)
Invalid default value for 'create appears when importing SQL_ Time 'error reporting solution
MySQL other hosts cannot connect to the local database
Basic use of redis
报错解决 —— io.UnsupportedOperation: can‘t do nonzero end-relative seeks
Unable to call numpy in pycharm, with an error modulenotfounderror: no module named 'numpy‘
QT creator shape
Test objects involved in safety test
Mysql 其他主机无法连接本地数据库
02-项目实战之后台员工信息管理
SSM integrated notes easy to understand version
AcWing 1294. Cherry Blossom explanation
[蓝桥杯2020初赛] 平面切分
自动机器学习框架介绍与使用(flaml、h2o)
Ubuntu 20.04 安装 MySQL
Django运行报错:Error loading MySQLdb module解决方法
csdn-Markdown编辑器
Database advanced learning notes -- SQL statement
Install mongdb tutorial and redis tutorial under Windows